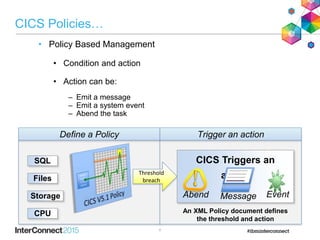
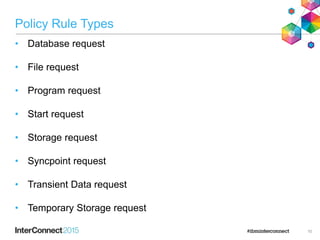
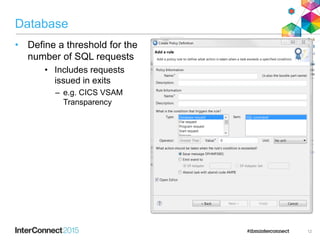
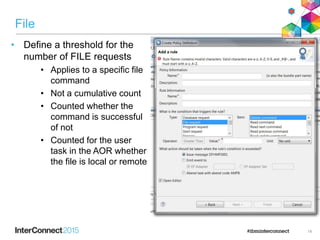
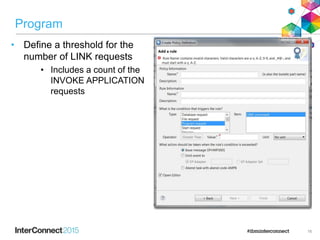
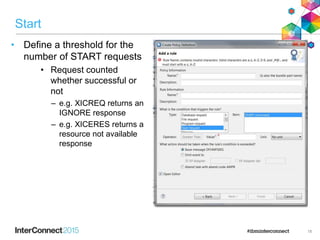
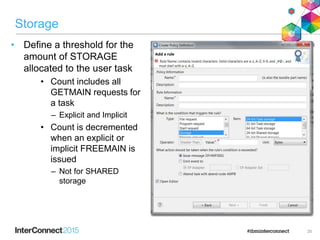
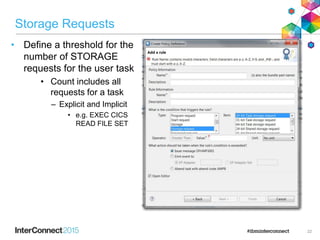
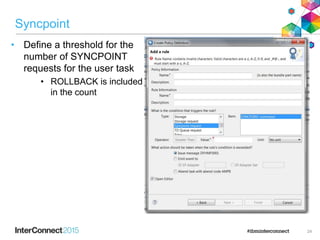
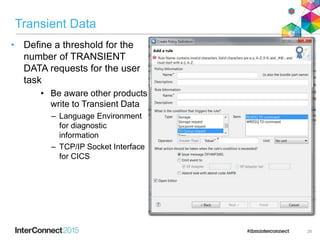
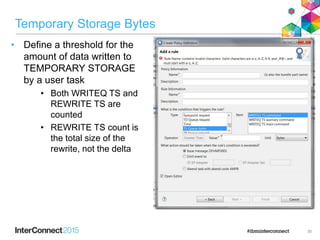
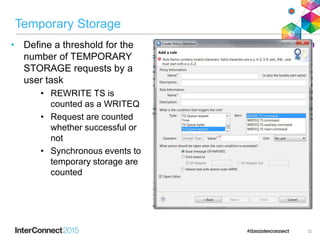
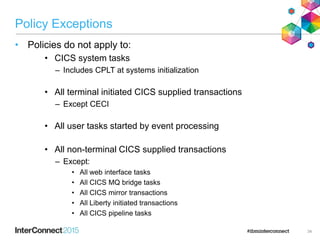
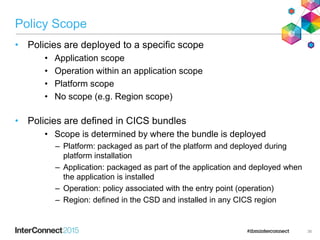
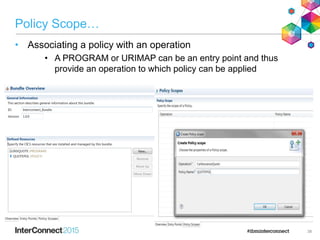
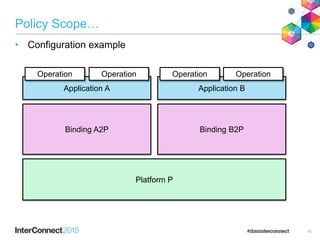
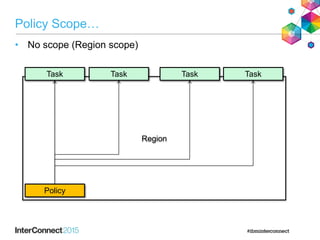
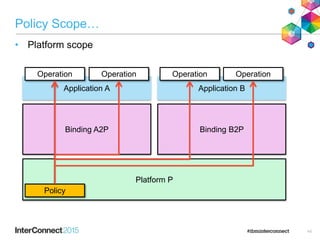
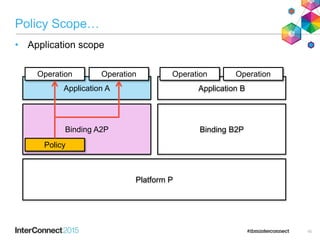
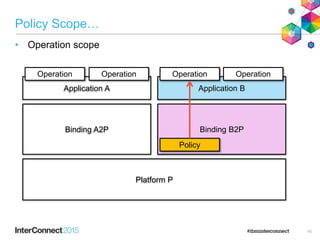
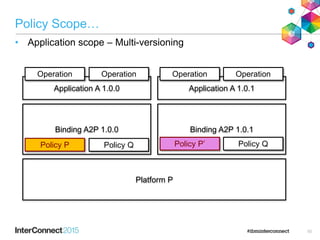
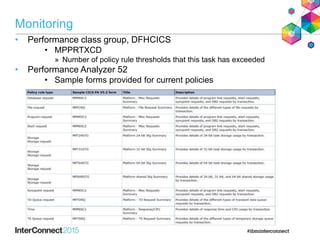
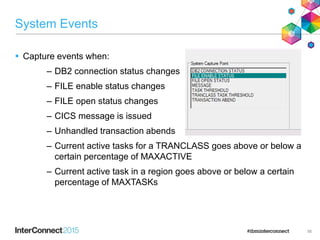
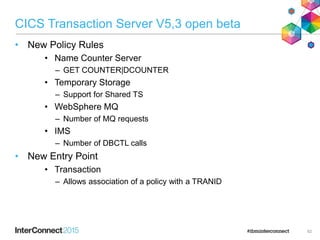
The document discusses CICS policy-based management, which allows users to set resource consumption thresholds for applications and take actions against rogue processes. Policies can be defined and bundled to control application and platform behavior, enabling automated responses such as notifications or task abortion. This new capability empowers users to proactively manage application performance and protect their systems.