This document discusses methods for discovering emerging topics in social streams using two approaches: NADS (Notice-Abnormality based Discovery of Subjects) and VFDT (Very Fast Decision Trees). It proposes a probability model that captures both the normal posting behavior of users as well as the frequency of users being mentioned in posts. This model is used to quantitatively measure the novelty and potential impact of a post based on user commenting behavior. The approaches can identify new topics as early or earlier than text-frequency based approaches, especially when topics are poorly represented by post texts alone. The document provides details on implementing the probability model, calculating text frequency scores, deriving anomaly scores, using change point detection to recognize emerging topics, and

![International Journal of Computer Sciences and Engineering Vol.-3(8), PP(136-139) Aug 2015, E-ISSN: 2347-2693
© 2015, IJCSE All Rights Reserved 137
words and considers just the nonverbal parts of the post.
Word recurrence is figured at that point again each word
which will be taken predominantly at that point again
extraction of the topic. The limitation is that a term-
recurrence based approach could endure from the
uncertainty caused by equivalent words at that point again
homonyms (plurals).It can’t be connected at the point when
the substance of the messages are for the most part non-
literary information. At that point again e.g. “great life
depends on liver”, where liver might be organ at that point
again living person, so there will be an uncertainty problem.
We can’t apply the system at the point when the content is
non-literary information.
II. IMPLEMENTATION DETAILS
2.1 PROBABILITY DISTRIBUTION
Relevancy Probability Model
Fig.2.1 Relevancy likelihood Model
We characterize a post in a social system by the number of
remarks it contains, and the set of clients who are said in the
post. We too consolidate the record recurrence into our
likelihood model which will upgrade the disco
exceptionally process. In place of joint dispersion we find
conditional joint likelihood which comprises of two parts:
the likelihood of the number of comment/ notice and the
likelihood of number of mentioned, both based on term
(word) frequency. The littler the term recurrence esteem
littler will be the likelihood of notice and mentioned.
1: Find likelihood of number of notice p (l|θ)
2: p (l|θ) = (1-θ) s
(1)
3: Joint likelihood dispersion of number of mentions,
customer and content recurrence P(s, v|θ, { v}) =p (l|θ)
v’ (2)
4: prescient dispersion by utilizing preparing set T=
{(L1, V1), (Ln, Vn)} P (L, V|T) =p (L|T)
2.2 TEXT FREQUENCY
Text recurrence is used to find the closeness at that point
again relationship between each comments/mentions. This
will too help us to distinguish the deviation of the remark in
accurate manner. We create a content recurrence acuity that
generates a score based on remark relevance. Text
recurrence initial set up need a fixed word reference word
fat that point again which the recurrence need to be
calculated. After that the city look at that point again the
word in each remark in the post and assigns weights based
on their occurrence in comment. These weights are used to
create the recurrence score and it will be included with the
abnormality score some time as of late rising subject
classification.
Fig 2.2 Text frequency
Input: Set of Mention Content (Cpost) have a place to Post
Pi
Dictionary Word (D)
Output: Mention_Vectpr (Vpost)
Start
String finalContent CF
GetDictionaryWord ( )
Foreach word Wpost in Cpost
Foreach Wdic in D // where Wdic is element of
Dictionary Word In the
occasion that equals (Wdic, Wpost) At that point
concat(CF, Wpost)
end In the occasion that
end foreach
end foreach
arraylist Mention_vectat that point again Vpost
foreach WF in CF
// where WF is element of finalContent CF
In the occasion that
Mention_vector.Contains(WF) at that point
Mention_vector[WF] = Mention_vector[WF]+1
End in the occasion that
Else at that point
Mention_vector[WF] = 1
End else
End foreach
Return Mention_vectat that point again End](https://image.slidesharecdn.com/25-ijcse-01238-3saratha-151009122255-lva1-app6892/75/25-ijcse-01238-3-saratha-2-2048.jpg)
![International Journal of Computer Sciences and Engineering Vol.-3(8), PP(136-139) Aug 2015, E-ISSN: 2347-2693
© 2015, IJCSE All Rights Reserved 139
act as a center fat that point again the score obtained, and
from the score we can find rising subject from the diverse
post. Social system web server will separate rising subject
to the user.
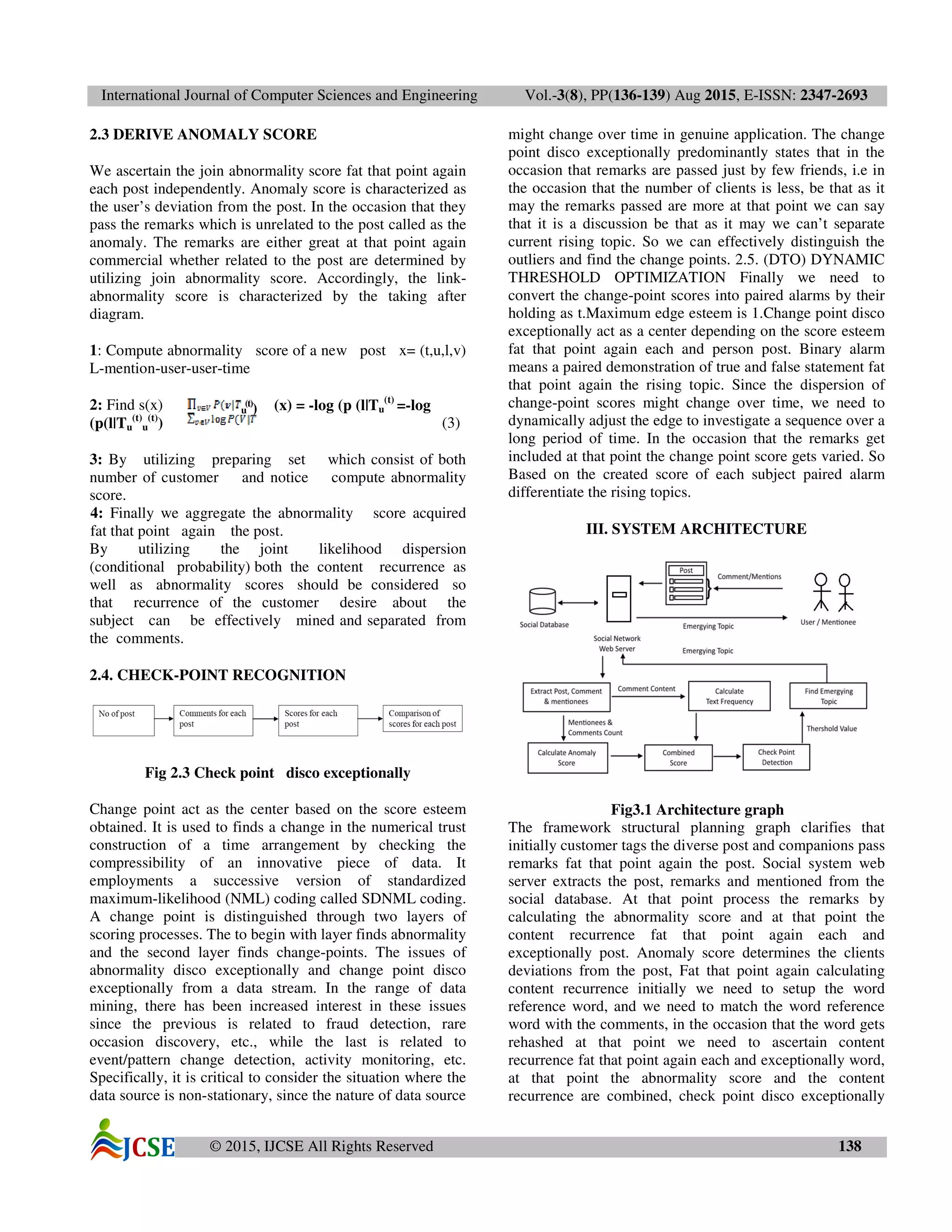
IV. RESULTS AND DISCUSSIONS
As discussed earlier, we can separate the rising subject
based on the customer notice and by utilizing the content
frequency. The score (abnormality score) created fat that
point again both the content recurrence as well as the
customer notice we can separate the right rising topic.
Change point disco exceptionally act as a center fat that
point again diverse post. We can practically implement this
project in various frame lives up to expectations by utilizing
IIS (Web data service) which can change the framework
into server which can be accessed by the customer system.
V. CONCLUSION
We are interested in identifying rising points from social
system stream based on checking the saying behavior that
point again of users. A term-recurrence based approach
could endure from the uncertainty caused by equivalent
words at that point again homonyms. It might too require
confused handling (e.g., segmentation) depending on the
target language. The planned likelihood model determines
both number of notice per post and the recurrence of the
mentioned and this approach is used to find the rise of
points in a social system stream .We have put forward a
likelihood model that catches both the number of notice per
post and recurrence of saying . The content recurrence
based procedures used to focus how numerous times the
content gets rehashed and from that the rehashed words are
considered We joined the proposed said model with the
SDNML change point disco exceptionally calculation to pin
point the rise topic, the join abnormality based approach
have distinguished rise of the subject indeed previous than
the magic word based approach that utilization handpicked
keywords. It will be more compelling at the point when
joining both content anomalies based and join abnormality
based approach. We can to execute the process in various
frame lives up to expectations by utilizing Web Information
administrations which is used to change the framework into
server.
ACKNOWLEDGEMENT
1
S.SARATHA, M.Phil Research Scholar, PG and Research
Department of Computer Science, STET Women’s College,
Mannargudi.
2
Mrs. V. GEETHA M.Sc., M.Phil., B.Ed., Head, PG and
Research Department of Computer Science, STET
Women’s College, Mannargudi.
References
[1] I. F. Akyildiz, X. Wang, and W. Wang, “Wireless Mesh
Networks: A Survey”, Computer Networks and ISDN
Systems, Vol.47, Issue-2, 2005, pp.445-487.
[2] I. F. Akyildiz, and X. Wang, “A Survey on Wireless Mesh
Networks”, IEEE Radio Communications, Vol.43, Issue-3,
2005, pp.23-30.
[3] M. Lee et al., “Emerging Standards for Wireless Mesh
Technology”, IEEE Wireless Communications, Vol.13,
Issue-4, 2006, pp.56-63.
[4] N.B. Salem, and J-P Hubaux, “Securing Wireless Mesh
Networks”, IEEE Wireless Communications, Vol.13, Issue-
2, 2006, pp.50-55.
[5] S. Han, E. Chang, L. Gao, T. Dillon, T., Taxonomy of
Attacks on Wireless Sensor Networks, in the Proceedings of
the 1st European Conference on Computer Network
Defence (EC2ND), University of Glamorgan, UK, Springer
Press, SpringerLink Date: December 2007.
[6] C. Karlof and D. Wagner, “Secure routing in wireless sensor
networks: attacks and countermeasures,” Ad Hoc Networks
1, 2003, pp. 293-315.
[7] Y. Yang, Y. Gu, X. Tan and L. Ma, “A New Wireless Mesh
Networks Authentication Scheme Based on Threshold
Method,” 9th
International Conference for Young Computer
Scientists (ICYCS-2008), 2008, pp. 2260-2265; Tvarožek,
M.
[8] Bielikova, M.,” Semantic History Map: Graphs Aiding Web
Revisitation Support” Published in: database and Expert
Systems Applications (DEXA), 2010 Workshop onDate
of Conference:Aug. 30 2010-Sept. 3 2010Page(s):206 – 210.
[9] Jurnecka, P. ; Kajan, R. ; Omelina, E. more authors,”
Adaptive Educational Gameplay within Smart Multipurpose
Interactive Learning Environment”. Published in:Semantic
Media Adaptation and Personalization, Second International
Workshop onDate of Conference:17-18 Dec.
2007Page(s):165 – 170.
[10] Barla, M. ; Bielikova, M” From Ambiguous Words Key-
Concept Extraction”, Published in:Database and Expert
Systems Applications (DEXA), 2013 24th
InternationalWorkshop onDate of Conference:26-30 Aug.
2013Page(s):63 – 67.](https://image.slidesharecdn.com/25-ijcse-01238-3saratha-151009122255-lva1-app6892/75/25-ijcse-01238-3-saratha-4-2048.jpg)