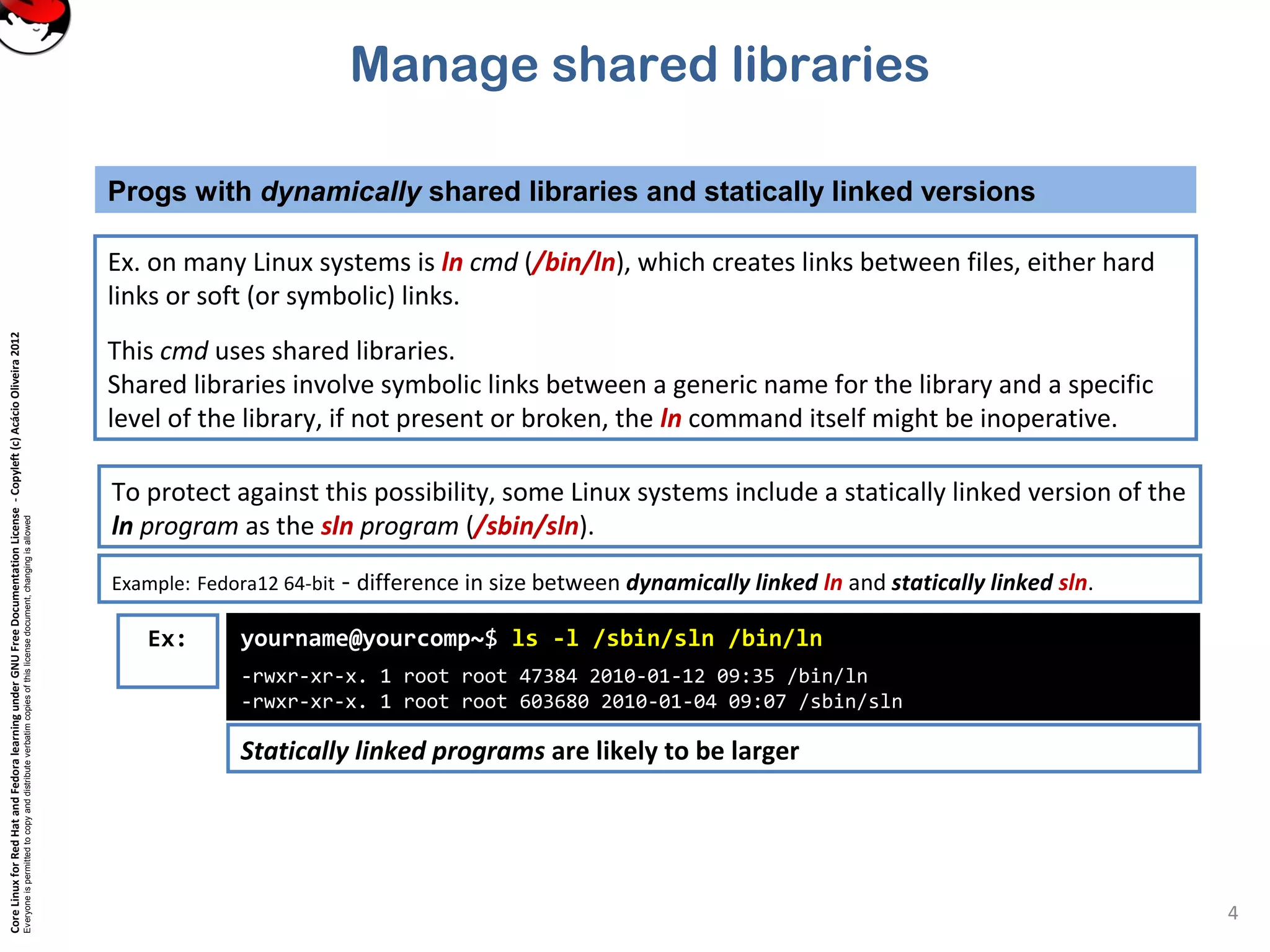
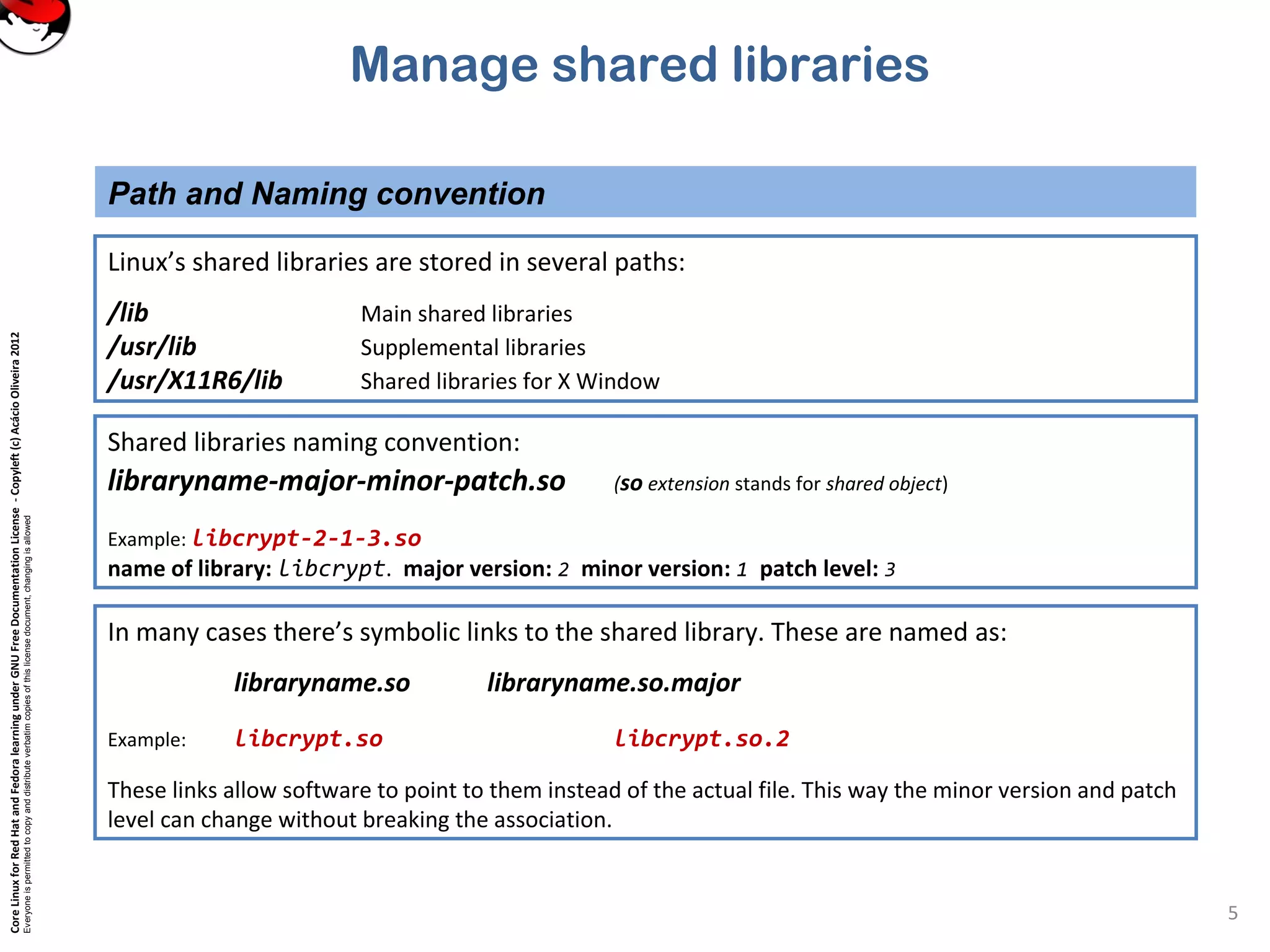
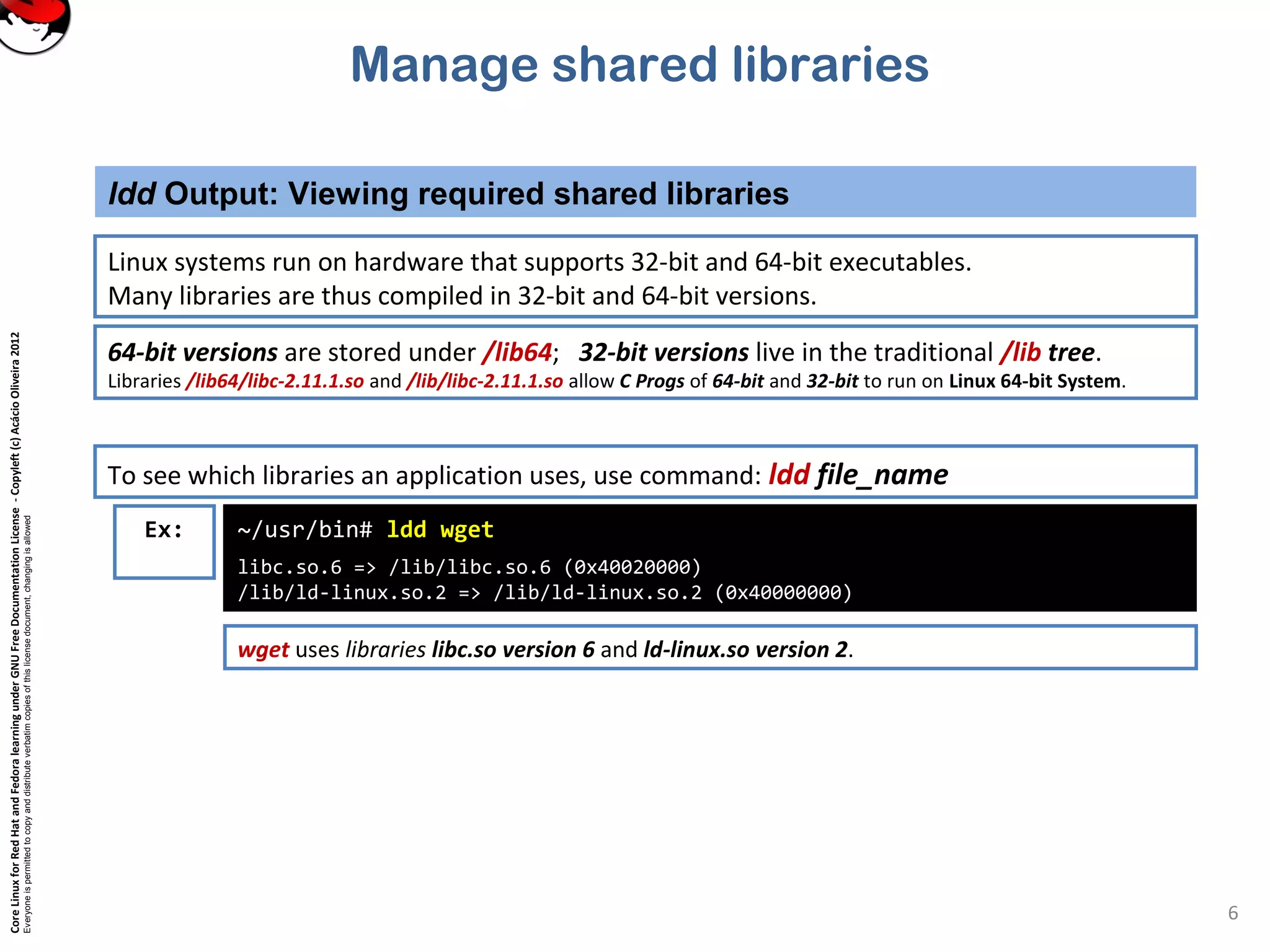
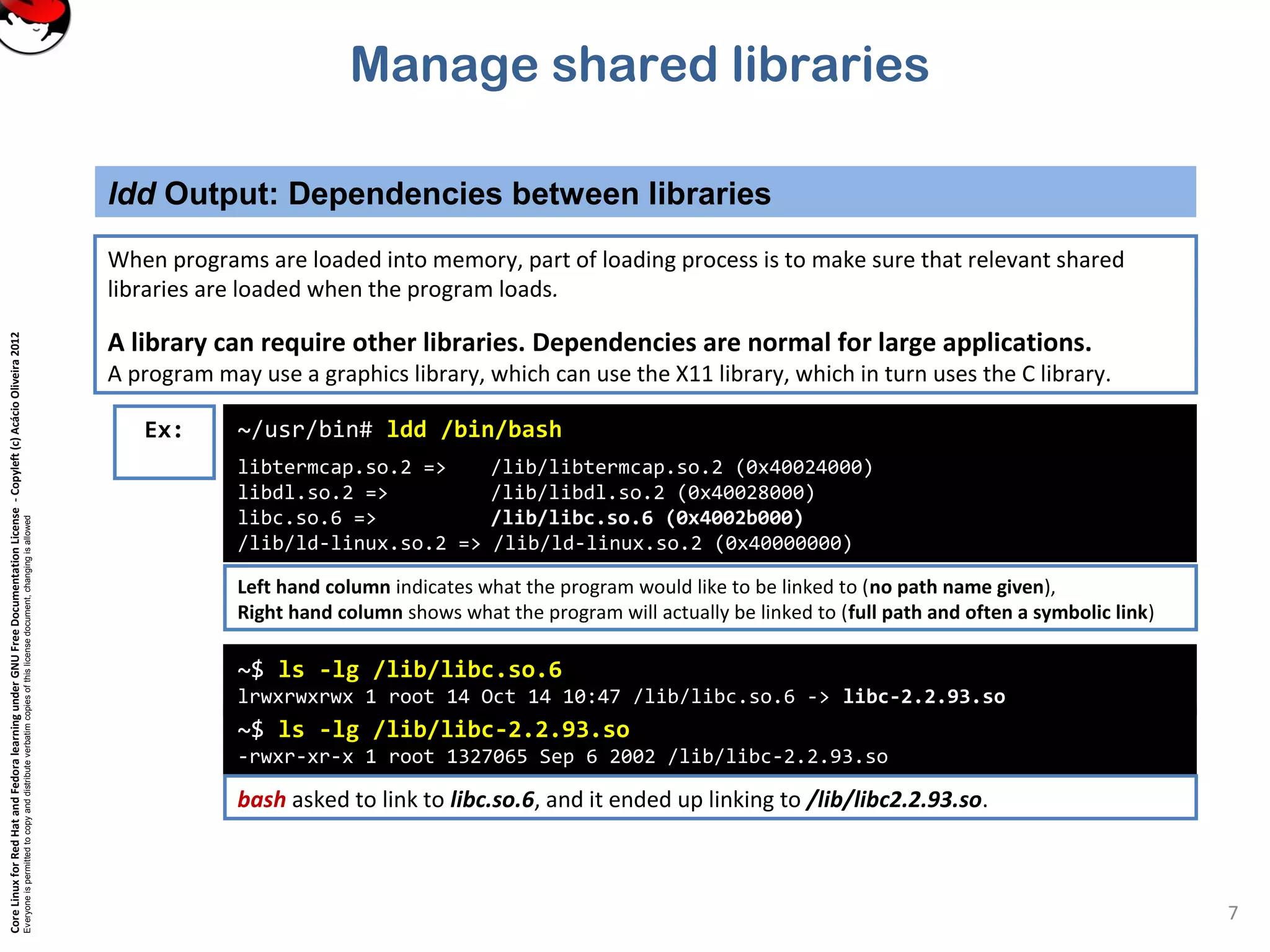
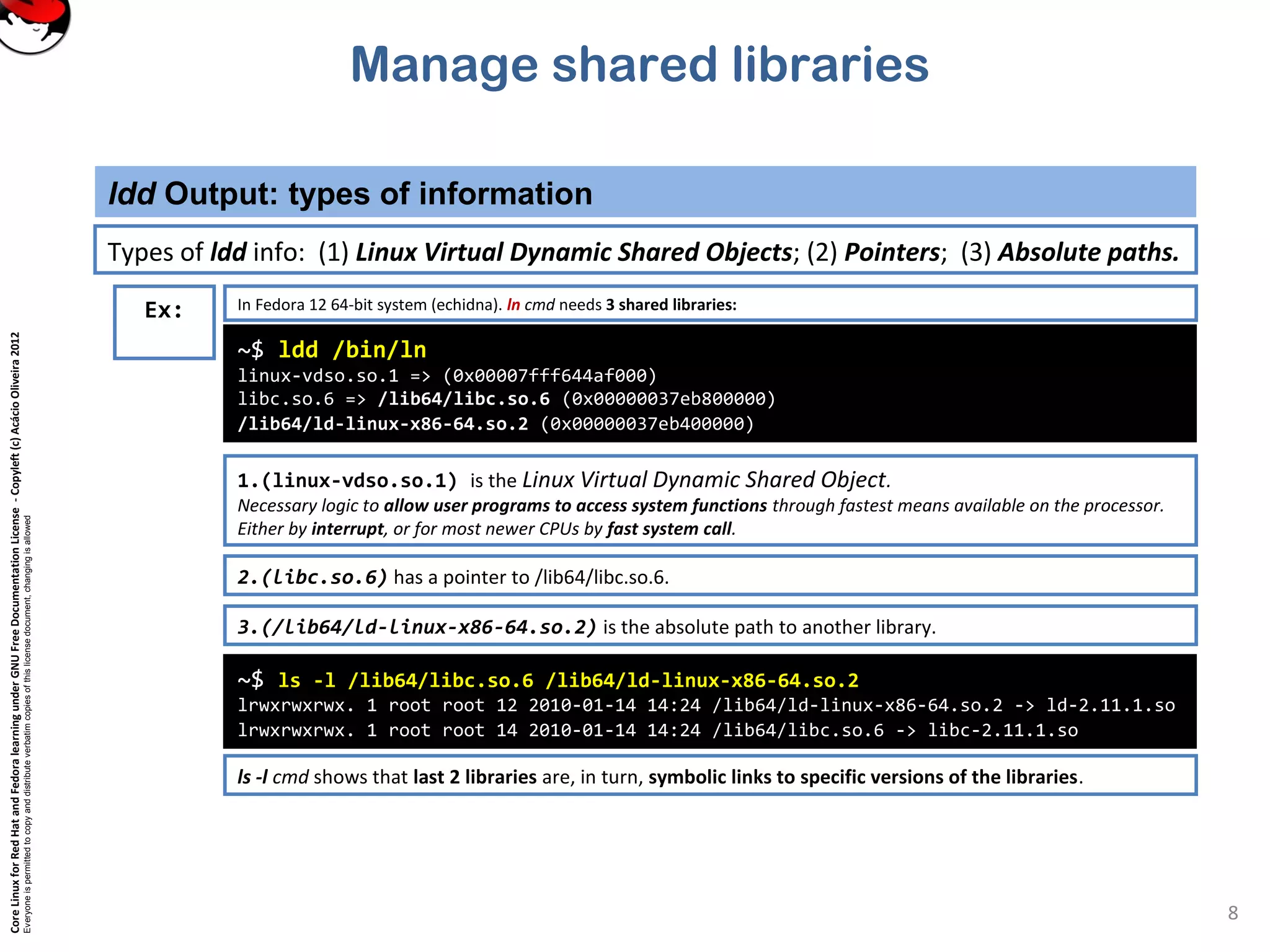
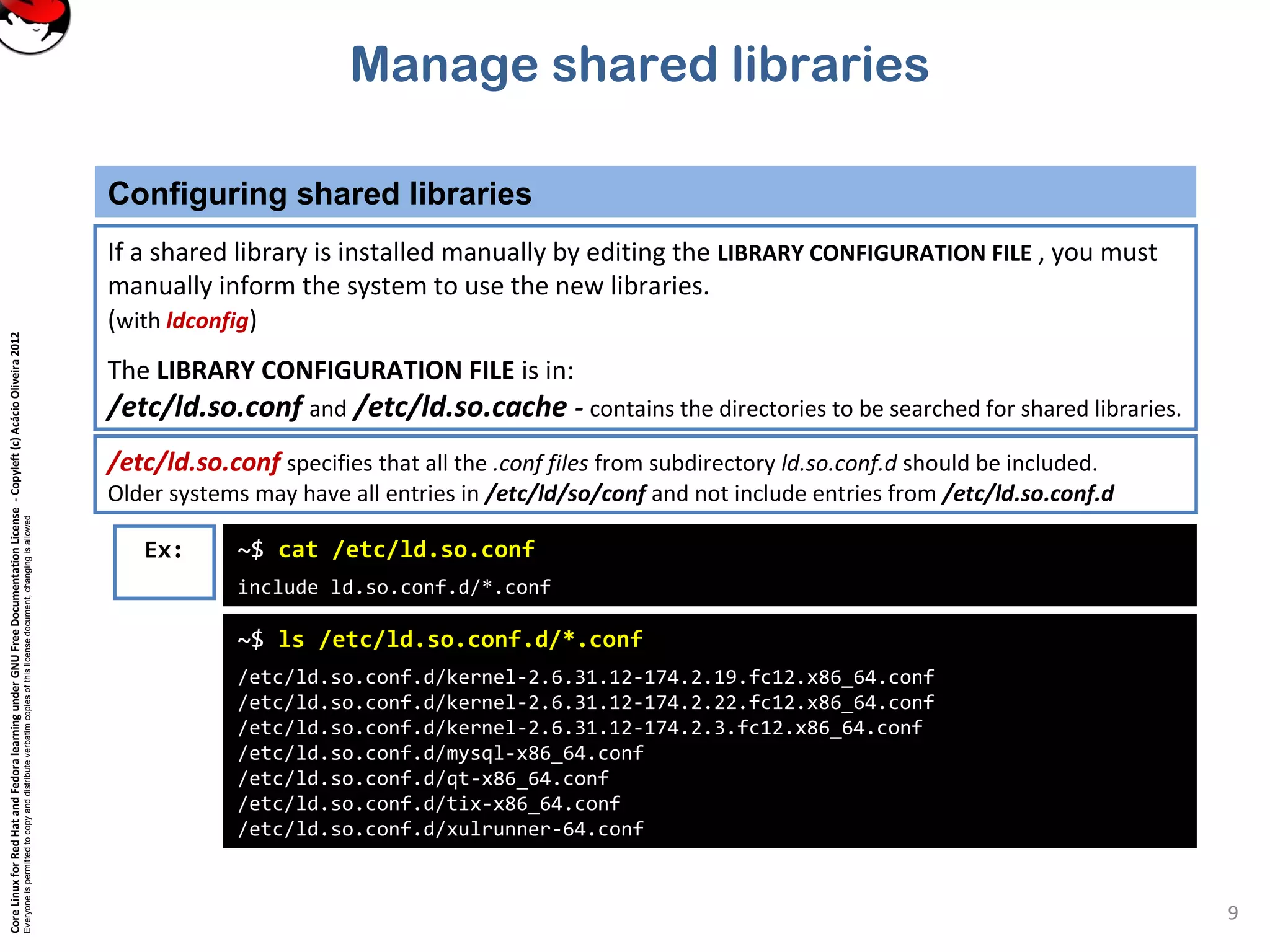
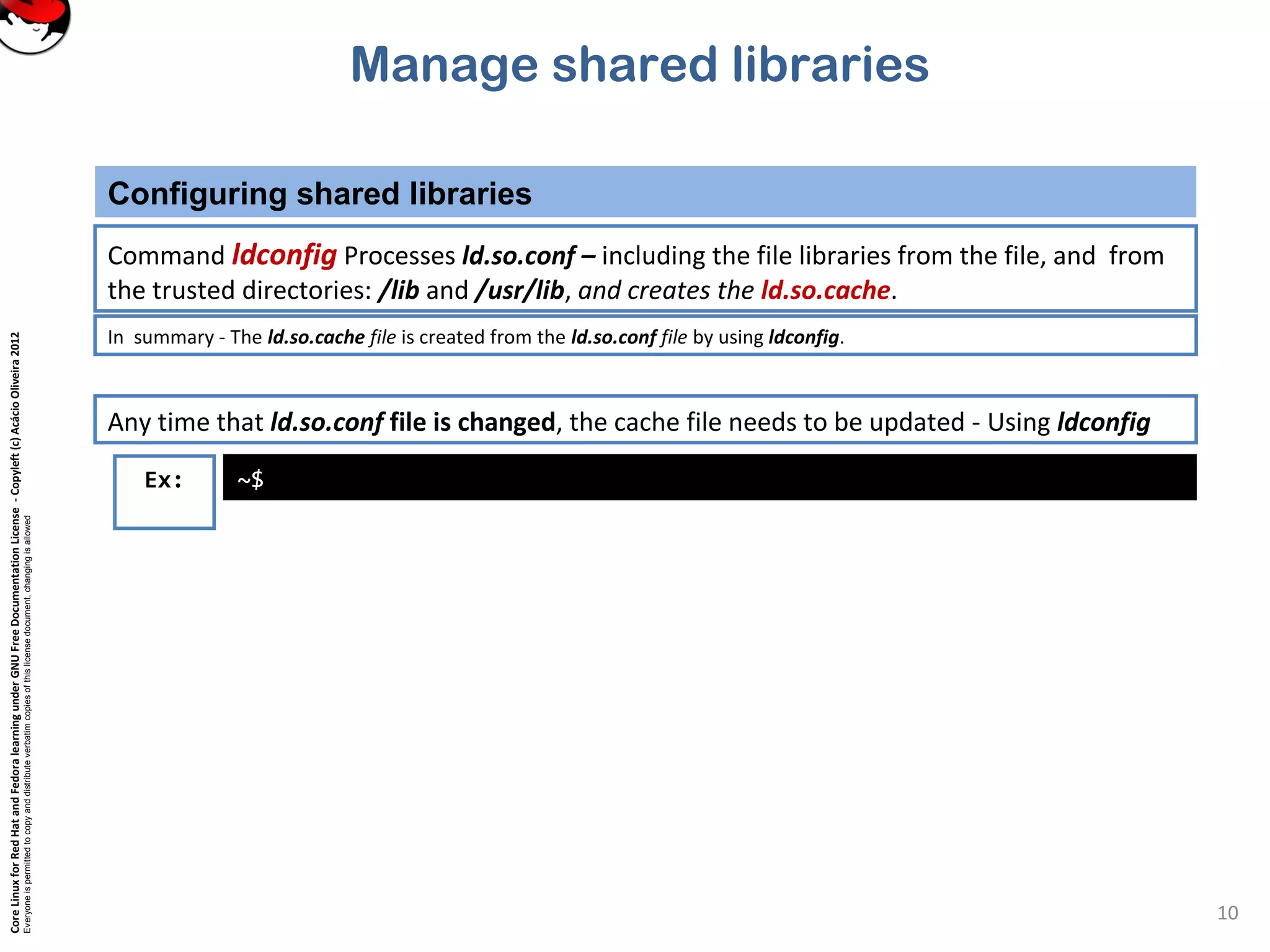
This document discusses managing shared libraries in Linux systems. It defines shared libraries as common code stored in files that are accessed by multiple programs. It describes how shared libraries are located, configured, and loaded, and some key tools used in managing them like ldd, ldconfig, and LD_LIBRARY_PATH. Specific topics covered include library file paths, naming conventions, dependencies between libraries, and ensuring applications can find non-standard library locations.