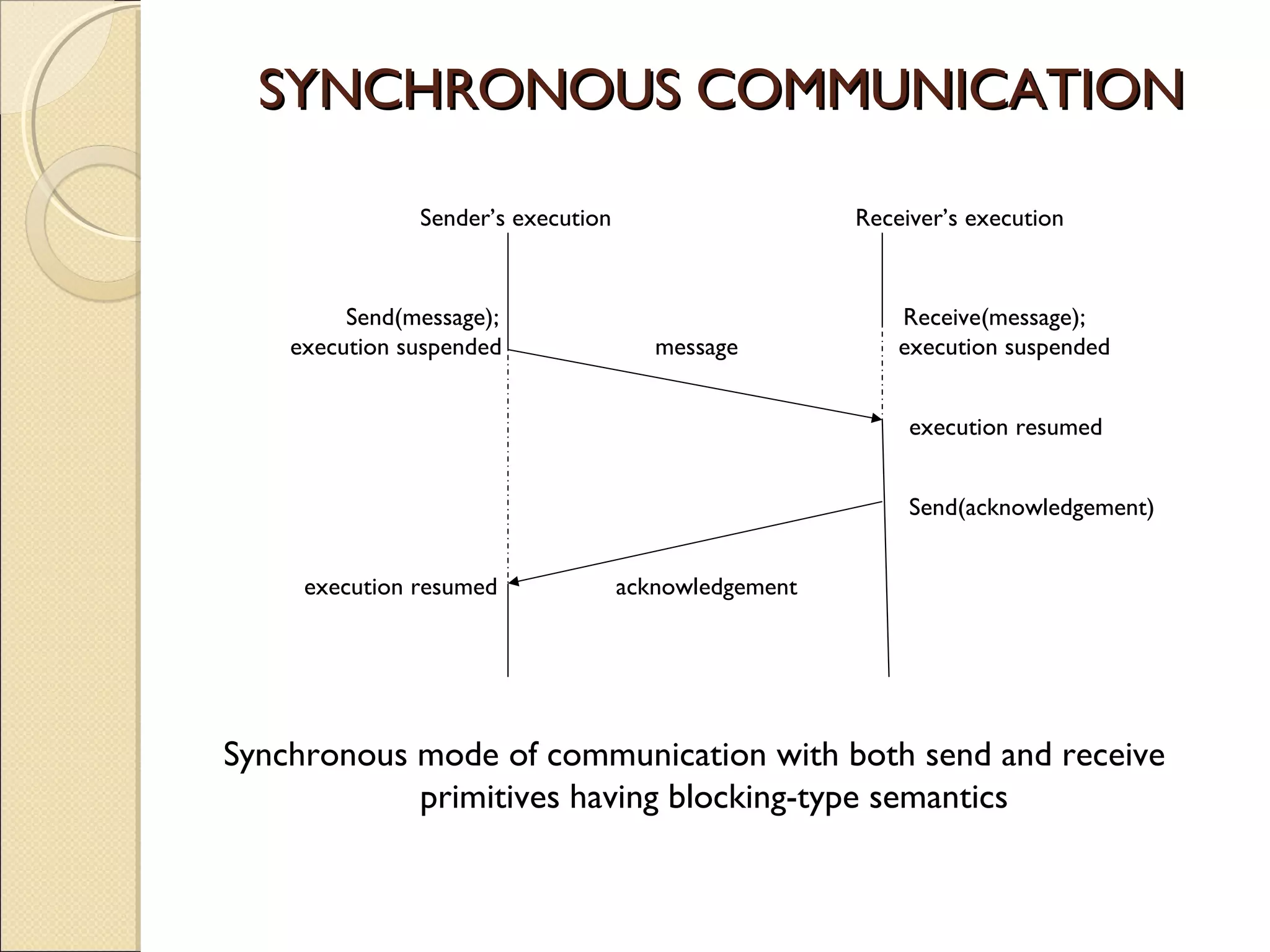
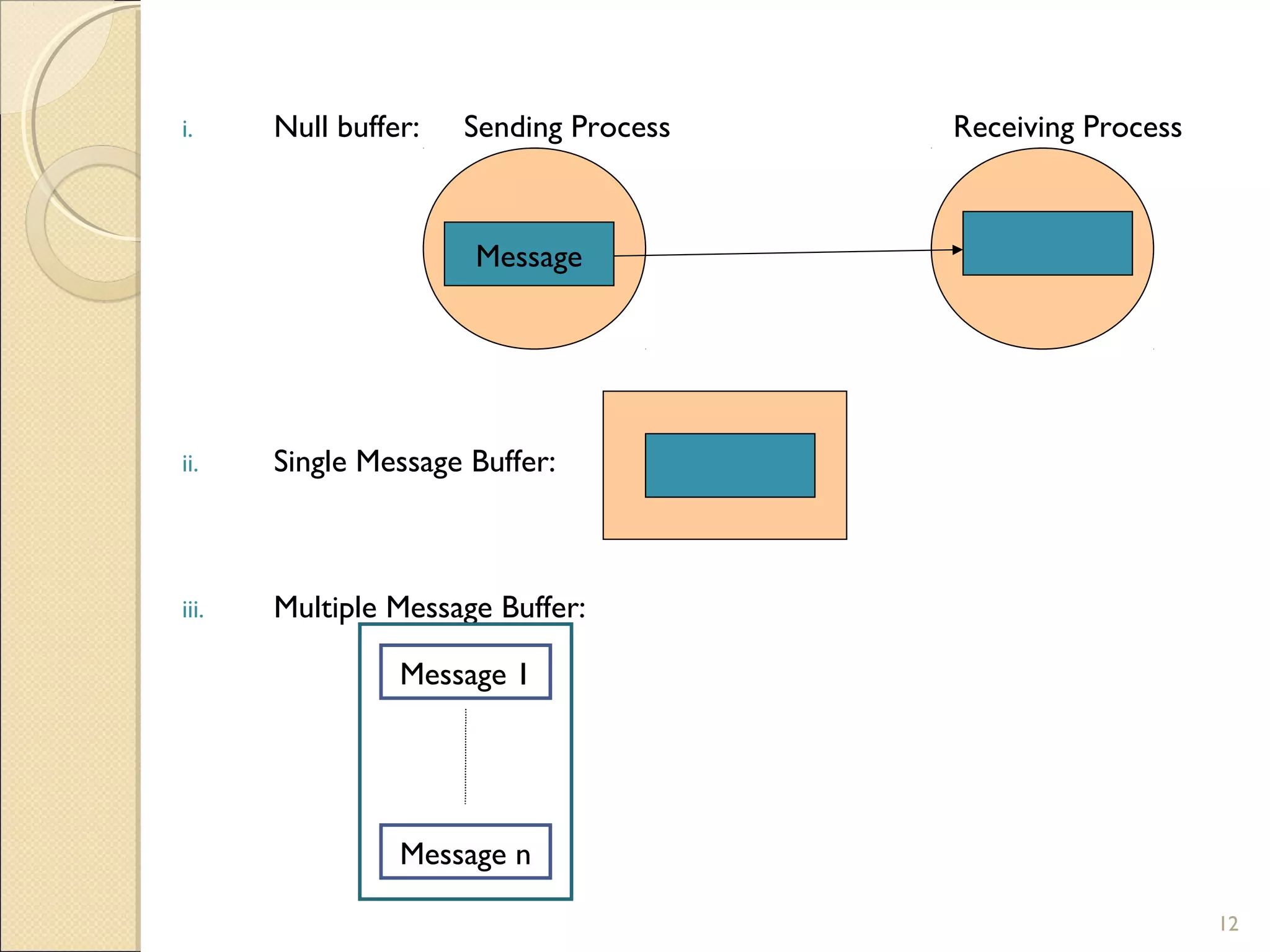
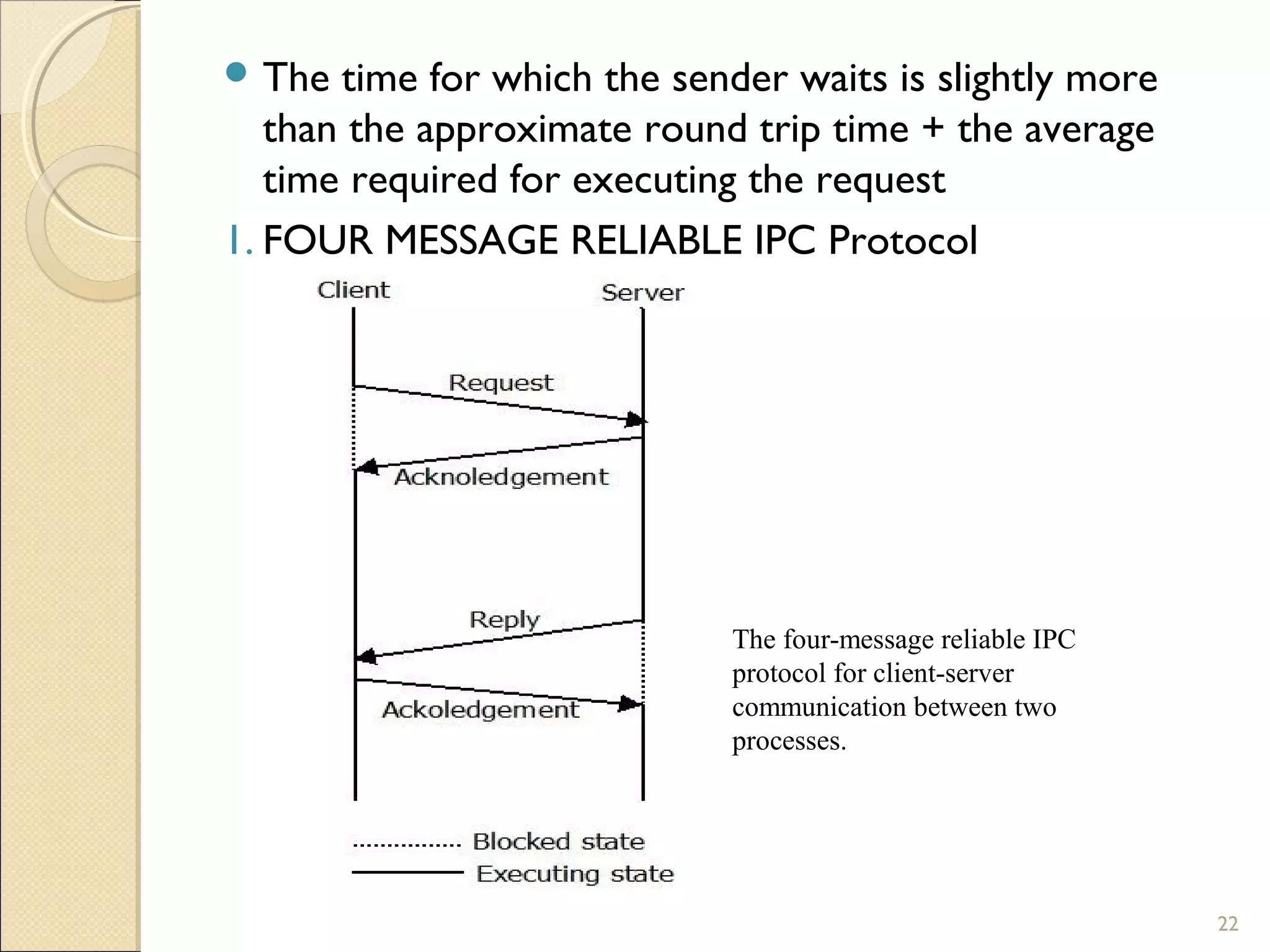
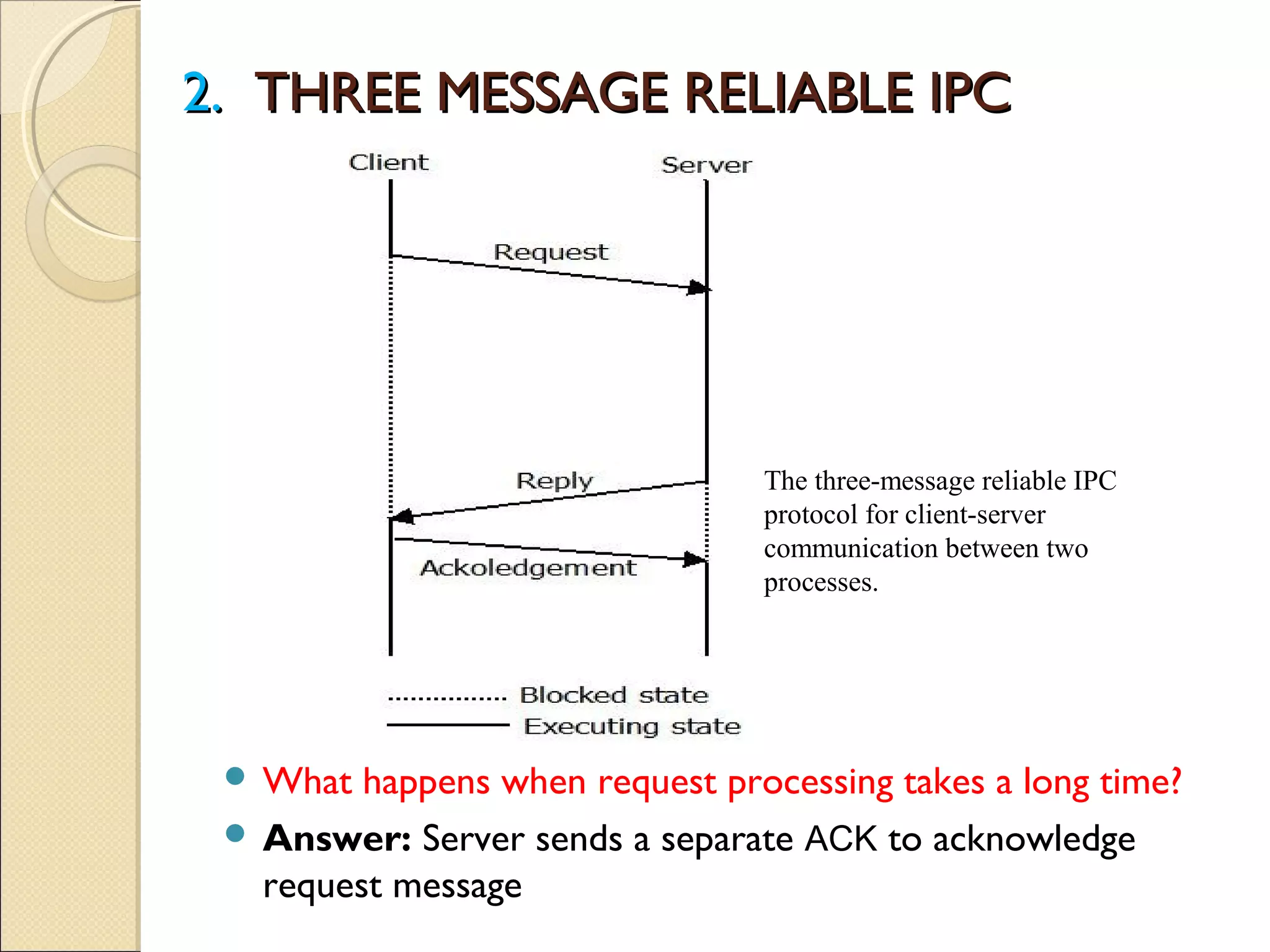
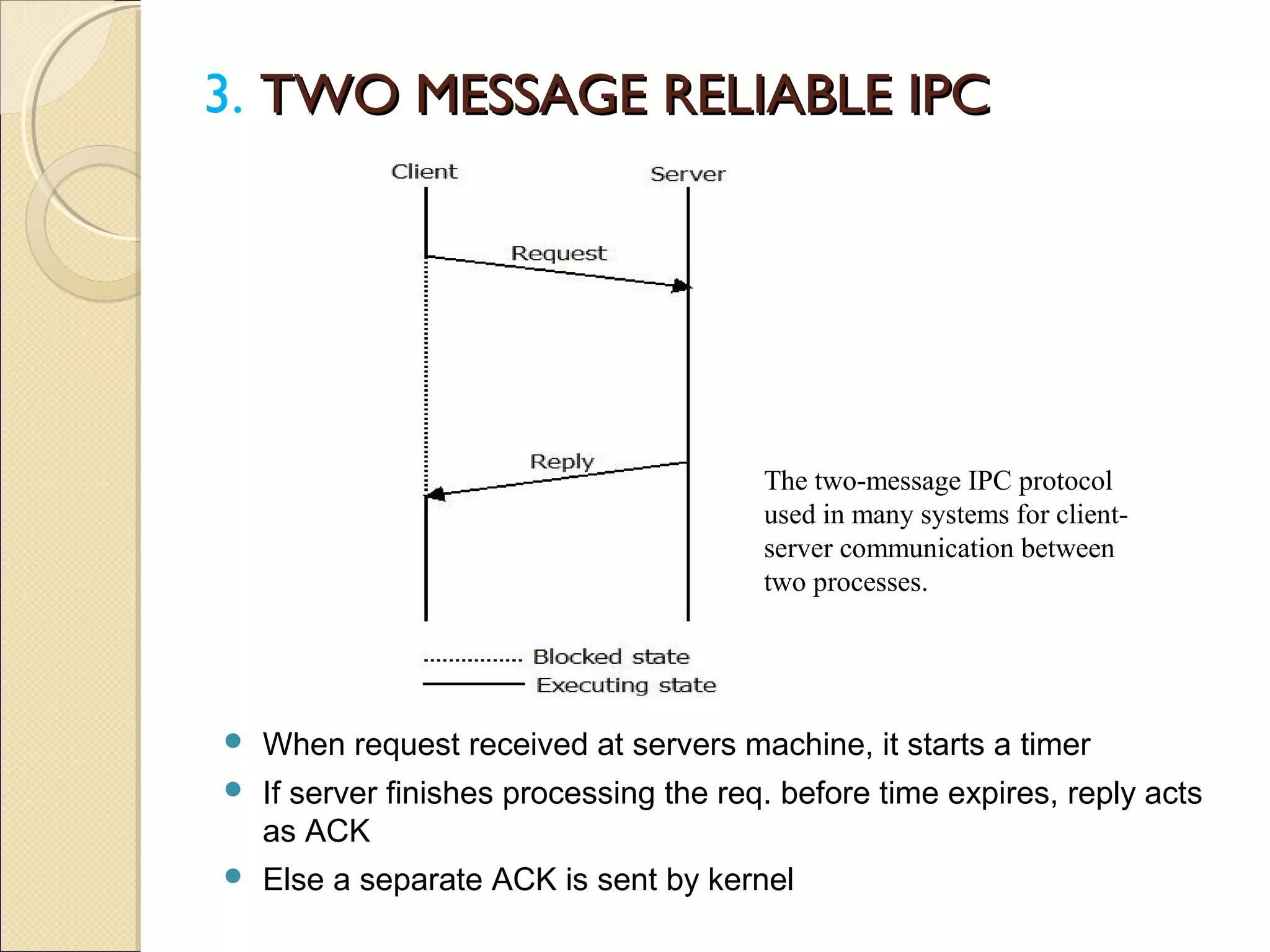
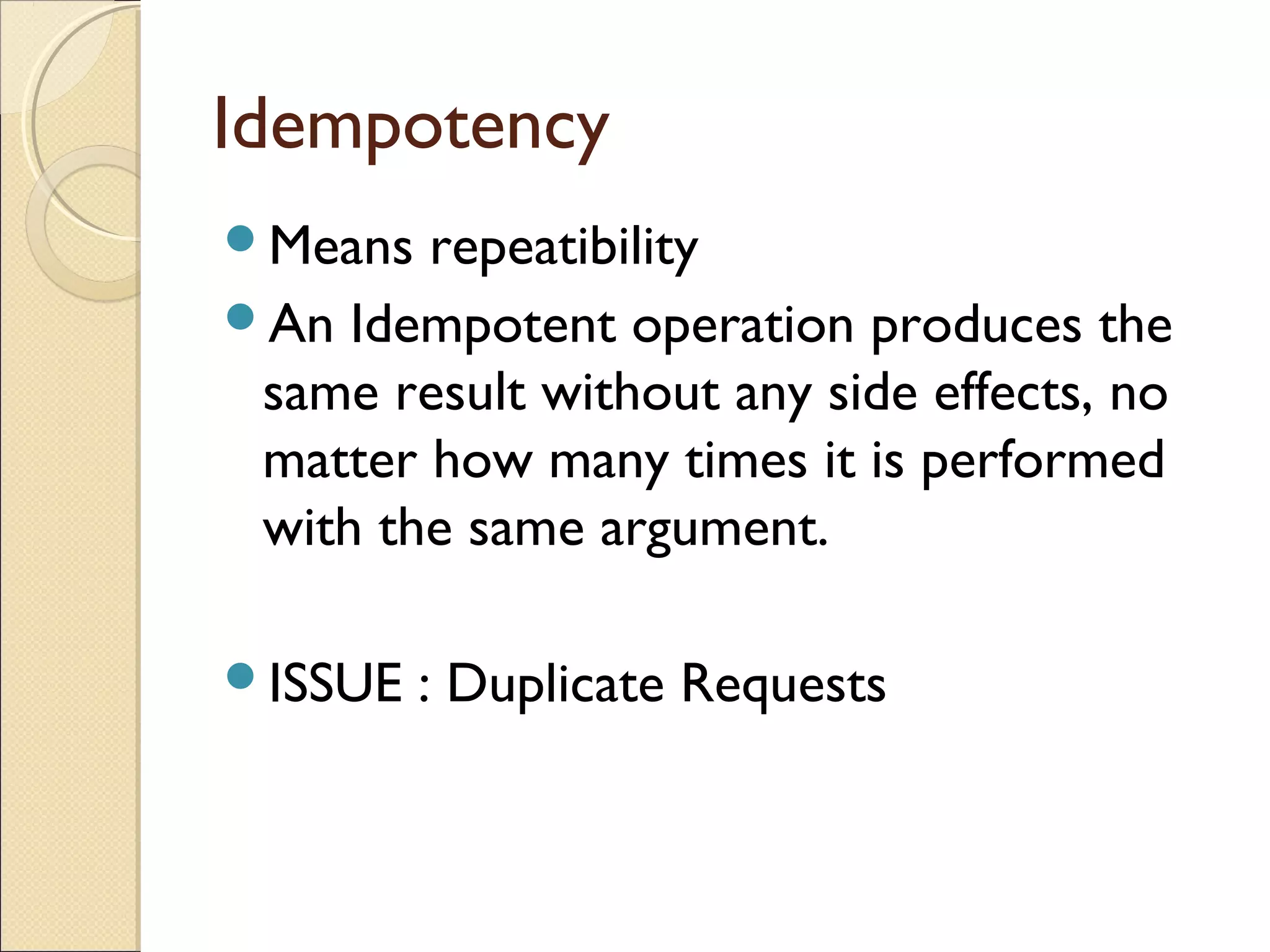
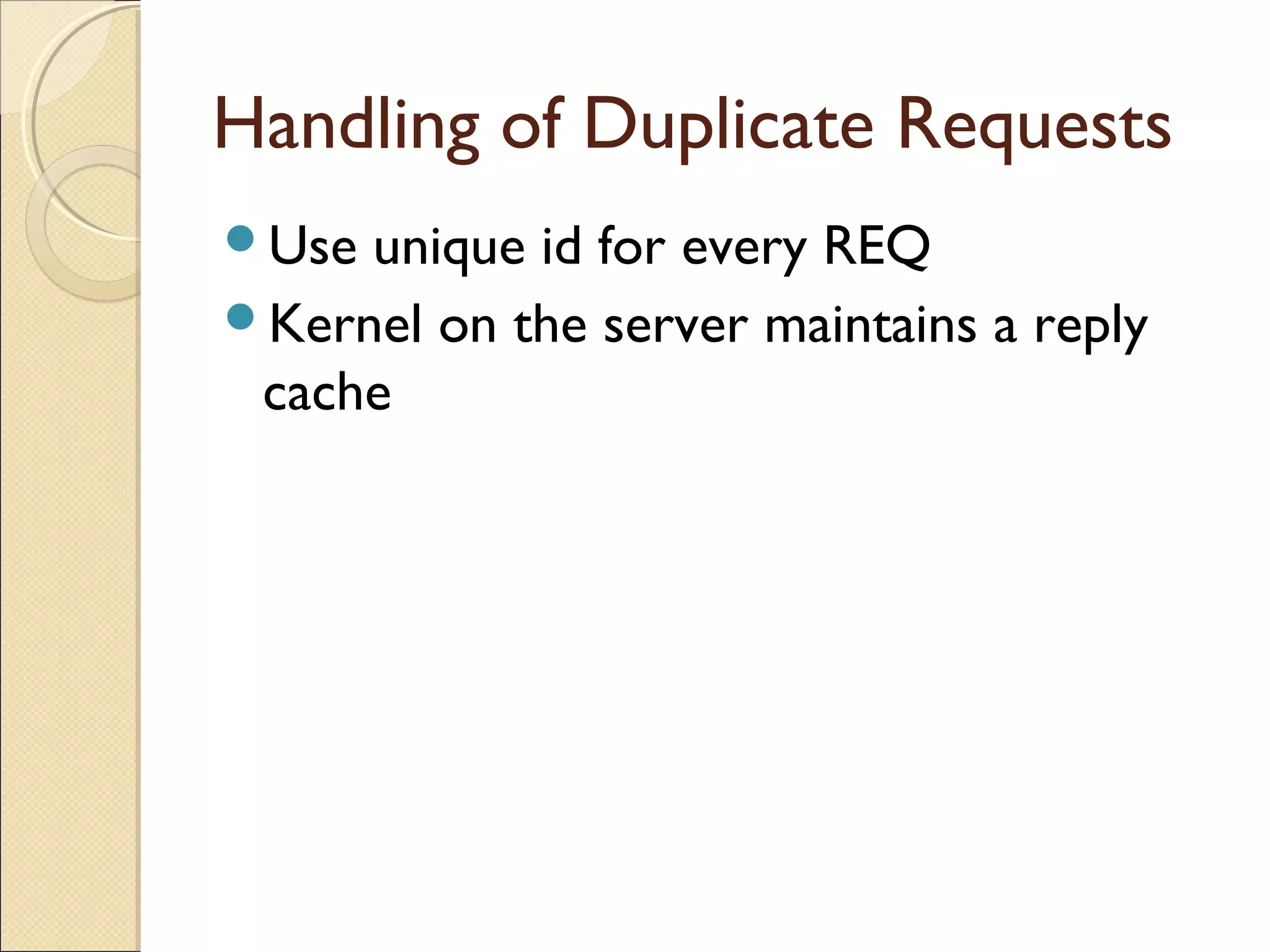
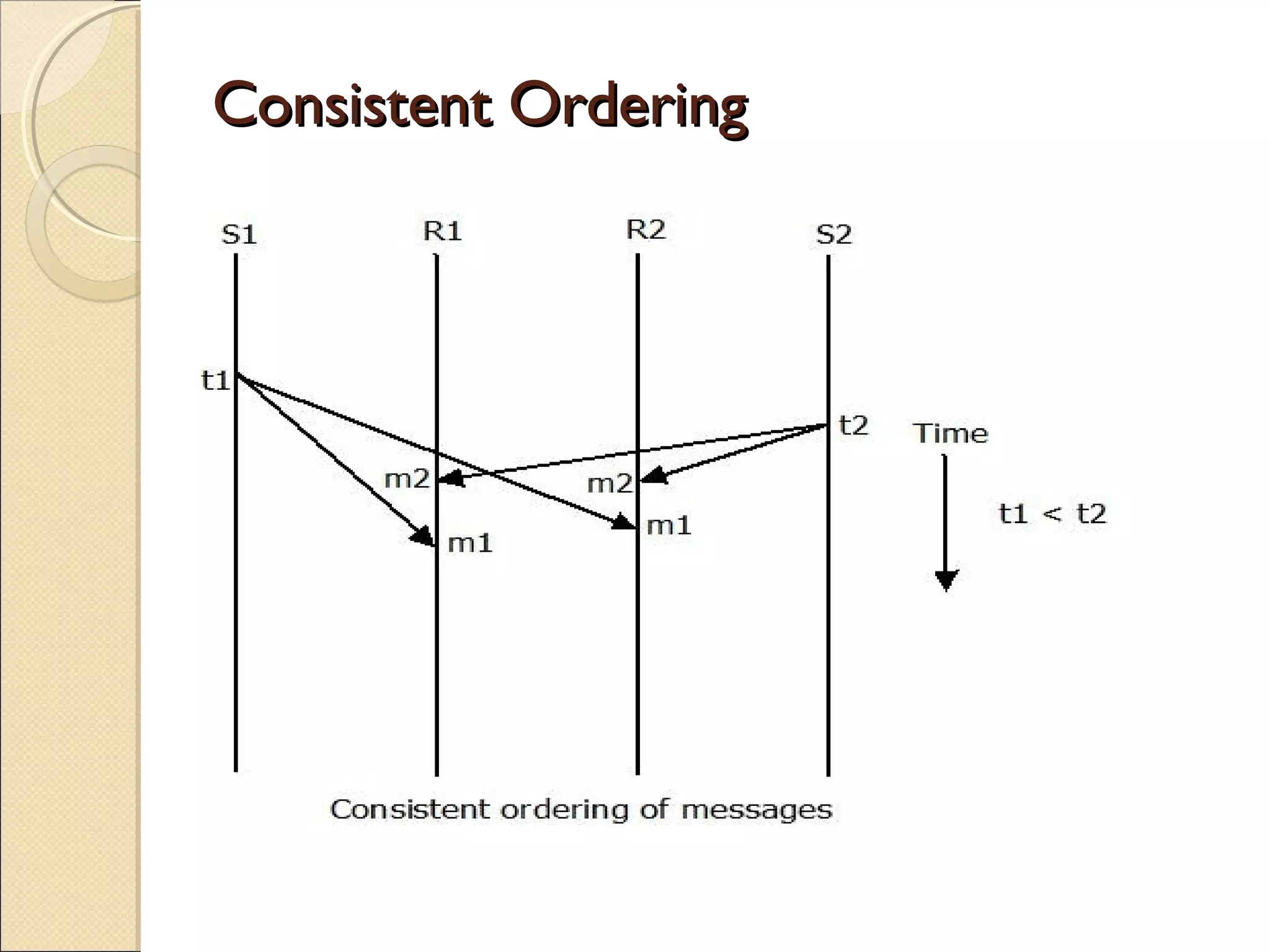
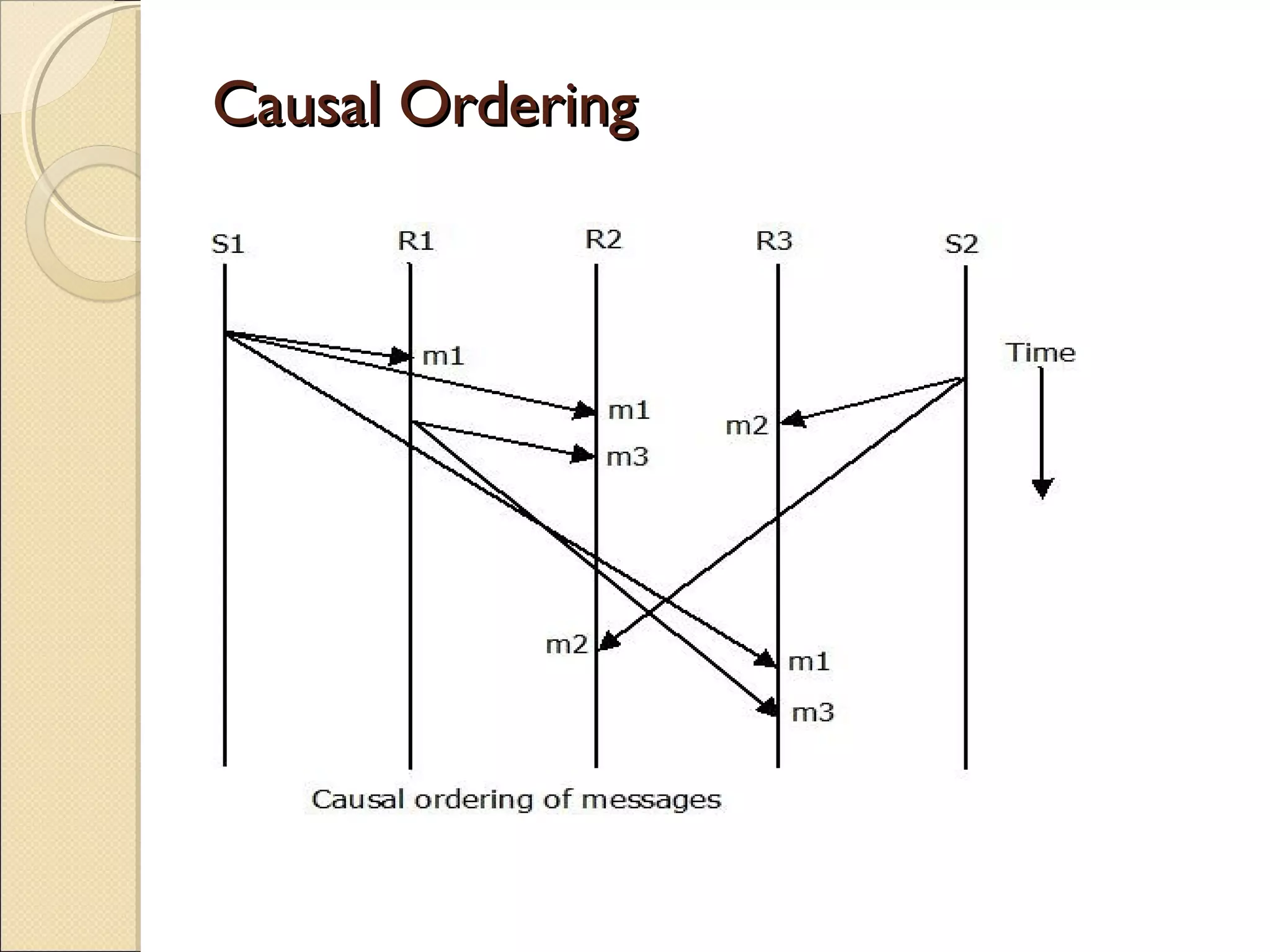
Message passing between processes can use either synchronous or asynchronous communication. With synchronous communication, sending and receiving blocks until the operation completes, while asynchronous does not block. There are issues to consider with blocking sends and receives, such as processes crashing or messages getting lost. Non-blocking receives use polling or interrupts to check for incoming messages. Reliable message passing protocols use acknowledgments and retransmissions to ensure reliable delivery.