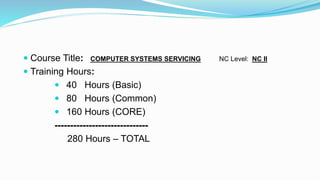
This document outlines four Certificate of Competency (COC) qualifications for computer systems servicing: installing and configuring computer systems, setting up computer networks, setting up computer servers, and maintaining and repairing computer systems and networks. It also describes occupational health and safety procedures, personal protective equipment, electrostatic discharge, 5S methodology, and dos and don'ts for working on computer systems. The total training hours required are 280 hours.