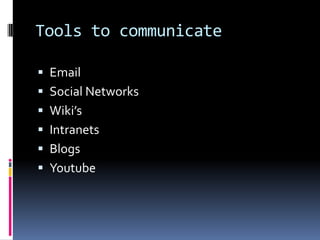
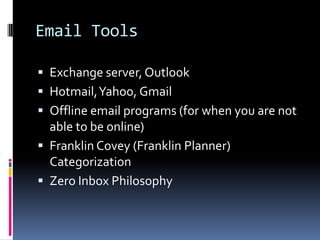
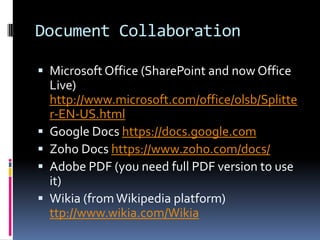
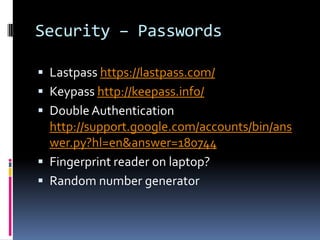
The document discusses challenges in modern office communication and data management, particularly focusing on information overload and the consumerization of IT resources. It explores various tools for communication, document collaboration, content management, and security, emphasizing the importance of an effective information strategy. Additionally, it introduces the 'zero inbox' philosophy for managing email more efficiently and offers recommendations for software and working trends in the digital age.