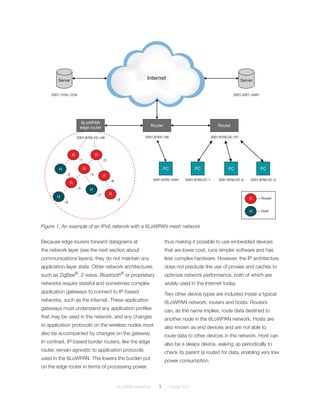
6LoWPAN is a networking standard that allows IPv6 packets to be transmitted efficiently over low-power wireless networks like IEEE 802.15.4. It defines an adaptation layer that compresses IPv6 and UDP headers to address challenges of limited bandwidth and device resources. 6LoWPAN networks connect to the internet using edge routers and support applications through protocols like CoAP that are optimized for low-power devices.