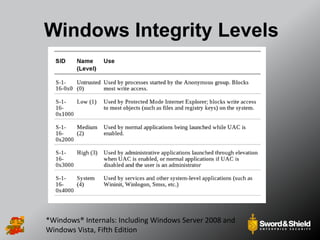
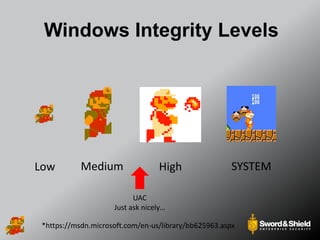
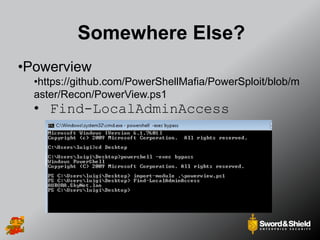
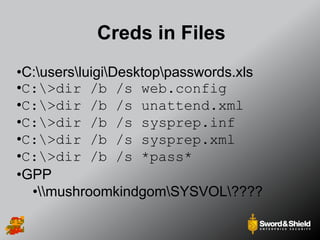
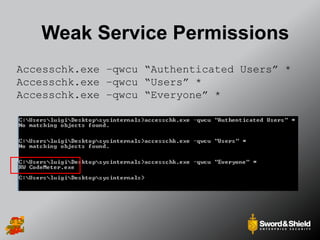
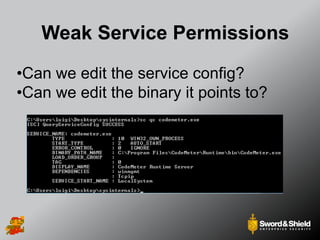
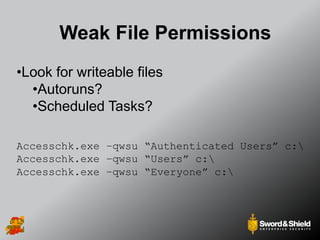
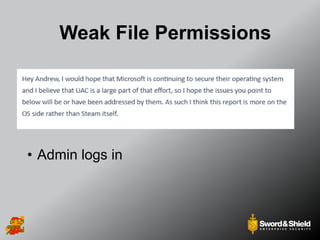
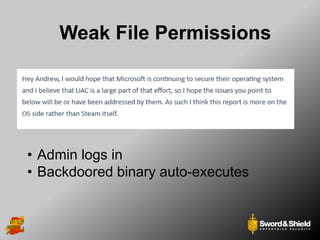
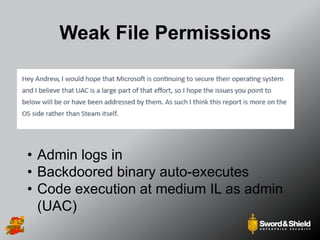
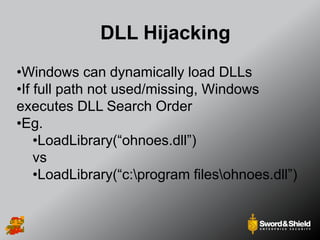
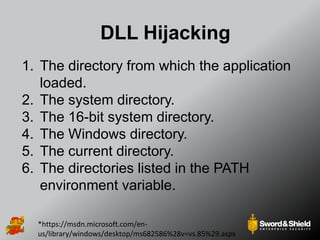
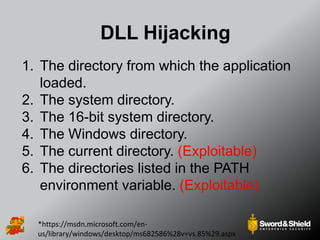
This document provides an overview of practical Windows privilege escalation techniques. It begins with introductions and disclaimers, then discusses Windows access control models and concepts like integrity levels. It proceeds to demonstrate potential escalation avenues like exploiting privileged access elsewhere on the network, extracting credentials from files, exploiting unpatched vulnerabilities, weak permissions on services/files, AlwaysInstallElevated policies, and DLL hijacking. The document emphasizes that privilege escalation is still possible even with UAC and provides tools and references for further information.