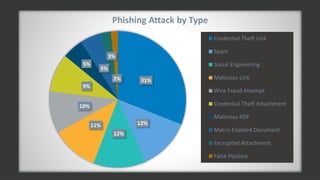
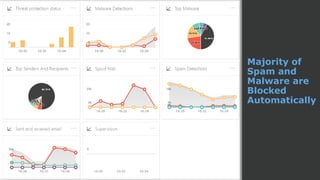
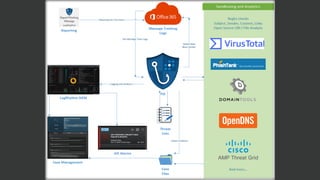
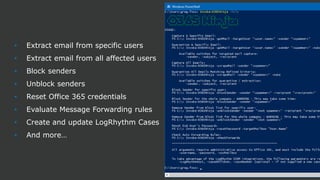
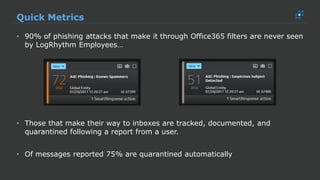
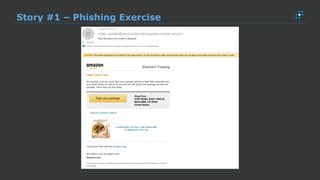
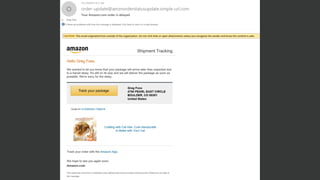
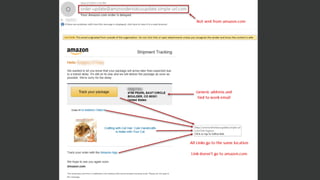
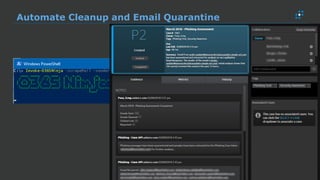
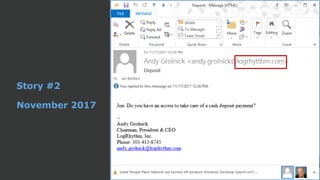
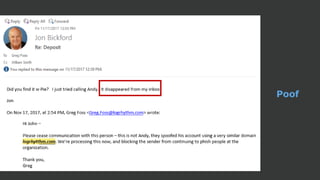
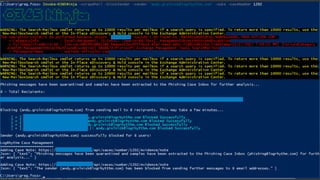
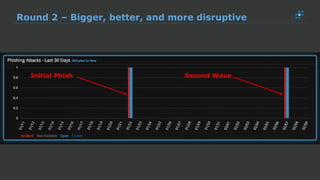
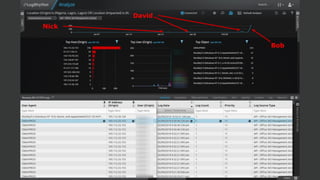
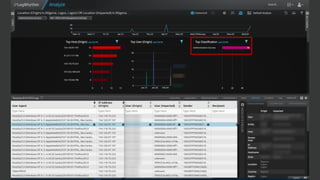
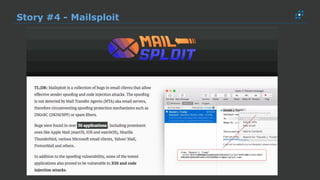
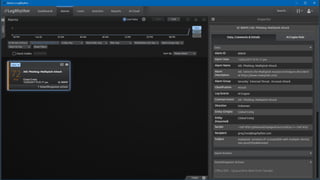
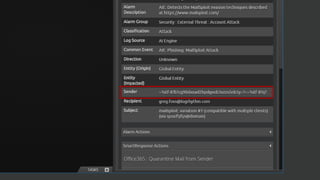
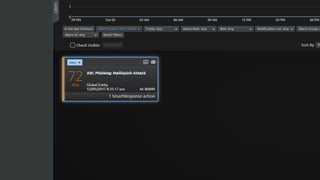
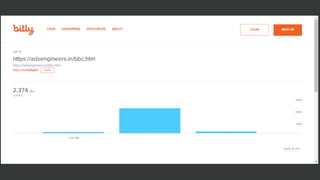
The document discusses the growing threat of phishing attacks, emphasizing that the majority go undetected despite filtering measures. It shares several case studies illustrating how such attacks have successfully penetrated defenses, suggesting the need for enhanced security protocols like MFA. Future plans for developing security tools include integrations with Office 365 and improved case management functionalities.
















![Thank You!
Questions?
Greg . Foss [at] logrhythm . com
@heinzarelli
https://github.com/LogRhythm-Labs/PIE/](https://image.slidesharecdn.com/piebsides-vancouver2018-180314182455/85/PIE-BSides-Vancouver-2018-61-320.jpg)