How dose a wheat flour milling machine work?
•
2 likes•175 views
A wheat flour milling machine works by using roller mills, rollers made of special alloys, plansifters for sifting, dampeners, bucket elevators and conveyors to process wheat into flour. Key components include roller mills, plansifters made of high-strength steel and wood, stainless steel pipes and dampeners, with electronic parts and motors from Siemens. The machine can produce customized, fortified flour in a semi-automatic packaging process.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
Similar to How dose a wheat flour milling machine work?
Similar to How dose a wheat flour milling machine work? (10)
Recently uploaded
Recently uploaded (20)
Event-Driven Architecture Masterclass: Challenges in Stream Processing

Event-Driven Architecture Masterclass: Challenges in Stream Processing
ChatGPT and Beyond - Elevating DevOps Productivity

ChatGPT and Beyond - Elevating DevOps Productivity
How to Check CNIC Information Online with Pakdata cf

How to Check CNIC Information Online with Pakdata cf
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
How to Check GPS Location with a Live Tracker in Pakistan

How to Check GPS Location with a Live Tracker in Pakistan
“Iamnobody89757” Understanding the Mysterious of Digital Identity.pdf

“Iamnobody89757” Understanding the Mysterious of Digital Identity.pdf
Microsoft CSP Briefing Pre-Engagement - Questionnaire

Microsoft CSP Briefing Pre-Engagement - Questionnaire
Observability Concepts EVERY Developer Should Know (DevOpsDays Seattle)

Observability Concepts EVERY Developer Should Know (DevOpsDays Seattle)
The Ultimate Prompt Engineering Guide for Generative AI: Get the Most Out of ...

The Ultimate Prompt Engineering Guide for Generative AI: Get the Most Out of ...
Intro to Passkeys and the State of Passwordless.pptx

Intro to Passkeys and the State of Passwordless.pptx
Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots

Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
How dose a wheat flour milling machine work?
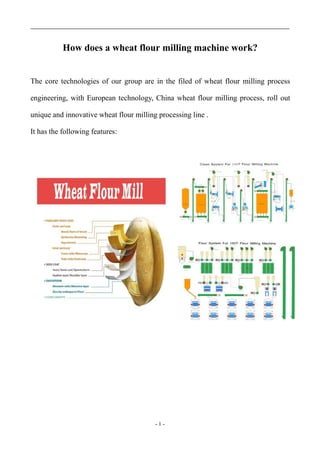
- 1. - 1 - How does a wheat flour milling machine work? The core technologies of our group are in the filed of wheat flour milling process engineering, with European technology, China wheat flour milling process, roll out unique and innovative wheat flour milling processing line . It has the following features:
- 2. - 2 - 1.Roller Mills 1)The partitioned paneling and swing-out feed module guarantee ideal access to the feeding and grinding rolls. This makes residue-free cleaning possible. 2) a pulse generator automatically adjust the feed material at the entrance door 3) bearing SKF 4) temperature monitor (option)
- 3. - 3 - 2.Roller: Two different alloys with a mixing ratio allow the perfect balance to be achieved between hardness and roughness.
- 4. - 4 - 3.Plansifter 1) Material: High-strength alloy steel 2)up and down sifter circles with steel plate overall by bending 3)Transmission system using spring force component institutions 4)Sieve frames of wood coated with synthetic resin,without backwire 5)All the inside walls as well as the doors are provided with high-grade insulation 6)Vertical and horizontal clamping system 4.Dampener:
- 5. - 5 - Stainless steel. 5.Bucket elevator and conveyor with reducer 6.PIPE:stainless steel in wheat flour milling machine section 7.Electronic parts: Siemens/Schneider
- 6. - 6 - 8. Plant Control System : PLC Controlling system. 9.Motor:Siemens 10.Reducer:flender/sumitomo /sew 11.Fortified dosser:for vitamins and minerals 12.Semi-automatic packaging machine: Detect weight,measure number of bags and fill automatically,customized as per client needs.
- 7. - 7 -
- 8. - 8 -
- 9. - 9 -
- 10. - 10 -
- 11. - 11 -
- 12. - 12 -
- 13. - 13 -
- 14. - 14 -
- 15. - 15 -
- 16. - 16 -
- 17. - 17 -
- 18. - 18 -
- 19. - 19 -
- 20. - 20 -