Report
Share
More Related Content
What's hot (18)
Viewers also liked
Viewers also liked (20)
Positive Hack Days. Pavlov. Network Infrastructure Security Assessment

Positive Hack Days. Pavlov. Network Infrastructure Security Assessment
Android System Architecture And Pen-testing of Android applications 

Android System Architecture And Pen-testing of Android applications
Positive Hack Days. Gurkin. Zero Day for SCADA (0-day)

Positive Hack Days. Gurkin. Zero Day for SCADA (0-day)
Huzeyfe Önal - Siber Savunma Sistemlerinde Profesyonel Arka Kapılar

Huzeyfe Önal - Siber Savunma Sistemlerinde Profesyonel Arka Kapılar
Collaboration Between Infosec Community and CERT Teams : Project Sonar case

Collaboration Between Infosec Community and CERT Teams : Project Sonar case
Презентация с Форума ИБ Директоров 16 апреля 2012г. "Безопасность инфраструкт...

Презентация с Форума ИБ Директоров 16 апреля 2012г. "Безопасность инфраструкт...
Recently uploaded
Recently uploaded (20)
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365

Tech-Forward - Achieving Business Readiness For Copilot in Microsoft 365
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
eminghuliev #nullpd
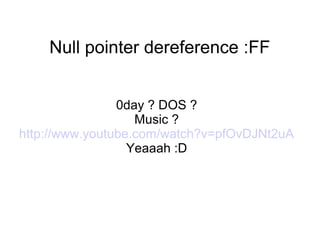
- 1. Null pointer dereference :FF 0day ? DOS ? Music ? http://www.youtube.com/watch?v=pfOvDJNt2uA Yeaaah :D
- 2. ENTER DEMO :FFFFFF int* x; // Allocate the pointers x and y int* y; // (but not the pointees) x = malloc(sizeof(int)); // Allocate an int pointee, // and set x to point to it *x = 42; // Dereference x to store 42 in its pointer *y = 13; // CRASH -- y does not have a pointer yet
- 3. int *ptr, a = 12 ptr = &a; /* ptr buffer a variable shows ptr = NULL; /* ptr set NULL */ *ptr = 8 /* crash! NULL pointer!!! value can not be determined*/ Sizede bi eğrilik görsendimi amk ?
- 4. NULL Pointer Dereference vulnerablity :S size_t size = strlen(input_str)+1; str = (char *)malloc(size); input_str is copied into dynamically allocated memory referenced by str memcpy(str, input_str, size); If malloc() fails, it returns a null pointer that is assigned to str When str is dereferenced in memcpy()
- 5. /home/te~wnyou.c #include <stdio.h> #include <stdlib.h> #include <string.h> int main(char *argc,char *argv[]) { char *str; char *input_string=argv[1]; size_t size = strlen(input_string)+1; str = (char *) malloc(size); memcpy(str, input_string,size); printf("%sn",str); free(str); ... return(0); } Insecure Codes ?
- 6. Reversing ? EAX: 0x0 EBX: 0xb7fbe000 --> 0x1a5d7c ECX: 0x0 EDX: 0xbffff204 --> 0xb7fbe000 --> 0x1a5d7c ESi: 0x0 EDi: 0x0 <======= EBP: 0xbffff1d8 --> 0x0 ESP: 0xbffff1a4 --> 0x0 EiP: 0xb7e9c756 (movdqu xmm1,XMMWORD PTR [edi]) =================== ======> 0xb7e9c756: movdqu xmm1,XMMWORD PTR [edi] CRASH !!!!!!!!!!!!!!!!!!! Reversing ?Reversing ?Reversing ?
