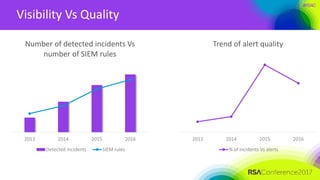
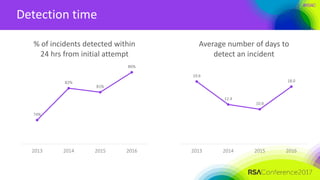
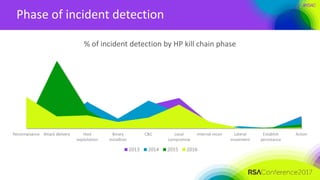
The document discusses lessons learned from building a cybersecurity operation center at DU Telecom, highlighting key findings such as the prevalence of forensic evidence in breaches and critical security metrics. It emphasizes the importance of identifying high-value targets and understanding the threat landscape while also focusing on advanced monitoring and detection strategies. Additionally, it outlines recommendations for setting security KPIs, identifying assets, and building use cases for proactive incident detection.