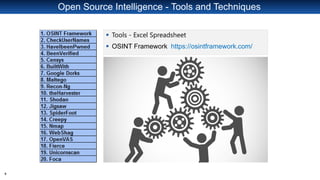
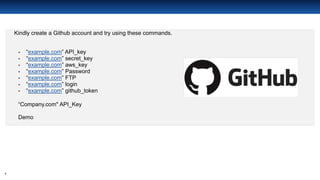
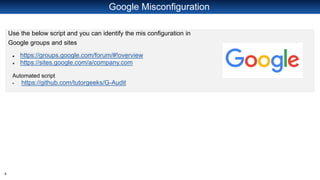
The document discusses open source intelligence (OSINT), including what it is, how it is used, techniques for gathering it, and tools that can be used. OSINT involves collecting publicly available data for intelligence purposes. It is produced from public sources and addresses specific intelligence needs. Security professionals use OSINT to identify vulnerabilities in organizations from accidental information leaks online or exposed assets. However, threat actors also use OSINT to find targets and vulnerabilities to exploit. The document recommends using OSINT proactively to find and address weaknesses before threats actors do. It provides examples of tools like Excel, OSINT Framework, Github search, and Wappalyzer that can be used to search public data and identify technical details about organizations and vulnerabilities.