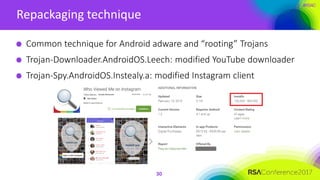
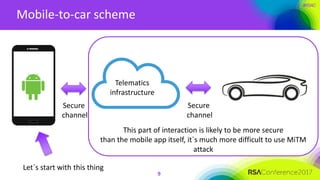
The document discusses the risks associated with remote access features in connected cars, highlighting how malware can compromise smartphone security, leading to car theft. It outlines various techniques used by cybercriminals to exploit vulnerabilities in mobile apps and devices, emphasizing the lack of protection in several connected car applications. The presentation calls for improved security measures for car applications, suggesting they should be as robust as those used in banking apps.






![#RSAC
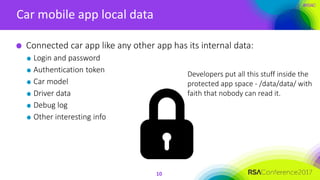
Stored data examples
11
[top tier auto manufacturer app] with
credentials.xml
[another top tier auto manufacturer app]
with prefs.{?????????}.xml](https://image.slidesharecdn.com/hta-r10-hey-android-where-is-my-car-170502092951/85/Hey-android-Where-is-my-car-11-320.jpg)














![#RSAC
Repackaging technique
29
In the case with the connected car app login activity can be patched
We modified app code, login and password are just showed as a toast
Patched app was successfully run
[top tier auto manufacturer] app](https://image.slidesharecdn.com/hta-r10-hey-android-where-is-my-car-170502092951/85/Hey-android-Where-is-my-car-29-320.jpg)