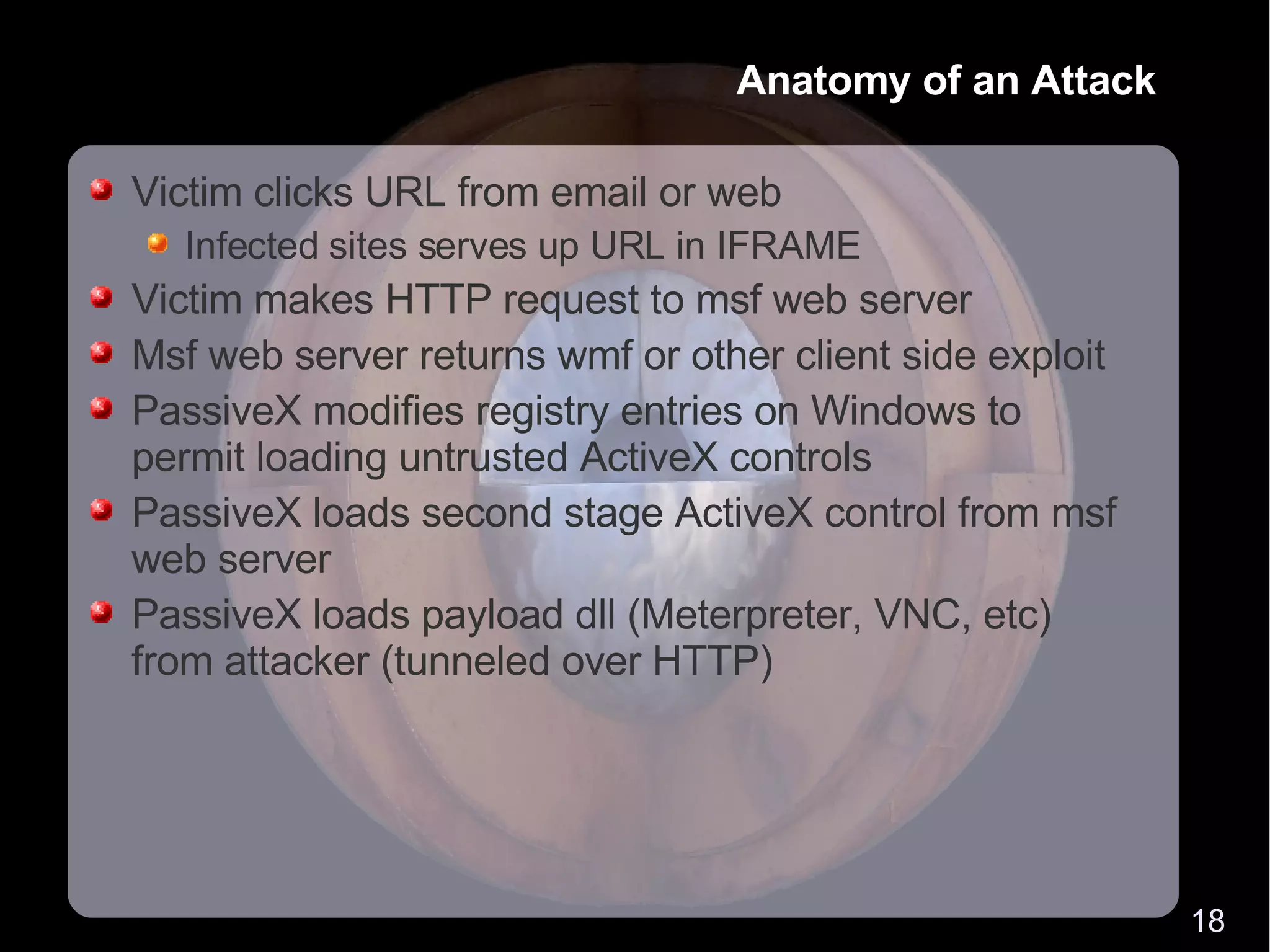
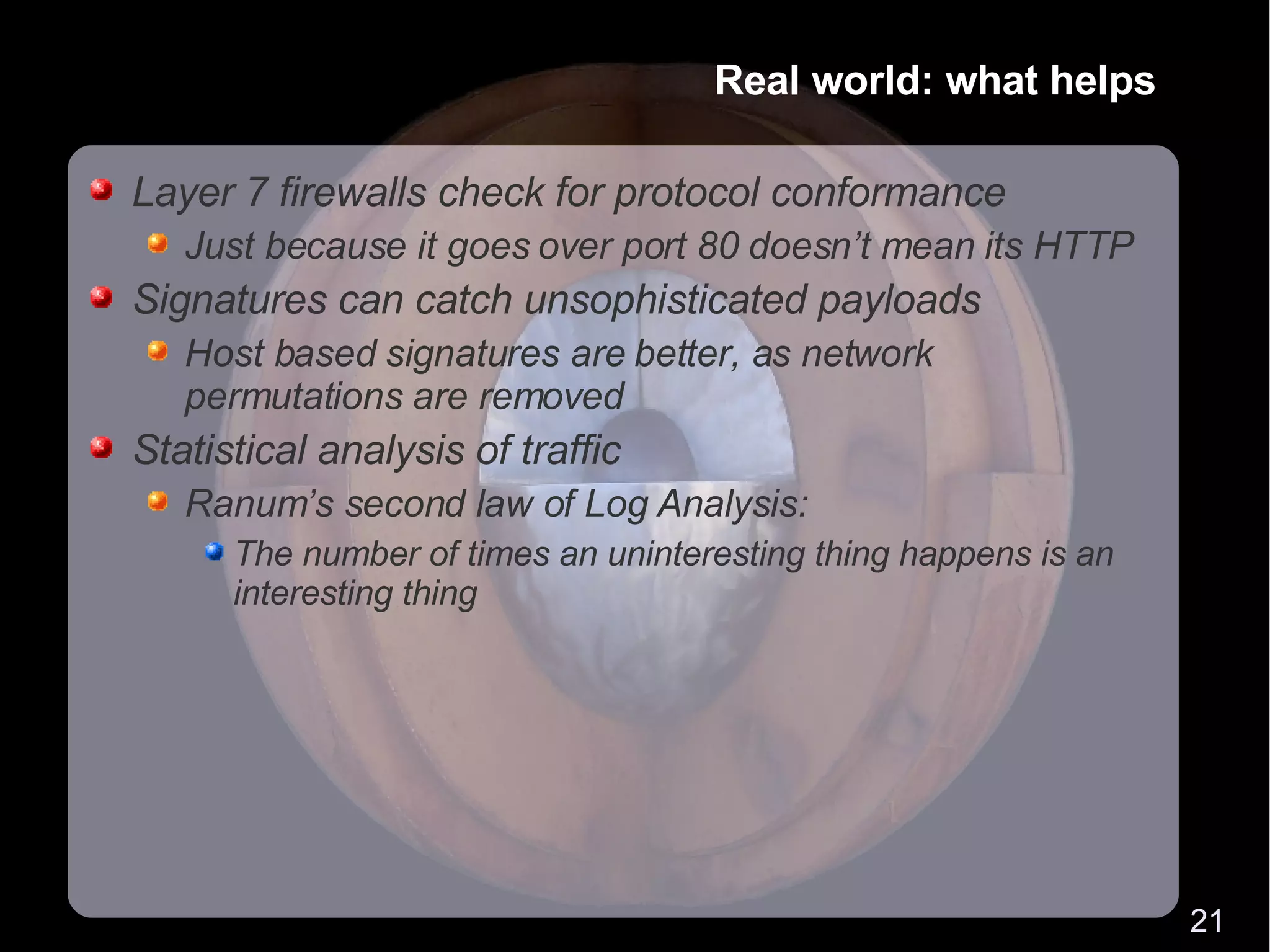
The document discusses how firewalls are commonly bypassed using techniques like tunneling traffic over allowed protocols like HTTP and DNS. It provides an example attack scenario where a victim is infected via a client-side exploit delivered over HTTP. While ideal security would involve disconnecting systems, more practical approaches include deep packet inspection, application-aware firewalls, and host-based signatures to detect protocol misuse and anomalous traffic.
![Quick Introduction About Me Christopher Byrd, CISSP Senior Security Engineer [email_address] www.riosec.com About Metasploit Primary developers H D Moore (hdm) and Matt Miller (skape) www.metasploit.com metasploit.blogspot.com](https://image.slidesharecdn.com/inside-out-hacking-bypassing-firewall2992/75/Inside-Out-Hacking-Bypassing-Firewall-2-2048.jpg)