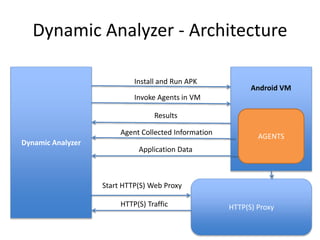
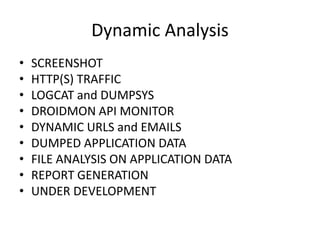
Mobile Security Framework is an open source automated mobile application testing framework capable of static and dynamic analysis of Android and iOS apps. It performs various analyses including permission analysis, API monitoring, and HTTP traffic analysis. The framework supports analyzing APK, IPA, and source code. It is available on GitHub and includes demos of static analysis on sample APK and IPA files. The presentation also describes a mobile security CTF challenge involving two Android apps, GETSECRET and SENDSECRET, that can be solved by analyzing the apps with Mobile Security Framework or other reversing techniques.