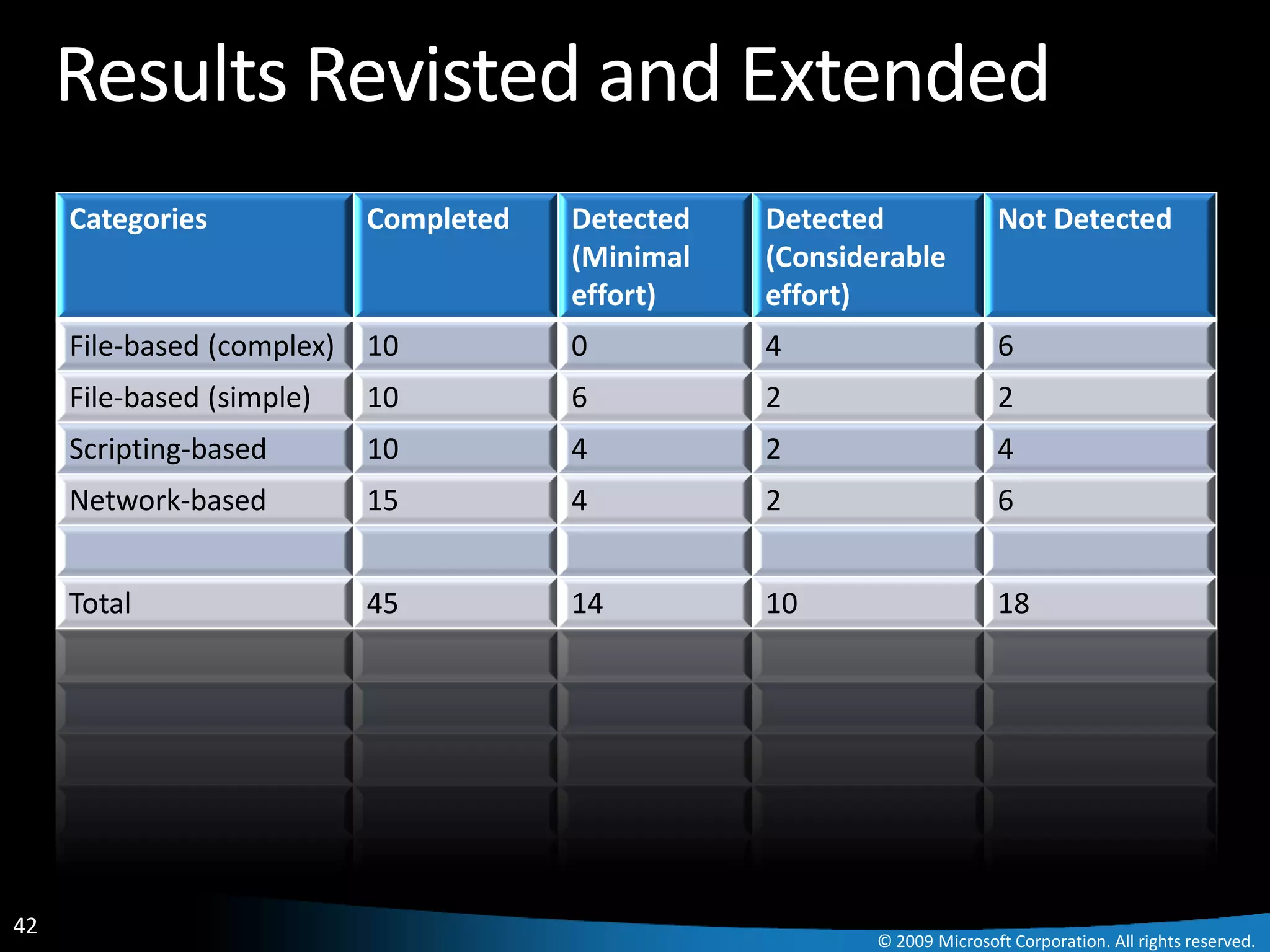
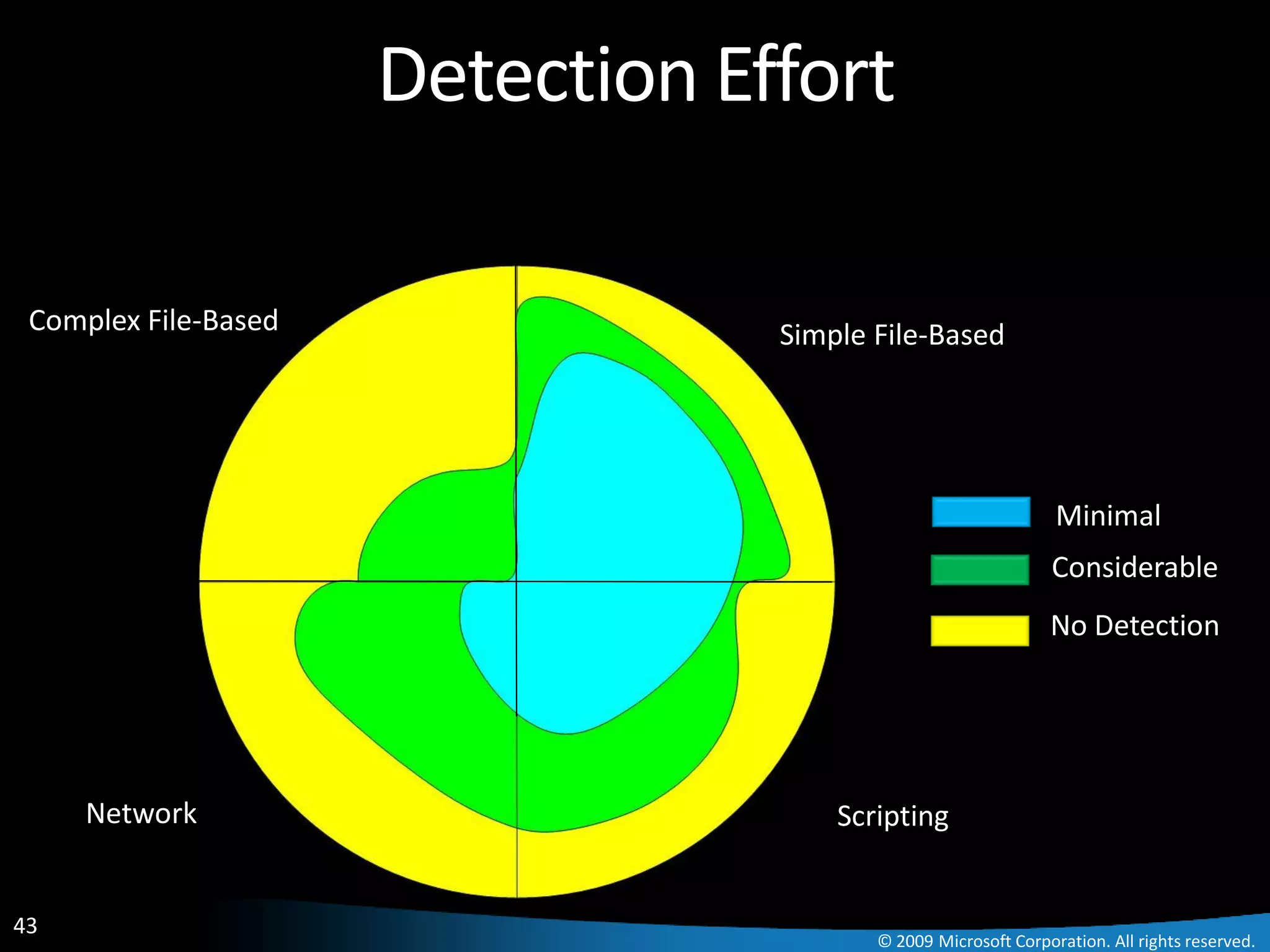
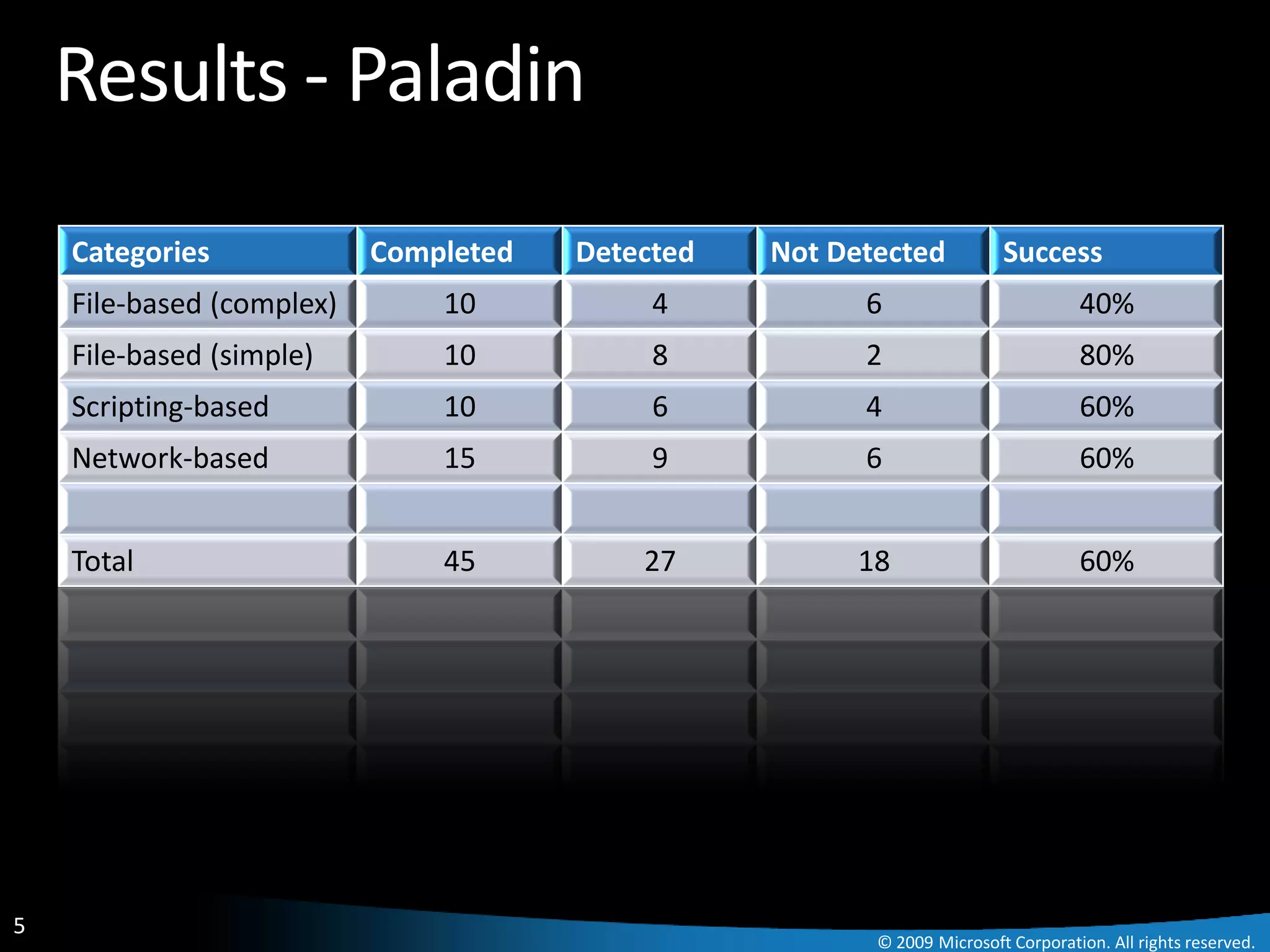
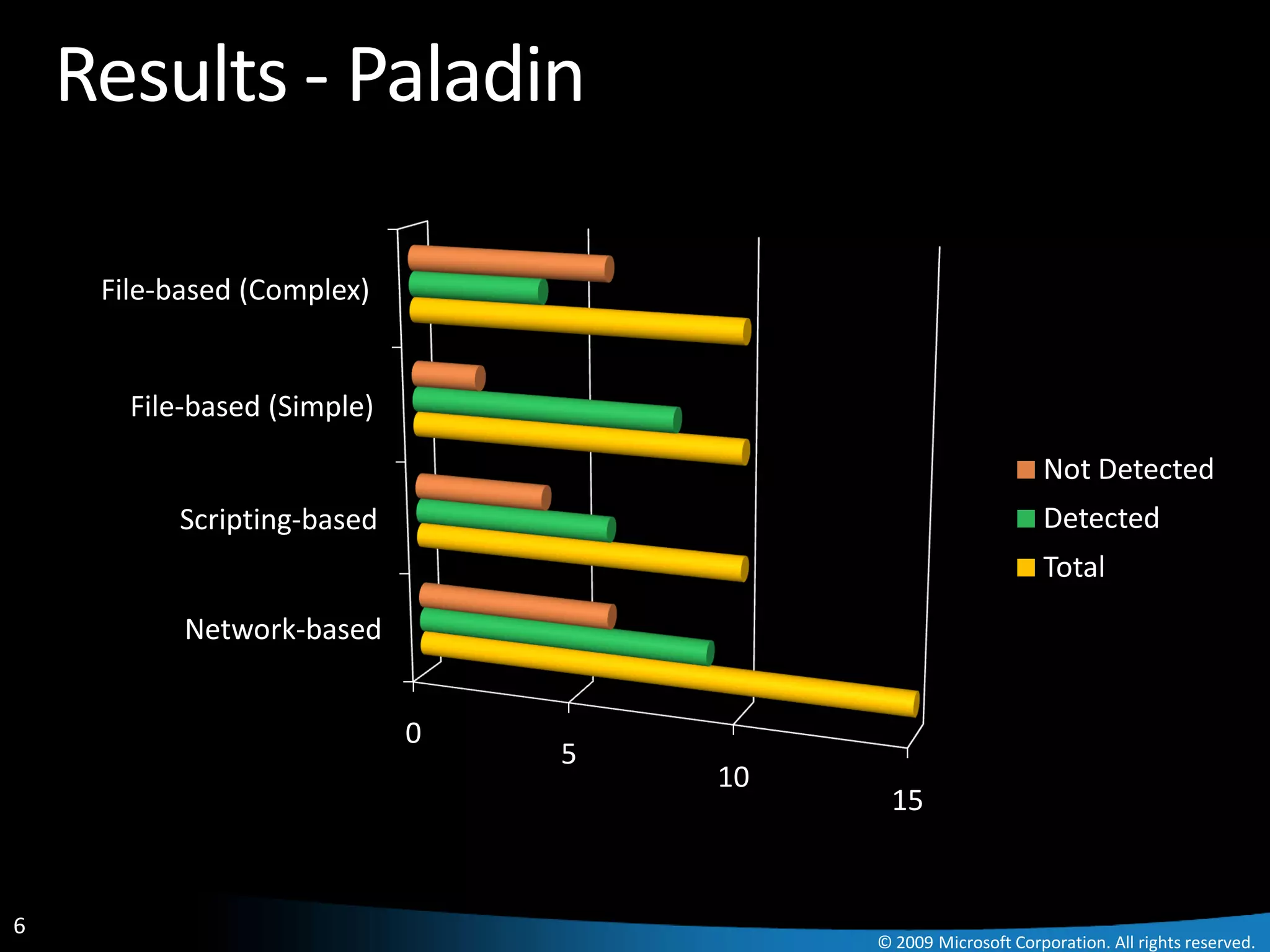
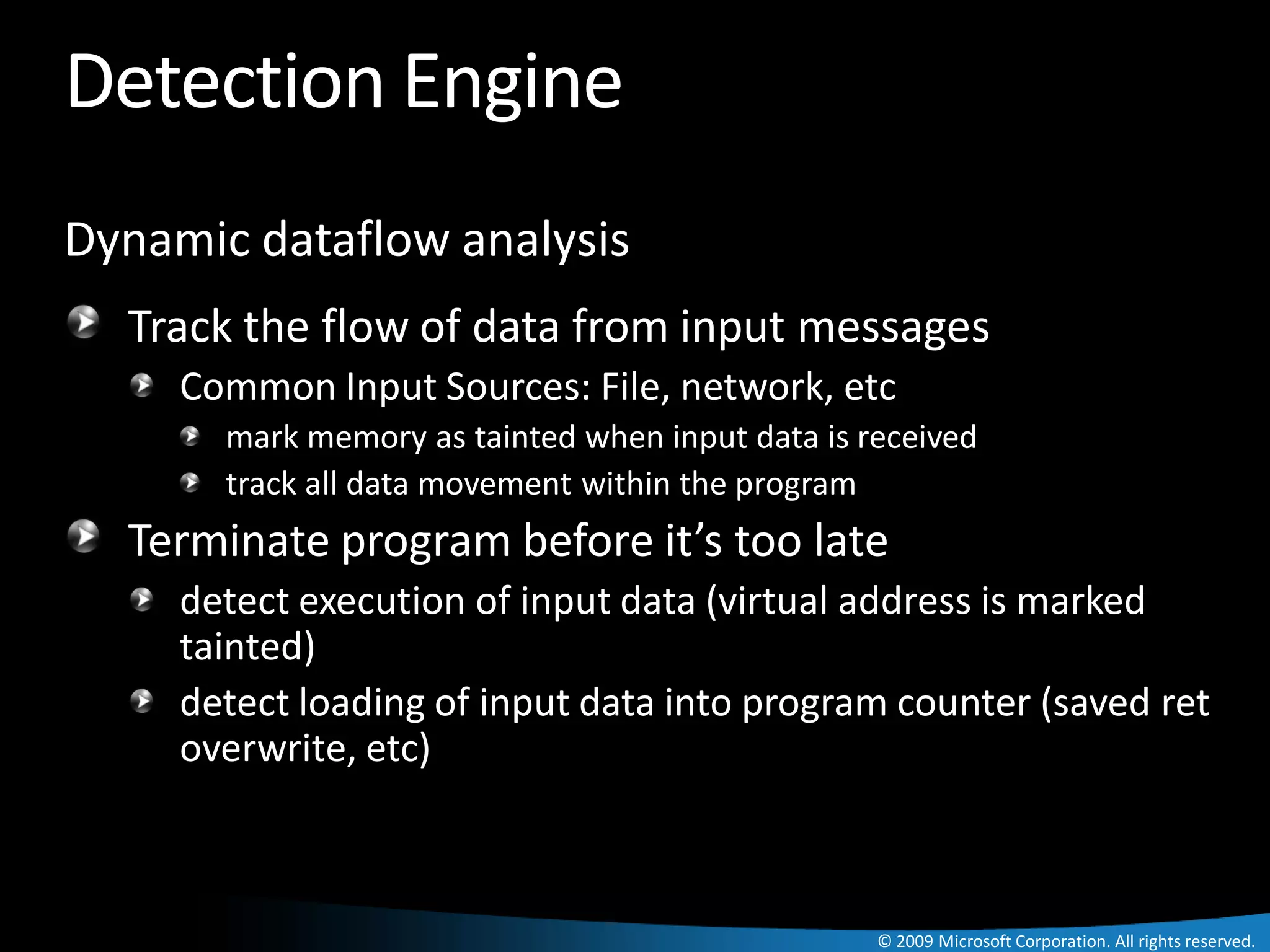
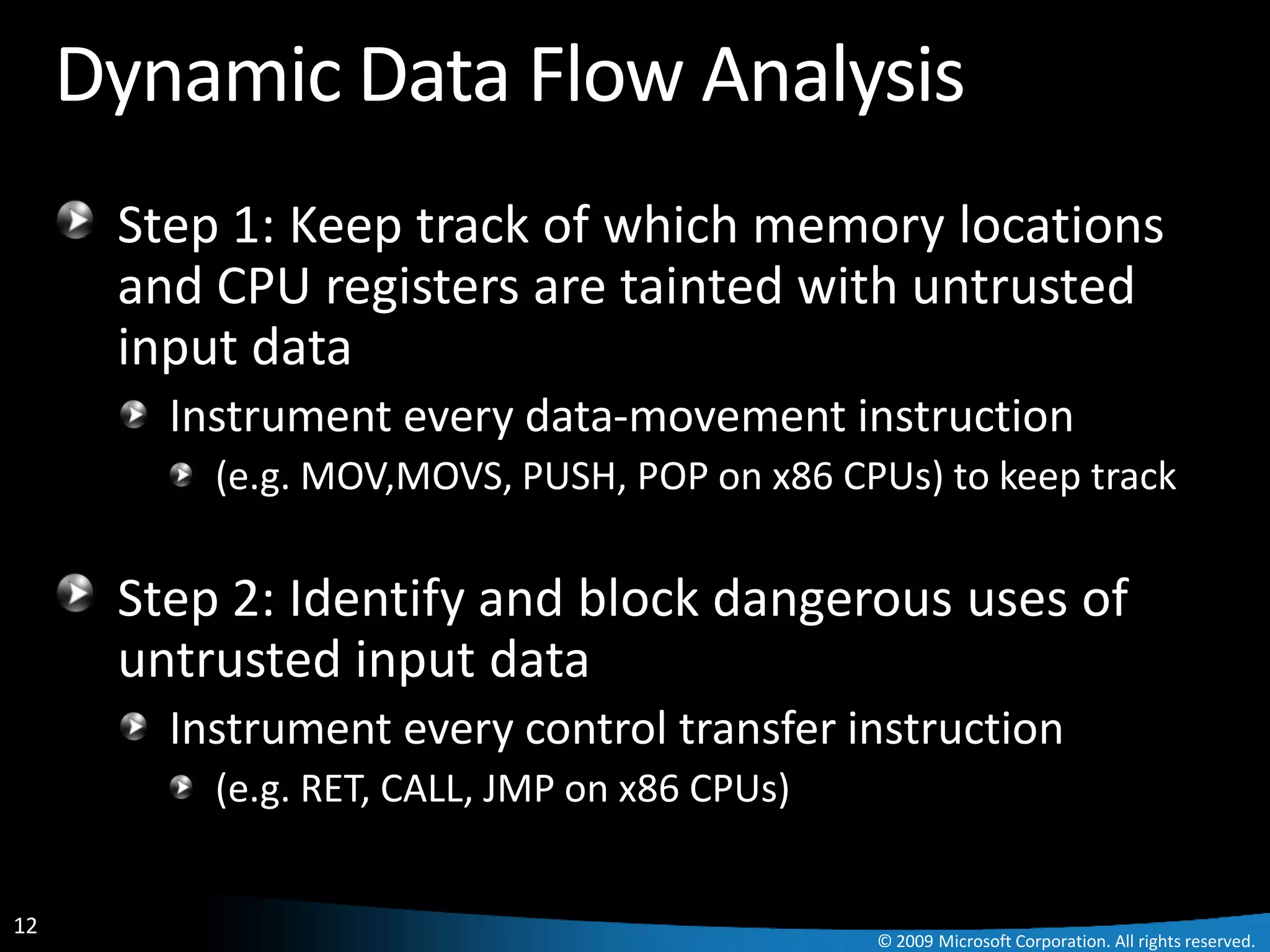
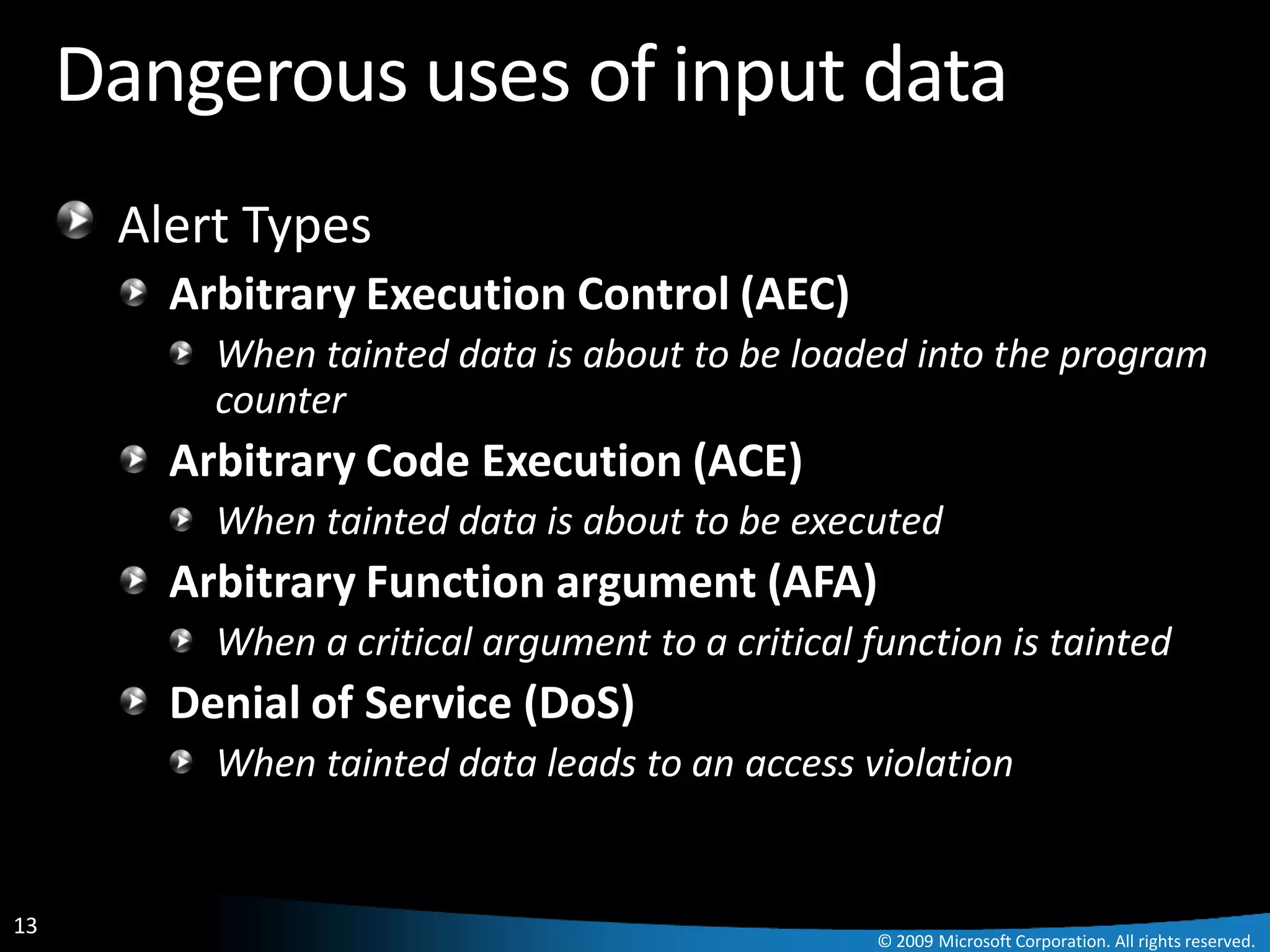
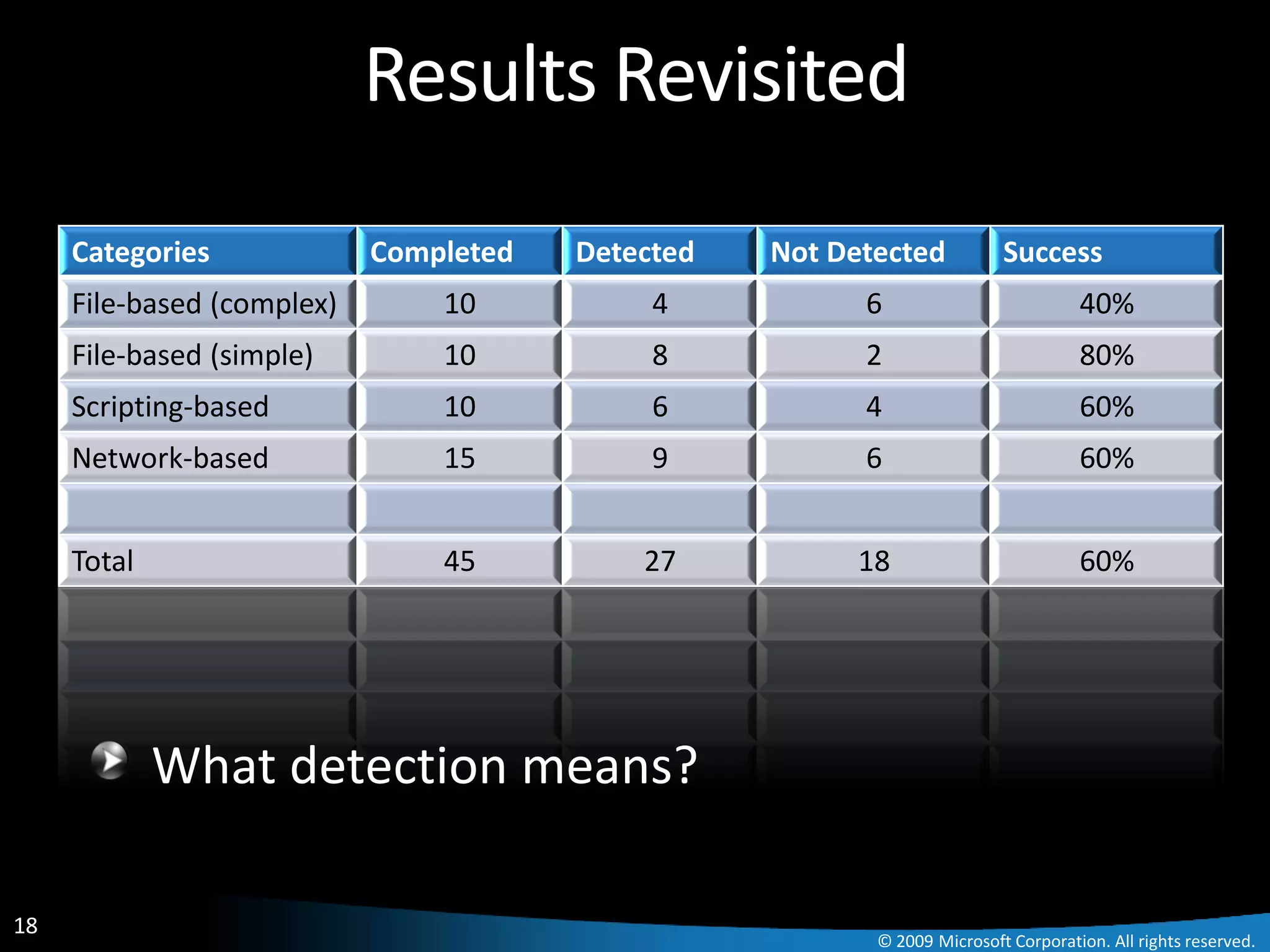
The document discusses Paladin, a suite of tools developed by Microsoft's Malware Protection Center to automate the analysis of exploits. Paladin uses dynamic data flow analysis and binary instrumentation to detect exploits by tracking the flow of untrusted input data. It analyzed 45 vulnerabilities and detected 27, for a success rate of 60%. The challenges of complex programs, false positives, and engineering issues in deployment are also reviewed.





![How does Vigilante work?
C:> _ ulnProcess
V
Stack C:> _
nirvExec /clientname “detector.dll” /attach 1033
C:> _ Exploit
exploitProcess
C:> _
Detector
Static Data
Code
Vigi_log.log
vulnProcess [pid:1033]
15
© 2009 Microsoft Corporation. All rights reserved.](https://image.slidesharecdn.com/cansecwest-100728172341-phpapp01/75/Cansec-West-2009-15-2048.jpg)
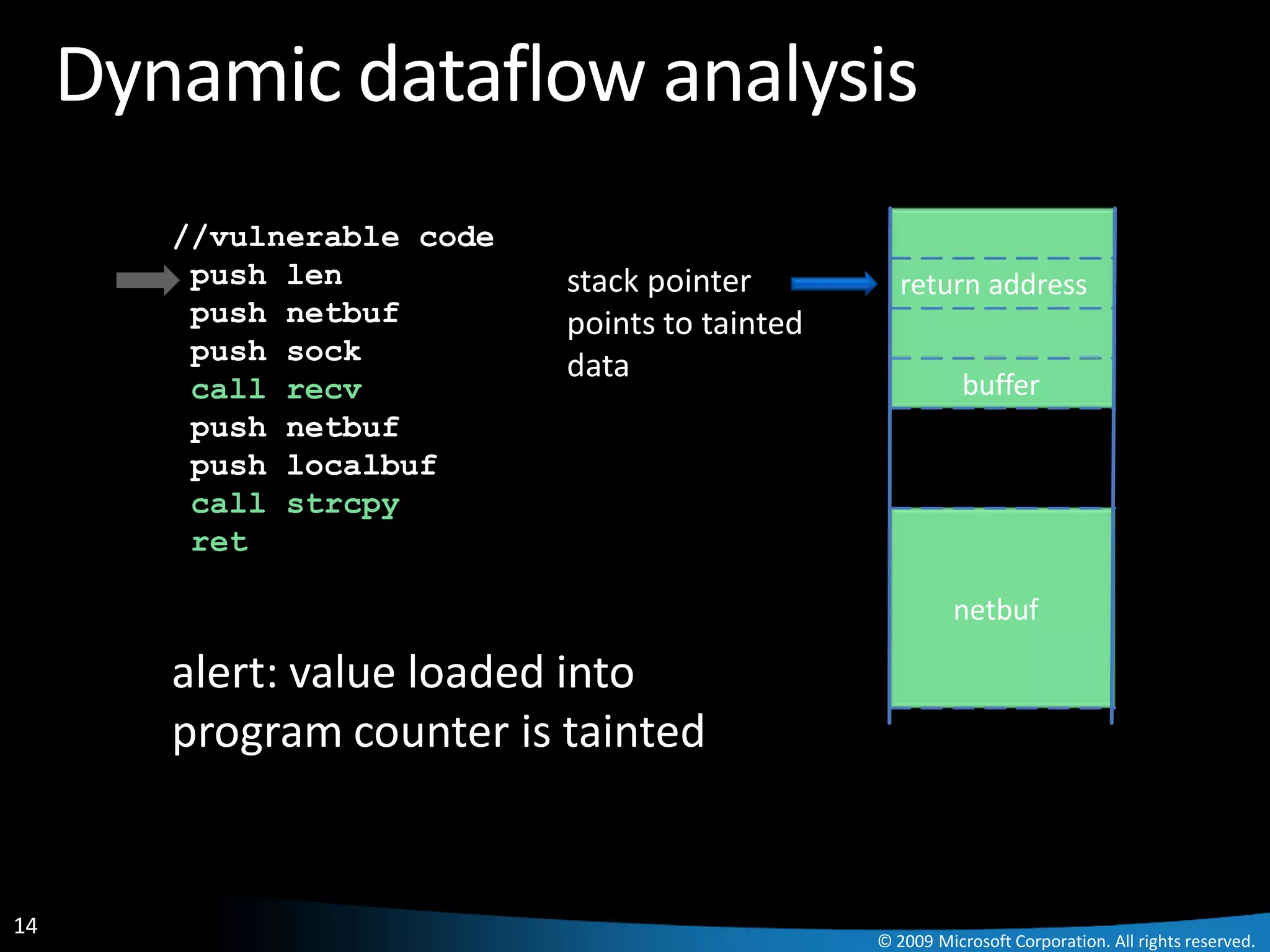
![Dynamic dataflow analysis
//vulnerable code
.EXE
push len
push buff
push sock
call recv buff
buff
mov eax, buf[3]
call eax
...
Detector
Alert!!!
Vulnerable Process
16
© 2009 Microsoft Corporation. All rights reserved.](https://image.slidesharecdn.com/cansecwest-100728172341-phpapp01/75/Cansec-West-2009-16-2048.jpg)






![False Alerts in Theory
Table Lookup:
result = table[in_byte]; // False Positive
result = table[in_byte]; // Should be
Implicit flows:
if (in_byte == 1) result = 1; // False Negative
if (in_byte == 1) result = 1; // Should be
if (in_byte == 2) result = 2; // False Negative
if (in_byte == 2) result = 2; // Should be
Arithmetic restrictions:
result = (in_byte & 0x00); // False Positive
result = (in_byte & 0x00); // Should be
27
Newsome and Song: “Influence: A Quantitative Approach for Data Integrity” © 2009 Microsoft Corporation. All rights reserved.](https://image.slidesharecdn.com/cansecwest-100728172341-phpapp01/75/Cansec-West-2009-27-2048.jpg)

![FPs in JumpTables Example
CVE-2006-4691: BO NetJoinDomain Workstation Service
Via RPC
CallRPCInterface(BYTES *In_Bytes)
{
NetJoinDomain= DispatchTable[In_Bytes];
Invoke( NetJoinDomain, // <<<<<<< FALSE POSITIVE
pArgBuffer,
ArgNum );
}
29
© 2009 Microsoft Corporation. All rights reserved.](https://image.slidesharecdn.com/cansecwest-100728172341-phpapp01/75/Cansec-West-2009-29-2048.jpg)
![FPs in tracking
CVE-2009-0076 (IE vulnerability CSS Memory
Corruption)
??C:Documents and SettingsvigilanteRecentdesktop.ini
Handle = 410 FileSize = 96
Tracked handle: Buf = 5fc0000
PostIoInitiation: pIosb=169646c; pBuf=5fc0000; hFile=410; hEvent=0
Io completed synchronously.
HandleIoCompletion: pIosb=169646c; dwLen=96
SetTaint: Base=5fc0000 Len=96
ADDR 0x5fc0000 - 0x5fc0095 set to dirty= 0x2
RANGE 5fc0000..5fc0095 set to = [2..97]
30
© 2009 Microsoft Corporation. All rights reserved.](https://image.slidesharecdn.com/cansecwest-100728172341-phpapp01/75/Cansec-West-2009-30-2048.jpg)
![Mitigations to FPs in Practice
Flags:
IndirectAddressing mov [disp + ref1 + ref2*i], 0xff
JmpCallIndirect jmp/call [disp + ref1 + ref2*i]
LowFalsePositives Turn off set of handlers
False Positives file
CVE-2008-2254 (IE HTML Obj Mem Corruption)
0x7d513573
0x7d518123
0x746c240a
0x75c59c7a
Policy File
31
© 2009 Microsoft Corporation. All rights reserved.](https://image.slidesharecdn.com/cansecwest-100728172341-phpapp01/75/Cansec-West-2009-31-2048.jpg)




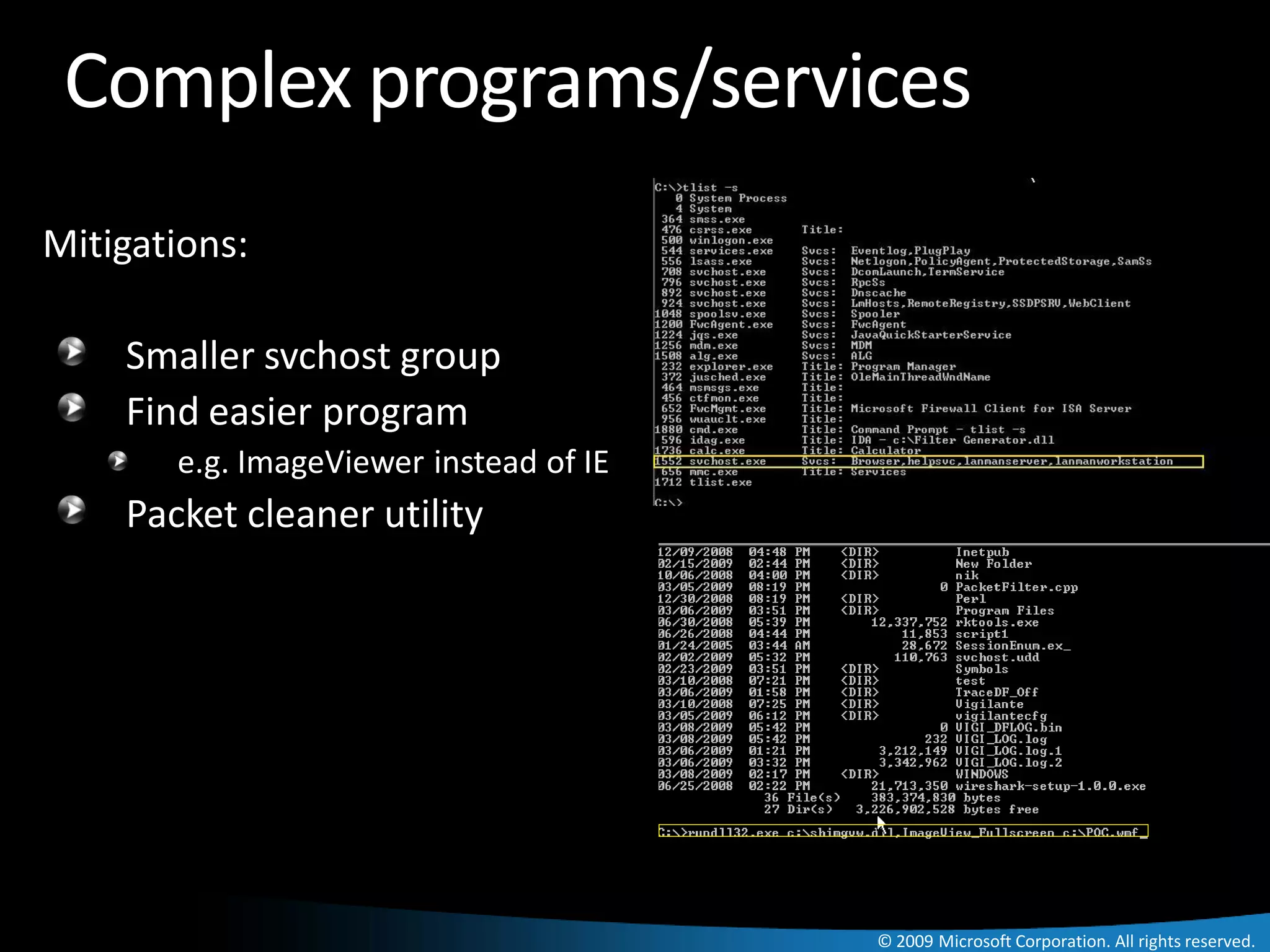
![Complex programs/services Example
VIGI_LOG.LOG -
??PIPEsrvsvc
CAN-2002-0724 LANMAN SetTaint: Base=d84d8 Len=44
ADDR 0xd84d8 - 0xd851b set to dirty= 0x2
vulnerability RANGE d84d8..d851b set to = [2..45]
mov rm8,rm8 -- dirty
EIP: 0x77ce3a77 ESP: 0x11cf940 TID: 0x6d0
DOS with unchecked buffer to Operand1: 0x0 Dirty: 0x6, 0x7, 0x0, 0x0
Operand2: 0xd84dc Dirty: 0x6, 0x7, 0x8, 0x9
NetShareEnum ----------------------------------------------
movz/sx r32,rm16 -- dirty
EIP: 0x77cc9f90 ESP: 0xc3fa84 TID: 0x748
Operand1: 0x0 Dirty: 0x12, 0x13, 0x0, 0x0
Operand2: 0xb3d52 Dirty: 0x12, 0x13, 0x0, 0x0
Operand2.RefdRegister1: 0x0 Dirty: 0x12, 0x13
----------------------------------------------
??PIPElsarpc
SetTaint: Base=d45f8 Len=44
ADDR 0xd45f8 - 0xd463b set to dirty= 0x46
RANGE d45f8..d463b set to = [46..89]
movz/sx r32,rm16 -- dirty
EIP: 0x77cc9b6e ESP: 0x1b9f6b0 TID: 0x6b8
Operand1: 0x18 Dirty: 0x4e, 0x4f, 0x0, 0x0
Operand2: 0x0 Dirty: 0x4e, 0x4f, 0x0, 0x0
38
© 2009 Microsoft Corporation. All rights reserved.](https://image.slidesharecdn.com/cansecwest-100728172341-phpapp01/75/Cansec-West-2009-38-2048.jpg)