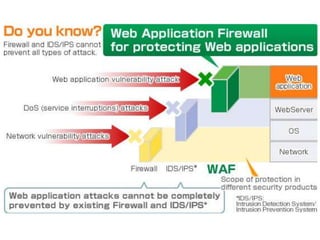
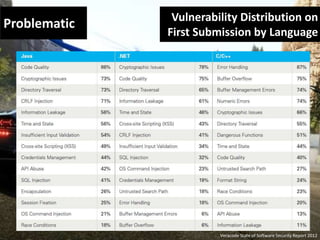
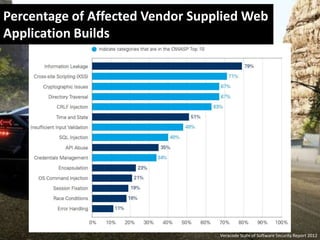
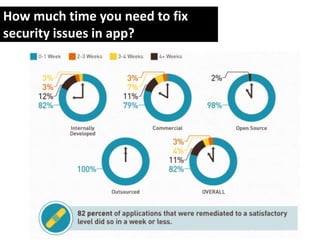
The document discusses the importance of web application firewalls (WAF) as a security measure for applications facing increasing threats such as data theft and hacking. It highlights the advantages of using a WAF in combination with dynamic application security testing to protect against vulnerabilities and data leakage. The document also identifies target audiences for WAF, including financial and healthcare organizations, and encourages engagement with the solution provided by SoftServe.