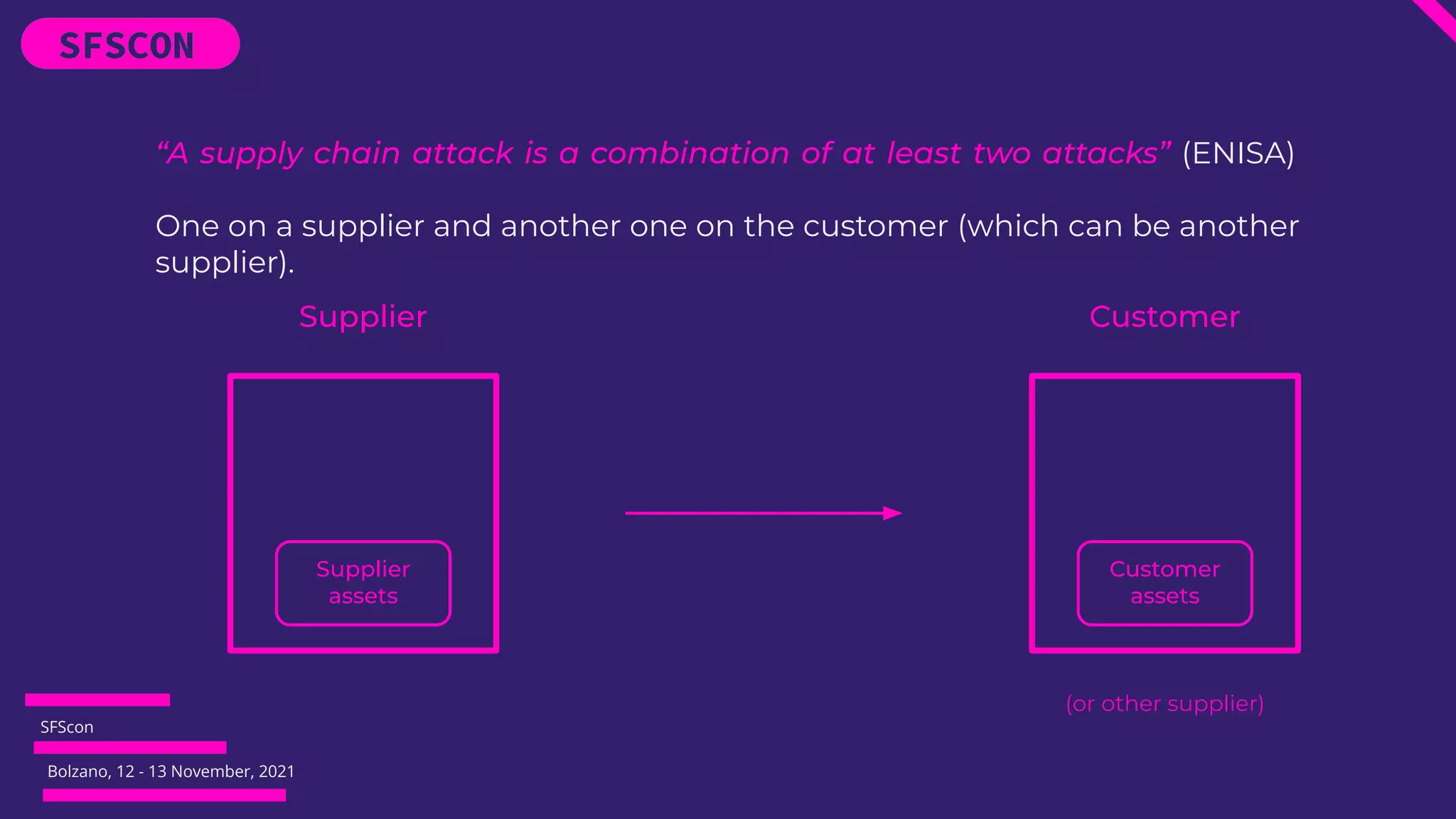
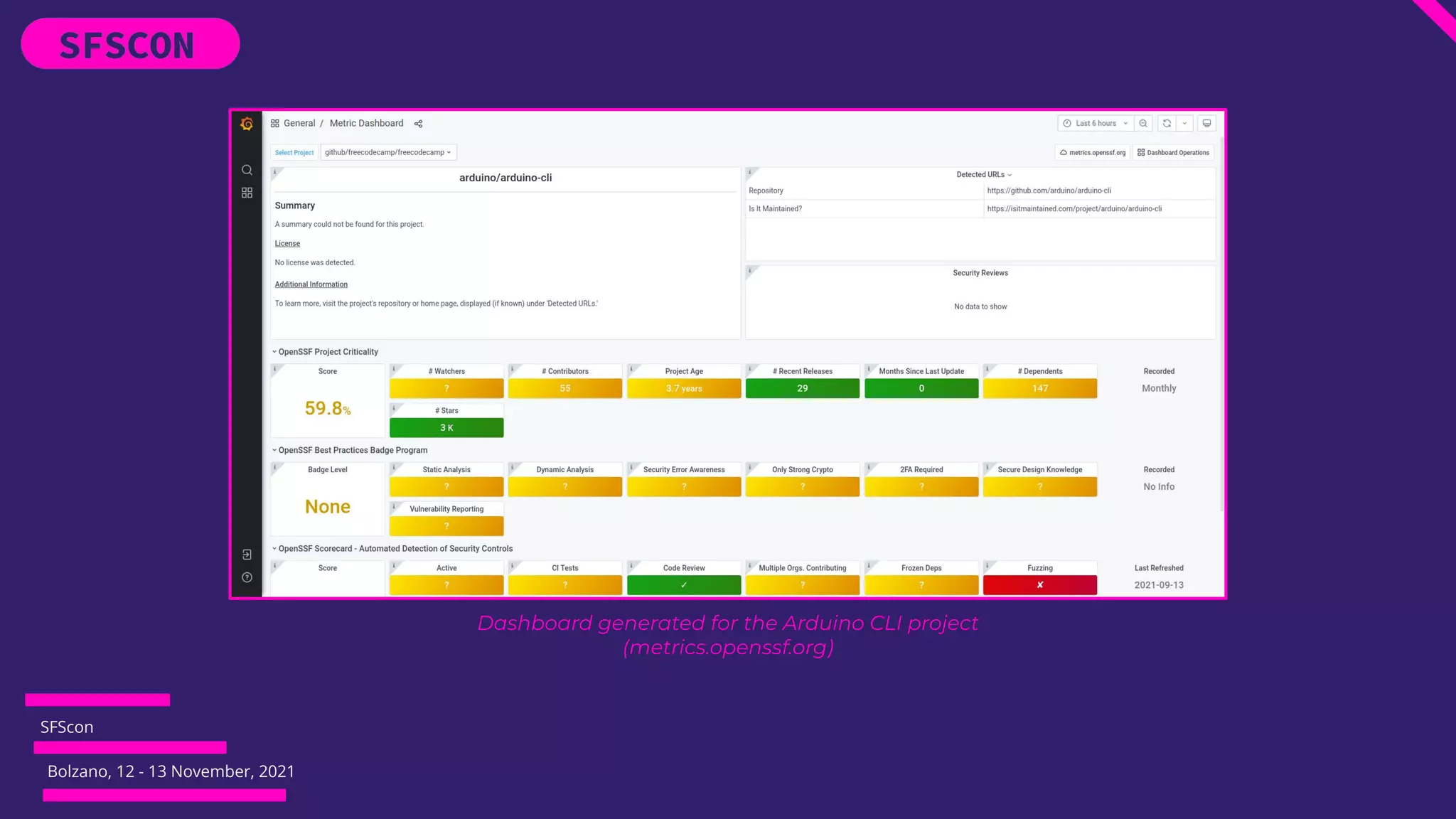
The document discusses supply chain attacks and how they can affect open source projects. It describes common types of supply chain attacks like namespace confusion, typosquatting, and malicious code injection. It then discusses how the OpenSSF Security Metrics and Security Scorecards tools can help open source projects reduce risks from supply chain attacks by providing security data and scorecards that evaluate projects' security practices and posture.