Digital Transformation and the Role of IAM
•
0 likes•4,007 views
We surveyed 200 IT decision makers across four countries to learn where they are in their journey and the role that identity and access management (IAM) plays in the path to digital transformation.
Report
Share
Report
Share
Recommended
Digital Transformation and Security for the Modern Business Part 1 – Finance

Digital Transformation and Security for the Modern Business Part 1 – FinanceXenith Document Systems Ltd
More Related Content
What's hot
Digital Transformation and Security for the Modern Business Part 1 – Finance

Digital Transformation and Security for the Modern Business Part 1 – FinanceXenith Document Systems Ltd
What's hot (20)
Digital Transformation and Security for the Modern Business Part 1 – Finance

Digital Transformation and Security for the Modern Business Part 1 – Finance
Global Cybersecurity Market Industry Trends, Analysis Report 2021

Global Cybersecurity Market Industry Trends, Analysis Report 2021
The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...

The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...
Cybersecurity 2020: Your Biggest Threats and How You Can Prevent Them 

Cybersecurity 2020: Your Biggest Threats and How You Can Prevent Them
Why Zero Trust Architecture Will Become the New Normal in 2021

Why Zero Trust Architecture Will Become the New Normal in 2021
Deutsche Telekom Partnering Operating Alliance Summit - Zimperium

Deutsche Telekom Partnering Operating Alliance Summit - Zimperium
Viewers also liked
Viewers also liked (7)
Identity-Defined Privacay & Security for Internet of Things

Identity-Defined Privacay & Security for Internet of Things
Identity and Access Management Survey: Current Market Challenges and Solutions

Identity and Access Management Survey: Current Market Challenges and Solutions
Similar to Digital Transformation and the Role of IAM
IT Resilience and Cloud : Seminar Protecting Mission-Critical Application Aga...

IT Resilience and Cloud : Seminar Protecting Mission-Critical Application Aga...PT Datacomm Diangraha
[Event] Digital transformation : How it affects us - PRESENTATION POST LUXEMB...![[Event] Digital transformation : How it affects us - PRESENTATION POST LUXEMB...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Event] Digital transformation : How it affects us - PRESENTATION POST LUXEMB...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Event] Digital transformation : How it affects us - PRESENTATION POST LUXEMB...POST Telecom for Business
Similar to Digital Transformation and the Role of IAM (20)
Amsterdam 2015 Identity Summit: Welcome and Keynote: Using Identity to Empowe...

Amsterdam 2015 Identity Summit: Welcome and Keynote: Using Identity to Empowe...
Preparing for the Future of Enterprise Mobility -- Insights Not to Miss

Preparing for the Future of Enterprise Mobility -- Insights Not to Miss
IT Resilience and Cloud : Seminar Protecting Mission-Critical Application Aga...

IT Resilience and Cloud : Seminar Protecting Mission-Critical Application Aga...
Growing the Digital Business: Accenture Mobility Research 2015

Growing the Digital Business: Accenture Mobility Research 2015
[Infographic] Cloud Integration Drivers and Requirements in 2015![[Infographic] Cloud Integration Drivers and Requirements in 2015](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Cloud Integration Drivers and Requirements in 2015](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Cloud Integration Drivers and Requirements in 2015
Infographic: Bringing Your Cloud Visibility Back Into Focus

Infographic: Bringing Your Cloud Visibility Back Into Focus
SURVEY RESULTS: ACCELERATING INNOVATION AND THE DIGITAL JOURNEY - INFOGRAPHIC

SURVEY RESULTS: ACCELERATING INNOVATION AND THE DIGITAL JOURNEY - INFOGRAPHIC
[Event] Digital transformation : How it affects us - PRESENTATION POST LUXEMB...![[Event] Digital transformation : How it affects us - PRESENTATION POST LUXEMB...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Event] Digital transformation : How it affects us - PRESENTATION POST LUXEMB...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Event] Digital transformation : How it affects us - PRESENTATION POST LUXEMB...
Identity Summit UK: KEYNOTE: ‘USING IDENTITY TO EMPOWER CIOS’

Identity Summit UK: KEYNOTE: ‘USING IDENTITY TO EMPOWER CIOS’
Infographic: Cloud Security & SMBs - What You Need to Know in 2015

Infographic: Cloud Security & SMBs - What You Need to Know in 2015
More from Ping Identity
More from Ping Identity (20)
Security Practices: The Generational Gap | Infographic

Security Practices: The Generational Gap | Infographic
Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...

Hybrid IAM: Fuelling Agility in the Cloud Transformation Journey | Gartner IA...
LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES

LES ATTITUDES DES CONSOMMATEURS À L’ÈRE DES CYBERATTAQUES
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN?
Consumer Attitudes in a Post-breach Era: The Geographical Gap

Consumer Attitudes in a Post-breach Era: The Geographical Gap
Standard Based API Security, Access Control and AI Based Attack - API Days Pa...

Standard Based API Security, Access Control and AI Based Attack - API Days Pa...
ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS

ATTITUDES DES CONSOMMATEURS A L’ERE DES PIRATAGES LE CONFLIT DE GENERATIONS
2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap

2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap
WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...

WIE TICKEN VERBRAUCHER IM ZEITALTER DER DATENSCHUTZVERLETZUNGEN? ALLES EINE F...
Fishing for a CIAM Platform? 11 Question to Ask Before You Buy

Fishing for a CIAM Platform? 11 Question to Ask Before You Buy
Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)

Criteria for Effective Modern IAM Strategies (Gartner IAM 2018)
Webinar: Three Steps to Transform Your Mobile App into a Security Factor

Webinar: Three Steps to Transform Your Mobile App into a Security Factor
Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass 

Webinar: Deep Diving Into the KuppingerCole IDaaS Leadership Compass
Recently uploaded
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Recently uploaded (20)
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
WSO2's API Vision: Unifying Control, Empowering Developers

WSO2's API Vision: Unifying Control, Empowering Developers
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Elevate Developer Efficiency & build GenAI Application with Amazon Q

Elevate Developer Efficiency & build GenAI Application with Amazon Q
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Introduction to Multilingual Retrieval Augmented Generation (RAG)

Introduction to Multilingual Retrieval Augmented Generation (RAG)
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Digital Transformation and the Role of IAM
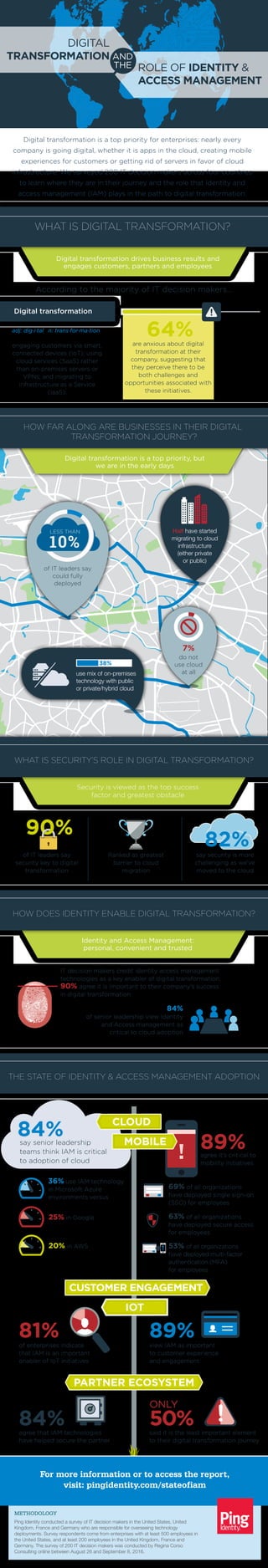
- 1. 89% 81% agree it’s critical to mobility initiatives Digital transformation drives business results and engages customers, partners and employees adj: dig·i·tal n: trans·for·ma·tion engaging customers via smart, connected devices (IoT); using cloud services (SaaS) rather than on-premises servers or VPNs; and migrating to Infrastructure as a Service (IaaS). According to the majority of IT decision makers... are anxious about digital transformation at their company, suggesting that they perceive there to be both challenges and opportunities associated with these initiatives. of IT leaders say could fully deployed LESS THAN 10% use mix of on-premises technology with public or private/hybrid cloud 38% Half have started migrating to cloud infrastructure (either private or public) do not use cloud at all 7% WHAT IS DIGITAL TRANSFORMATION? HOW FAR ALONG ARE BUSINESSES IN THEIR DIGITAL TRANSFORMATION JOURNEY? Digital transformation is a top priority, but we are in the early days WHAT IS SECURITY’S ROLE IN DIGITAL TRANSFORMATION? Security is viewed as the top success factor and greatest obstacle HOW DOES IDENTITY ENABLE DIGITAL TRANSFORMATION? Identity and Access Management: personal, convenient and trusted THE STATE OF IDENTITY & ACCESS MANAGEMENT ADOPTION Digital transformation is a top priority for enterprises: nearly every company is going digital, whether it is apps in the cloud, creating mobile experiences for customers or getting rid of servers in favor of cloud infrastructure. We surveyed 200 IT decision makers across four countries to learn where they are in their journey and the role that identity and access management (IAM) plays in the path to digital transformation. Digital transformation 64% of IT leaders say security key to digital transformation Ranked as greatest barrier to cloud migration say security is more challenging as we’ve moved to the cloud 90% 82% IT decision makers credit identity access management technologies as a key enabler of digital transformation, 90% agree it is important to their company’s success in digital transformation. 84% of senior leadership view Identity and Access management as critical to cloud adoption DIGITAL TRANSFORMATION AND THE ROLE OF IDENTITY & ACCESS MANAGEMENT CLOUD IOT MOBILE CUSTOMER ENGAGEMENT PARTNER ECOSYSTEM 84%say senior leadership teams think IAM is critical to adoption of cloud 36% use IAM technology in Microsoft Azure environments versus 25% in Google 20% in AWS ! 69% of all organizations have deployed single sign-on (SSO) for employees 63% of all organizations have deployed secure access for employees 53% of all organizations have deployed multi-factor authentication (MFA) for employees + of enterprises indicate that IAM is an important enabler of IoT initiatives 89%view IAM as important to customer experience and engagement Ping Identity conducted a survey of IT decision makers in the United States, United Kingdom, France and Germany who are responsible for overseeing technology deployments. Survey respondents come from enterprises with at least 500 employees in the United States, and at least 200 employees in the United Kingdom, France and Germany. The survey of 200 IT decision makers was conducted by Regina Corso Consulting online between August 26 and September 8, 2016. METHODOLOGY For more information or to access the report, visit: pingidentity.com/stateofiam 84%agree that IAM technologies have helped secure the partner 50% ONLY said it is the least important element to their digital transformation journey
