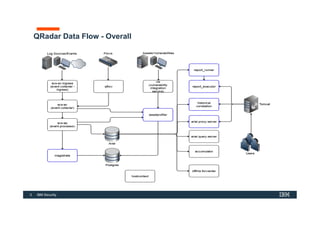
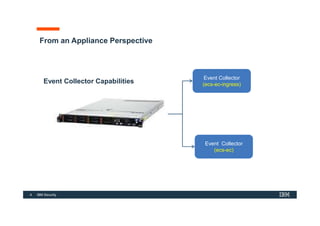
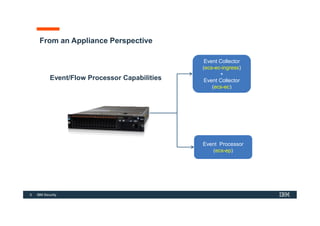
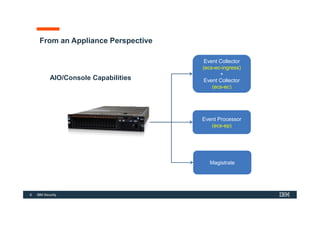
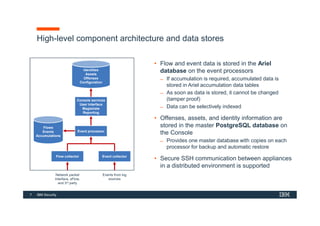
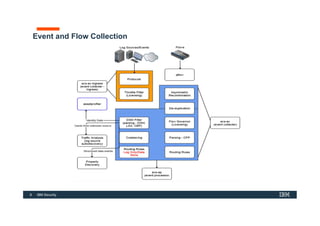
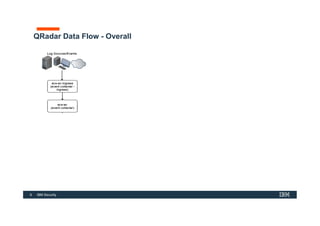
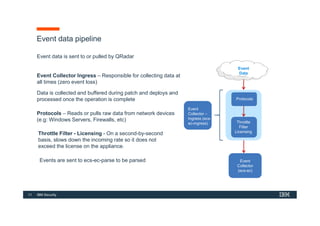
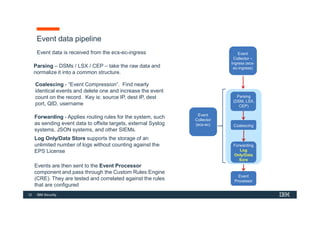
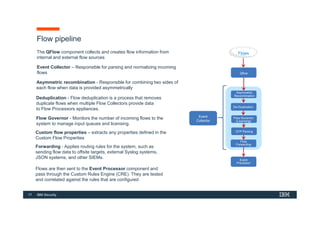
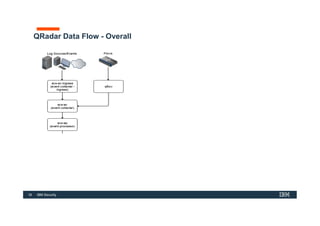
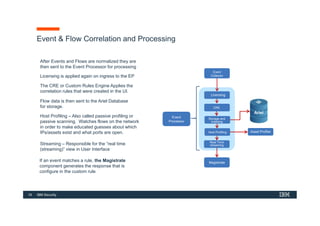
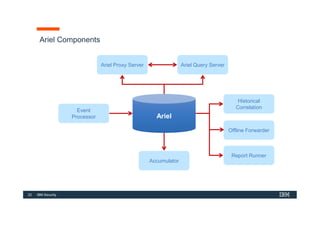
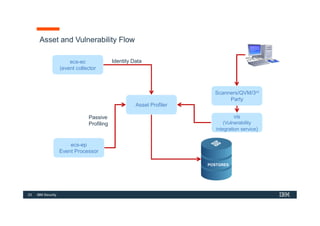
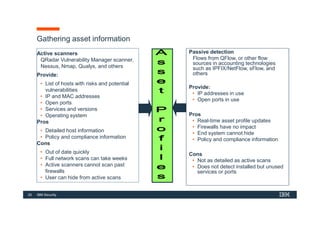
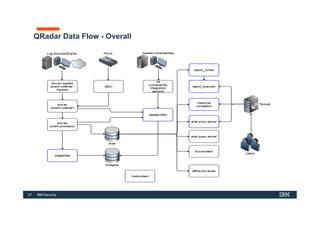
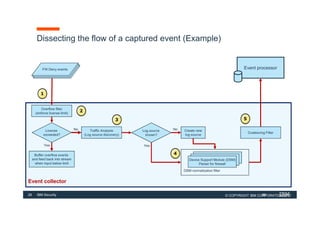
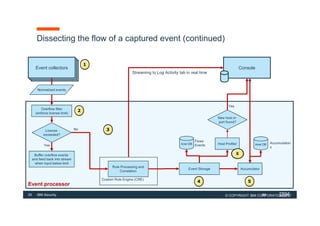
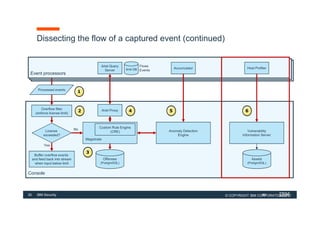
The document discusses how IBM QRadar collects and processes security data such as events and network flows. It describes the key components involved in data collection, normalization, storage, correlation and generation of offenses. Data flows through event collectors, event processors, databases and other components, and is correlated using custom rules to detect anomalies and security threats. The document provides an overview of QRadar's architecture and data flow.