The document outlines a hierarchical taxonomic framework for classifying cyber security incidents in industrial control systems, emphasizing completeness, clarity, and adaptability. It details the framework's characteristics, such as unambiguity and repeatability, and presents a comprehensive classification of 268 security incidents to inform threat intelligence. The paper serves as a resource for researchers, engineers, and students in the field of ICS cyber security.


![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
Declaration
3
Industrial Control System Security Taxonomic Framework
with Application to a Comprehensive Incidents Survey
International Journal of Critical Infrastructure Protection (Q1)
M. Mehdi Ahmadian, Dr. Mehdi Shajari, Ali Shafiee
https://doi.org/10.1016/j.ijcip.2020.100356
Received date: 12 August 2018
Revised date: 20 October 2019
Accepted date: 26 February 2020
Please cite this article as: Mohammad Mehdi Ahmadian , Mehdi Shajari , Mohammad Ali Shafiee , Industrial Control
System Security Taxonomic Framework with Application to a Comprehensive Incidents Survey, International Journal
of Critical Infrastructure Protection (2020), doi:https://doi.org/10.1016/j.ijcip.2020.100356 © 2020
[This presentation is based on preprint version]
Amirkabir University of Technology Information Security & E-Commerce lab. (ISEC)](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-3-320.jpg)








![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
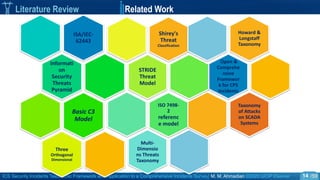
Literature Review Three Orthogonal Dimensional Classification Model
سد شکستن
St. Louis
(2005)
• Ruf et al [3].
16](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-16-320.jpg)
![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
Literature Review The STRIDE Threat Model [7]
سد شکستن
St. Louis
(2005)
17](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-17-320.jpg)
![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
Literature Review The Multi-Dimensions Threats Taxonomy
سد شکستن
St. Louis
(2005)
• Jouini et al. [9]
18](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-18-320.jpg)
![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
Literature Review Open & Comprehensive Framework for CPS Incidents
سد شکستن
St. Louis
(2005)
• Miller et al. [12, 13]
19](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-19-320.jpg)
![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
Literature Review Open & Comprehensive Framework for CPS Incidents
سد شکستن
St. Louis
(2005)
• Howard and Longstaff [10]
20
• For studying other related works refer to paper.](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-20-320.jpg)

![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
o Problem:
• There is an overlap between “threat” and “attack”.
• Most of the resources in related work were addressed threats and attacks, regardless of the exact
definition of these two categories and their differences
• Various information security literature has different definitions of security threat.
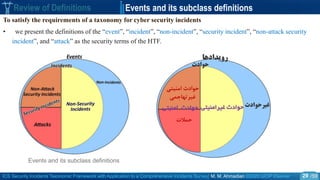
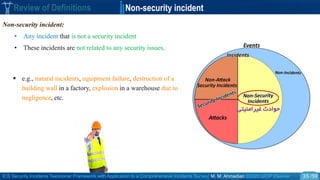
Review of Definitions Security Threat
o Generally, the security threat is anything that has the potential to cause damage to system assets.
“a threat is a potential cause of an unwanted incident, which may result in harm to a system or
organization”. [ISO / IEC 13335-1(2004) and ISO / IEC 27000(2016)]
“ potentially damaging action (intended or unintended) or capability (internal or external) to adversely
impact through a vulnerability is called a threat” [ISA/IEC-62443 ].
“a threat is a potential violation of security” [Bishop 2005 ].
22](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-22-320.jpg)
![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
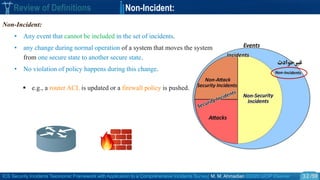
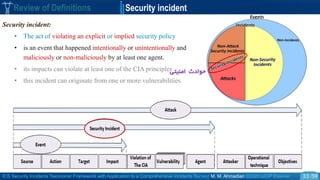
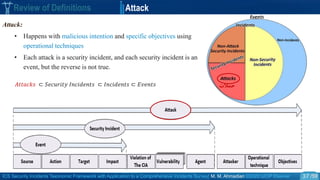
Review of Definitions Security Threat Vs. Attack
o Security Threat and attack in the HTF :
• “a threat is a potential violation of security [Bishop 2005 ]”
The violation needs not actually to occur to be a threat.
The fact that the violation might occur means that those actions could cause it to occur
must be guarded against (or prepared for); these actions are called attacks.
23](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-23-320.jpg)








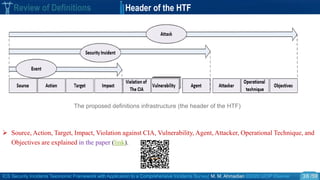



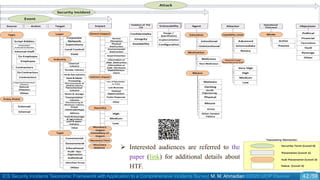
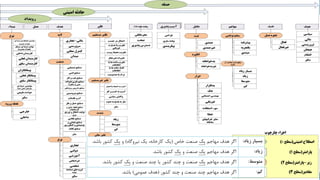

![ICS Security Incidents Taxonomic Framework with Application to a Comprehensive Incidents Survey| M. M. Ahmadian ©2020 IJCIP Elsevier /59
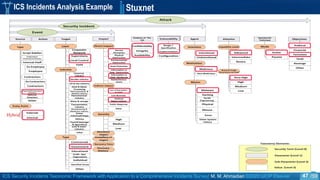
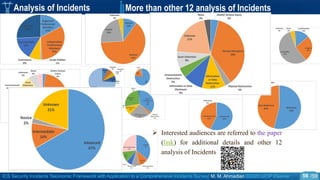
ICS Incidents Analysis Example
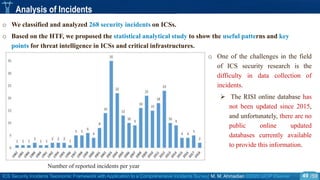
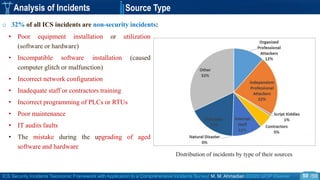
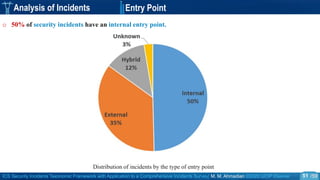
o We collected the most important publicly available ICS incidents.
• ICS-Cert , Bitdefender , Symantec , Securelist , Securityweek , Computerworld , Repository of
Industrial Security Incidents (RISI ) online database, Idaho National Laboratory , and some articles
such as [18] and [19].
o The dataset covers 268 ICS security incidents publicly reported to have affected process control or
industrial automation in SCADA or DCS systems within the period of 1982 to 2018.
o In the analysis, we add two other parameters:
• Credibility of the Information
• (1) cannot be determined, (2) improbable, (3) doubtful, (4) possibly true, (5) probably true, and (6)
confirmed
• Amount of Technical Information Available:
• (1) no specifics, (2) high-level summary only, (3) some details, (4) many details, (5) extensive details, and
(6) comprehensive details with supporting evidence.
45](https://image.slidesharecdn.com/ahmadianicssecuritytaxonomicframeworkijcipelsevier99040122-200820063927/85/slide-44-320.jpg)