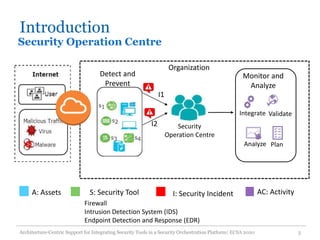
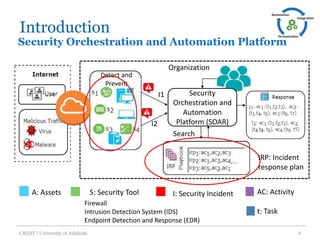
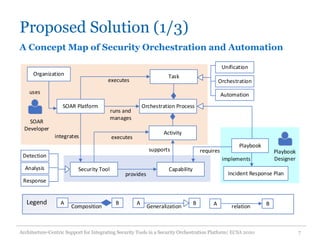
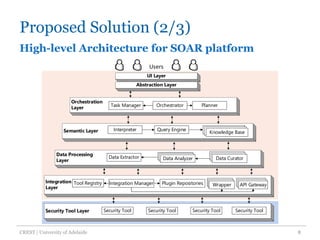
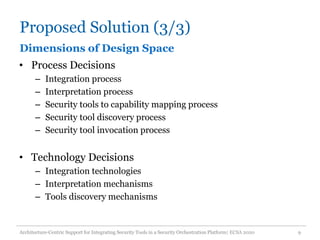
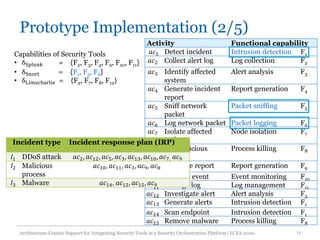
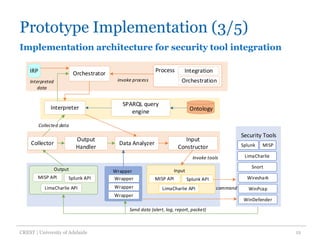
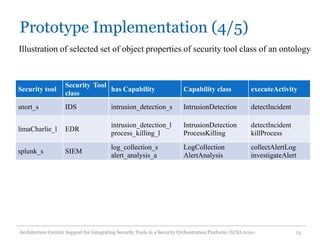
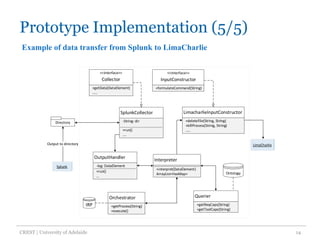
The document discusses an architecture-centric approach for integrating security tools into a security orchestration platform to enhance agility and modularity. It outlines the challenges faced by existing platforms and proposes a layered architecture that supports automation and integration processes for incident response. Additionally, the authors present a prototype implementation showcasing the capabilities of various security tools and suggest future work for deployment automation and large-scale mapping.