Is Your Mobile Workforce Beach Ready? - SAP Infographic
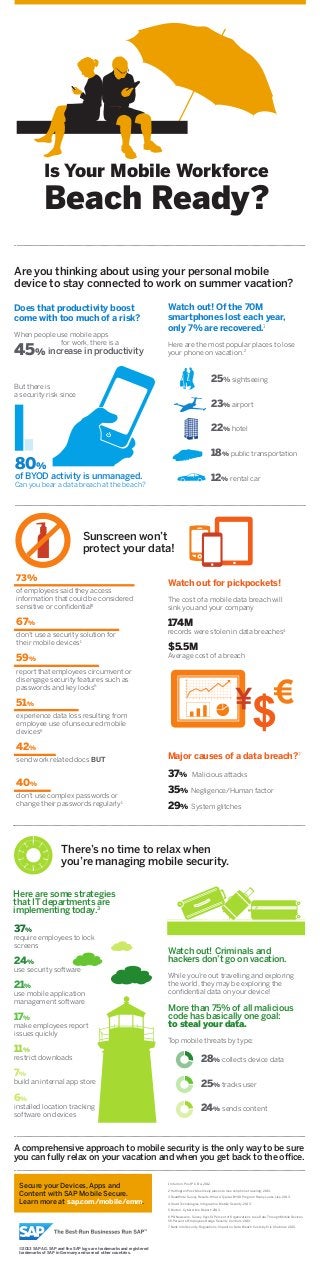
- 1. Is Your Mobile Workforce Beach Ready? Are you thinking about using your personal mobile device to stay connected to work on summer vacation? Does that productivity boost come with too much of a risk? When people use mobile apps for work, there is a 45% increase in productivity Watch out! Of the 70M smartphones lost each year, only 7% are recovered.1 Here are the most popular places to lose your phone on vacation.2 25% sightseeing But there is a security risk since 23% airport 22% hotel 18% public transportation 80% 12% rental car of BYOD activity is unmanaged. Can you bear a data breach at the beach? Sunscreen won’t protect your data! 73% of employees said they access information that could be considered sensitive or confidential8 67% Watch out for pickpockets! The cost of a mobile data breach will sink you and your company 174M don’t use a security solution for their mobile devices1 records were stolen in data breaches4 59% Average cost of a breach $5.5M report that employees circumvent or disengage security features such as passwords and key locks6 51% experience data loss resulting from employee use of unsecured mobile devices6 42% send work related docs BUT Major causes of a data breach?7 37% 40% don’t use complex passwords or change their passwords regularly1 Malicious attacks 35% Negligence/Human factor 29% System glitches There’s no time to relax when you’re managing mobile security. Here are some strategies that IT departments are implementing today.3 37% require employees to lock screens 24% use security software Watch out! Criminals and hackers don’t go on vacation. 21% While you’re out travelling and exploring the world, they may be exploring the confidential data on your device! 17% More than 75% of all malicious code has basically one goal: to steal your data. use mobile application management software make employees report issues quickly 11% restrict downloads 7% build an internal app store 6% installed location tracking software on devices Top mobile threats by type: 28% collects device data 25% tracks user 24% sends content A comprehensive approach to mobile security is the only way to be sure you can fully relax on your vacation and when you get back to the office. Secure your Devices, Apps and Content with SAP Mobile Secure. Learn more at sap.com/mobile/emm. 1 Intuition, Post PC Era; 2012. 2 Huffington Post, Most likely places to lose cell phone traveling; 2013. 3 ReadWrite Survey Results: What A Typical BYOD Program Really Looks Like, 2013. 4 Savid Technologies, Infographic: Mobile Security, 2013. 5 Norton, Cybercrime Report; 2013. 6 PR Newswire, Survey Says 51 Percent of Organizations Lose Data Through Mobile Devices, 59 Percent of Employees Dodge Security Controls; 2013. 7 Bank Info Security, Regulations' Impact on Data Breach Costs by Eric Chabrow; 2013. ©2013 SAP AG. SAP and the SAP logo are trademarks and registered trademarks of SAP in Germany and several other countries.
