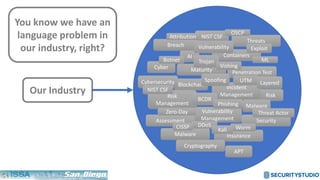
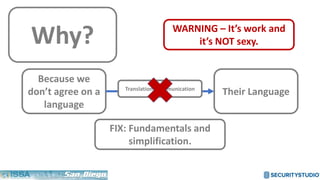
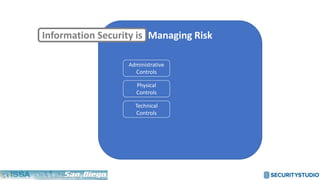
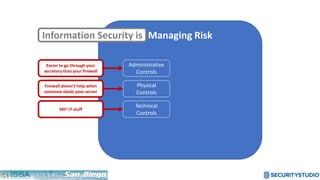
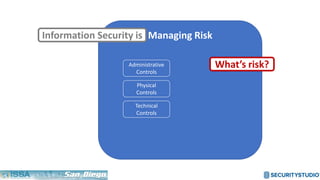
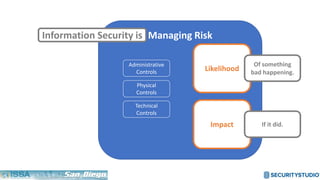
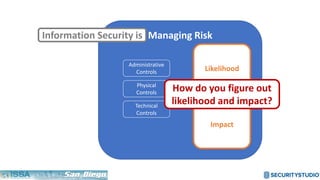
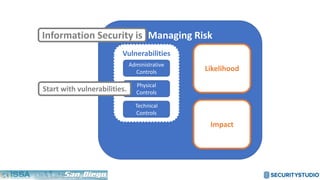
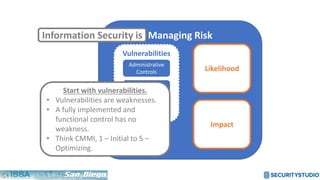
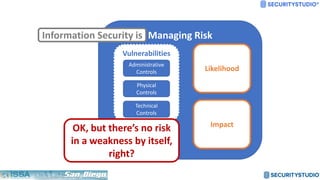
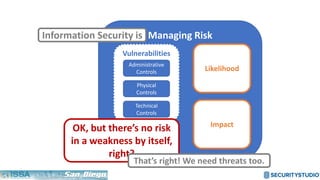
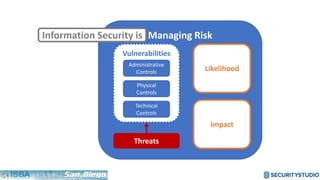
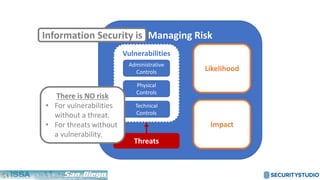
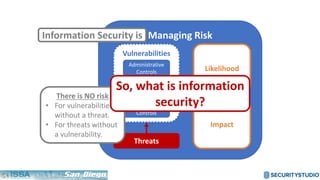
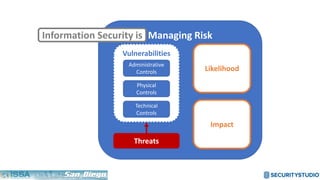
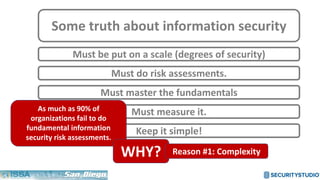
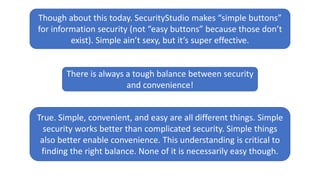
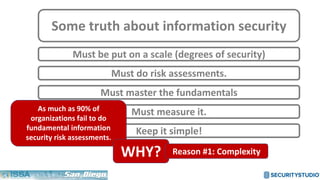
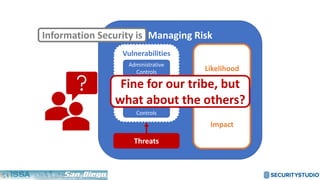
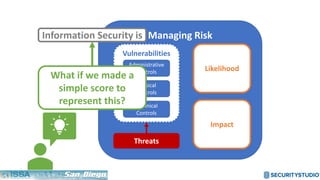
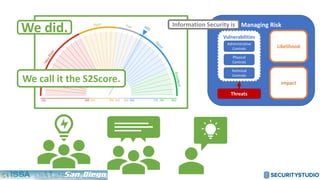
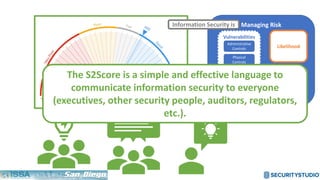
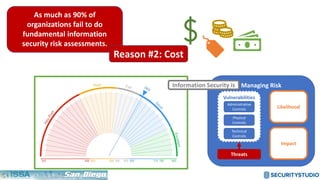
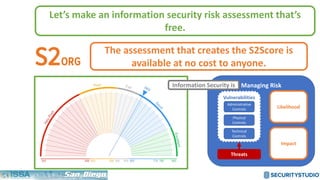
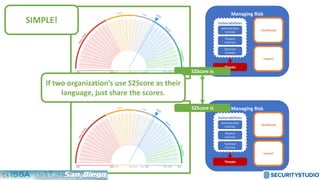
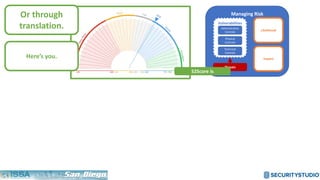
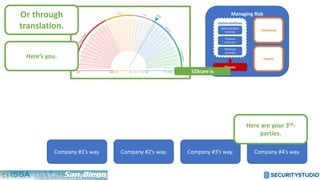
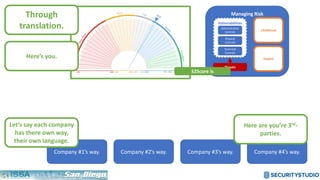
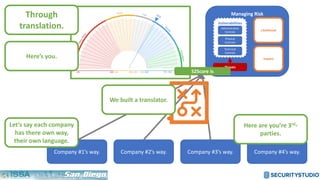
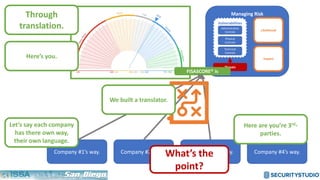
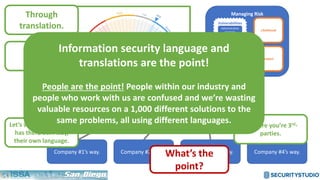
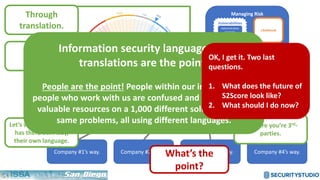
The document discusses solving the language problem in information security. It begins by explaining that information security is about managing risk by assessing threats and vulnerabilities, and using administrative, physical, and technical controls. It then introduces the S2Score as a simple scoring system to communicate security in a common language. The document advocates for making security assessments free and accessible to all, and developing translation tools to map different organizations' risk scoring systems to a common scale. The overall goal is to establish a shared security language to improve understanding and coordination across the industry.