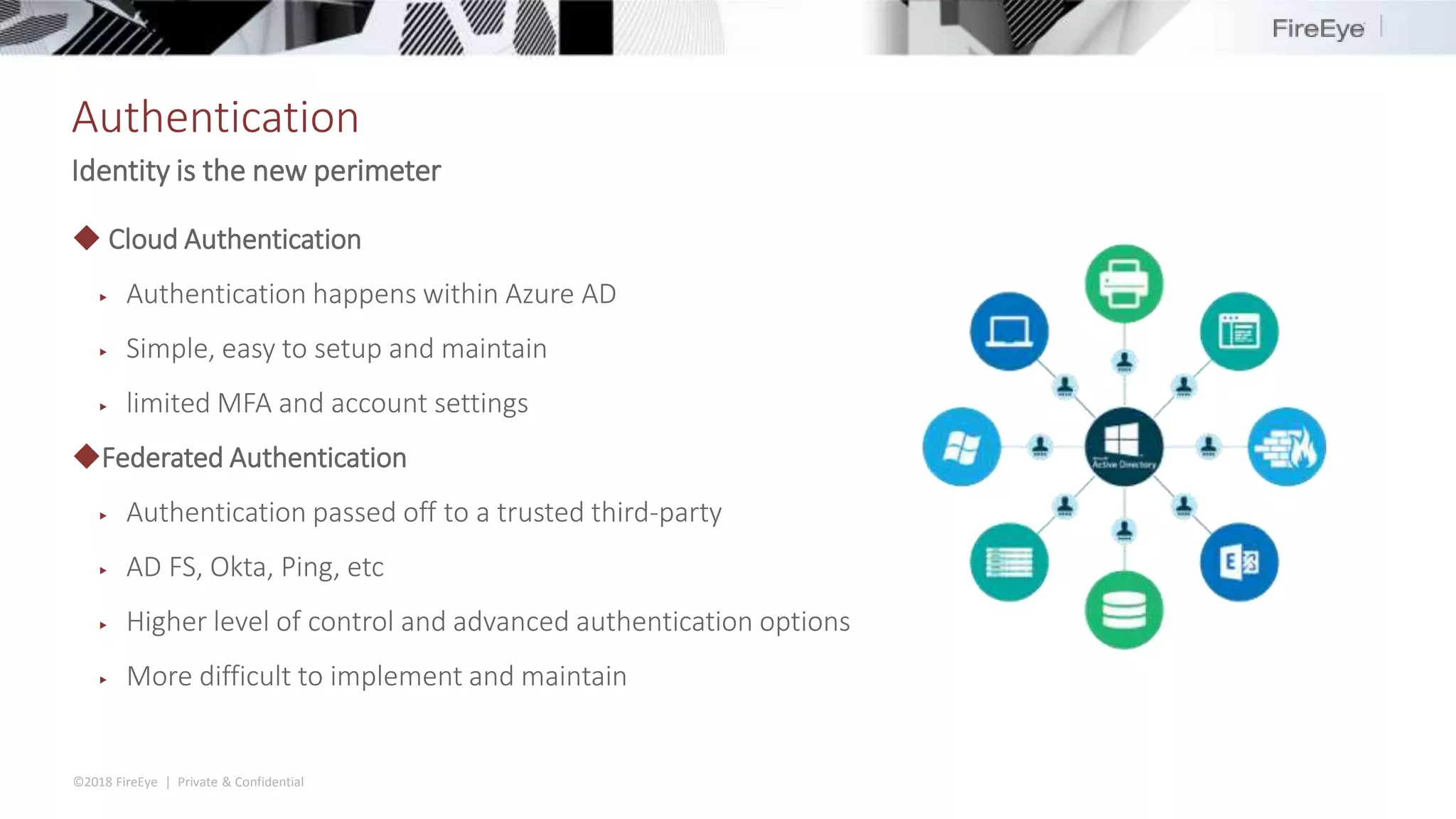
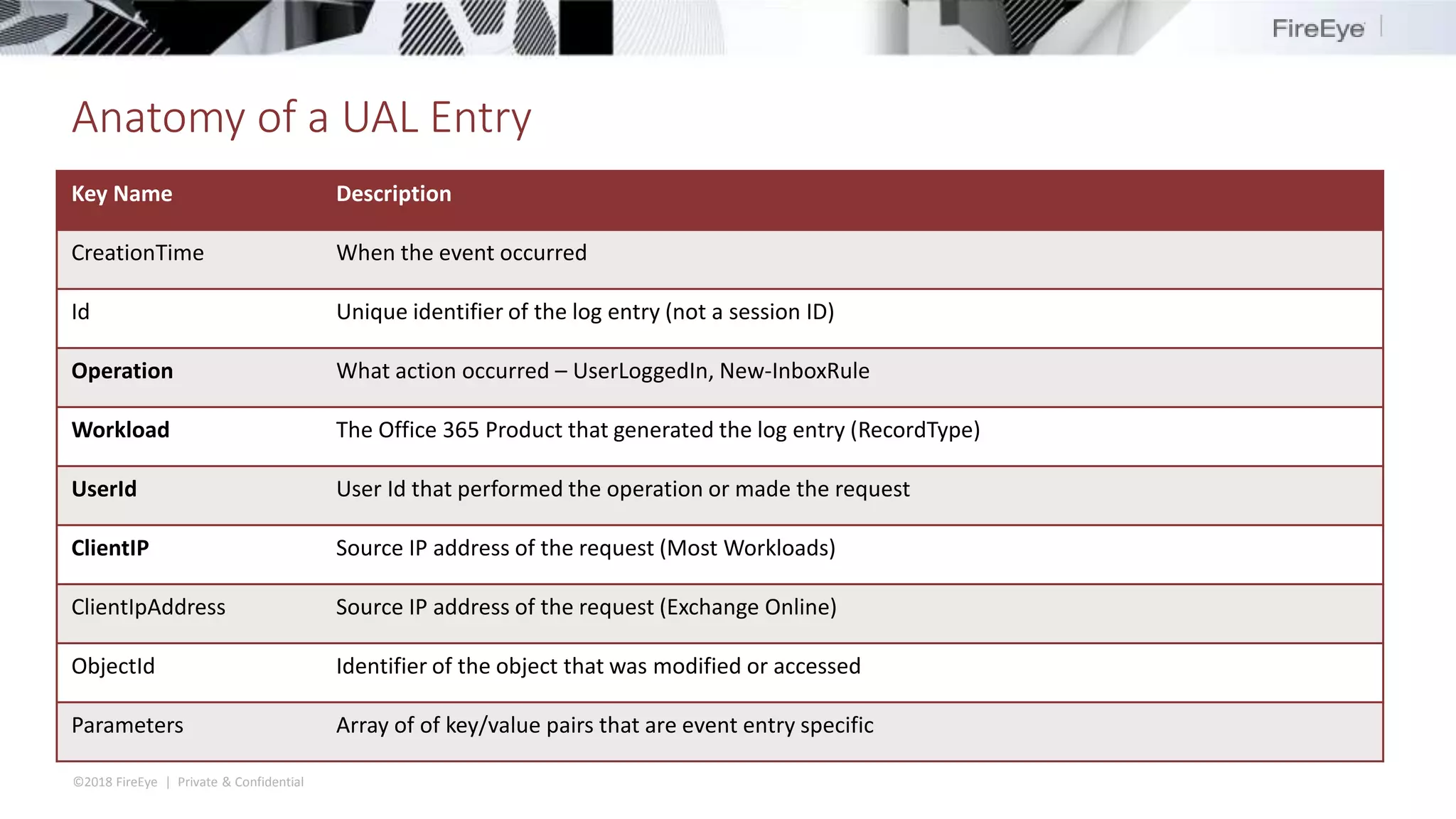
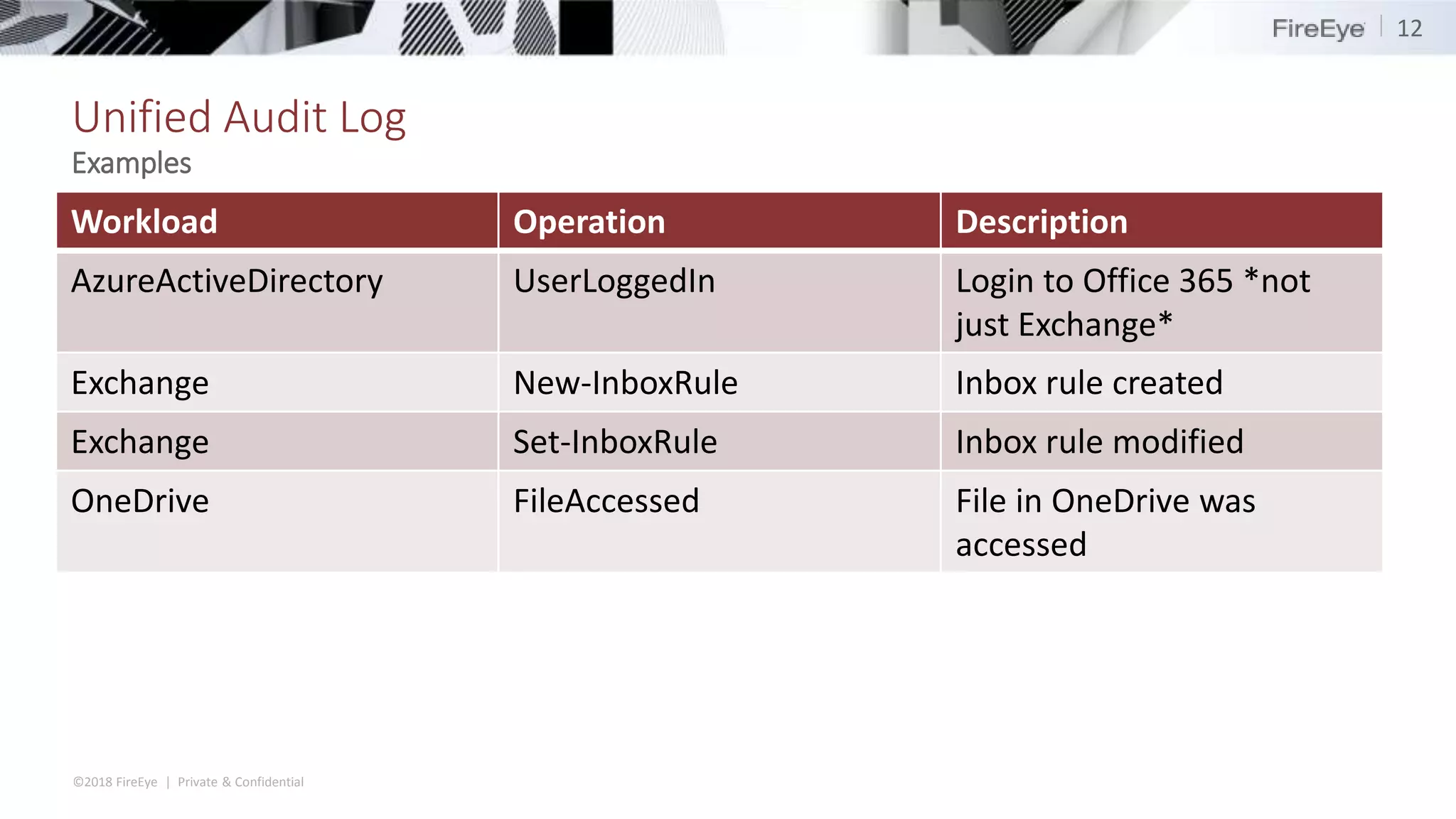
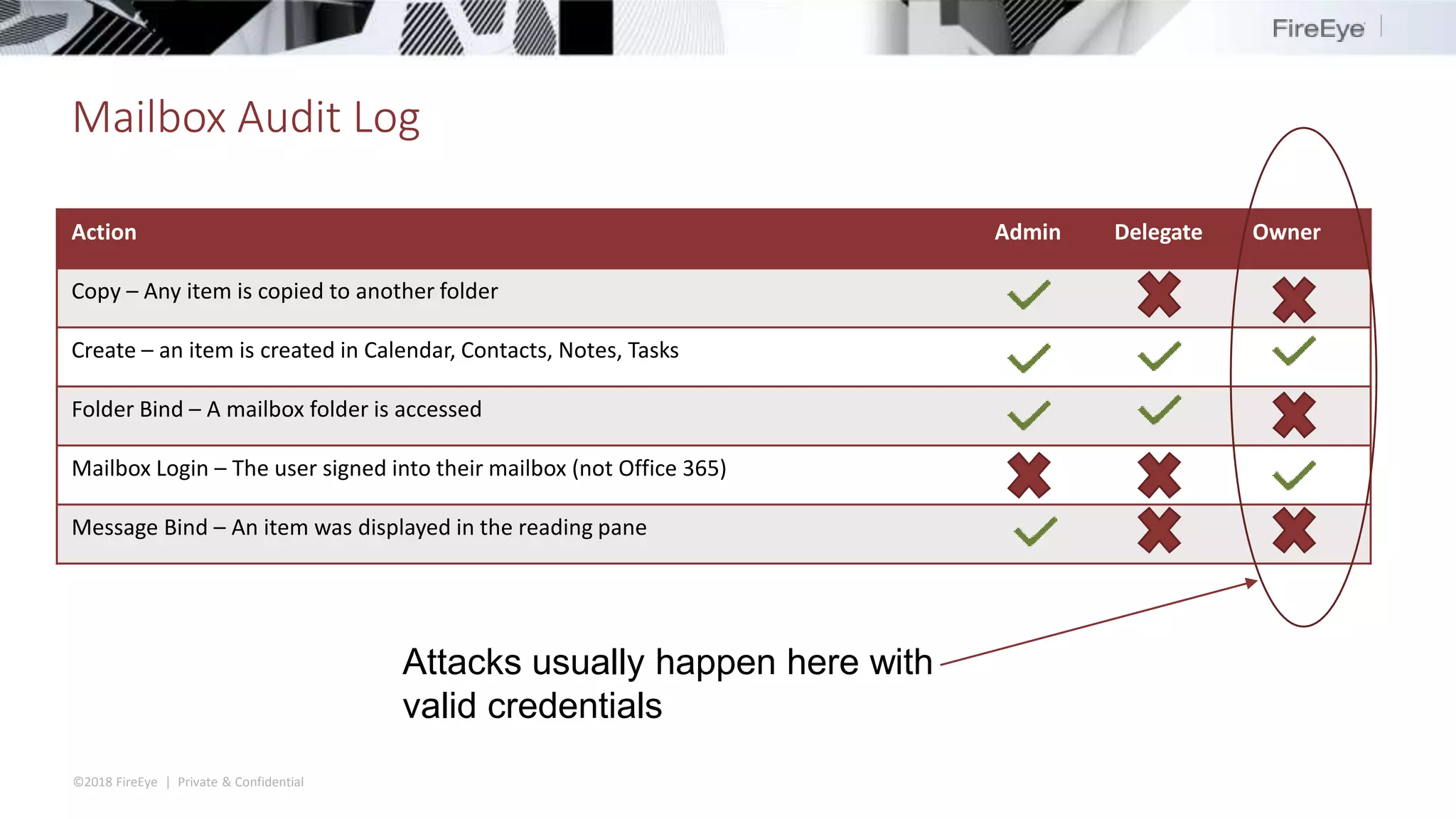
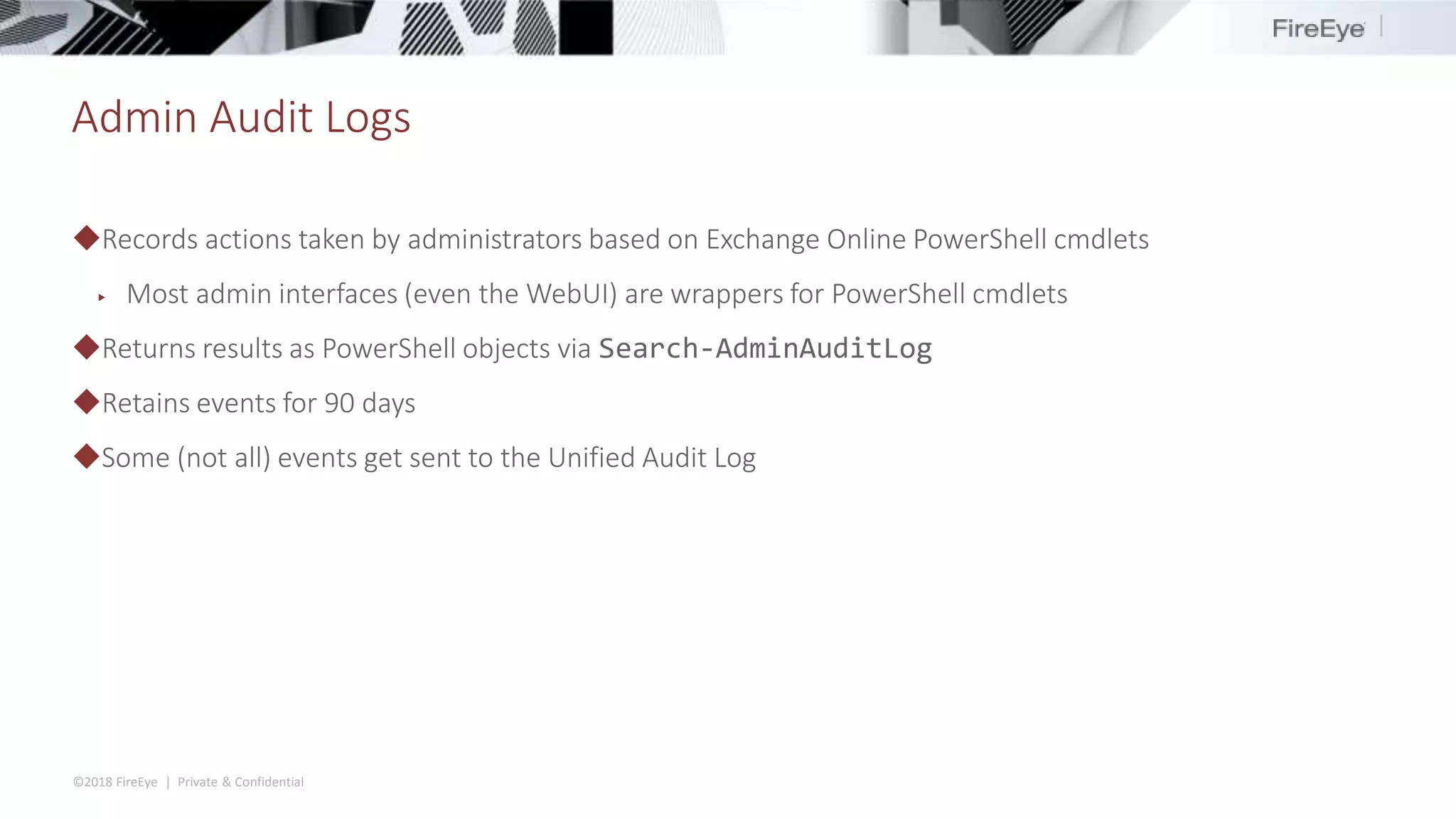
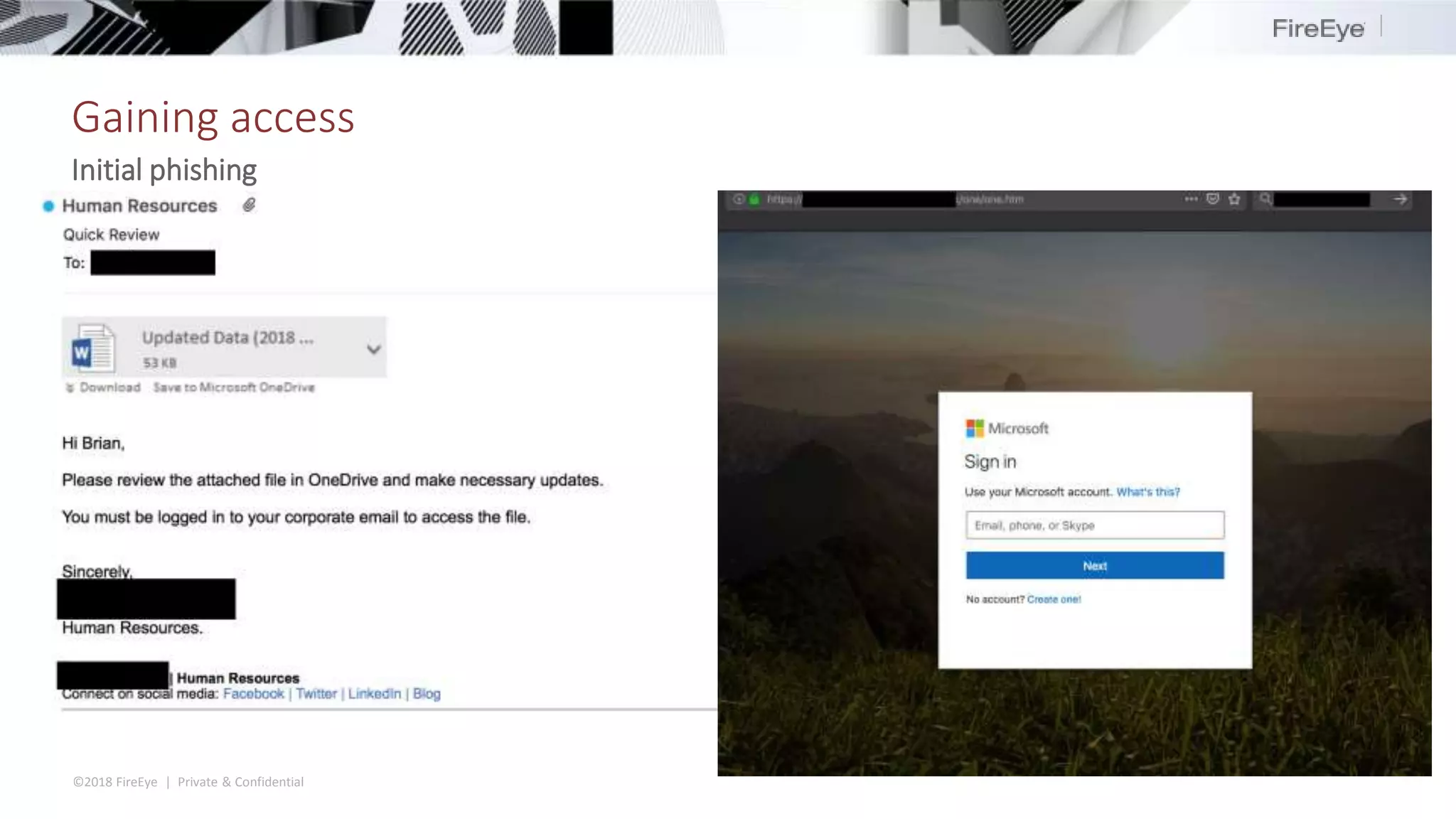
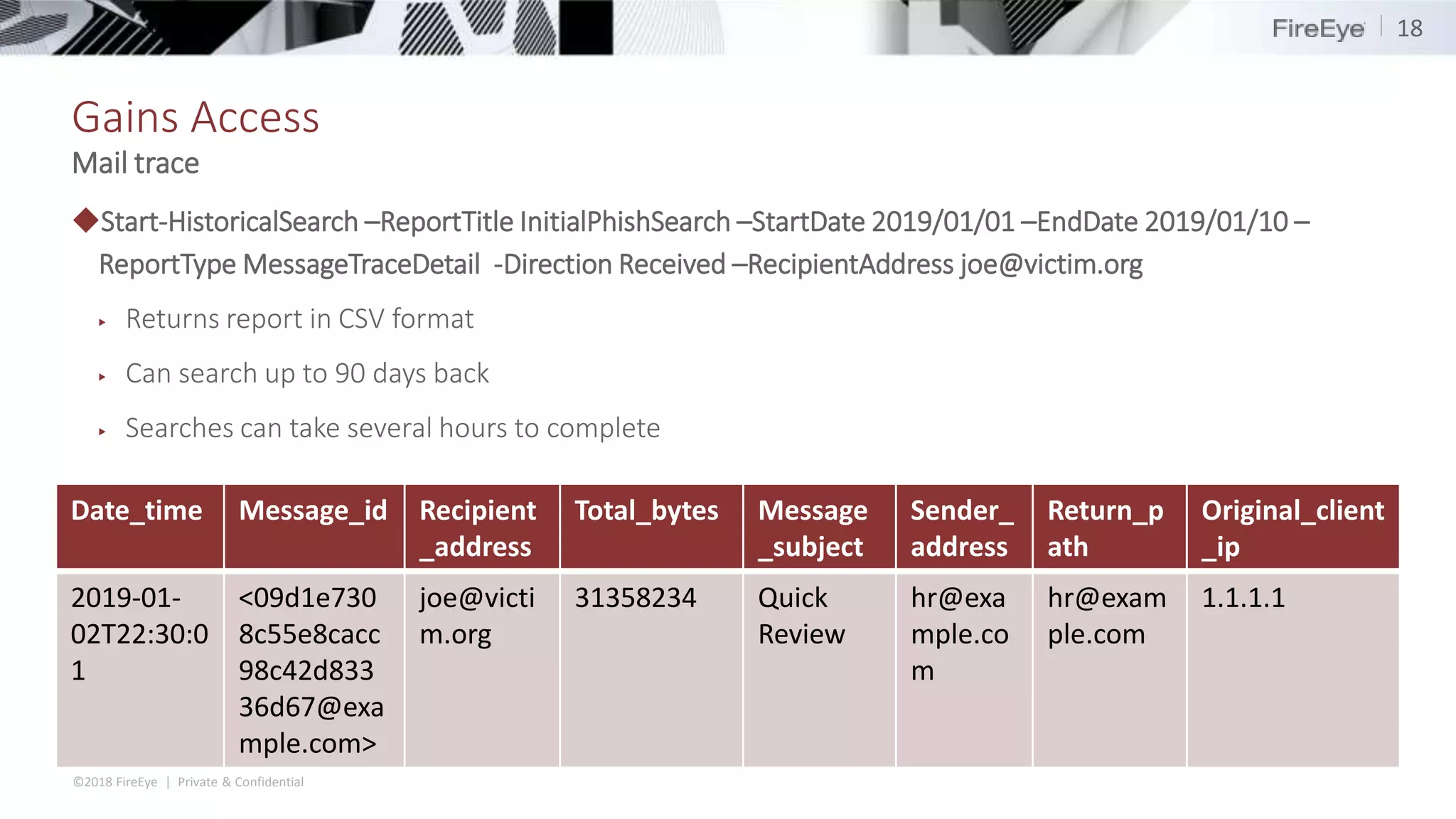
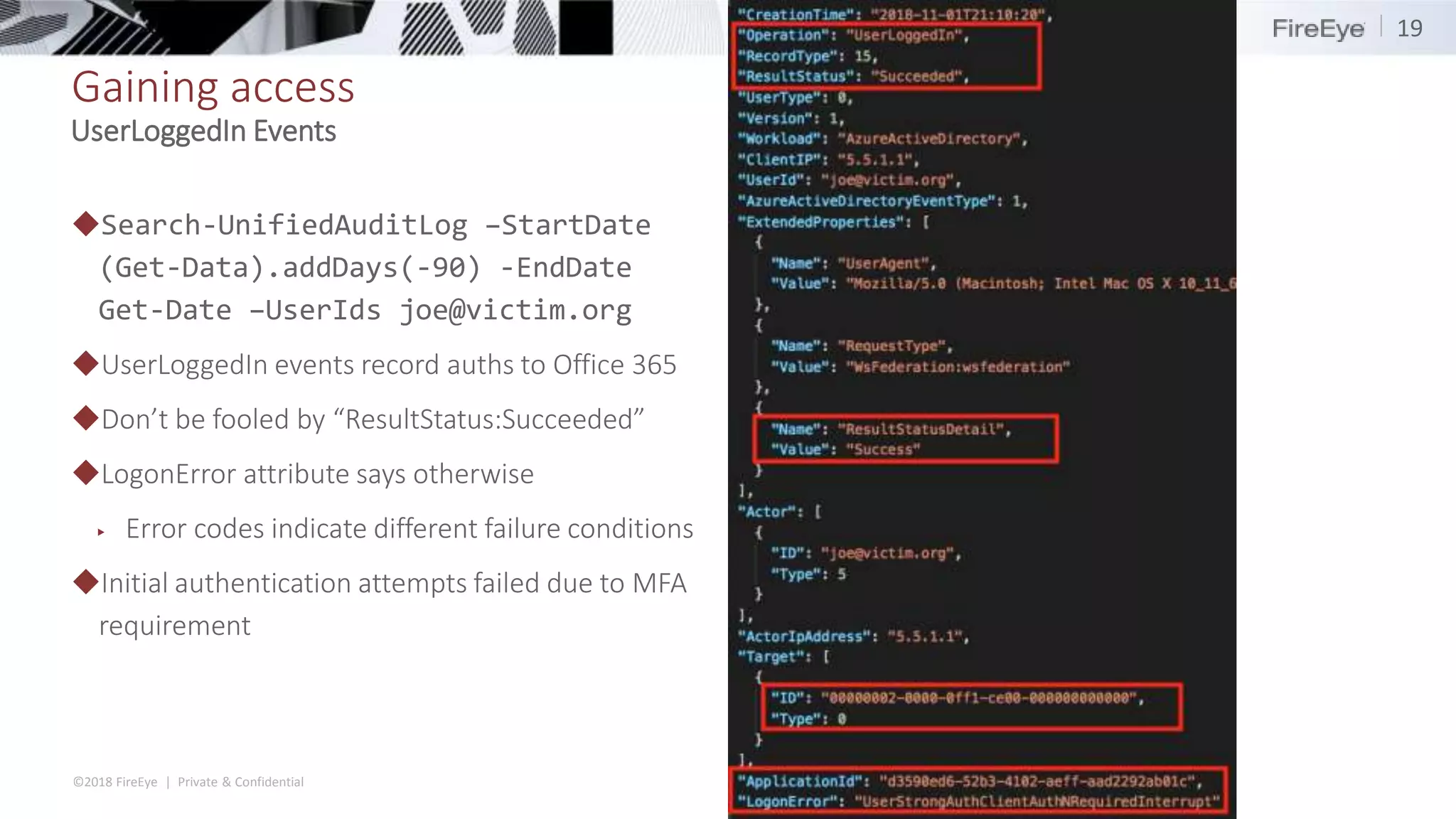
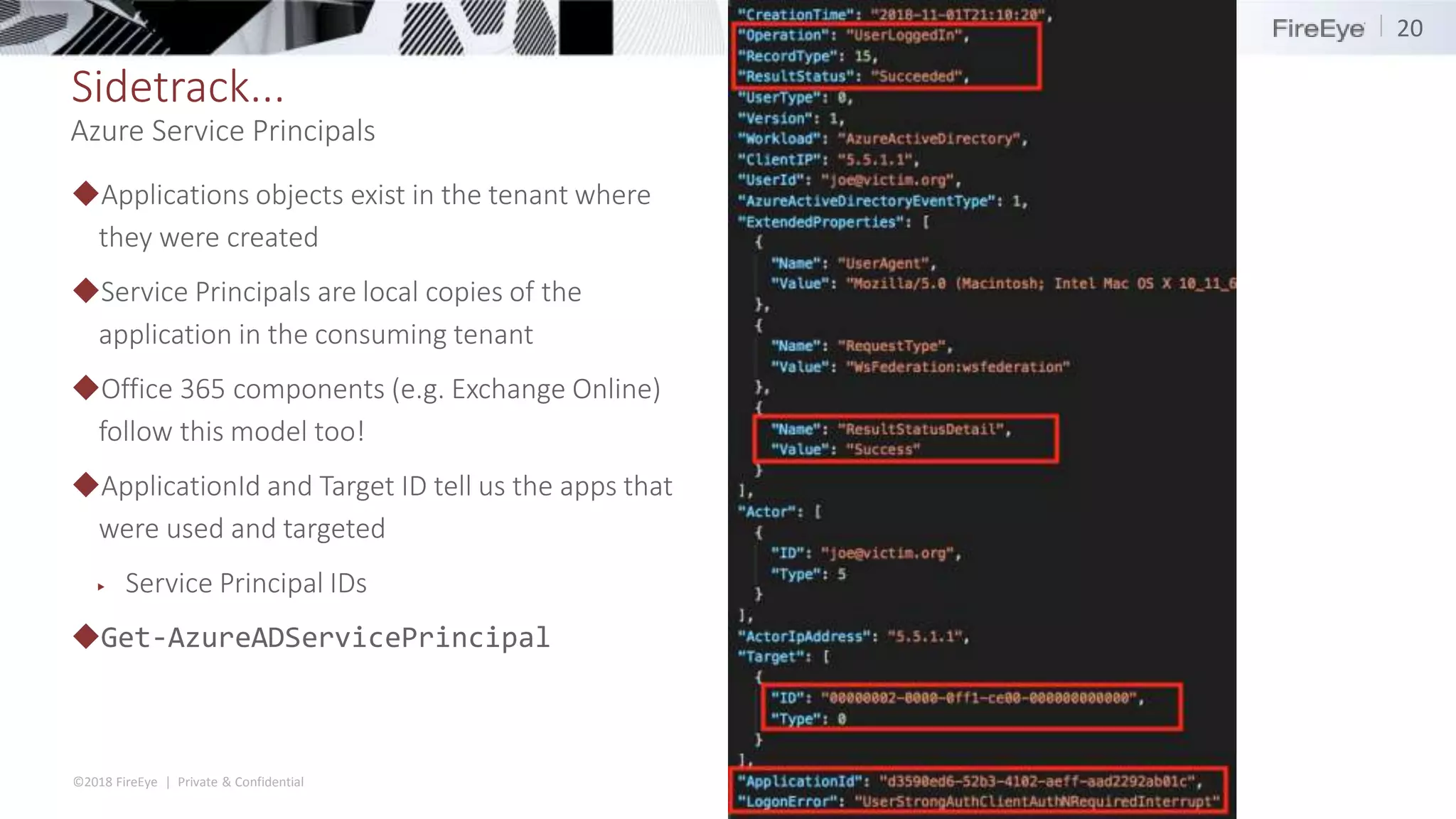
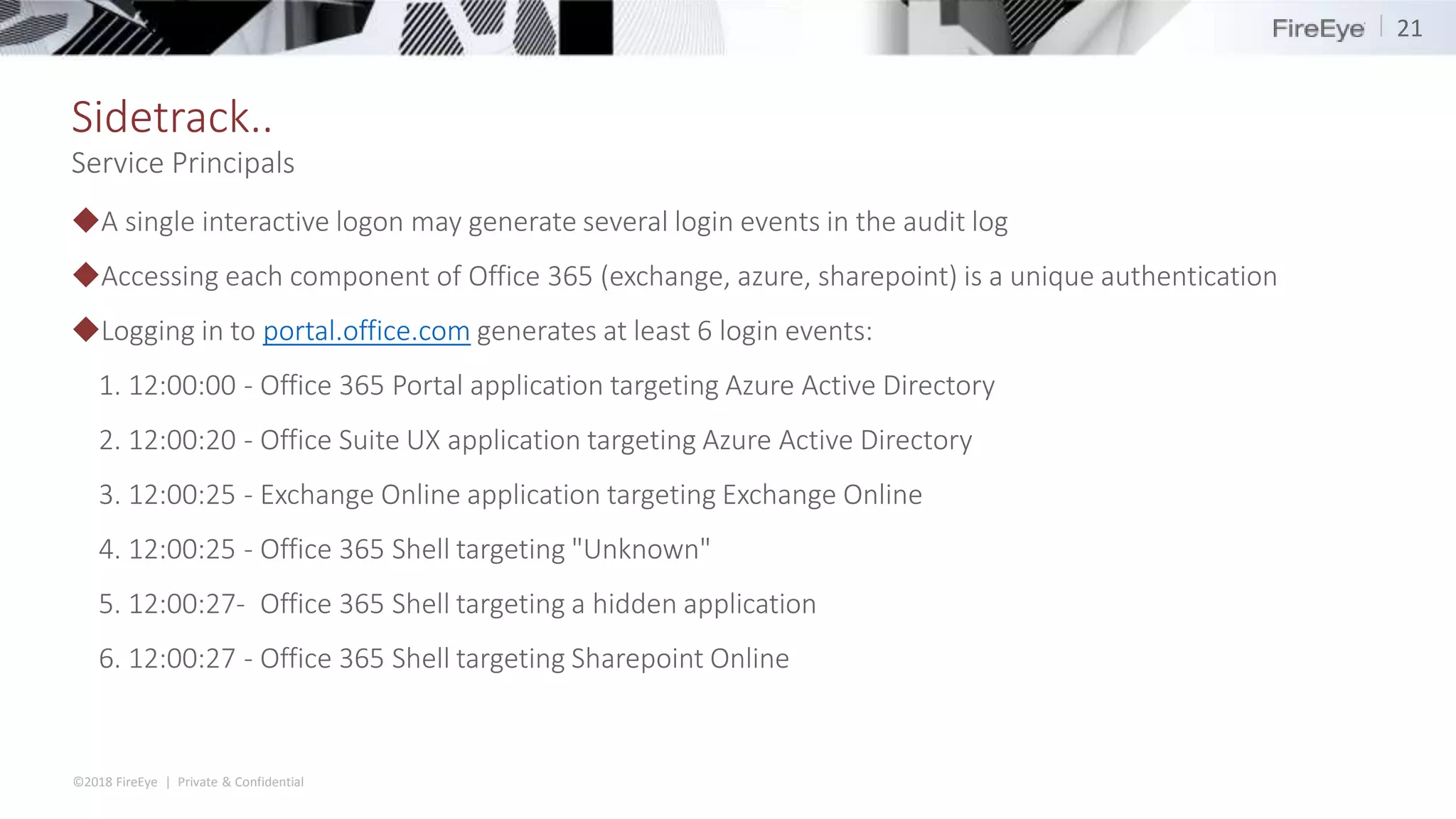
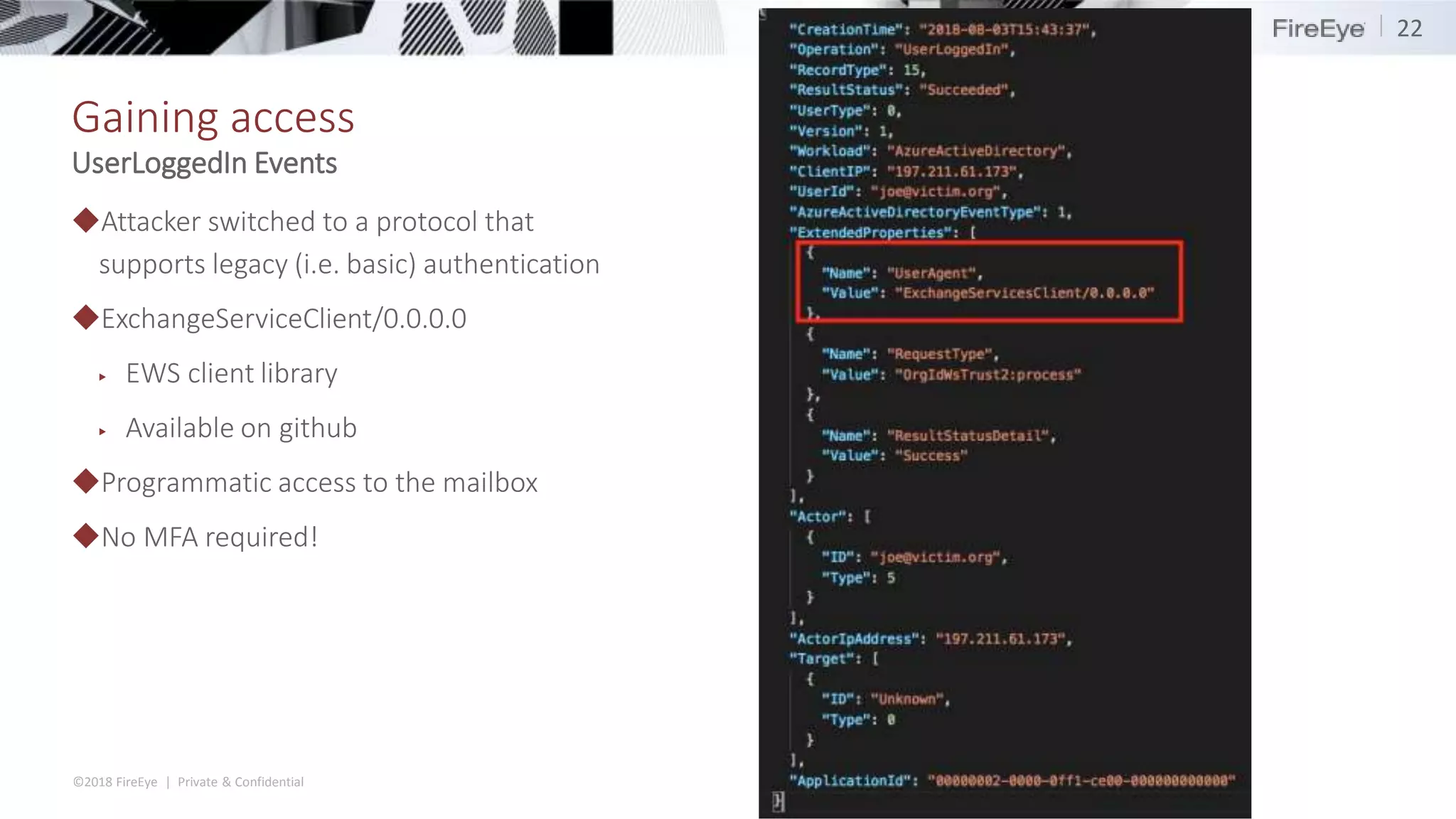
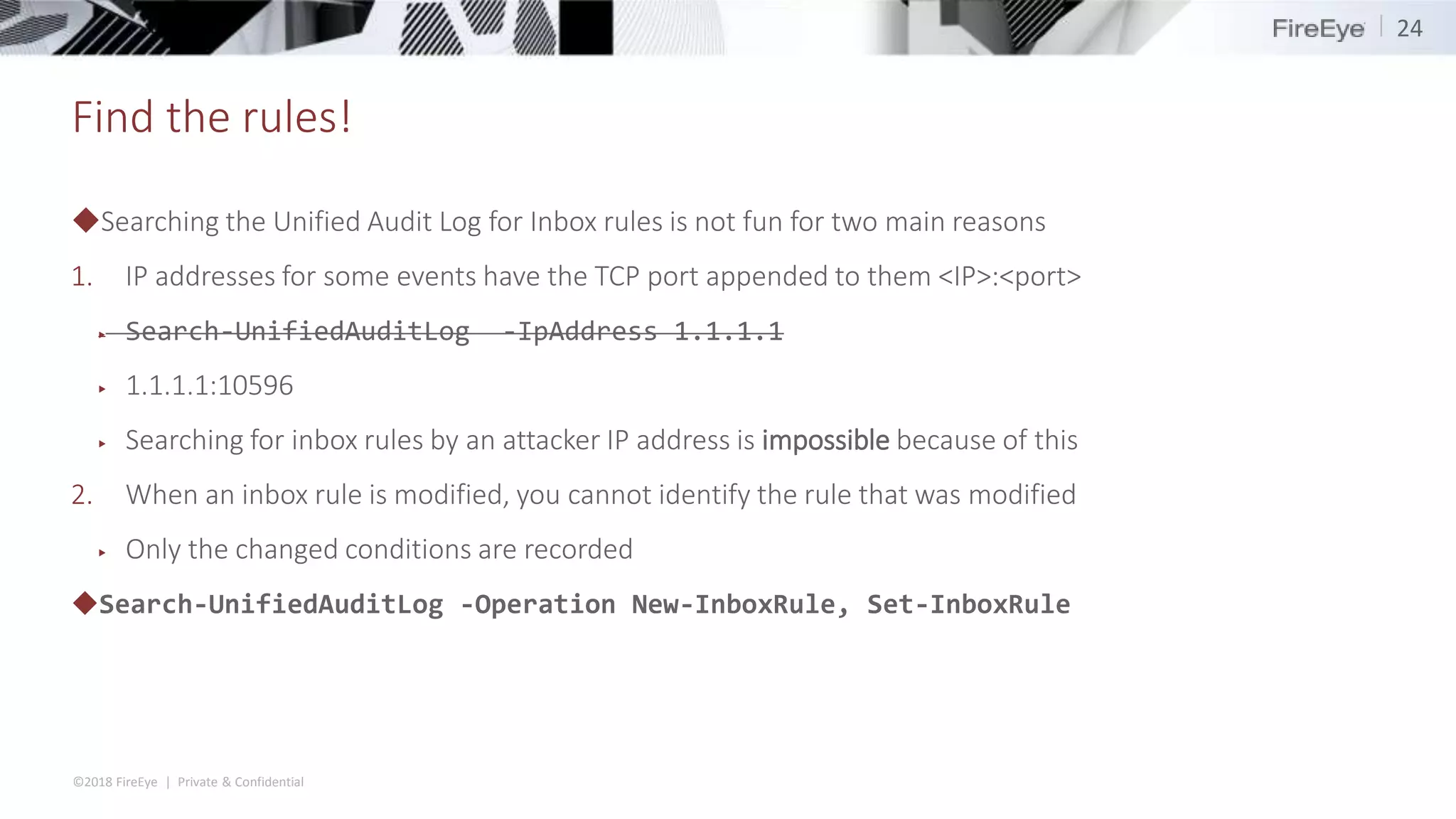
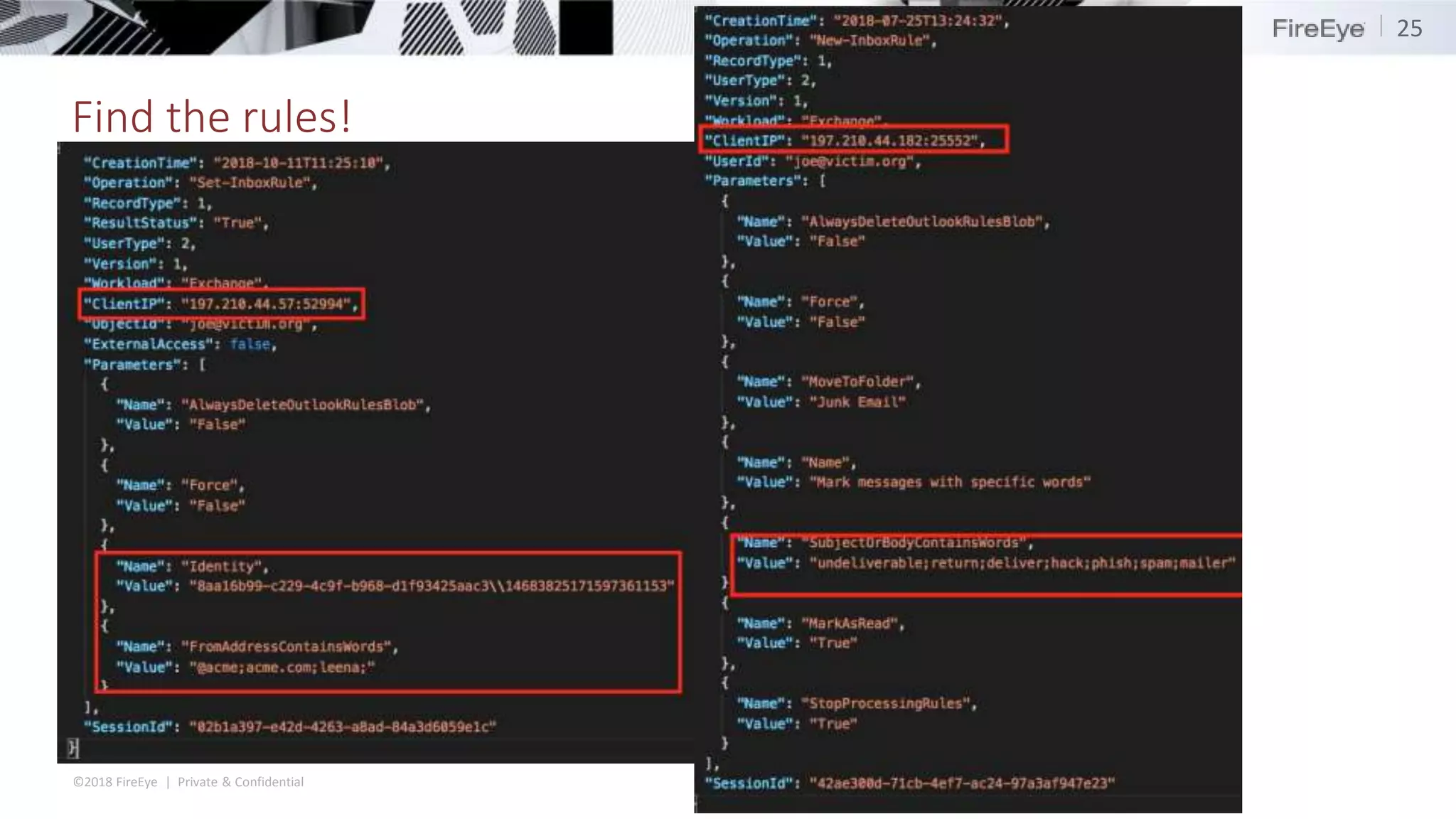
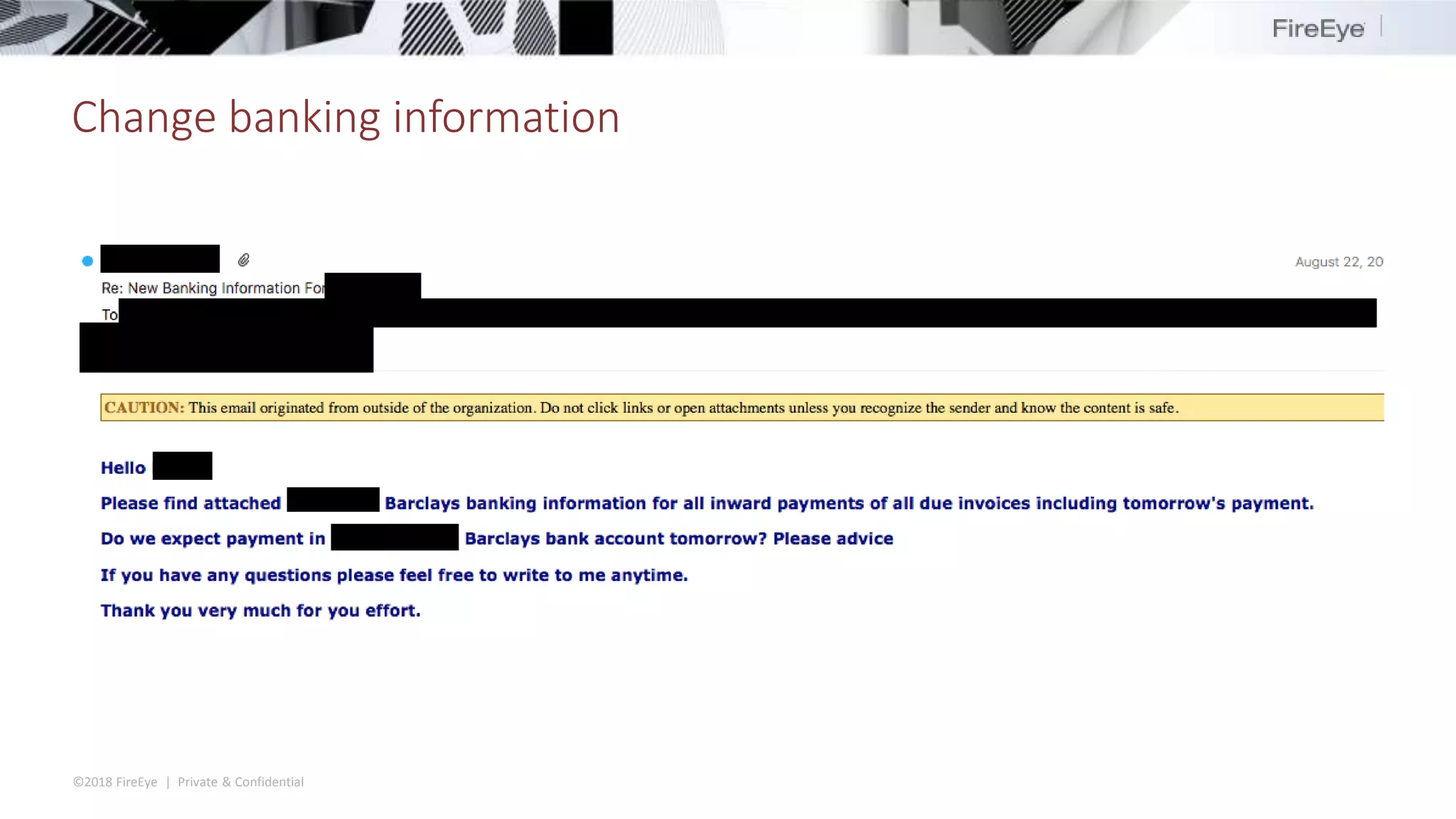
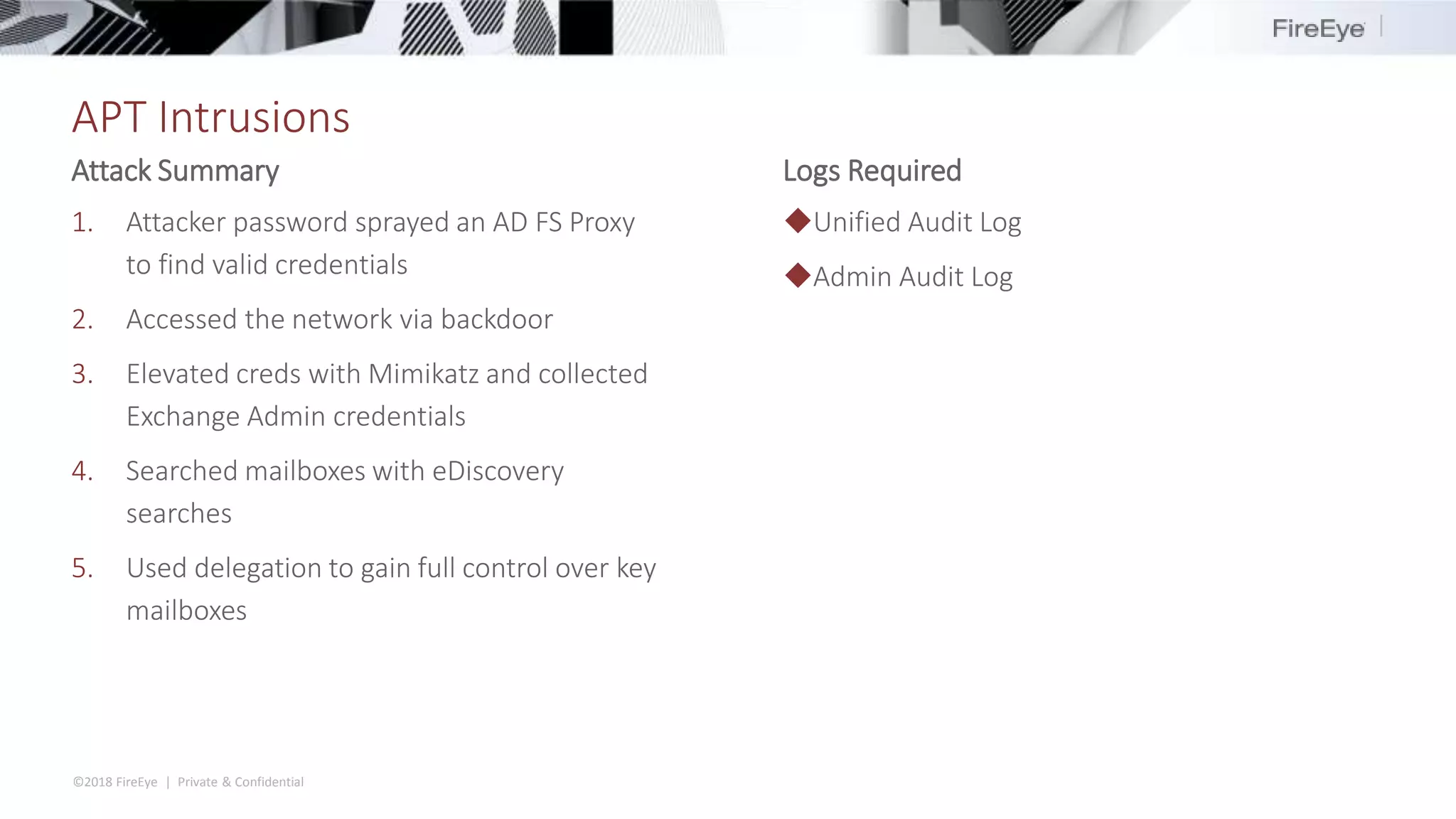
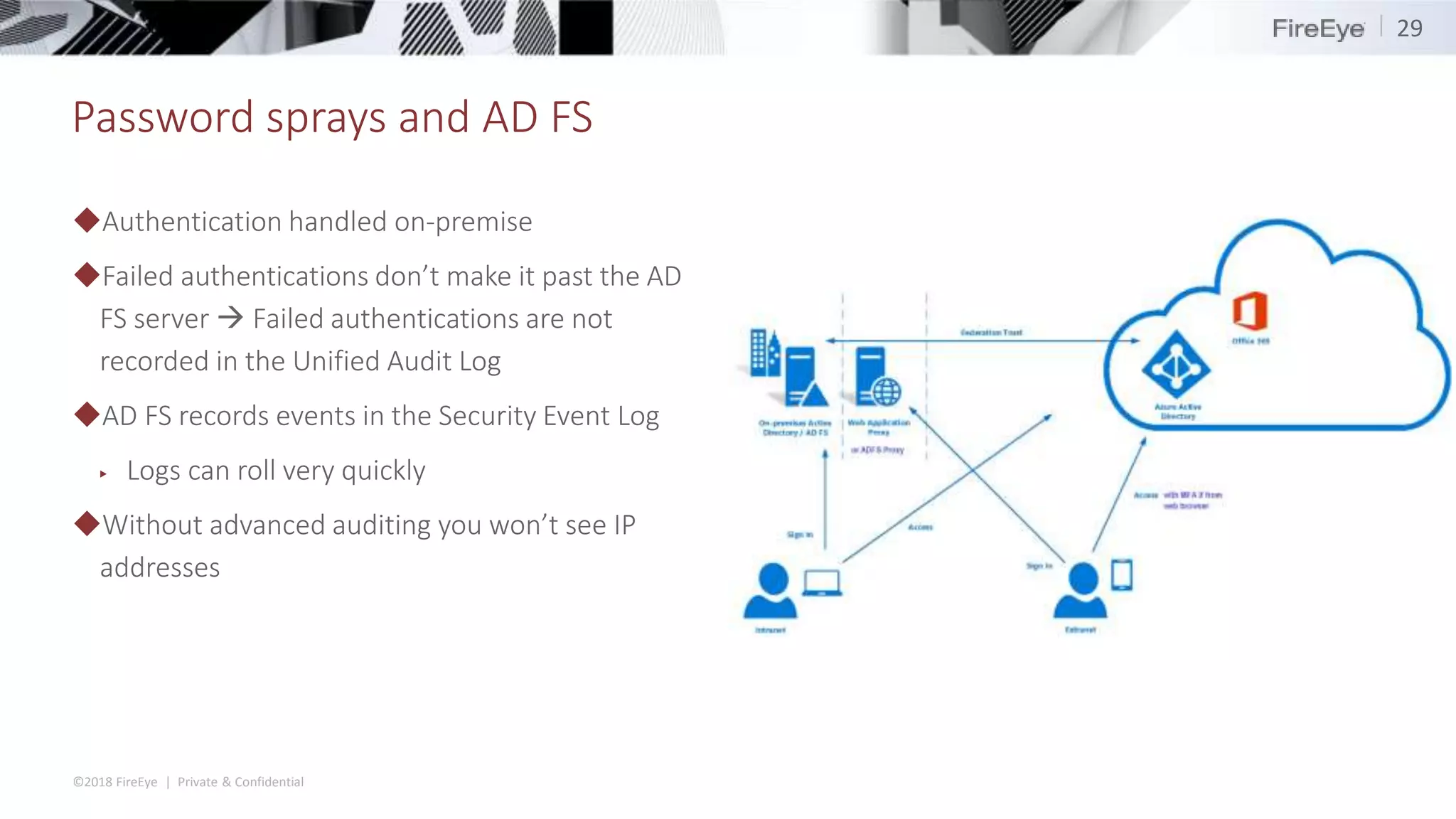
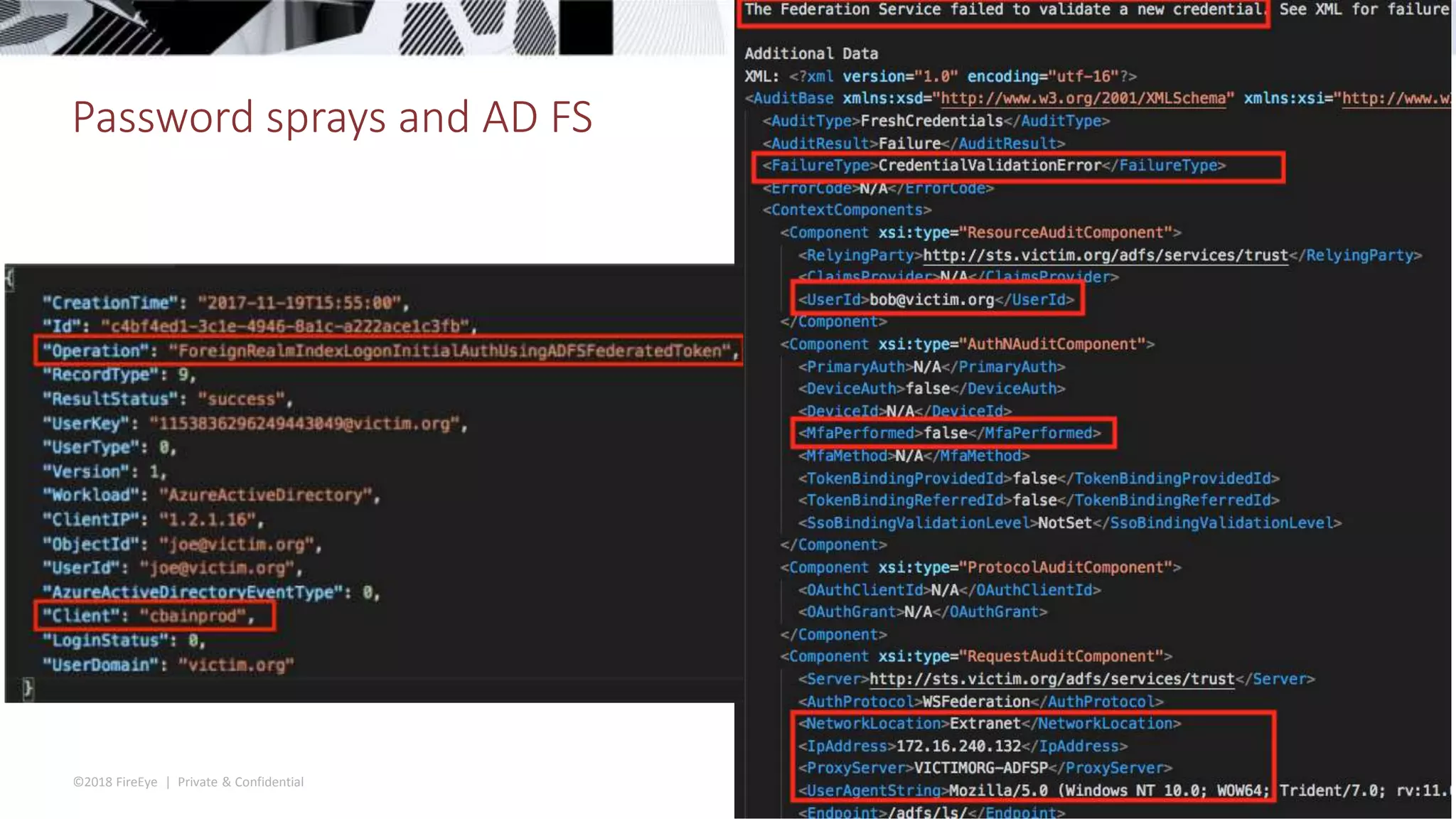
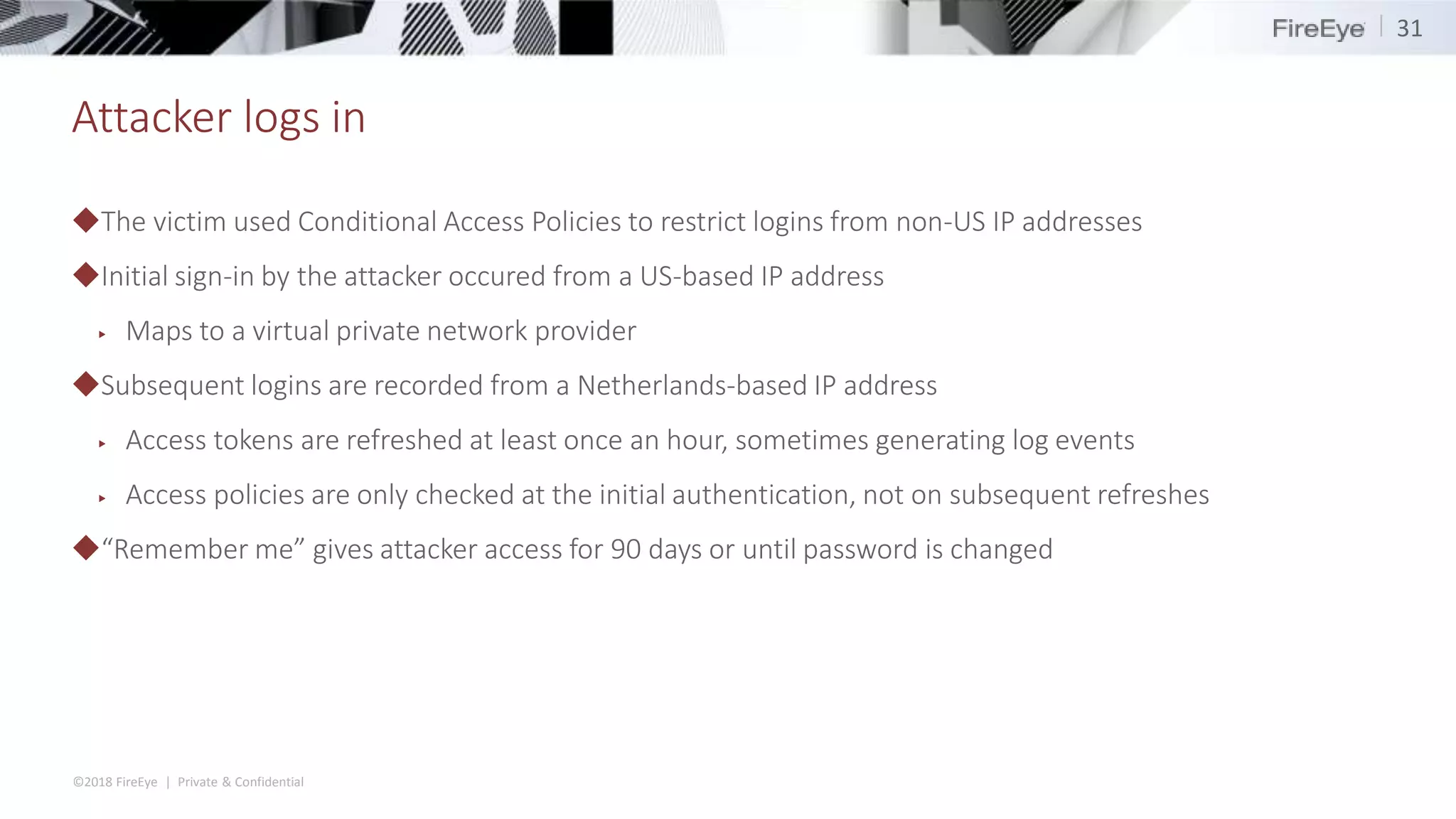
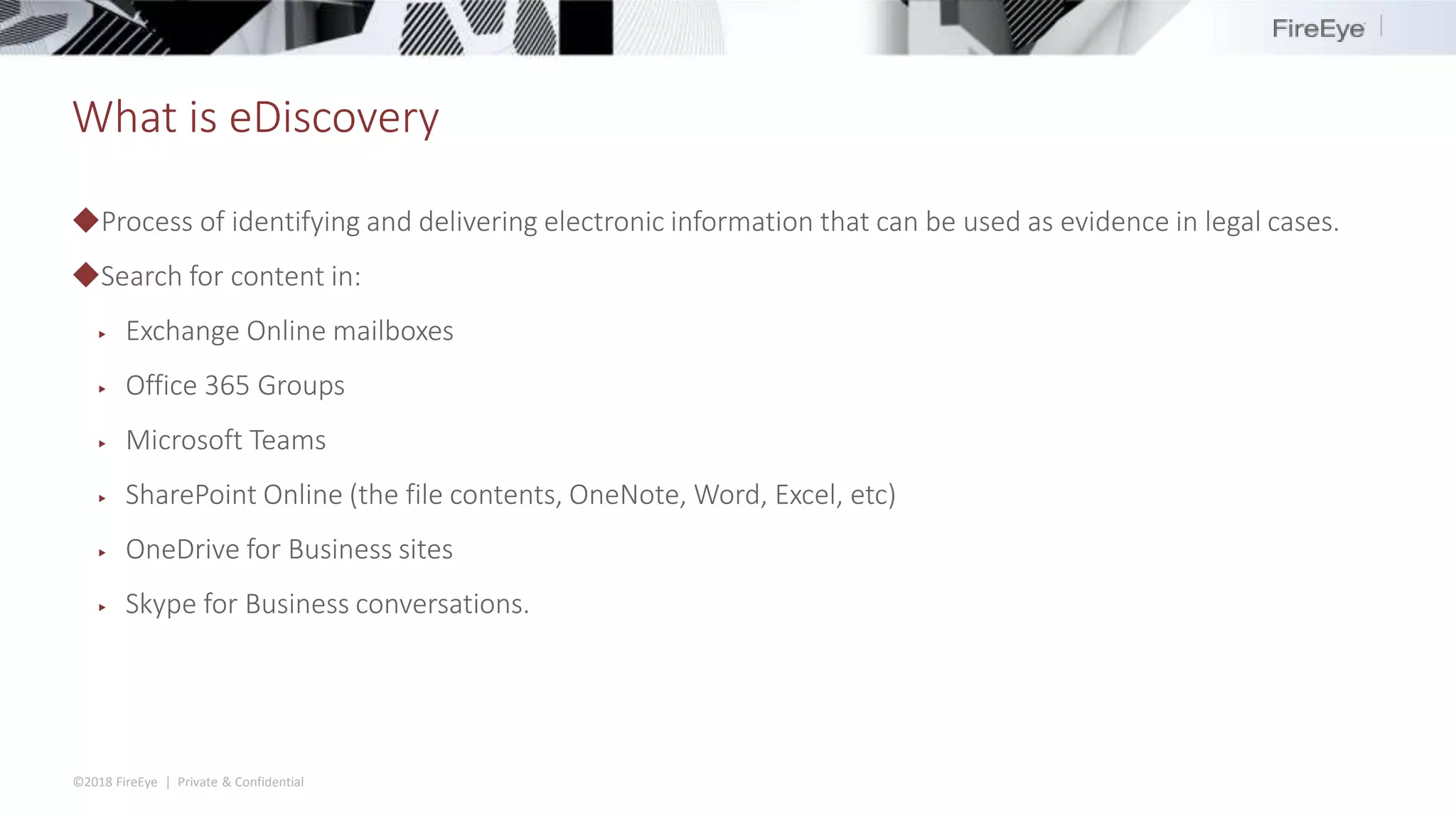
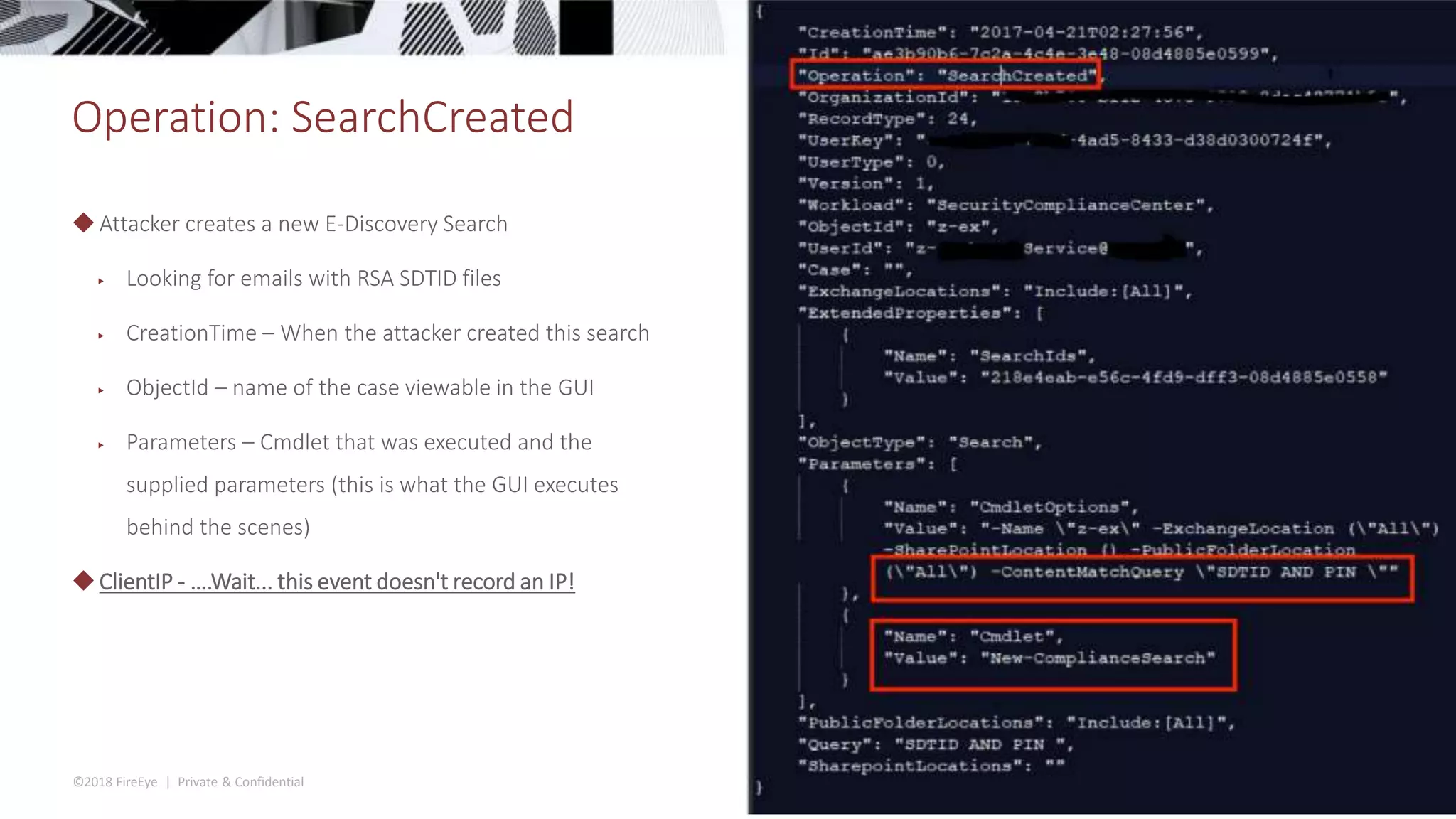
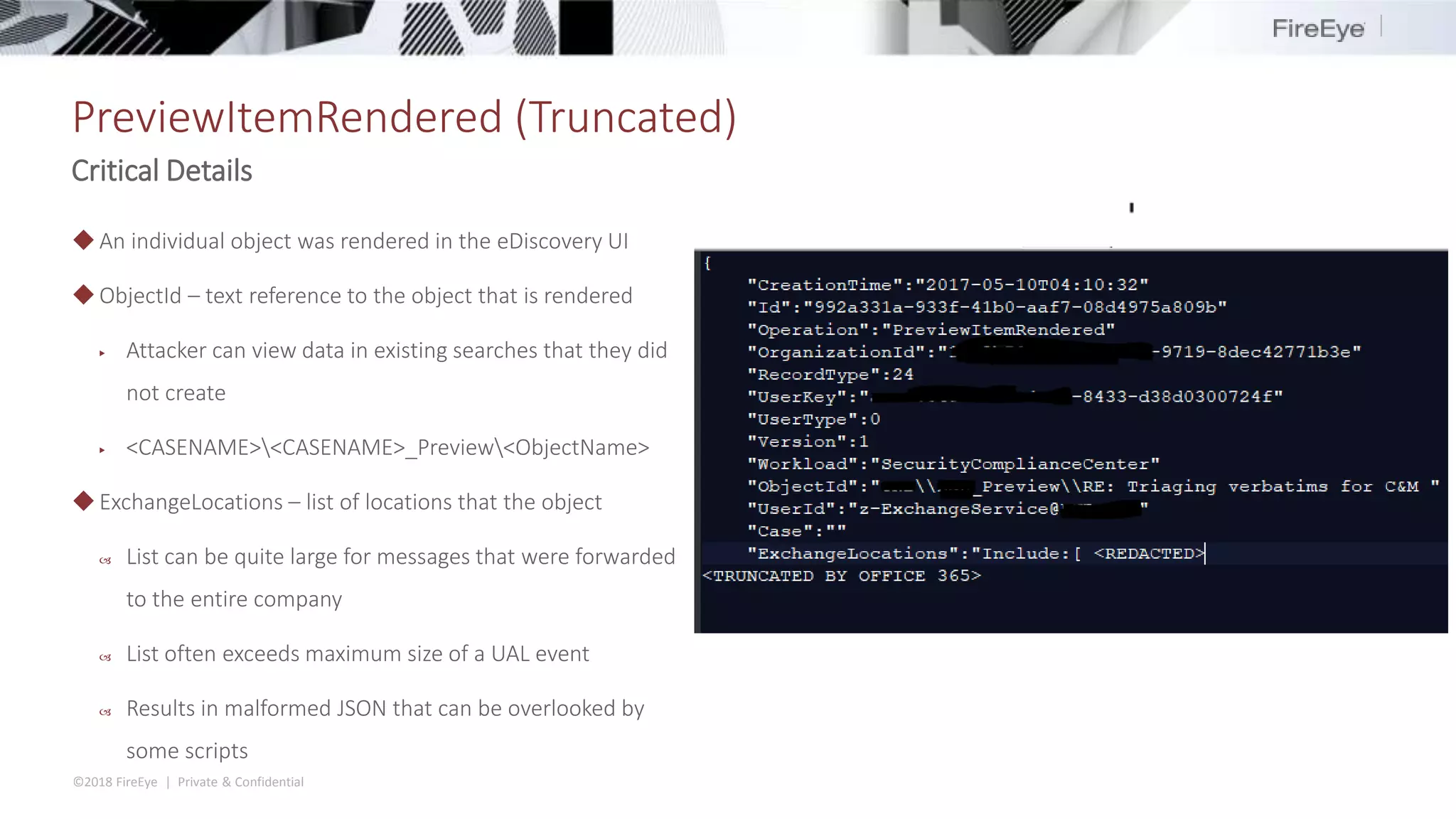
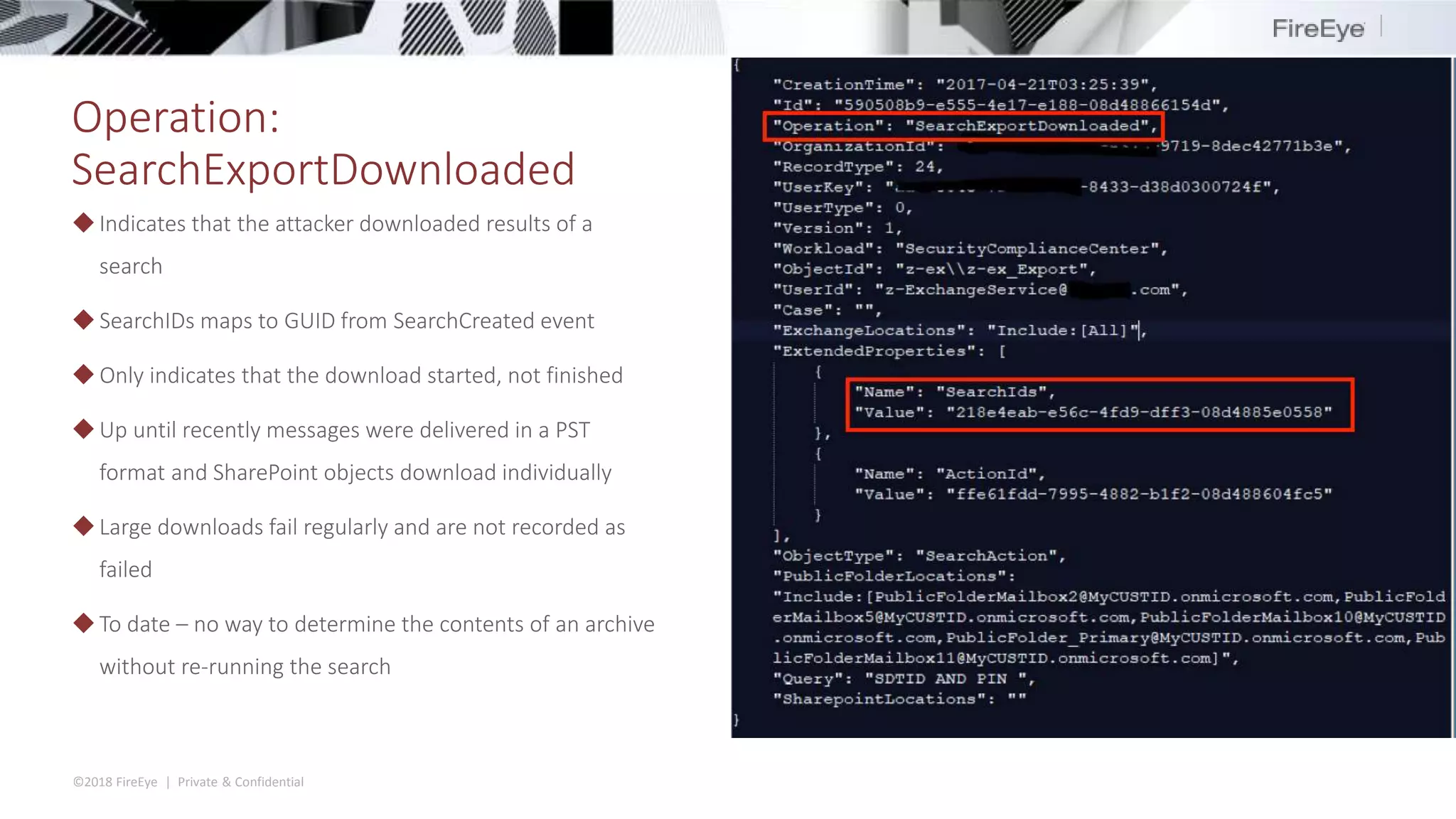
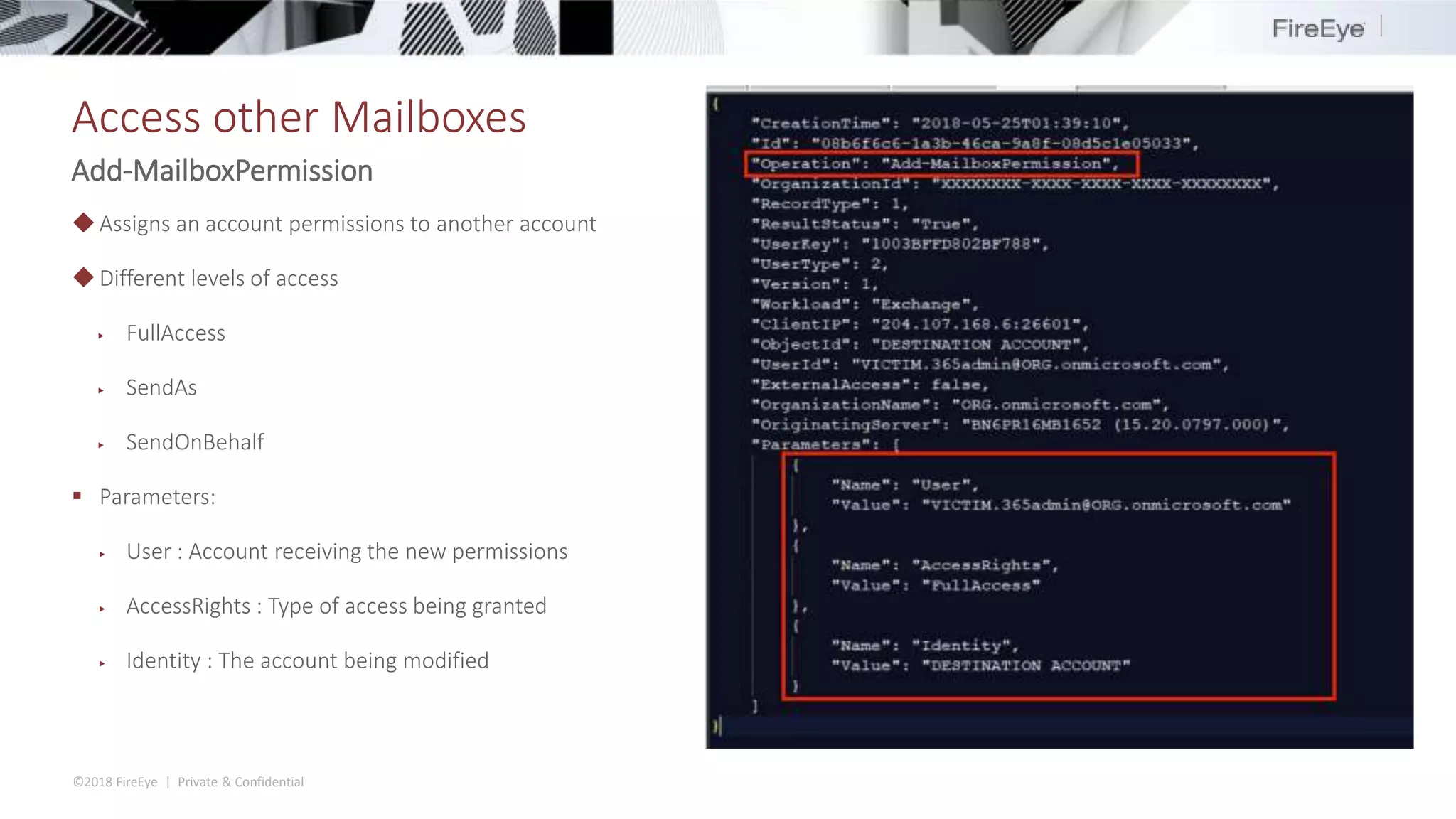
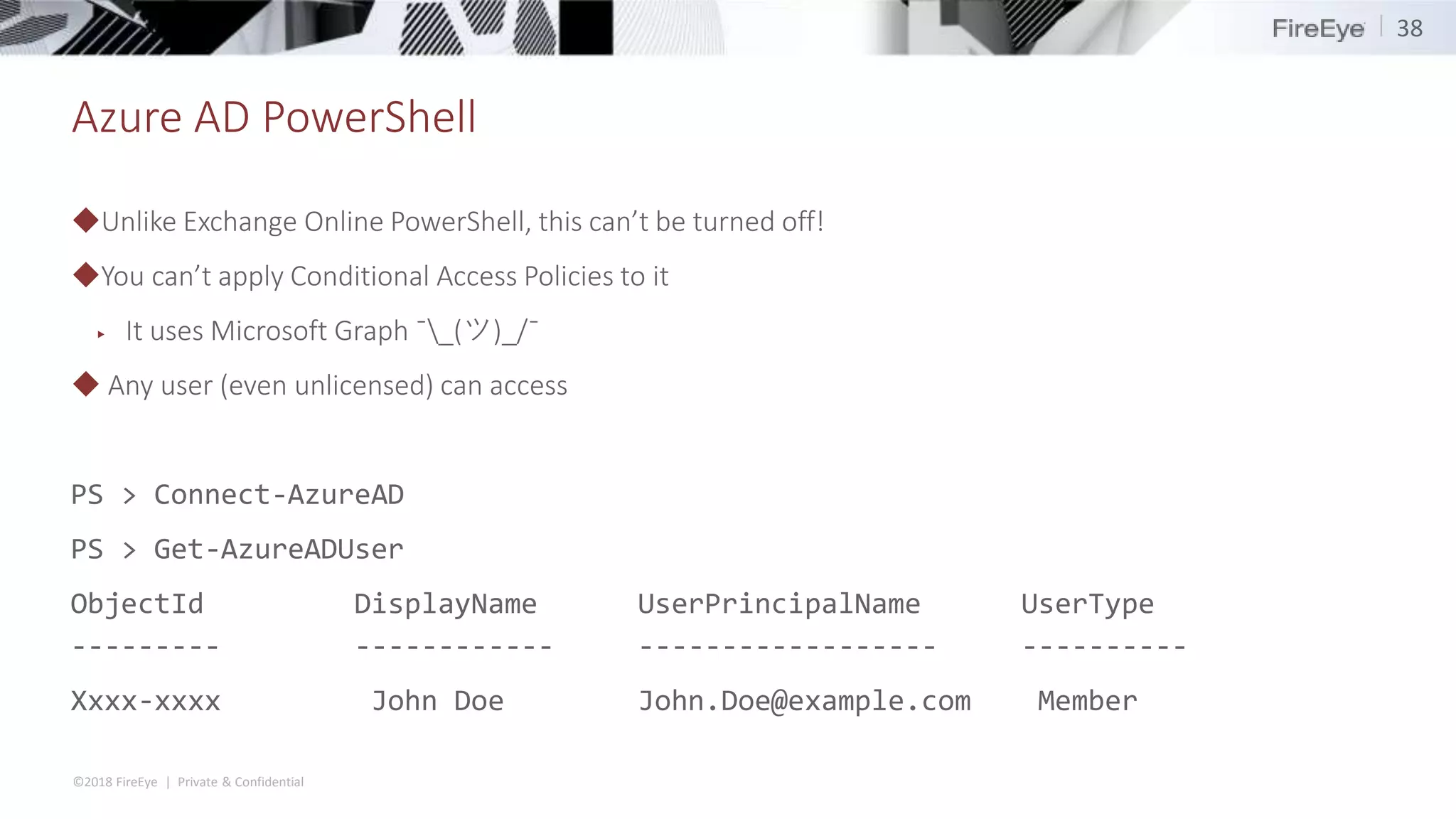
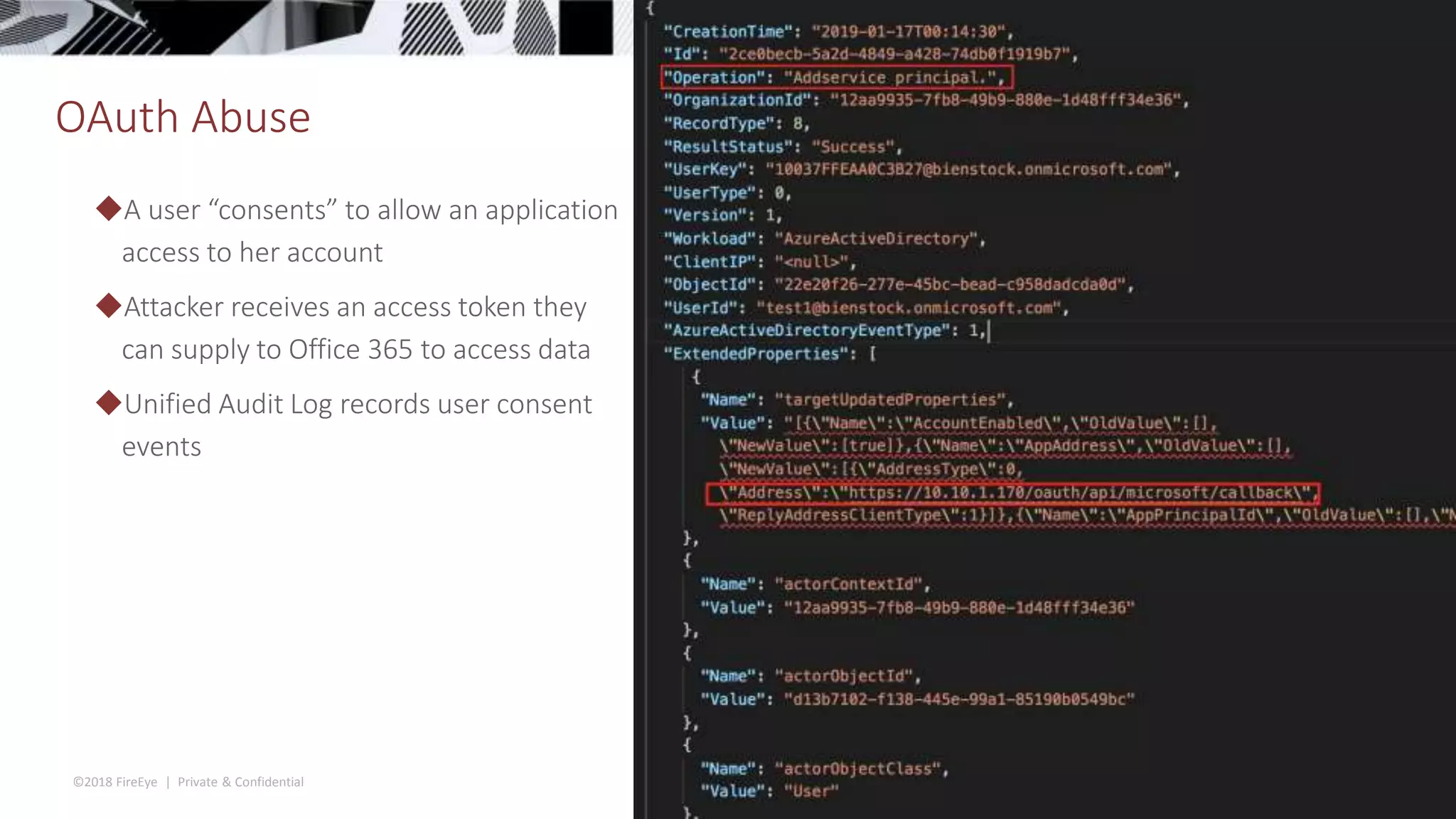
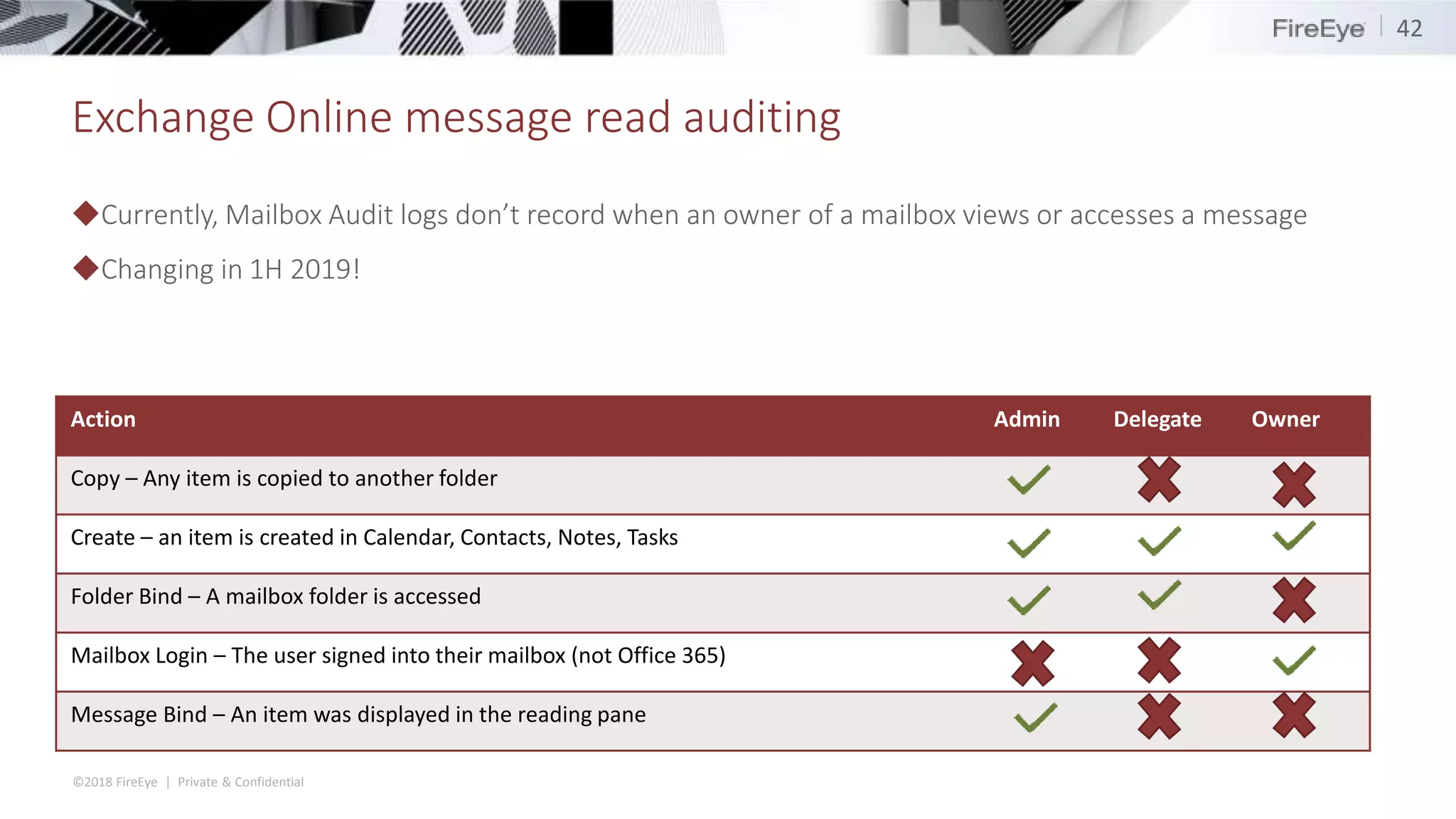
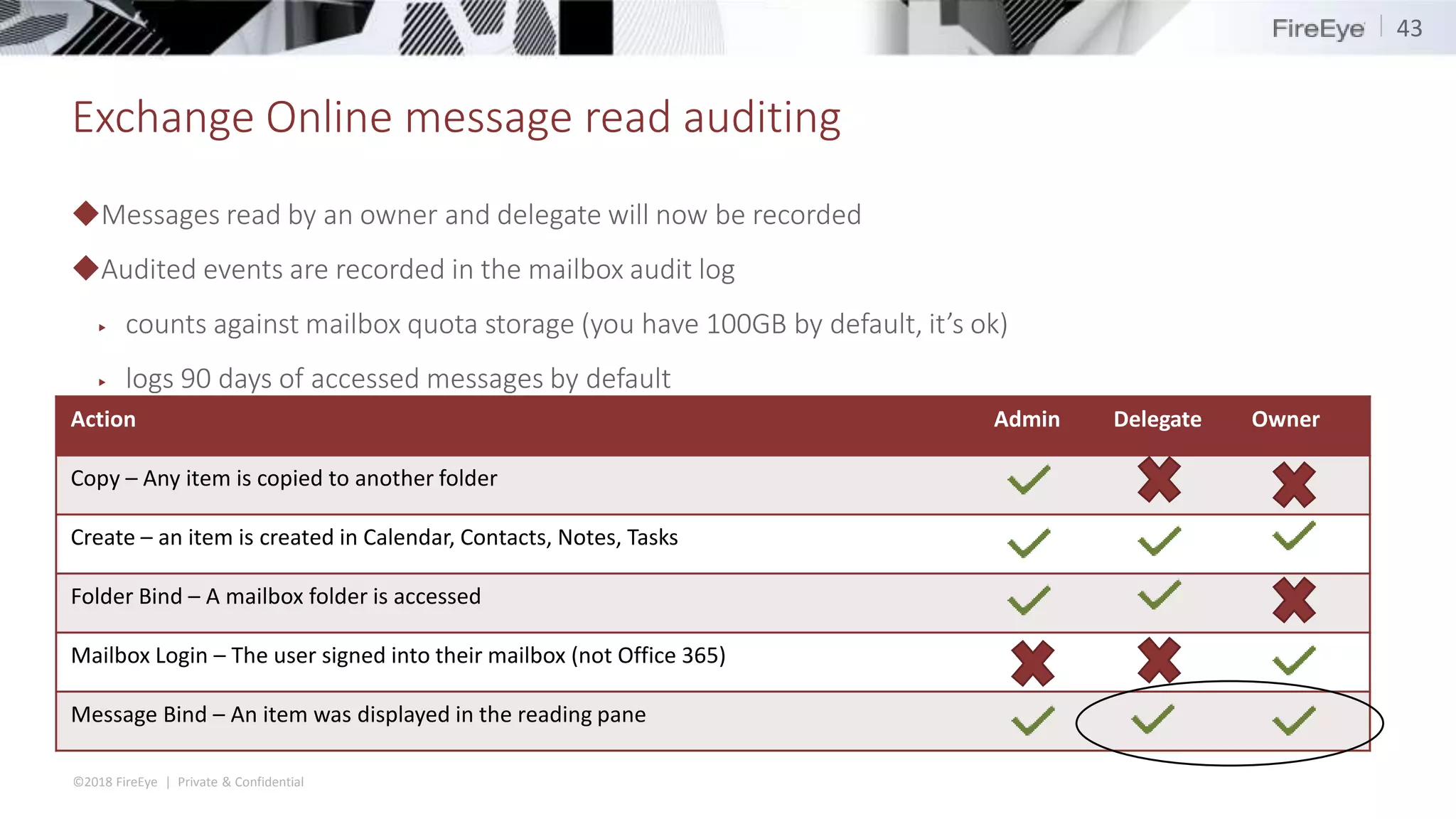
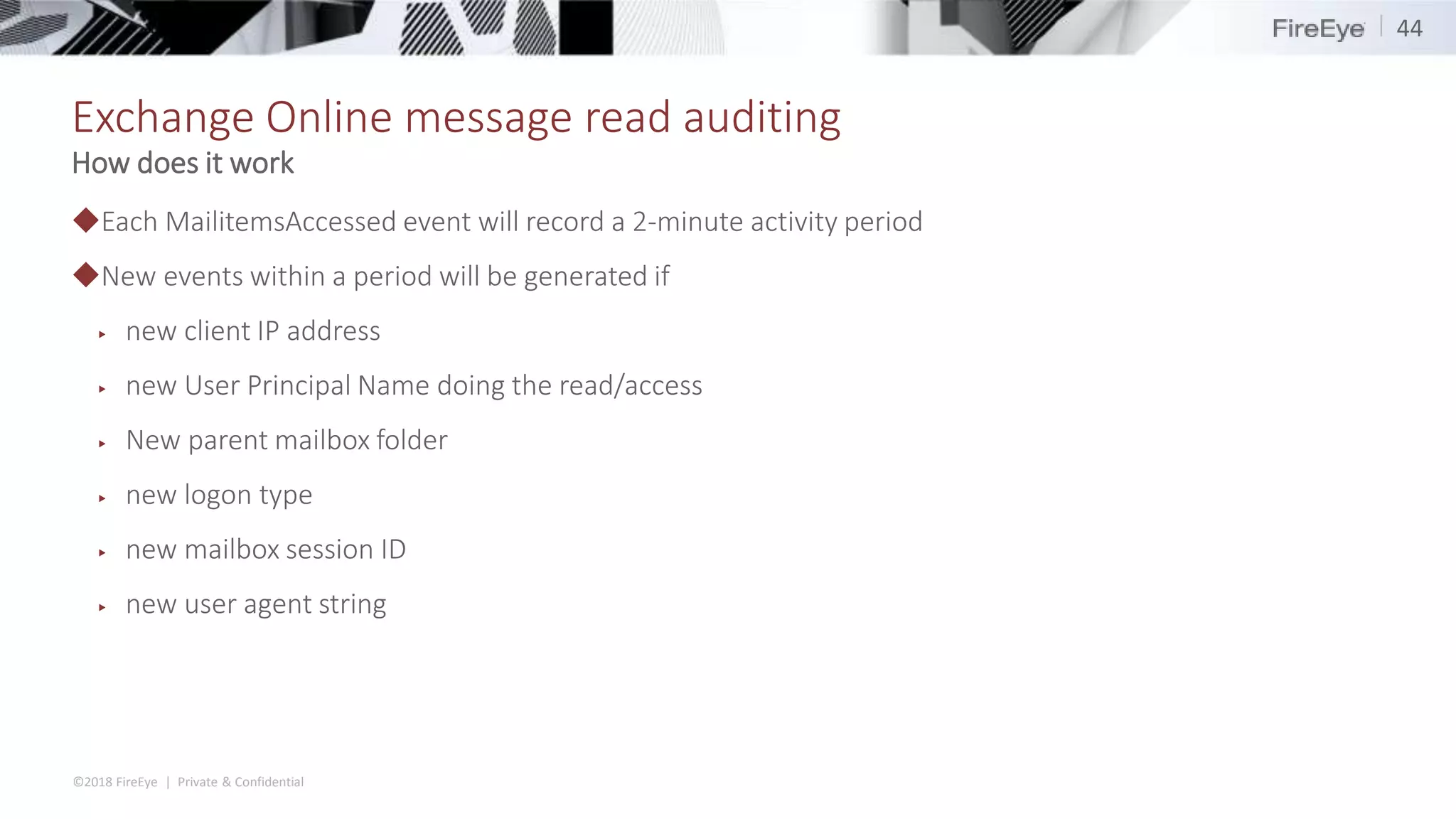
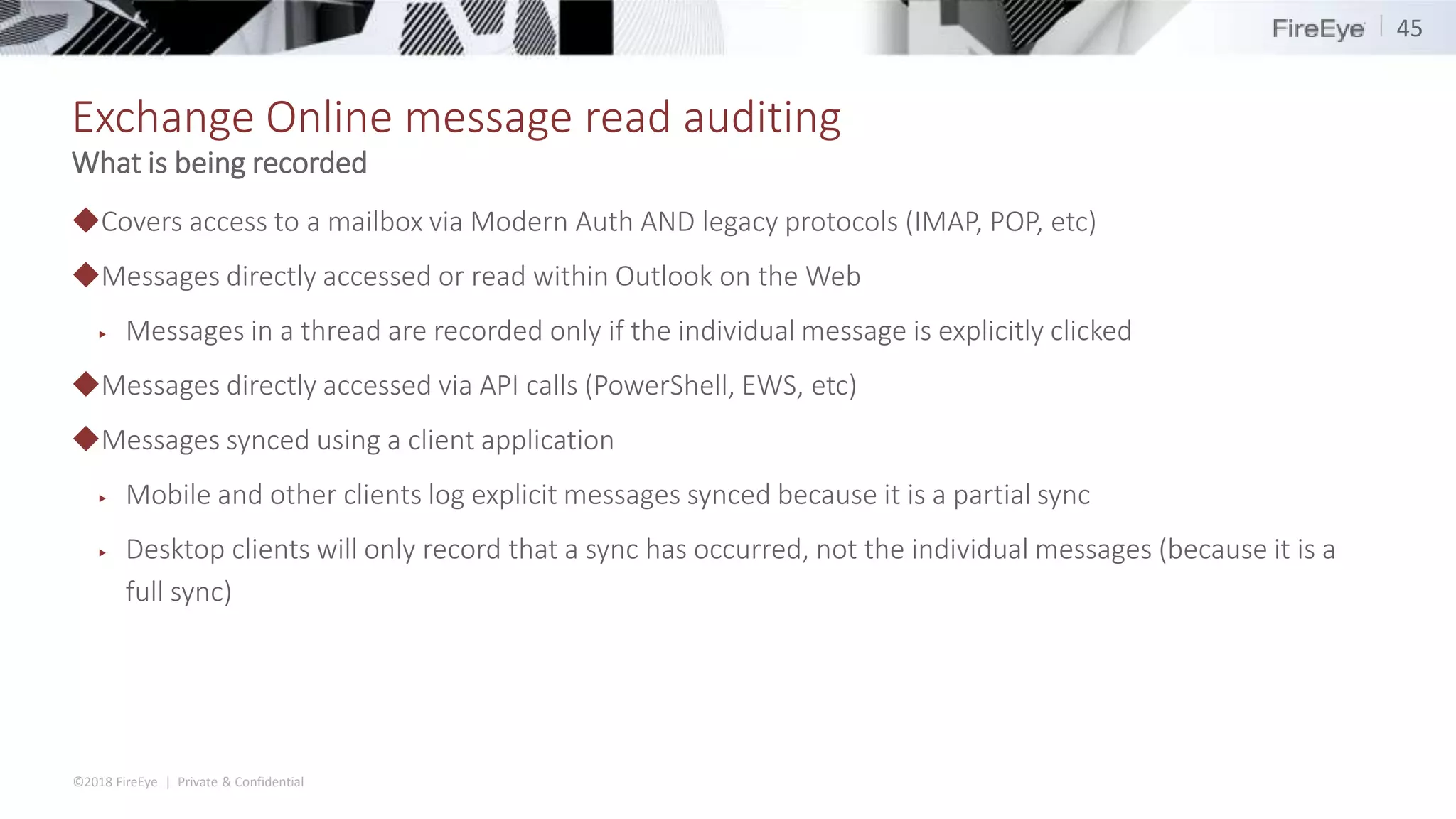
The document discusses the complexities and security issues of Office 365, especially in the context of business email compromise (BEC) and state-sponsored attacks. It explains different authentication methods, the significance of audit logs, and the methods attackers use to exploit vulnerabilities within Office 365 environments. The documentation also emphasizes the need for comprehensive auditing and monitoring to mitigate risks and enhance security postures.