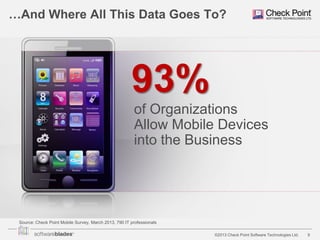
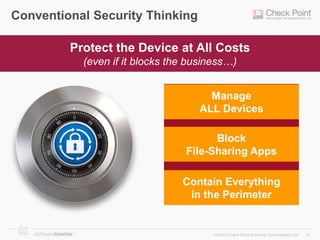
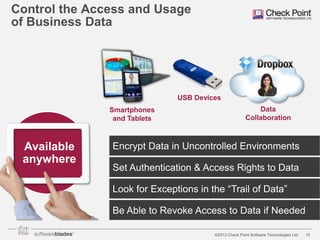
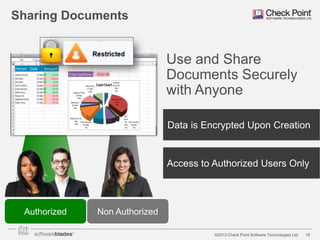
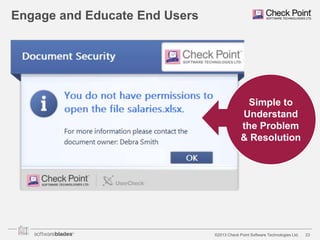
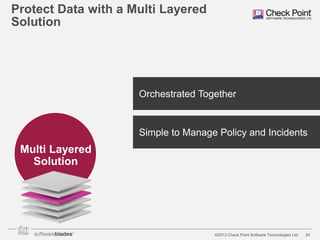
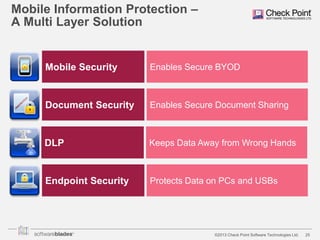
The document discusses the need for organizations to protect business data as it moves outside the traditional network boundaries due to trends like bring your own device (BYOD) and cloud file sharing. It advocates adopting a multi-layered solution to secure data on mobile devices, documents, and endpoints through mobile security, document security, data loss prevention, and endpoint security products. This approach allows organizations to enable BYOD and secure information sharing while still protecting sensitive data from ending up in the wrong hands.




![Data Loss at Organizations
54%
of Organizations
Experienced
Data Loss
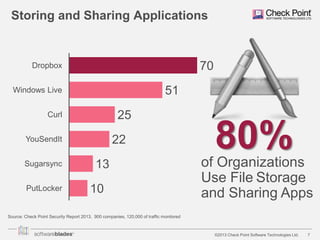
Source: Check Point Security Report 2013, 900 companies, 120,000 of traffic monitored
[Restricted] ONLY for designated groups and individuals
©2013 Check Point Software Technologies Ltd.
8](https://image.slidesharecdn.com/mobilesecurity-131204090535-phpapp01/85/Check-Point-Mobile-Security-8-320.jpg)