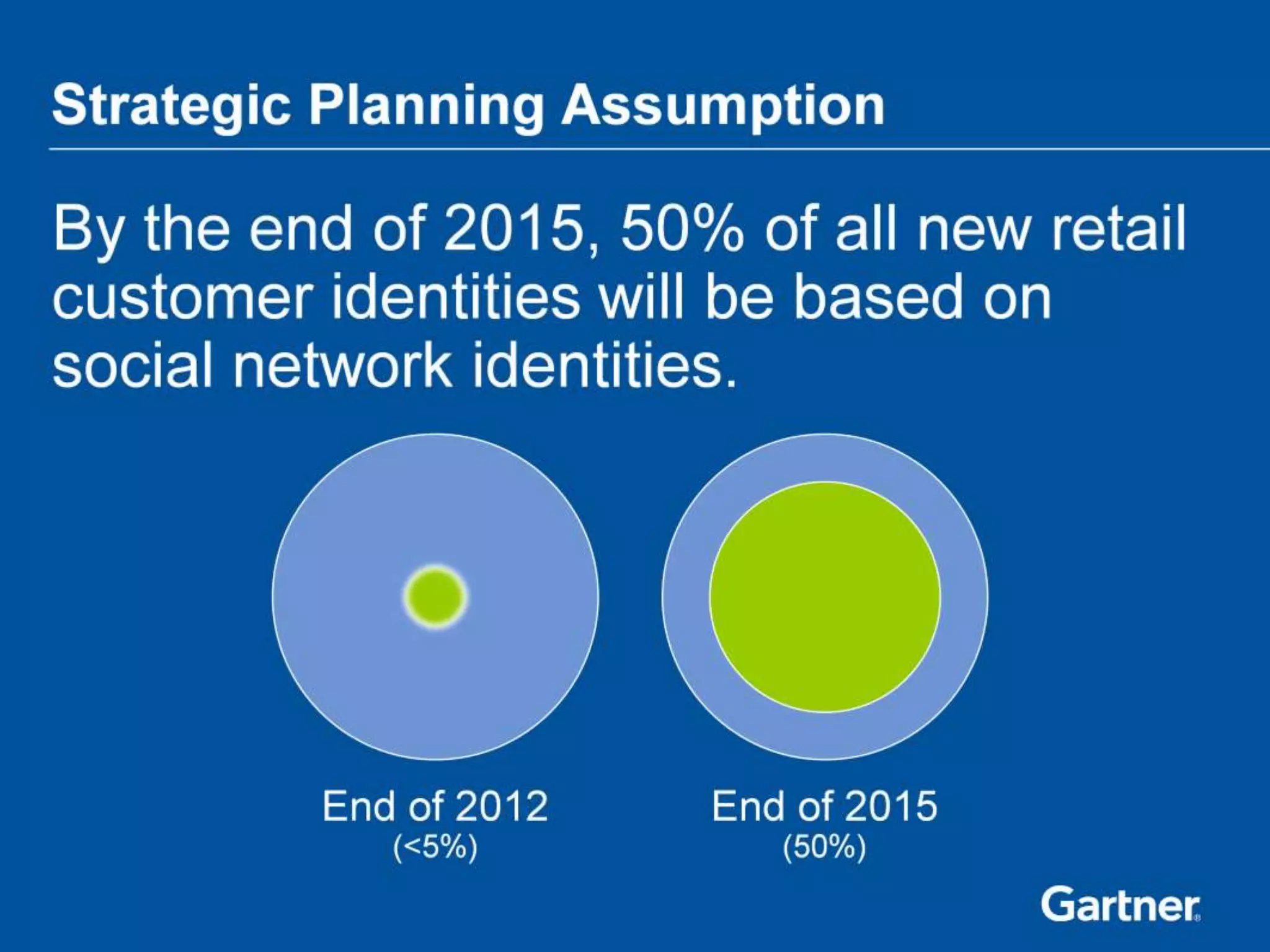
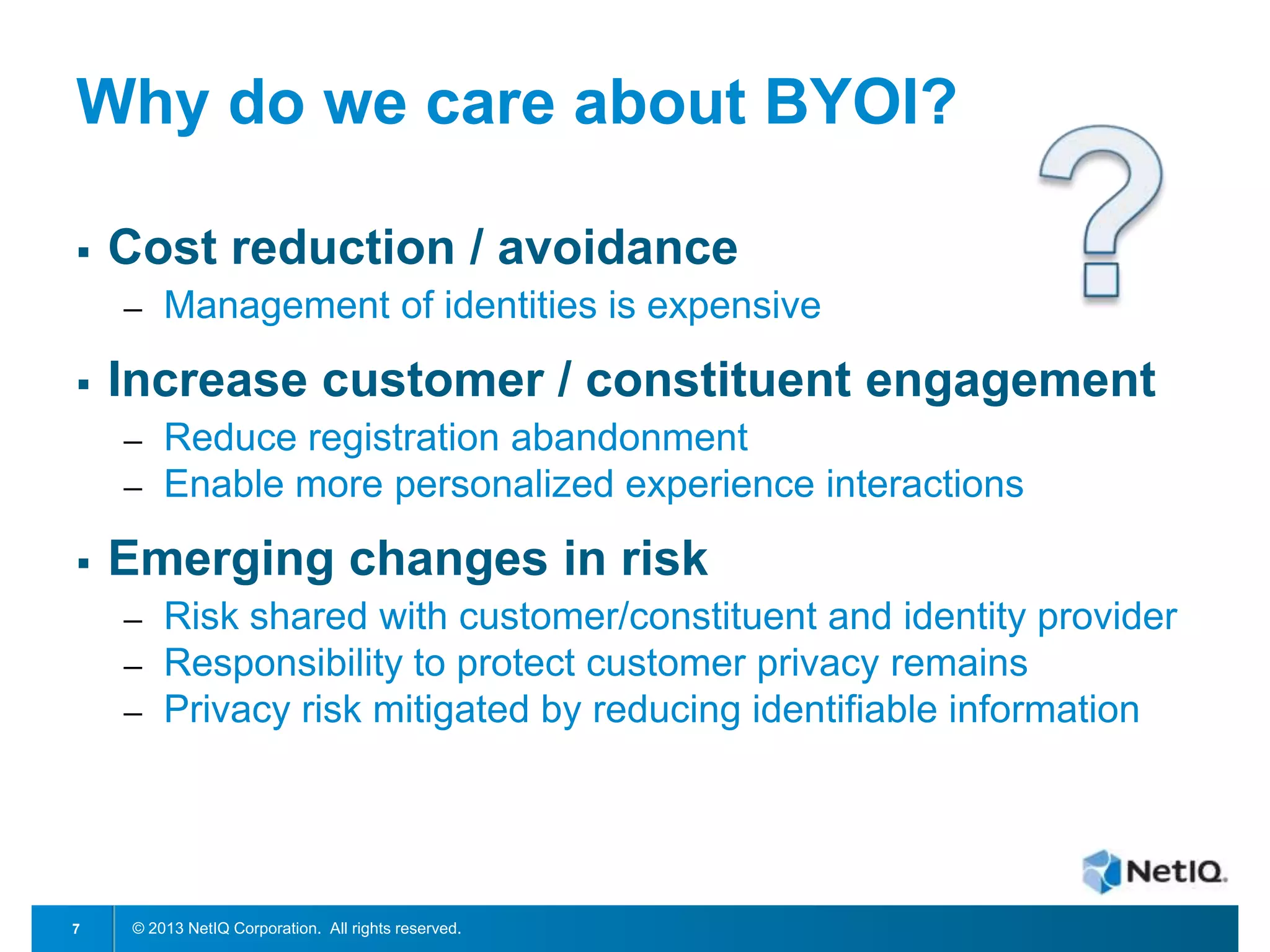
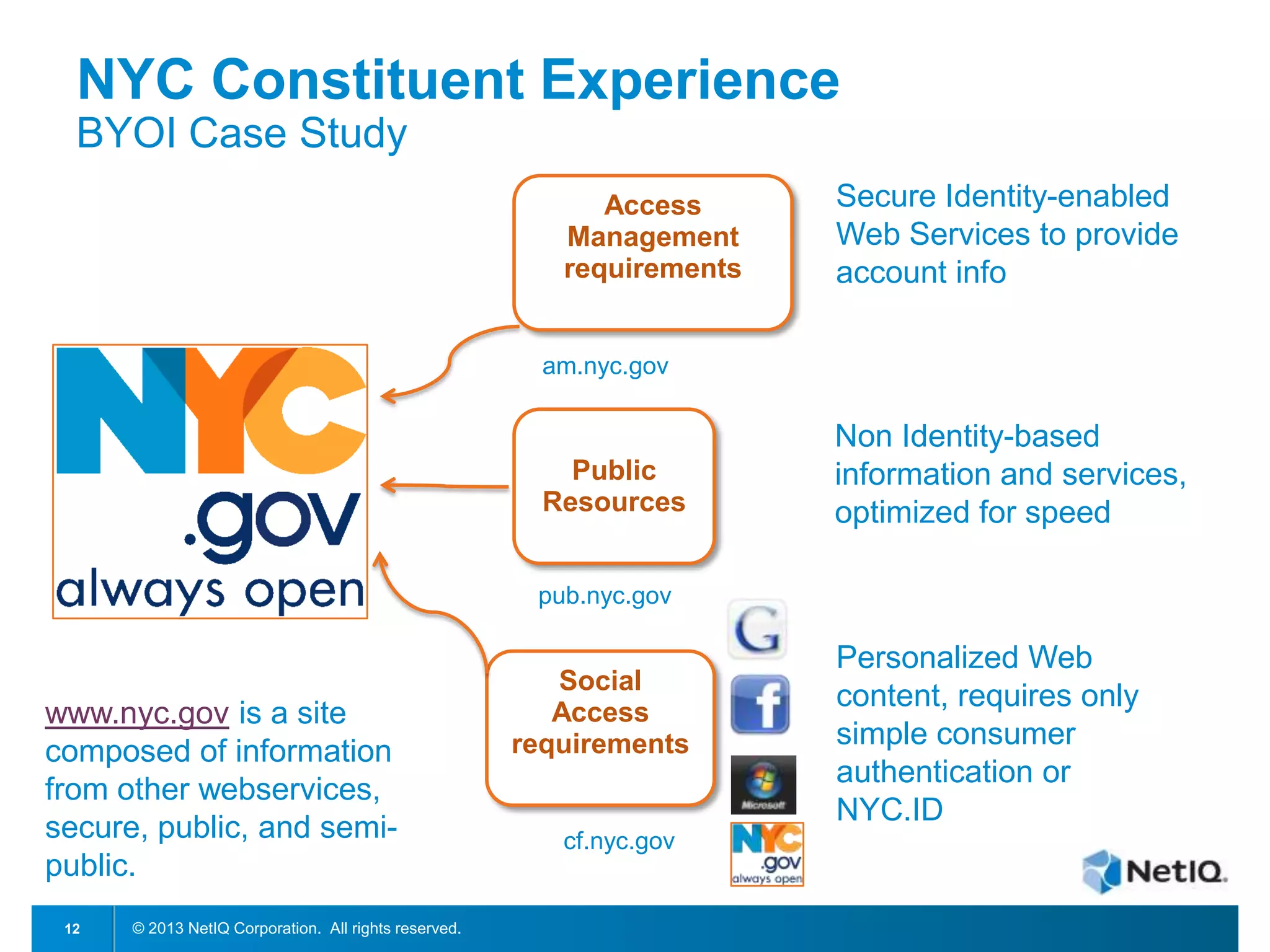
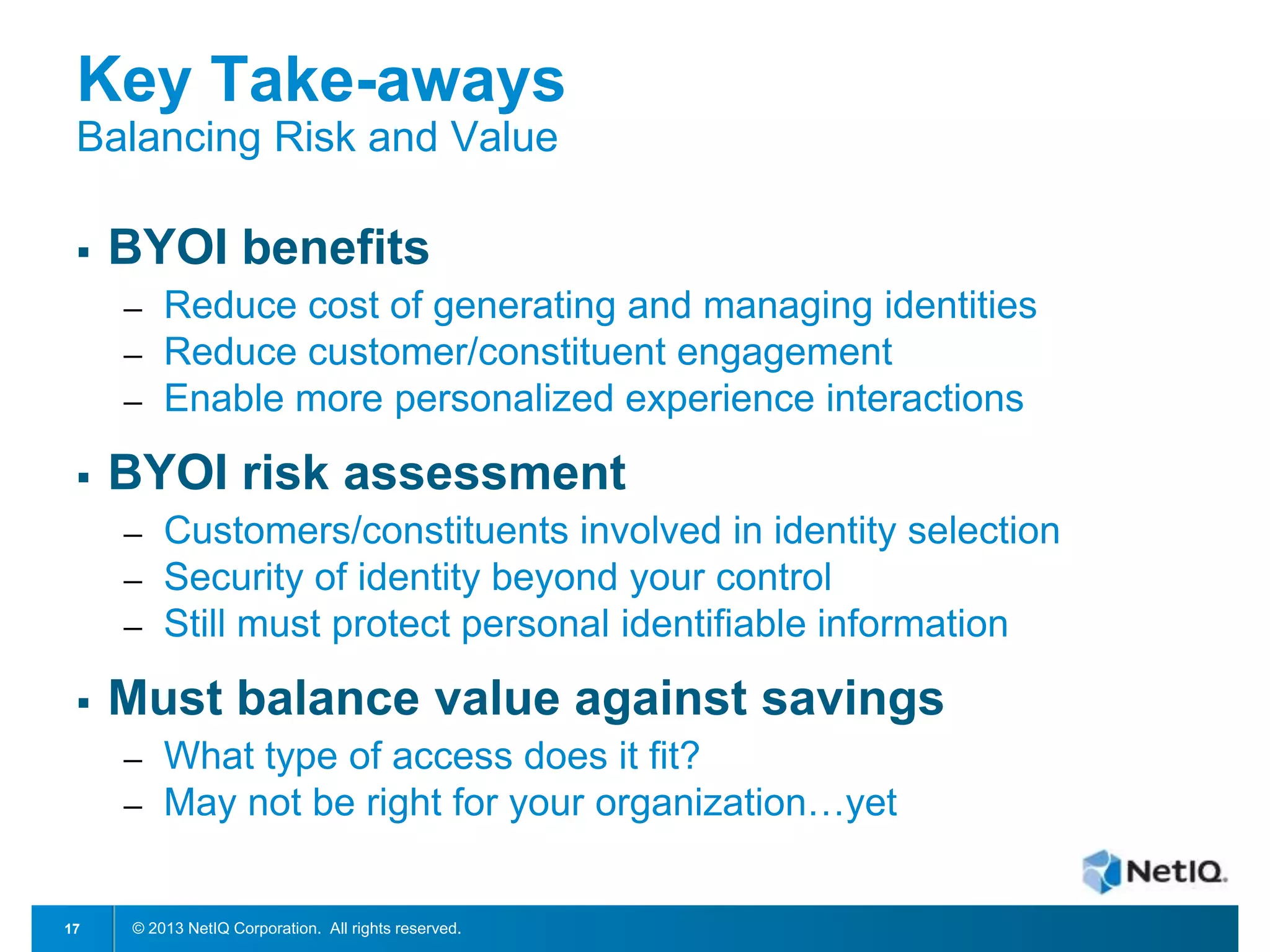
The document discusses Bring Your Own Identity (BYOI) strategies for organizations, emphasizing the potential benefits of cost reduction and improved customer engagement while addressing security concerns. It highlights trends in BYOI adoption, such as the merging of personal devices and identities and the need for risk assessment based on user access levels. A case study on NYC's BYOI implementation illustrates the varying requirements and security considerations based on the nature of user interactions.