Trees and Graphs in data structures and Algorithms
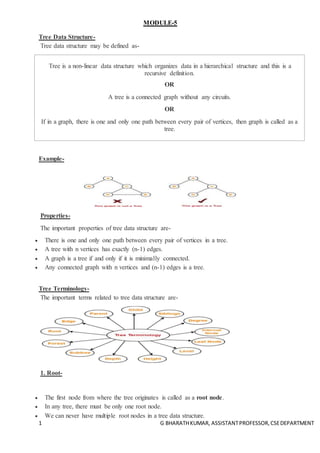
- 1. 1 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT MODULE-5 Tree Data Structure- Tree data structure may be defined as- Tree is a non-linear data structure which organizes data in a hierarchical structure and this is a recursive definition. OR A tree is a connected graph without any circuits. OR If in a graph, there is one and only one path between every pair of vertices, then graph is called as a tree. Example- Properties- The important properties of tree data structure are- There is one and only one path between every pair of vertices in a tree. A tree with n vertices has exactly (n-1) edges. A graph is a tree if and only if it is minimally connected. Any connected graph with n vertices and (n-1) edges is a tree. Tree Terminology- The important terms related to tree data structure are- 1. Root- The first node from where the tree originates is called as a root node. In any tree, there must be only one root node. We can never have multiple root nodes in a tree data structure.
- 2. 2 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Example- Here, node A is the only root node. 2. Edge- The connecting link between any two nodes is called as an edge. In a tree with n number of nodes, there are exactly (n-1) number of edges. Example- 3. Parent- The node which has a branch from it to any other node is called as a parent node. In other words, the node which has one or more children is called as a parent node. In a tree, a parent node can have any number of child nodes. Example- Here, Node A is the parent of nodes B and C Node B is the parent of nodes D, E and F Node C is the parent of nodes G and H Node E is the parent of nodes I and J Node G is the parent of node K 4. Child- The node which is a descendant of some node is called as a child node. All the nodes except root node are child nodes. Example-
- 3. 3 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Here, Nodes B and C are the children of node A Nodes D, E and F are the children of node B Nodes G and H are the children of node C Nodes I and J are the children of node E Node K is the child of node G 5. Siblings- Nodes which belong to the same parent are called as siblings. In other words, nodes with the same parent are sibling nodes. Example- Here, Nodes B and C are siblings Nodes D, E and F are siblings Nodes G and H are siblings Nodes I and J are siblings 6. Degree- Degree of a node is the total number of children of that node. Degree of a tree is the highest degree of a node among all the nodes in the tree. Example- Here, Degree of node A = 2 Degree of node B = 3 Degree of node C = 2
- 4. 4 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Degree of node D = 0 Degree of node E = 2 Degree of node F = 0 Degree of node G = 1 Degree of node H = 0 Degree of node I = 0 Degree of node J = 0 Degree of node K = 0 7. Internal Node- The node which has at least one child is called as an internal node. Internal nodes are also called as non-terminal nodes. Every non-leaf node is an internal node. Example- Here, nodes A, B, C, E and G are internal nodes. 8. Leaf Node- The node which does not have any child is called as a leaf node. Leaf nodes are also called as external nodes or terminal nodes. Example- Here, nodes D, I, J, F, K and H are leaf nodes. 9. Level- In a tree, each step from top to bottom is called as level of a tree. The level count starts with 0 and increments by 1 at each level or step. Example- 10. Height-
- 5. 5 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Total number of edges that lies on the longest path from any leaf node to a particular node is called as height of that node. Height of a tree is the height of root node. Height of all leaf nodes = 0 Example- Here, Height of node A = 3 Height of node B = 2 Height of node C = 2 Height of node D = 0 Height of node E = 1 Height of node F = 0 Height of node G = 1 Height of node H = 0 Height of node I = 0 Height of node J = 0 Height of node K = 0 11. Depth- Total number of edges from root node to a particular node is called as depth of that node. Depth of a tree is the total number of edges from root node to a leaf node in the longest path. Depth of the root node = 0 The terms “level” and “depth” are used interchangeably. Example- Here, Depth of node A = 0 Depth of node B = 1 Depth of node C = 1 Depth of node D = 2 Depth of node E = 2 Depth of node F = 2 Depth of node G = 2
- 6. 6 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Depth of node H = 2 Depth of node I = 3 Depth of node J = 3 Depth of node K = 3 12. Subtree- In a tree, each child from a node forms a subtree recursively. Every child node forms a subtree on its parent node. Example- 13. Forest- A forest is a set of disjoint trees. Example- 1. Binary Tree A binary tree is a tree-type non-linear data structure with a maximum of two children for each parent. Every node in a binary tree has a left and right reference along with the data element. The node at the top of the hierarchy of a tree is called the root node. The nodes that hold other sub-nodes are the parent nodes. A parent node has two child nodes: the left child and right child. Hashing, routing data for network traffic, data compression, preparing binary heaps, and binary search trees are some of the applications that use a binary tree. Terminologies associatedwithBinary Trees andTypes of Binary Trees
- 7. 7 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Node: It represents a termination point in a tree. Root: A tree’s topmost node. Parent: Each node (apart from the root) in a tree that has at least one sub-node of its own is called a parent node. Child: A node that straightway came from a parent node when moving away from the root is the child node. Leaf Node: These are external nodes. They are the nodes that have no child. Internal Node: As the name suggests, these are inner nodes with at least one child. Depth of a Tree: The number of edges from the tree’s node to the root is. Height of a Tree: It is the number of edges from the node to the deepest leaf. The tree height is also considered the root height. As you are now familiar with the terminologies associated with the binary tree and types of binary tree, it is time to understand the binary tree components. Binary Tree Components There are three binary tree components. Every binary tree node has these three components associated with it. It becomes an essential concept for programmers to understand these three binary tree components: 1. Data element 2. Pointer to left subtree 3. Pointer to right subtree These three binary tree components represent a node. The data resides in the middle. The left pointer points to the child node, forming the left sub-tree. The right pointer points to the child node at its right, creating the right subtree. Types of Binary Trees The structure of a full binary tree: It is a special kind of a binary tree that has either zero children or two children. It means that all the nodes in that binary tree should either have two child nodes of its parent node or the parent node is itself the leaf node or the external node. The structure of a complete binary tree: A complete binary tree is another specific type of binary tree where all the tree levels are filled entirely with nodes, except the lowest level of the tree.
- 8. 8 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT The structure of a perfect binary tree: A binary tree is said to be ‘perfect’ if all the internal nodes have strictly two children, and every external or leaf node is at the same level or same depth within a tree. BalancedBinary Tree A binary tree is said to be ‘balanced’ if the tree height is O(logN), where ‘N’ is the number of nodes. In a balanced binary tree, the height of the left and the right subtrees of each node should vary by at most one. An AVL Tree and a Red-Black Tree are some common examples of data structure that can generate a balanced binary search tree. Here is an example o f a balanced binary tree: Degenerate Binary Tree A binary tree is said to be a degenerate binary tree or pathological binary tree if every internal node has only a single child. Such trees are similar to a linked list performance-wise. Here is an example of a degenerate binary tree: Benefits of a Binary Tree The search operation in a binary tree is faster as compared to other trees Only two traversals are enough to provide the elements in sorted order It is easy to pick up the maximum and minimum elements
- 9. 9 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Graph traversal also uses binary trees Converting different postfix and prefix expressions are possible using binary trees Tree Traversal Traversal is a process to visit all the nodes of a tree and may print their values too. Because, all nodes are connected via edges (links) we always start from the root (head) node. That is, we cannot randomly access a node in a tree. There are three ways which we use to traverse a tree − In-order Traversal Pre-order Traversal Post-order Traversal Generally, we traverse a tree to search or locate a given item or key in the tree or to print all the values it contains. In-order Traversal In this traversal method, the left subtree is visited first, then the root and later the right sub- tree. We should always remember that every node may represent a subtree itself. If a binary tree is traversed in-order, the output will produce sorted key values in an ascending order. We start from A, and following in-order traversal, we move to its left subtree B. B is also traversed in-order. The process goes on until all the nodes are visited. The output of inorder traversal of this tree will be − D → B → E → A → F → C → G Algorithm Until all nodes are traversed − Step 1 − Recursively traverse left subtree. Step 2 − Visit root node. Step 3 − Recursively traverse right subtree. Pre-order Traversal In this traversal method, the root node is visited first, then the left subtree and finally the right subtree.
- 10. 10 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT We start from A, and following pre-order traversal, we first visit A itself and then move to its left subtree B. B is also traversed pre-order. The process goes on until all the nodes are visited. The output of pre-order traversal of this tree will be − A → B → D → E → C → F → G Algorithm Until all nodes are traversed − Step 1 − Visit root node. Step 2 − Recursively traverse left subtree. Step 3 − Recursively traverse right subtree. Post-order Traversal In this traversal method, the root node is visited last, hence the name. First we traverse the left subtree, then the right subtree and finally the root node. We start from A, and following Post-order traversal, we first visit the left subtree B. B is also traversed post-order. The process goes on until all the nodes are visited. The output of post-order traversal of this tree will be − D → E → B → F → G → C → A Algorithm Until all nodes are traversed − Step 1 − Recursively traverse left subtree. Step 2 − Recursively traverse right subtree. Step 3 − Visit root node. Program link: https://www.geeksforgeeks.org/tree-traversals-inorder-preorder-and-postorder/
- 11. 11 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT #include <stdio.h> #include <stdlib.h> /* A binary tree node has data, pointer to left child and a pointer to right child */ struct node { int data; struct node* left; struct node* right; }; /* Helper function that allocates a new node with the given data and NULL left and right pointers. */ struct node* newNode(int data) { struct node* node = (struct node*)malloc(sizeof(struct node)); node->data = data; node->left = NULL; node->right = NULL; return(node); } /* Given a binary tree, print its nodes according to the "bottom-up" postorder traversal. */ void Postorder(struct node* node) { if (node == NULL) return; // first recur on left subtree Postorder(node->left); // then recur on right subtree Postorder(node->right); // now deal with the node printf("%d ", node->data); } /* Given a binary tree, print its nodes in inorder*/ void Inorder(struct node* node) { if (node == NULL) return; /* first recur on left child */ Inorder(node->left); /* then print the data of node */ printf("%d ", node->data);
- 12. 12 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT /* now recur on right child */ Inorder(node->right); } /* Given a binary tree, print its nodes in preorder*/ void Preorder(struct node* node) { if (node == NULL) return; /* first print data of node */ printf("%d ", node->data); /* then recur on left sutree */ Preorder(node->left); /* now recur on right subtree */ Preorder(node->right); } /* Driver program to test above functions*/ int main() { struct node *root = newNode(1); root->left = newNode(2); root->right = newNode(3); root->left->left = newNode(4); root->left->right = newNode(5); printf("nPreorder traversal of binary tree is n"); Preorder(root); printf("nInorder traversal of binary tree is n"); Inorder(root); printf("nPostorder traversal of binary tree is n"); Postorder(root); getchar(); return 0; }
- 13. 13 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT 2. Binary SearchTree Binary Search Tree is a node-based binary tree data structure which has the following properties: The left subtree of a node contains only nodes with keys lesser than the node’s key. The right subtree of a node contains only nodes with keys greater than the node’s key. The left and right subtree each must also be a binary search tree. BST divides all its sub-trees into two segments; the left sub-tree and the right sub- tree and can be defined as − left_subtree (keys) < node (key) ≤ right_subtree (keys) Basic Operations Following are the basic operations of a tree − Search − Searches an element in a tree. Insert − Inserts an element in a tree. Pre-order Traversal − Traverses a tree in a pre-order manner. In-order Traversal − Traverses a tree in an in-order manner. Post-order Traversal − Traverses a tree in a post-order manner. Node Define a node having some data, references to its left and right child nodes. struct node { int data; struct node *leftChild; struct node *rightChild; };
- 14. 14 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Search Operation Whenever an element is to be searched, start searching from the root node. Then if the data is less than the key value, search for the element in the left subtree. Otherwise, search for the element in the right subtree. Follow the same algorithm for each node. Algorithm struct node* search(int data){ struct node *current = root; printf("Visiting elements: "); while(current->data != data){ if(current != NULL) { printf("%d ",current->data); //go to left tree if(current->data > data){ current = current->leftChild; } //else go to right tree else { current = current->rightChild; } //not found if(current == NULL){ return NULL; } } } return current; } Insert Operation Whenever an element is to be inserted, first locate its proper location. Start searching from the root node, then if the data is less than the key value, search for the empty location in the left subtree and insert the data. Otherwise, search for the empty location in the right subtree and insert the data. Algorithm void insert(int data) { struct node *tempNode = (struct node*) malloc(sizeof(struct node)); struct node *current; struct node *parent; tempNode->data = data; tempNode->leftChild = NULL; tempNode->rightChild = NULL; //if tree is empty
- 15. 15 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT if(root == NULL) { root = tempNode; } else { current = root; parent = NULL; while(1) { parent = current; //go to left of the tree if(data < parent->data) { current = current->leftChild; //insert to the left if(current == NULL) { parent->leftChild = tempNode; return; } } //go to right of the tree else { current = current->rightChild; //insert to the right if(current == NULL) { parent->rightChild = tempNode; return; } } } } } Binary Tree – In a binary tree, a node can have maximum two children. Consider the left skewed binary tree shown in Figure 1. Searching: For searching element 2, we have to traverse all elements (assuming we do breadth first traversal). Therefore, searching in binary tree has worst case complexity of O(n). Insertion: For inserting element as left child of 2, we have to traverse all elements. Therefore, insertion in binary tree has worst case complexity of O(n). Deletion: For deletion of element 2, we have to traverse all elements to find 2 (assuming we do breadth first traversal). Therefore, deletion in binary tree has worst case complexity of O(n). Binary Search Tree (BST) – BST is a special type of binary tree in which left child of a node has value less than the parent and right child has value greater than parent. Consider the left skewed BST shown in Figure 2.
- 16. 16 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Searching: For searching element 1, we have to traverse all elements (in order 3, 2, 1). Therefore, searching in binary search tree has worst case complexity of O(n). In general, time complexity is O(h) where h is height of BST. Insertion: For inserting element 0, it must be inserted as left child of 1. Therefore, we need to traverse all elements (in order 3, 2, 1) to insert 0 which has worst case complexity of O(n). In general, time complexity is O(h). Deletion: For deletion of element 1, we have to traverse all elements to find 1 (in order 3, 2, 1). Therefore, deletion in binary tree has worst case complexity of O(n). In general, time complexity is O(h). AVL/ Height Balanced Tree – AVL tree is binary search tree with additional property that difference between height of left sub-tree and right sub-tree of any node can’t be more than 1. For example, BST shown in Figure 2 is not AVL as difference between left sub-tree and right sub-tree of node 3 is 2. However, BST shown in Figure 3 is AVL tree. Searching: For searching element 1, we have to traverse elements (in order 5, 4, 1) = 3 = log2n. Therefore, searching in AVL tree has worst case complexity of O(log2n). Insertion: For inserting element 12, it must be inserted as right child of 9. Therefore, we need to traverse elements (in order 5, 7, 9) to insert 12 which has worst case complexity of O(log2n). Deletion: For deletion of element 9, we have to traverse elements to find 9 (in order 5, 7, 9). Therefore, deletion in binary tree has worst case complexity of O(log2n).
- 17. 17 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT 3. ThreadedBinary Tree A threaded binary tree is a binary tree variant that facilitates traversal in a particular order (often the same order already defined for the tree). : The binary tree nodes may have atmost 2 childrens. If they have only one children or no children then link part in the linkedlist representation remains NULL. By using Threaded binary tree we can reuse that empty links. There are two types of threaded binary trees. Single Threaded: Where a NULL right pointers is made to point to the inorder successor (if successor exists) Double Threaded: Where both left and right NULL pointers are made to point to inorder predecessor and inorder successor respectively. The predecessor threads are useful for reverse inorder traversal and postorder traversal. The threads are also useful for fast accessing ancestors of a node. Following diagram shows an example Single Threaded Binary Tree. The dotted lines represent threads. C representation of a Threaded Node Following is C representation of a single-threaded node. struct Node { int data; struct Node *left, *right; bool rightThread; }
- 18. 18 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Following diagram demonstrates inorder order traversal using threads.
- 19. 19 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT 4. AVL/ Height Balanced Tree What if the input to binary search tree comes in a sorted (ascending or descending) manner? It will then look like this − It is observed that BST's worst-case performance is closest to linear search algorithms, that is Ο(n). In real-time data, we cannot predict data pattern and their frequencies. So, a need arises to balance out the existing BST. Named after their inventor Adelson, Velski & Landis, AVL trees are height balancing binary search tree. AVL tree checks the height of the left and the right sub-trees and assures that the difference is not more than 1. This difference is called the Balance Factor. Here we see that the first tree is balanced and the next two trees are not balanced − In the second tree, the left subtree of C has height 2 and the right subtree has height 0, so the difference is 2. In the third tree, the right subtree of A has height 2 and the left is missing, so it is 0, and the difference is 2 again. AVL tree permits difference (balance factor) to be only 1. BalanceFactor = height(left-sutree) − height(right-sutree) If the difference in the height of left and right sub-trees is more than 1, the tree is balanced using some rotation techniques.
- 20. 20 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT AVL Rotations To balance itself, an AVL tree may perform the following four kinds of rotations − Left rotation Right rotation Left-Right rotation Right-Left rotation The first two rotations are single rotations and the next two rotations are double rotations. To have an unbalanced tree, we at least need a tree of height 2. With this simple tree, let's understand them one by one. Left Rotation If a tree becomes unbalanced, when a node is inserted into the right subtree of the right subtree, then we perform a single left rotation − In our example, node A has become unbalanced as a node is inserted in the right subtree of A's right subtree. We perform the left rotation by making A the left- subtree of B. Right Rotation AVL tree may become unbalanced, if a node is inserted in the left subtree of the left subtree. The tree then needs a right rotation. As depicted, the unbalanced node becomes the right child of its left child by performing a right rotation.
- 21. 21 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Left-Right Rotation Double rotations are slightly complex version of already explained versions of rotations. To understand them better, we should take note of each action performed while rotation. Let's first check how to perform Left-Right rotation. A left-right rotation is a combination of left rotation followed by right rotation. State Action A node has been inserted into the right subtree of the left subtree. This makes C an unbalanced node. These scenarios cause AVL tree to perform left-right rotation. We first perform the left rotation on the left subtree of C. This makes A, the left subtree of B. Node C is still unbalanced, however now, it is because of the left- subtree of the left-subtree. We shall now right-rotate the tree, making B the new root node of this subtree. C now becomes the right subtree of its own left subtree. The tree is now balanced. Right-Left Rotation The second type of double rotation is Right-Left Rotation. It is a combination of right rotation followed by left rotation.
- 22. 22 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT State Action A node has been inserted into the left subtree of the right subtree. This makes A, an unbalanced node with balance factor 2. First, we perform the right rotation along C node, making C the right subtree of its own left subtree B. Now, B becomes the right subtree of A. Node A is still unbalanced because of the right subtree of its right subtree and requires a left rotation. A left rotation is performed by making B the new root node of the subtree. A becomes the left subtree of its right subtree B. The tree is now balanced.
- 23. 23 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Graphs A Graph is a non-linear data structure consisting of nodes and edges. The nodes are sometimes also referred to as vertices and the edges are lines or arcs that connect any two nodes in the graph. A Graph consists of a finite set of vertices(or nodes) and set of Edges which connect a pair of nodes. For searching in graphs, there are two different methods. The Breadth First Search and the Depth First searching techniques. Breadth First Search (BFS) The Breadth First Search (BFS) traversal is an algorithm, which is used to visit all of the nodes of a given graph. In this traversal algorithm one node is selected and then all of the adjacent nodes are visited one by one. After completing all of the adjacent vertices, it moves further to check another vertex and checks its adjacent vertices again. To implement this algorithm, we need to use the Queue data structure. All the adjacent vertices are added into the queue when all adjacent vertices are completed, one item is removed from the queue and start traversing through that vertex again. Depth First Search (DFS) The Depth-First Search (DFS) is a graph traversal algorithm. In this algorithm, one starting vertex is given, and when an adjacent vertex is found, it moves to that adjacent vertex first and tries to traverse in the same manner. It moves through the whole depth, as much as it can go, after that it backtracks to reach previous vertices to find the new path. To implement DFS in an iterative way, we need to use the stack data structure. If we want to do it recursively, external stacks are not needed, it can be done internal stacks for the recursion calls. Depth First Search (DFS) algorithm traverses a graph in a depthward motion and uses a stack to remember to get the next vertex to start a search, when a dead end occurs in any iteration. As in the example given above, DFS algorithm traverses from S to A to D to G to E to B first, then to F and lastly to C. It employs the following rules. Rule 1 − Visit the adjacent unvisited vertex. Mark it as visited. Display it. Push it in a stack. Rule 2 − If no adjacent vertex is found, pop up a vertex from the stack. (It will pop up all the vertices from the stack, which do not have adjacent vertices.) Rule 3 − Repeat Rule 1 and Rule 2 until the stack is empty.
- 24. 24 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Step Traversal Description 1 Initialize the stack. 2 Mark S as visited and put it onto the stack. Explore any unvisited adjacent node from S. We have three nodes and we can pick any of them. For this example, we shall take the node in an alphabetical order. 3 Mark A as visited and put it onto the stack. Explore any unvisited adjacent node from A. Both S and D are adjacent to A but we are concerned for unvisited nodes only. 4 Visit D and mark it as visited and put onto the stack. Here, we have B and C nodes, which are adjacent to D and both are unvisited. However, we shall again choose in an alphabetical order. 5 We choose B, mark it as visited and put onto the stack. Here B does not have any unvisited adjacent node. So, we pop B from the stack.
- 25. 25 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT 6 We check the stack top for return to the previous node and check if it has any unvisited nodes. Here, we find D to be on the top of the stack. 7 Only unvisited adjacent node is from D is C now. So we visit C, mark it as visited and put it onto the stack. Breadth First Search (BFS) algorithm traverses a graph in a breadthward motion and uses a queue to remember to get the next vertex to start a search, when a dead end occurs in any iteration. As in the example given above, BFS algorithm traverses from A to B to E to F first then to C and G lastly to D. It employs the following rules. Rule 1 − Visit the adjacent unvisited vertex. Mark it as visited. Display it. Insert it in a queue. Rule 2 − If no adjacent vertex is found, remove the first vertex from the queue. Rule 3 − Repeat Rule 1 and Rule 2 until the queue is empty. Step Traversal Description 1 Initialize the queue.
- 26. 26 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT 2 We start from visiting S (starting node), and mark it as visited. 3 We then see an unvisited adjacent node from S. In this example, we have three nodes but alphabetically we choose A, mark it as visited and enqueue it. 4 Next, the unvisited adjacent node from S is B. We mark it as visited and enqueue it. 5 Next, the unvisited adjacent node from S is C. We mark it as visited and enqueue it. 6 Now, S is left with no unvisited adjacent nodes. So, we dequeue and find A. 7 From A we have D as unvisited adjacent node. We mark it as visited and enqueue it.
- 27. 27 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT BFS vs DFS S.NO BFS DFS 1. BFS stands for Breadth First Search. DFS stands forDepth First Search. 2. BFS(Breadth First Search) uses Queue data structure for finding the shortest path. DFS(Depth First Search) uses Stack data structure. 3. BFS can be used to find single source shortest path in an unweighted graph, because in BFS, we reach a vertex with minimum number of edges from a source vertex. In DFS, we might traverse through more edges to reach a destination vertex from a source. 3. BFS is more suitable for searching vertices which are closer to the given source. DFS is more suitable when there are solutions away from source. 4. BFS considers all neighbors first and therefore not suitable for decision making trees used in games or puzzles. DFS is more suitable for game or puzzle problems. We make a decision, then explore all paths through this decision. And if this decision leads to win situation, we stop. 5. The Time complexity of BFS is O(V + E) when Adjacency List is used and O(V^2) when Adjacency Matrix is used, where V stands forvertices and E stands for edges. The Time complexity of DFS is also O(V + E) when Adjacency List is used and O(V^2) when Adjacency Matrix is used,where V stands forvertices and E stands for edges. Breadth First Search (BFS) Algorithm Breadth first search is a graph traversal algorithm that starts traversing the graph from root node and explores all the neighbouring nodes. Then, it selects the nearest node and explore all the unexplored nodes. The algorithm follows the same process for each of the nearest node until it finds the goal. The algorithm of breadth first search is given below. The algorithm starts with examining the node A and all of its neighbours. In the next step, the neighbours of the nearest node of A are explored and process continues in the further steps. The algorithm explores all neighbours of all the nodes and ensures that each node is visited exactly once and no node is visited twice. Algorithm o Step 1: SET STATUS = 1 (ready state) for each node in G
- 28. 28 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT o Step 2: Enqueue the starting node A and set its STATUS = 2 (waiting state) o Step 3: Repeat Steps 4 and 5 until QUEUE is empty o Step 4: Dequeue a node N. Process it and set its STATUS = 3 (processed state). o Step 5: Enqueue all the neighbours of N that are in the ready state (whose STATUS = 1) and set their STATUS = 2 (waiting state) [END OF LOOP] o Step 6: EXIT Example Consider the graph G shown in the following image, calculate the minimum path p from node A to node E. Given that each edge has a length of 1. Solution: Minimum Path P can be found by applying breadth first search algorithm that will begin at node A and will end at E. the algorithm uses two queues, namely QUEUE1 and QUEUE2. QUEUE1 holds all the nodes that are to be processed while QUEUE2 holds all the nodes that are processed and deleted from QUEUE1. Lets start examining the graph from Node A. 1. Add A to QUEUE1 and NULL to QUEUE2. 1. QUEUE1 = {A} 2. QUEUE2 = {NULL} 2. Delete the Node A from QUEUE1 and insert all its neighbours. Insert Node A into QUEUE2 1. QUEUE1 = {B, D} 2. QUEUE2 = {A} 3. Delete the node B from QUEUE1 and insert all its neighbours. Insert node B into QUEUE2. 1. QUEUE1 = {D, C, F}
- 29. 29 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT 2. QUEUE2 = {A, B} 4. Delete the node D from QUEUE1 and insert all its neighbours. Since F is the only neighbour of it which has been inserted, we will not insert it again. Insert node D into QUEUE2. 1. QUEUE1 = {C, F} 2. QUEUE2 = { A, B, D} 5. Delete the node C from QUEUE1 and insert all its neighbours. Add node C to QUEUE2. 1. QUEUE1 = {F, E, G} 2. QUEUE2 = {A, B, D, C} 6. Remove F from QUEUE1 and add all its neighbours. Since all of its neighbours has already been added, we will not add them again. Add node F to QUEUE2. 1. QUEUE1 = {E, G} 2. QUEUE2 = {A, B, D, C, F} 7. Remove E from QUEUE1, all of E's neighbours has already been added to QUEUE1 therefore we will not add them again. All the nodes are visited and the target node i.e. E is encountered into QUEUE2. 1. QUEUE1 = {G} 2. QUEUE2 = {A, B, D, C, F, E} Now, backtrack from E to A, using the nodes available in QUEUE2. The minimum path will be A → B → C → E. Depth First Search (DFS) Algorithm Depth first search (DFS) algorithm starts with the initial node of the graph G, and then goes to deeper and deeper until we find the goal node or the node which has no children. The algorithm, then backtracks from the dead end towards the most recent node that is yet to be completely unexplored. The data structure which is being used in DFS is stack. The process is similar to BFS algorithm. In DFS, the edges that leads to an unvisited node are called discovery edges while the edges that leads to an already visited node are called block edges. Algorithm o Step 1: SET STATUS = 1 (ready state) for each node in G o Step 2: Push the starting node A on the stack and set its STATUS = 2 (waiting state) o Step 3: Repeat Steps 4 and 5 until STACK is empty o Step 4: Pop the top node N. Process it and set its STATUS = 3 (processed state) o Step 5: Push on the stack all the neighbours of N that are in the ready state (whose STATUS = 1) and set their STATUS = 2 (waiting state) [END OF LOOP] o Step 6: EXIT Example : Consider the graph G along with its adjacency list, given in the figure below. Calculate the order to print all the nodes of the graph starting from node H, by using depth first search (DFS) algorithm.
- 30. 30 G BHARATHKUMAR, ASSISTANTPROFESSOR,CSEDEPARTMENT Solution : Push H onto the stack 1. STACK : H POP the top element of the stack i.e. H, print it and push all the neighbours of H onto the stack that are is ready state. 1. Print H 2. STACK : A Pop the top element of the stack i.e. A, print it and push all the neighbours of A onto the stack that are in ready state. 1. Print A 2. Stack : B, D Pop the top element of the stack i.e. D, print it and push all the neighbours of D onto the stack that are in ready state. 1. Print D 2. Stack : B, F Pop the top element of the stack i.e. F, print it and push all the neighbours of F onto the stack that are in ready state. 1. Print F 2. Stack : B Pop the top of the stack i.e. B and push all the neighbours 1. Print B 2. Stack : C Pop the top of the stack i.e. C and push all the neighbours. 1. Print C 2. Stack : E, G Pop the top of the stack i.e. G and push all its neighbours. 1. Print G 2. Stack : E Pop the top of the stack i.e. E and push all its neighbours. 1. Print E 2. Stack : Hence, the stack now becomes empty and all the nodes of the graph have been traversed. The printing sequence of the graph will be : 1. H → A → D → F → B → C → G → E
