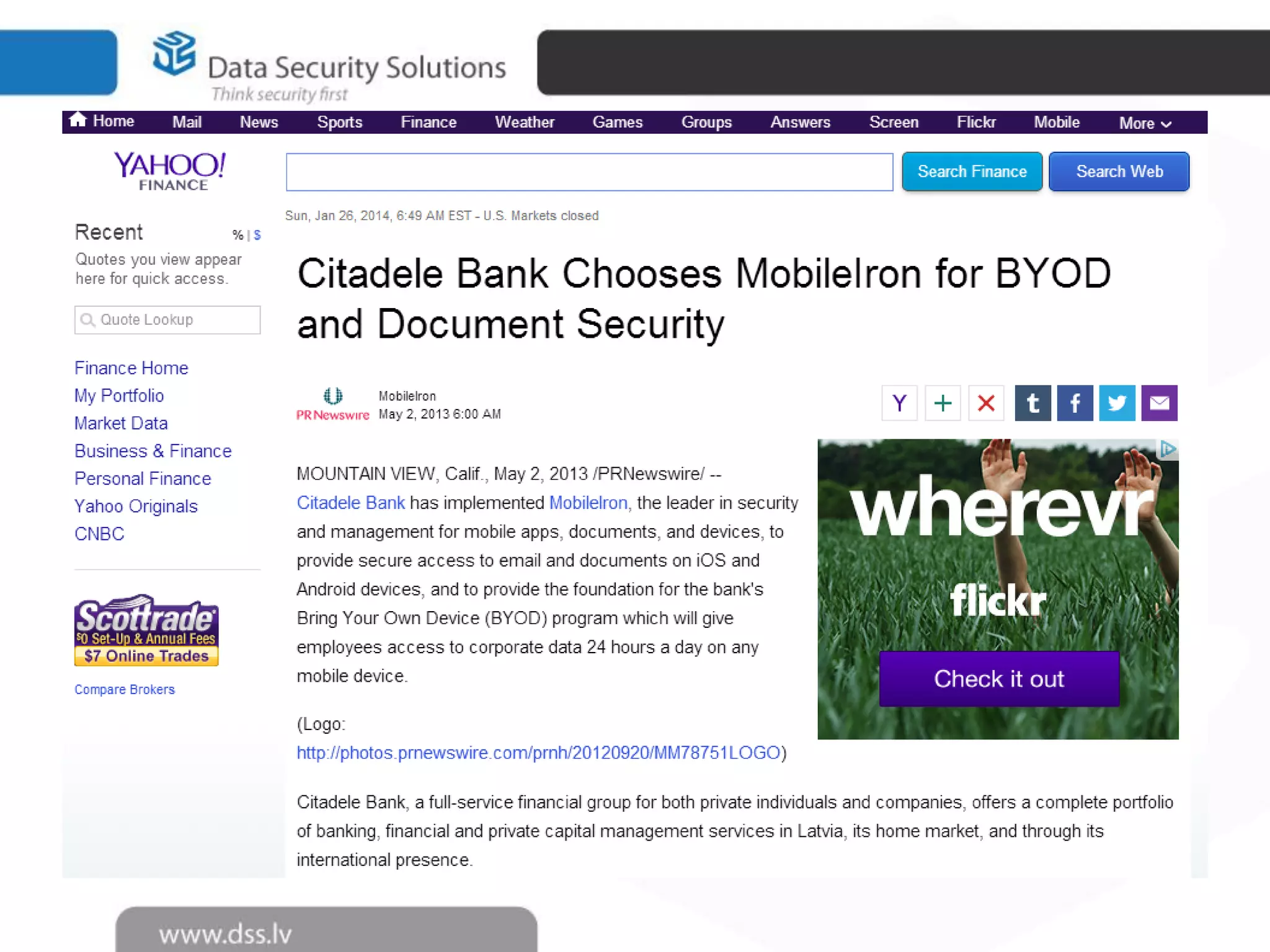
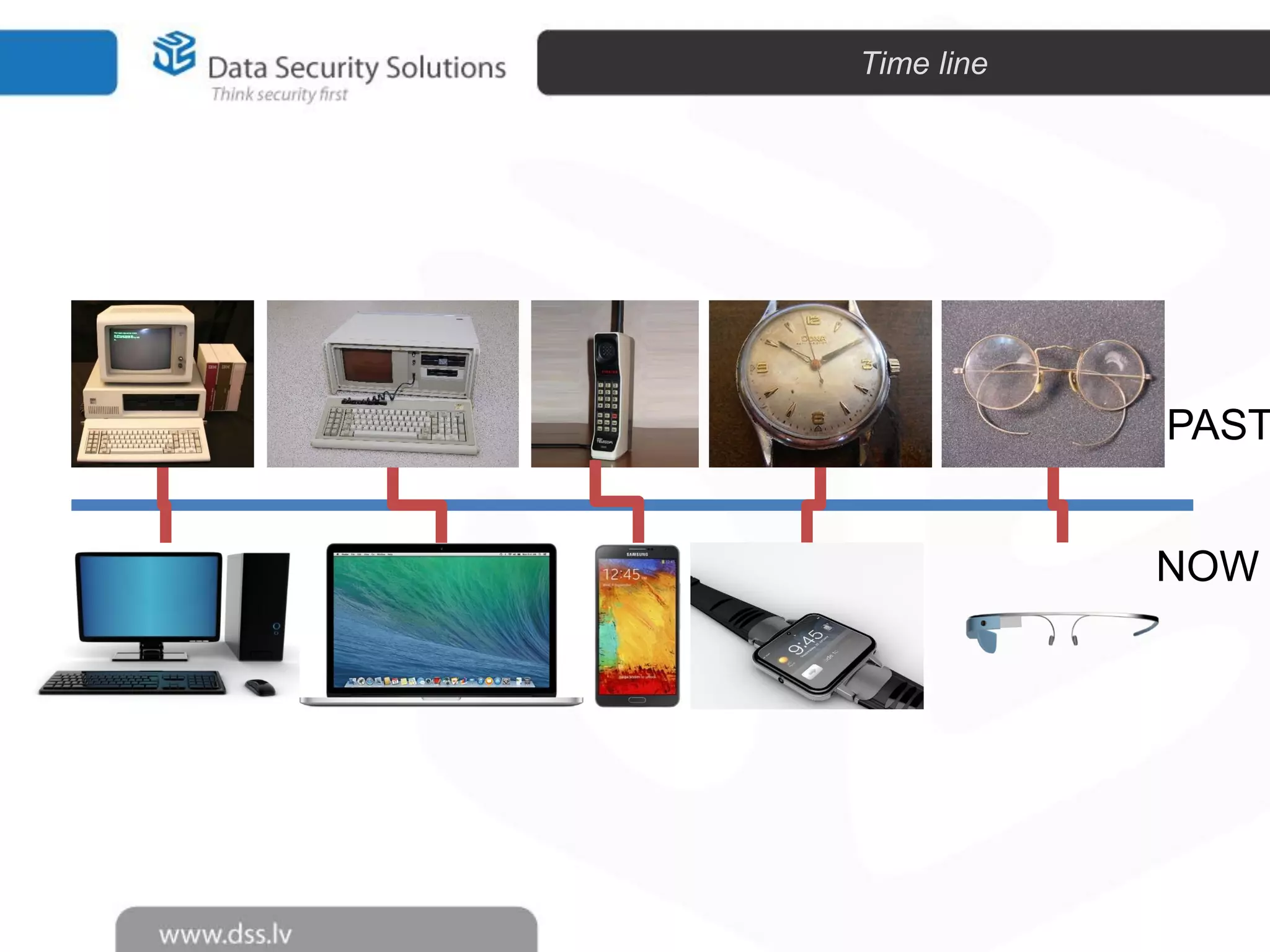
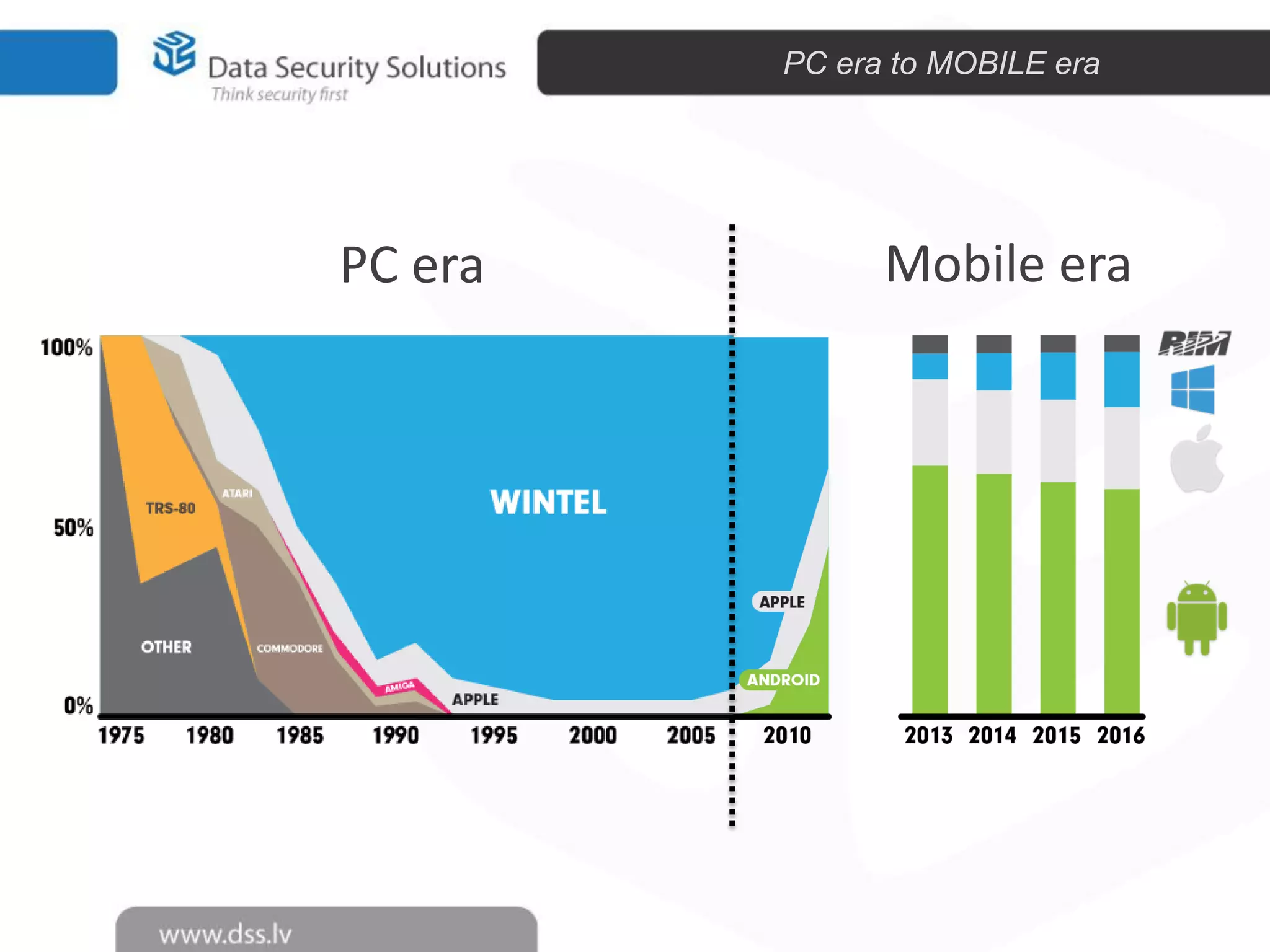
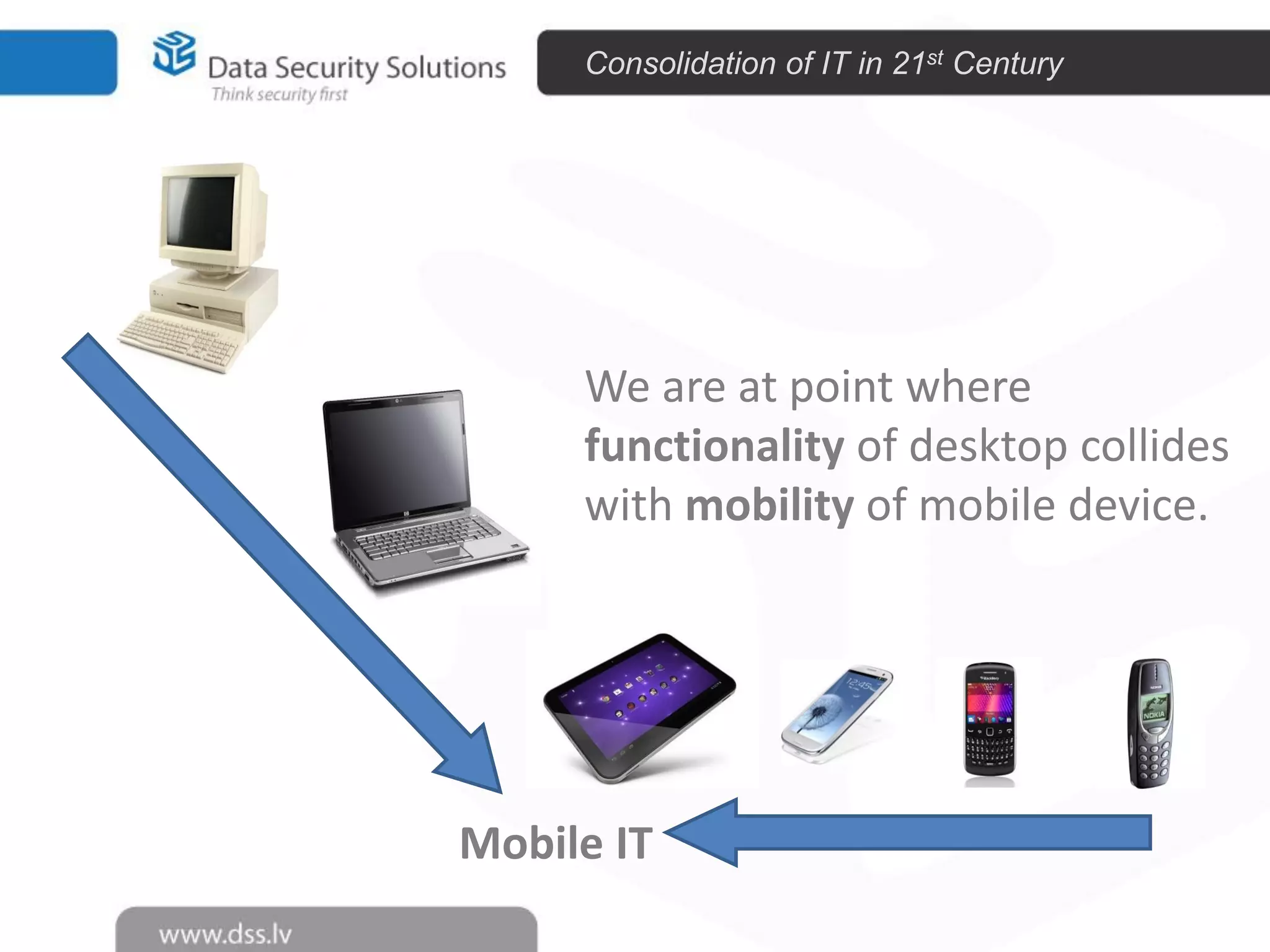
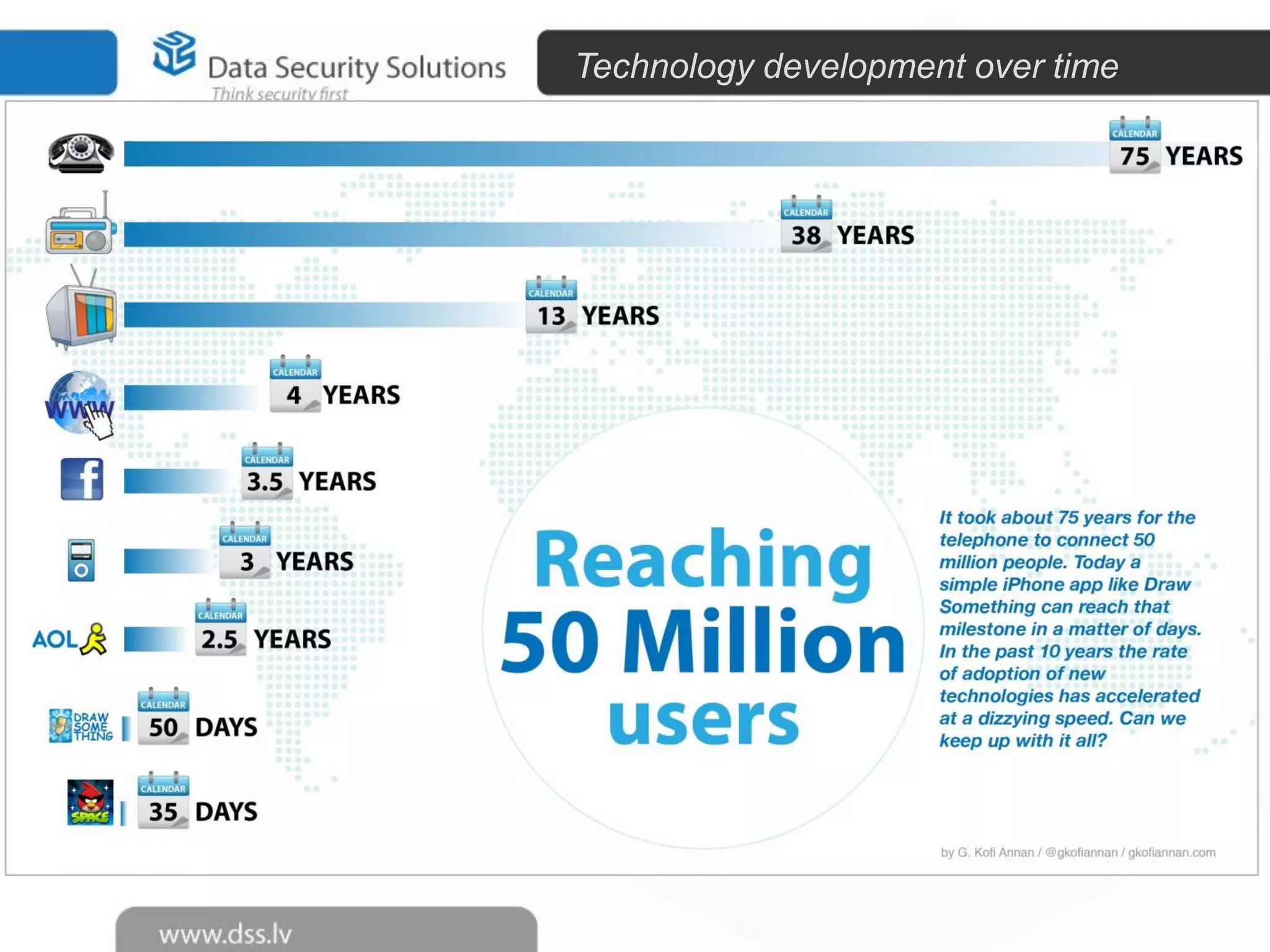
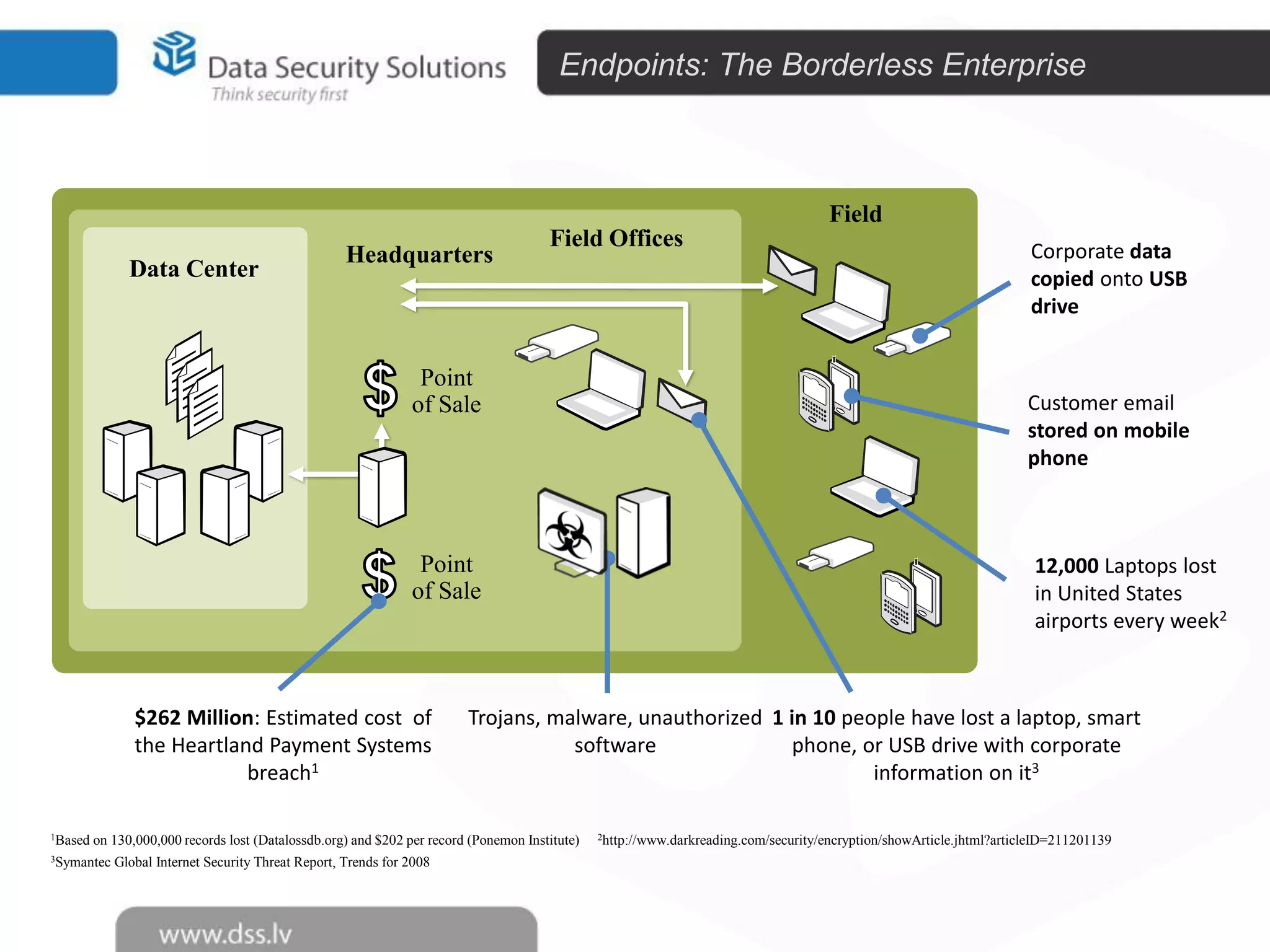
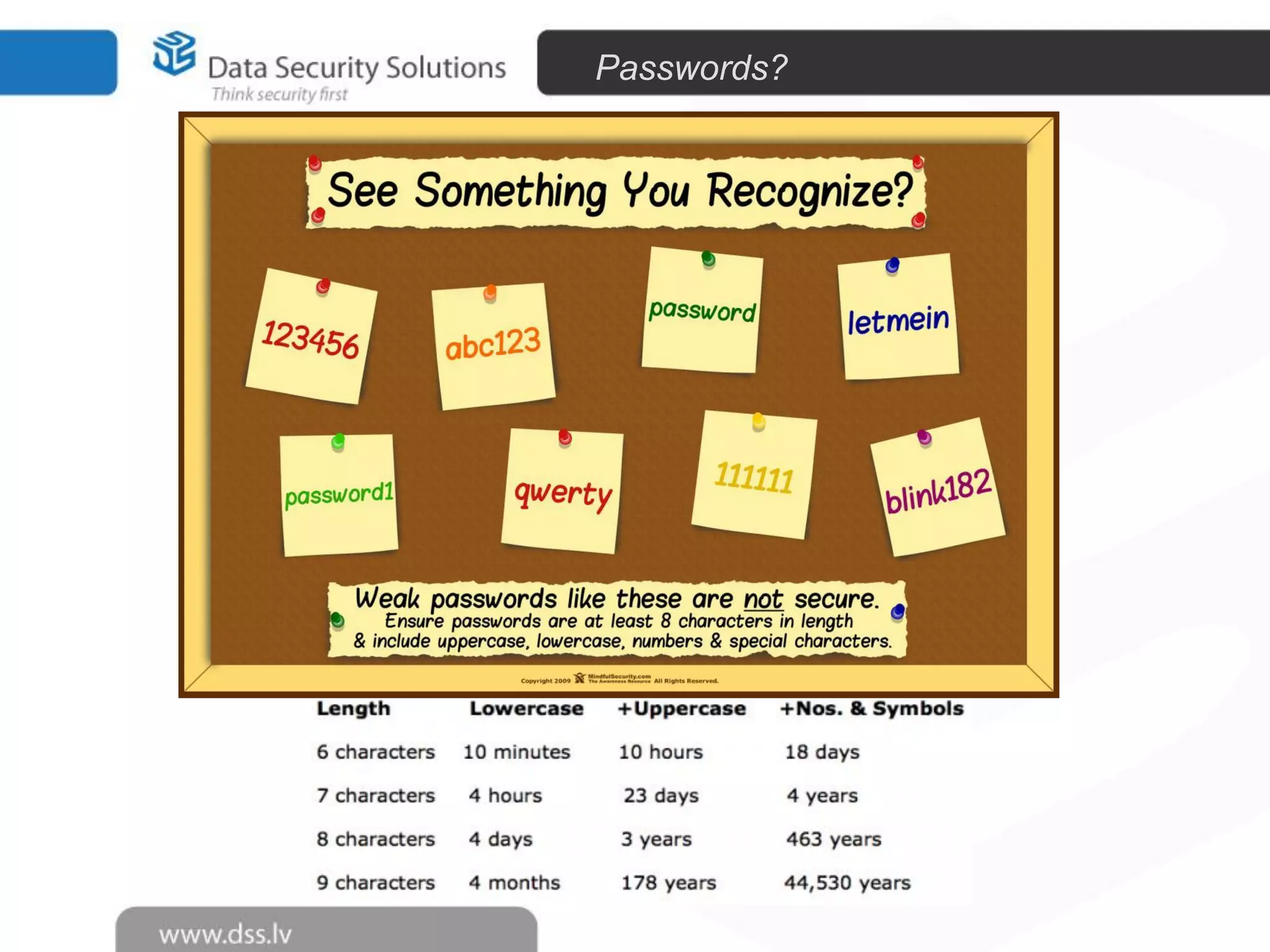
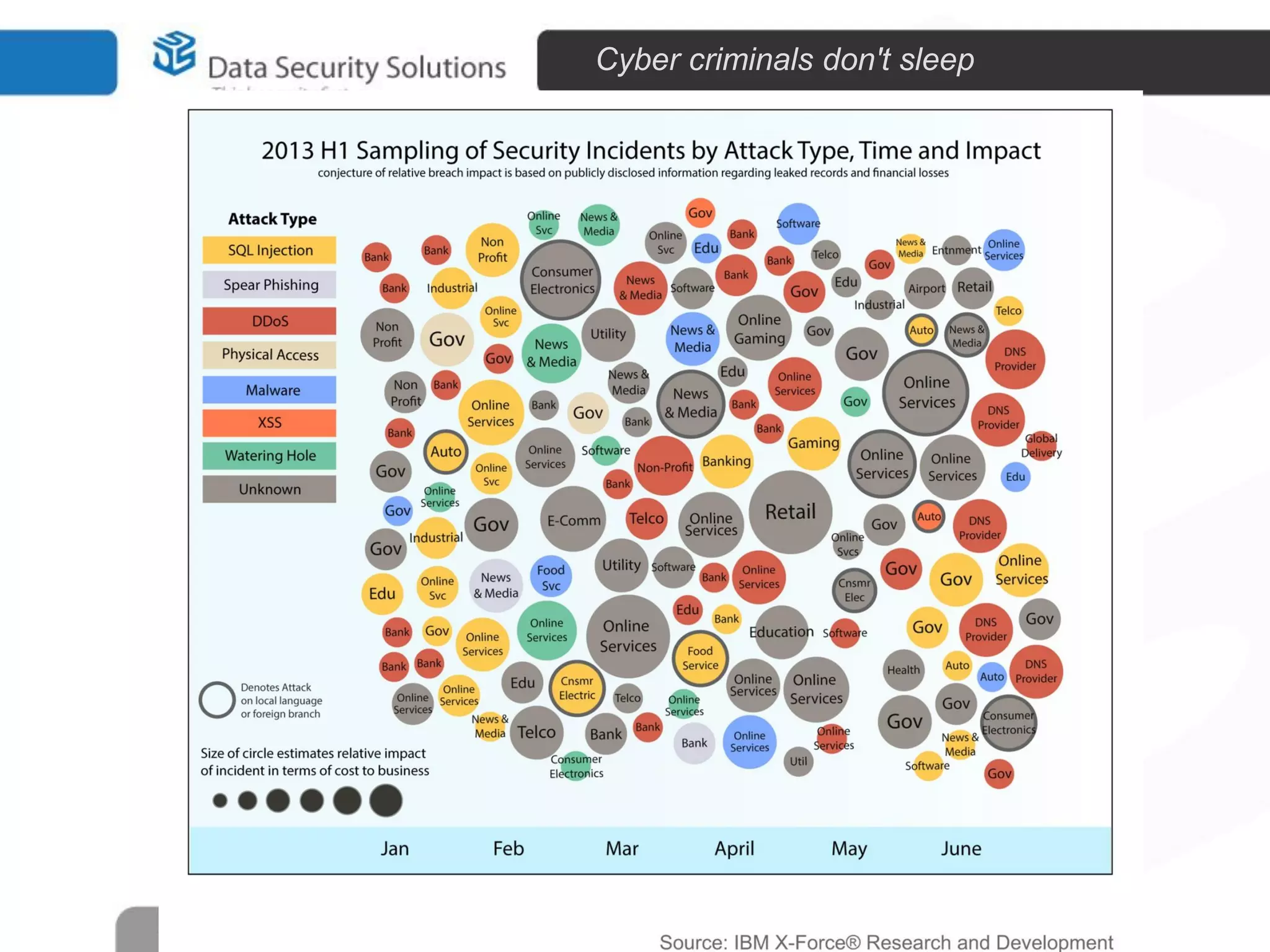
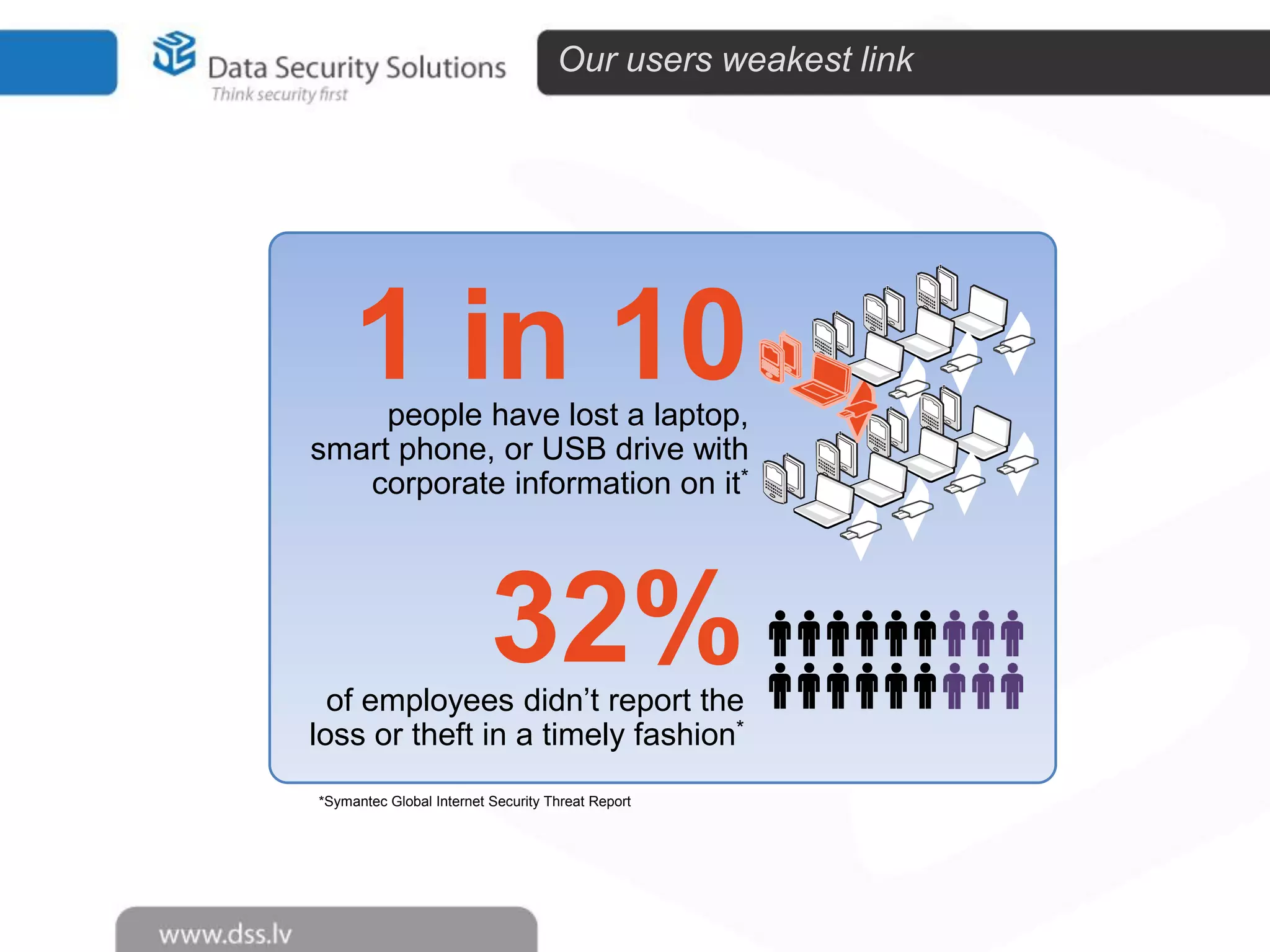
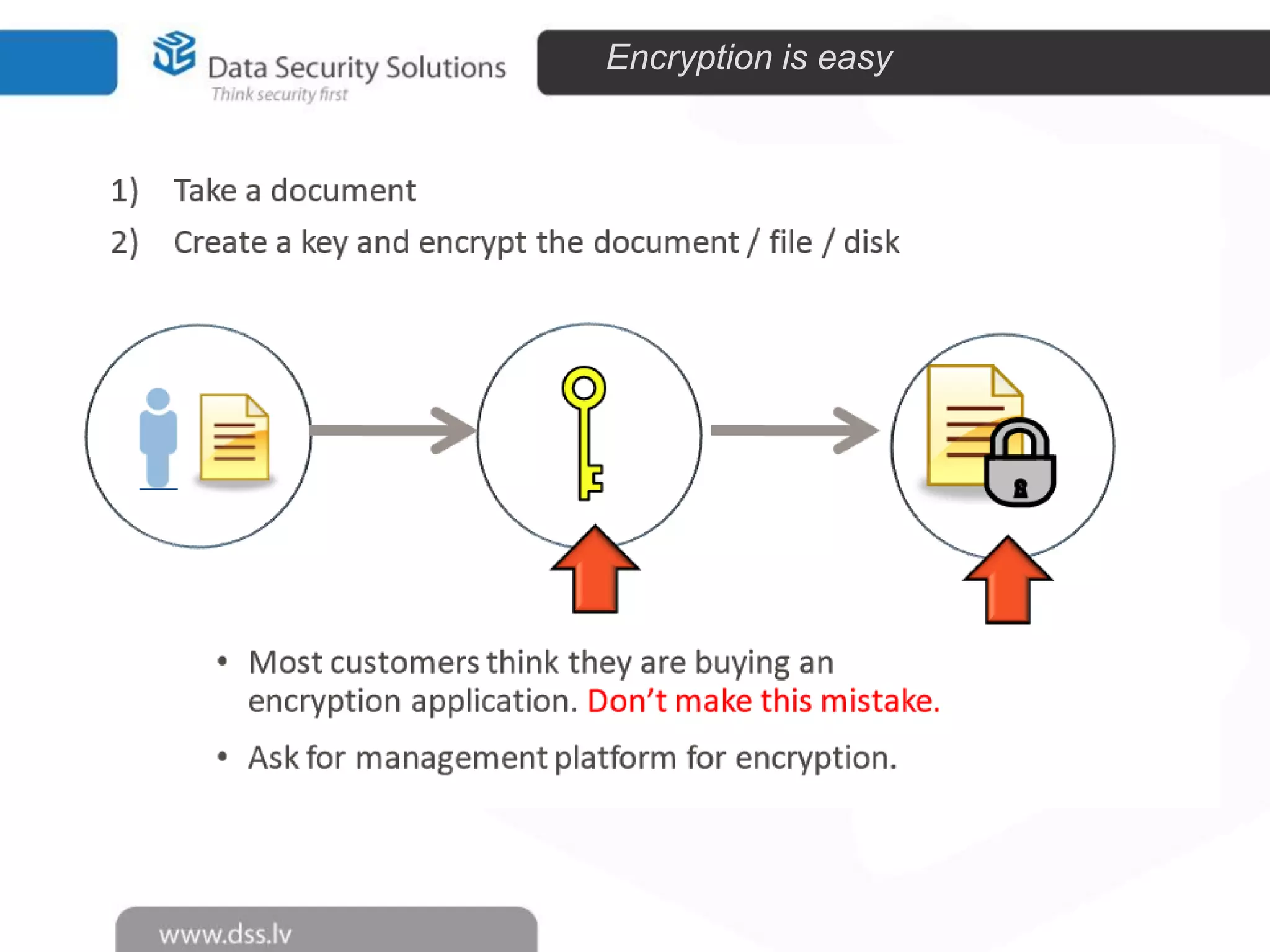
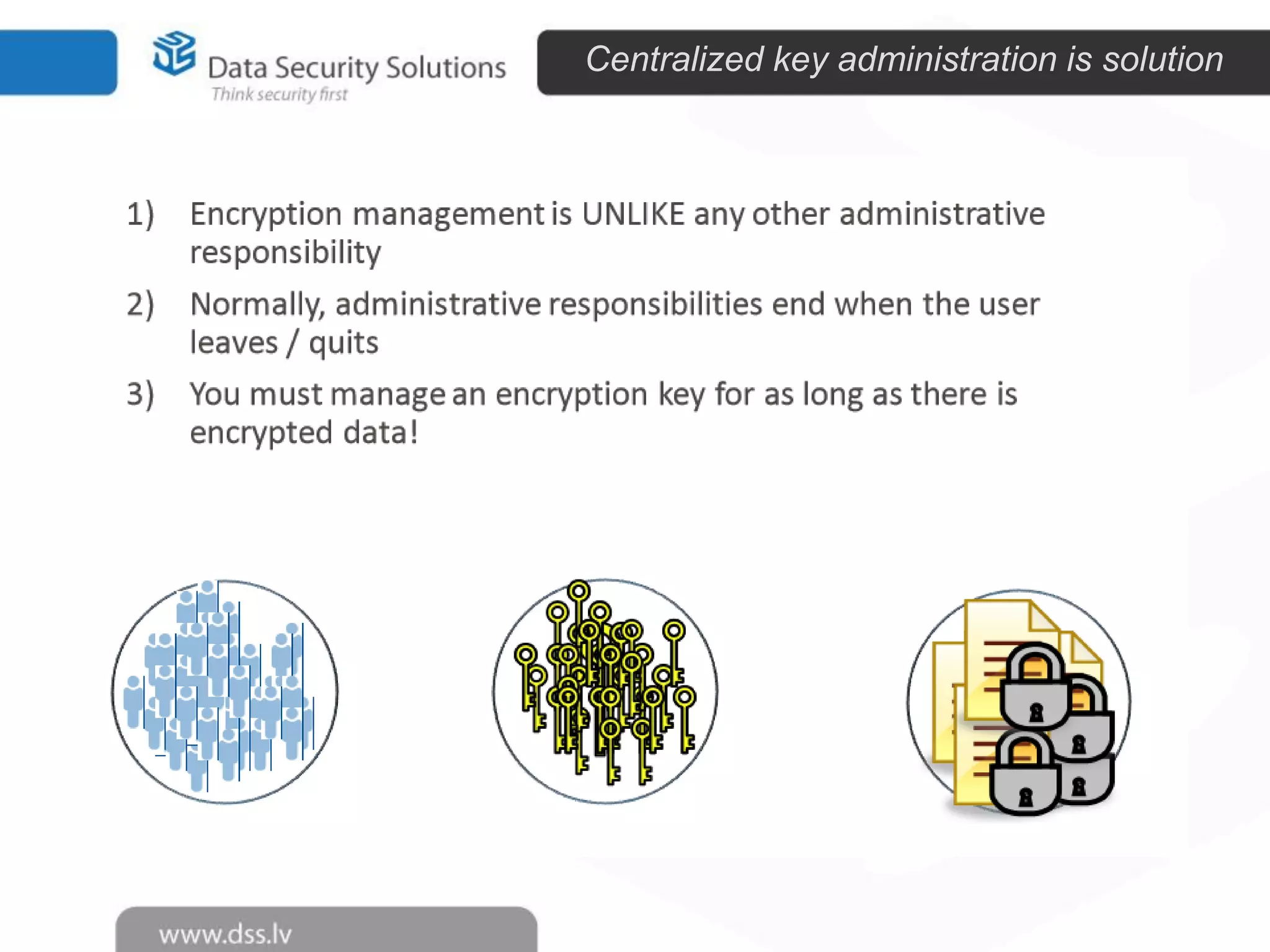
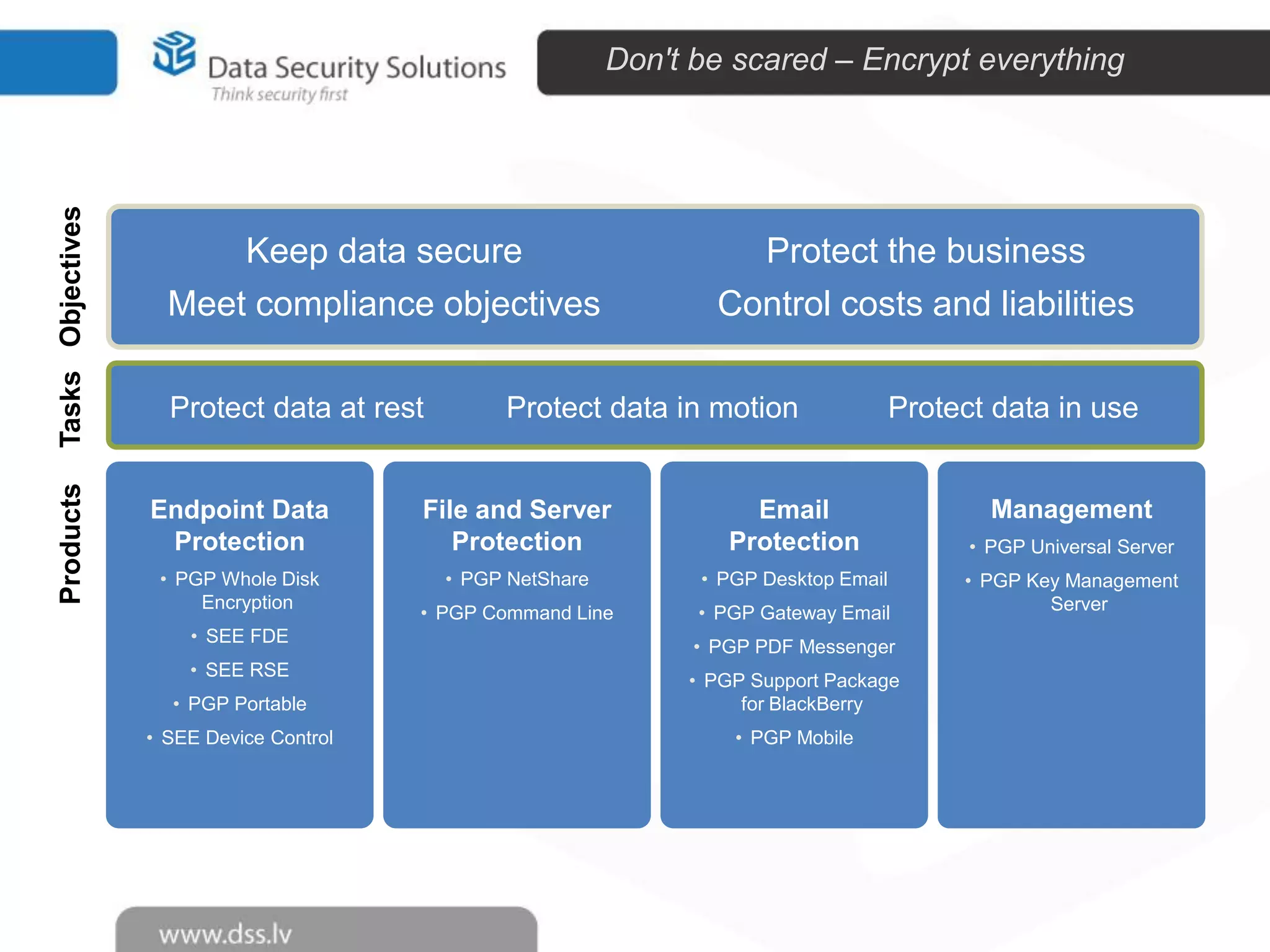
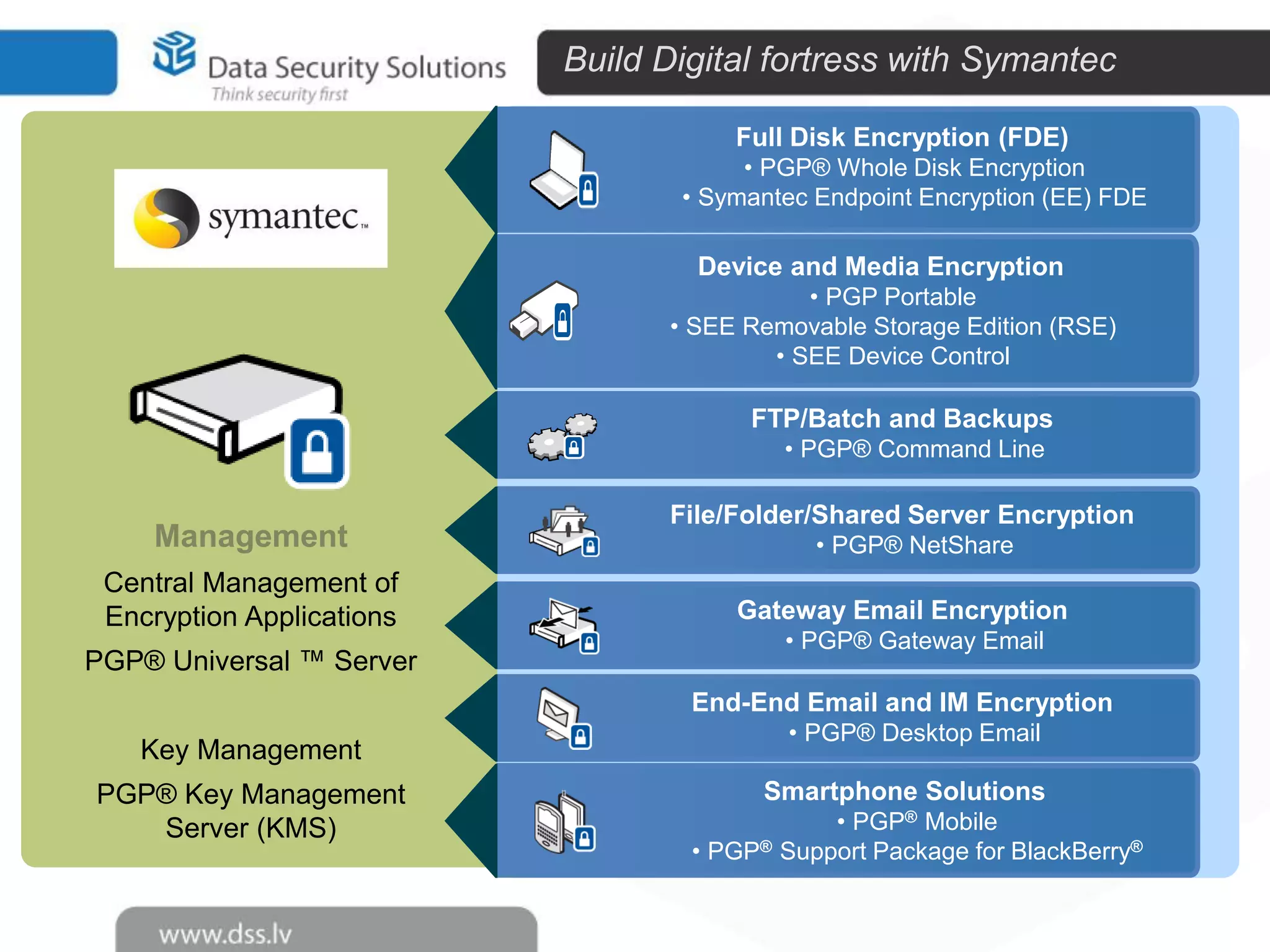
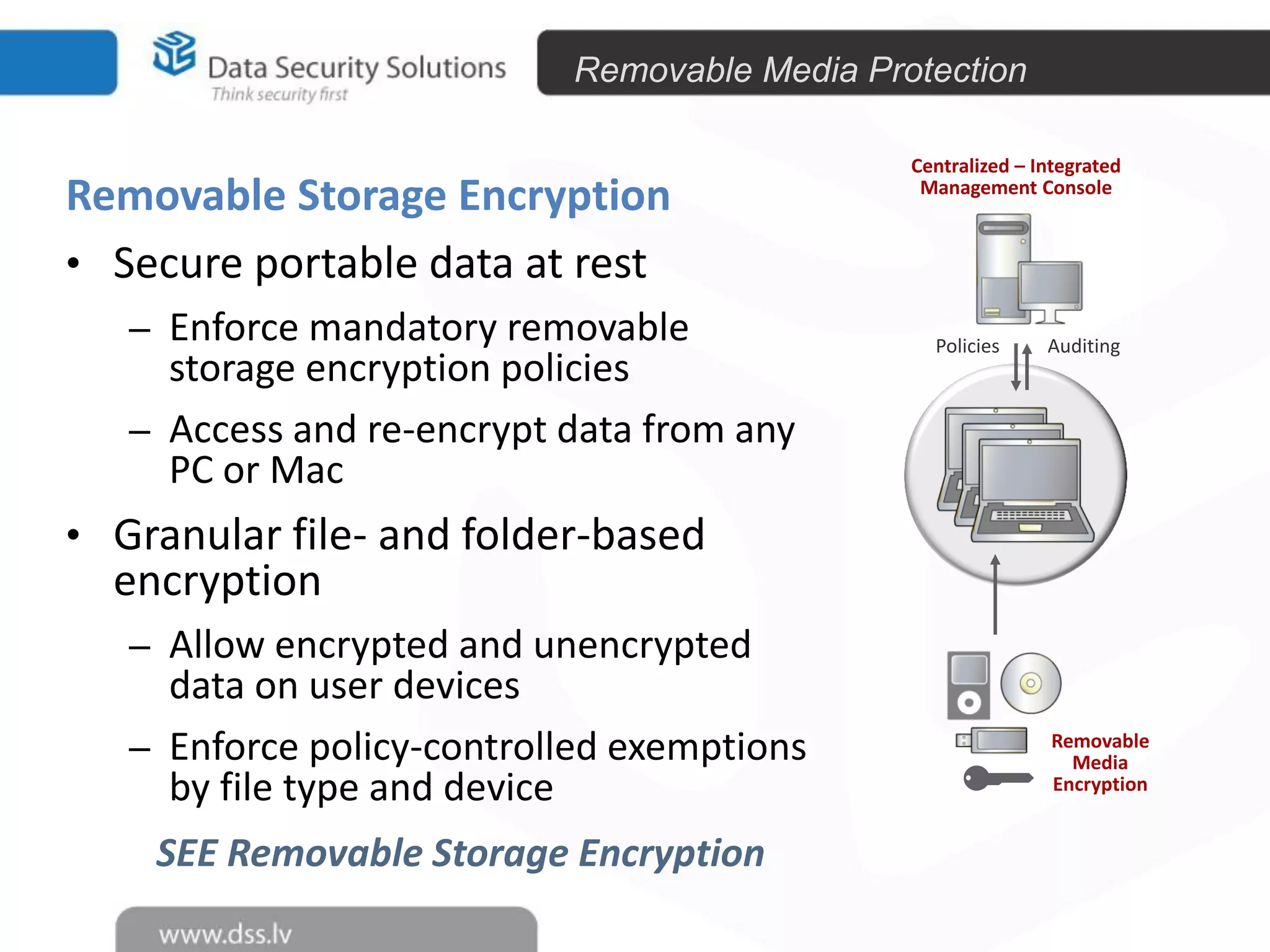
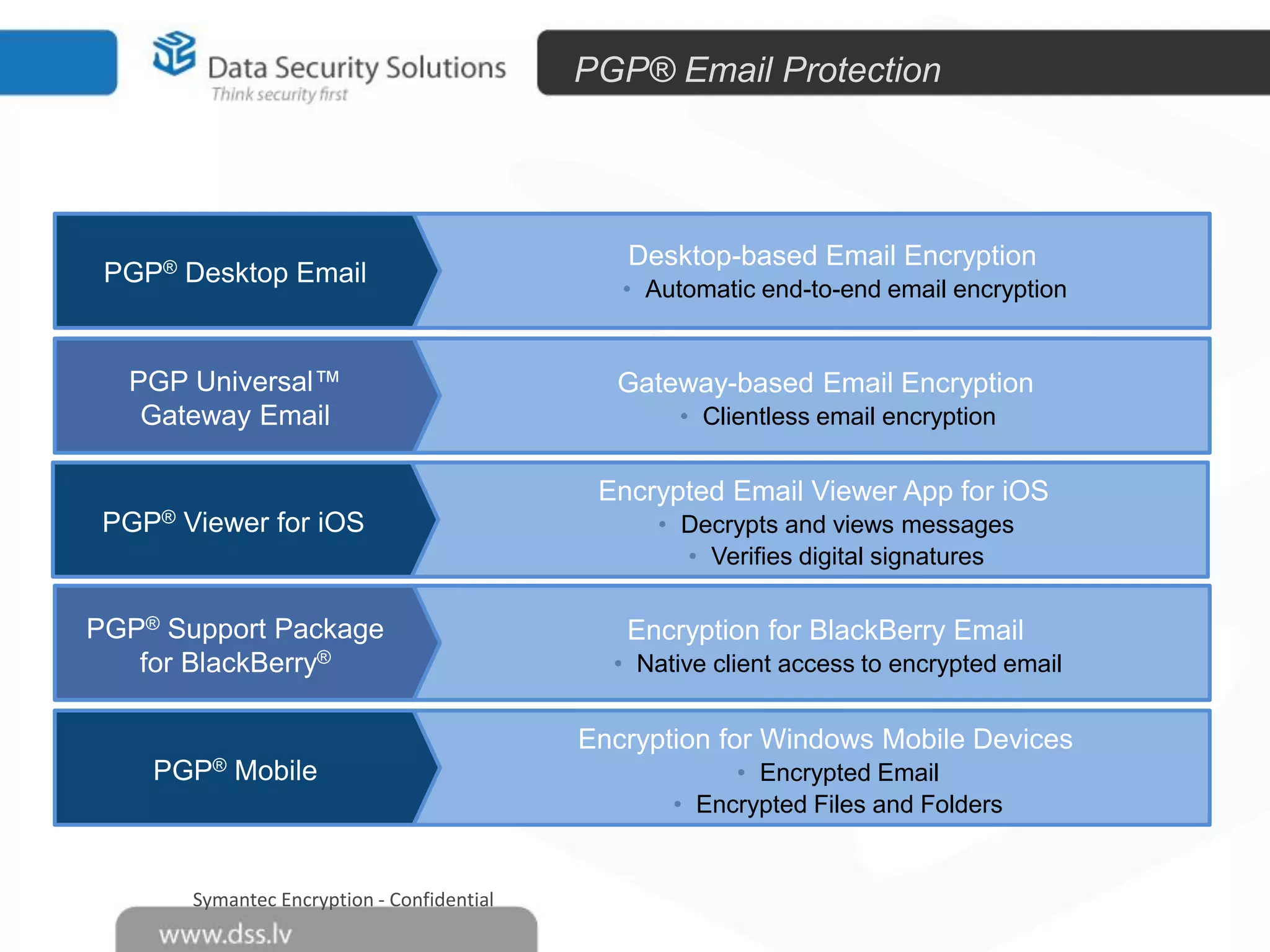
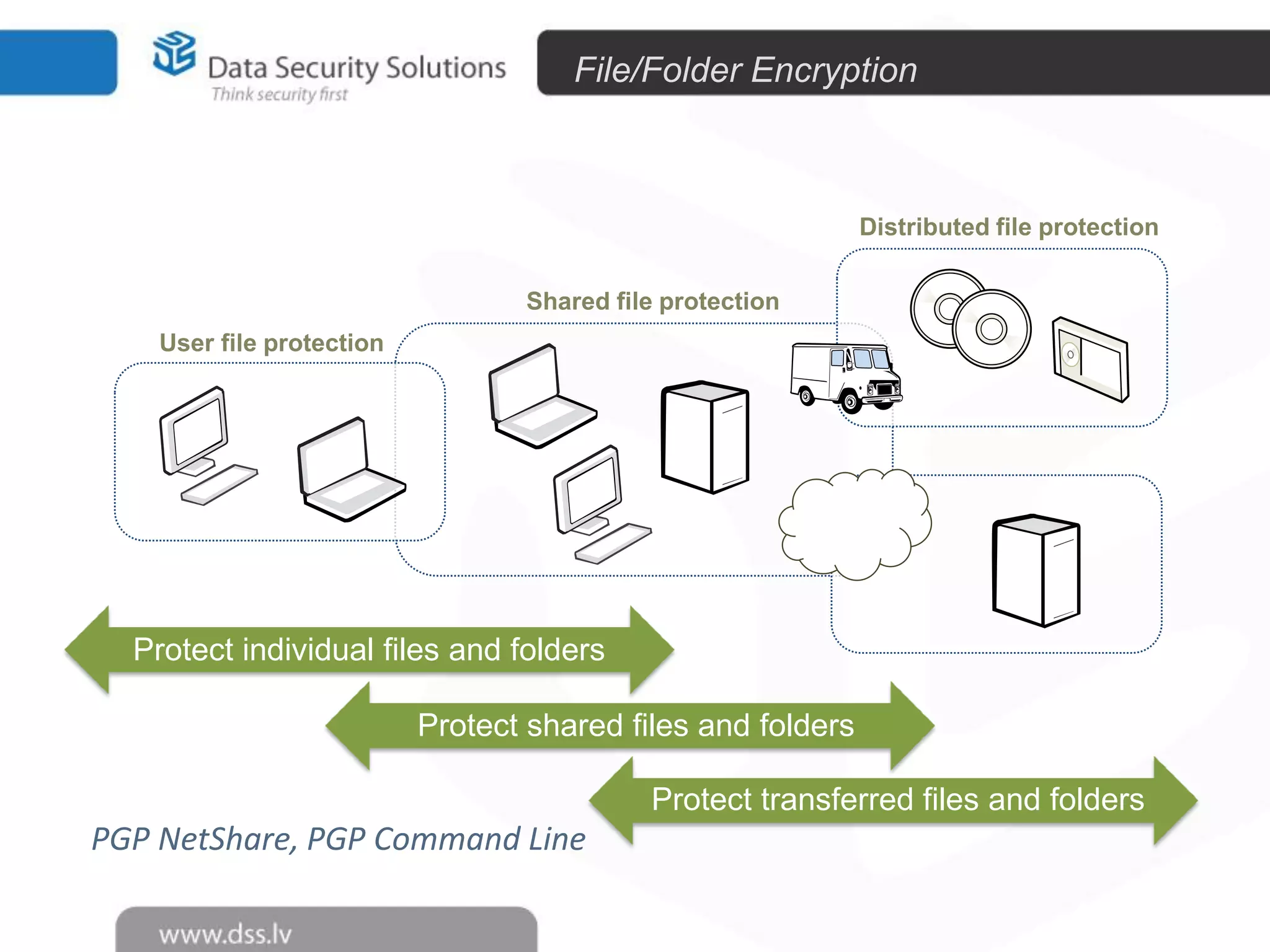
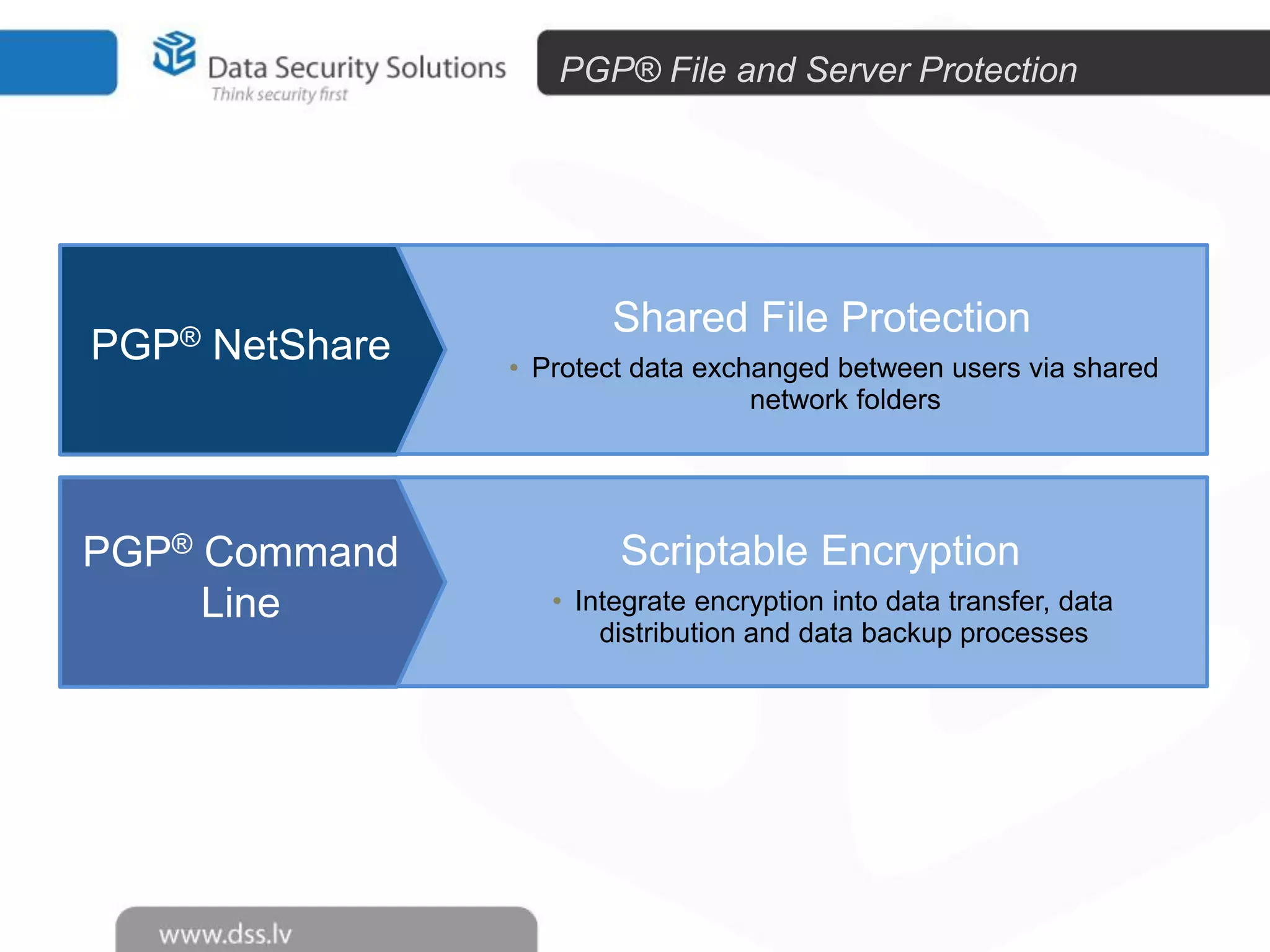
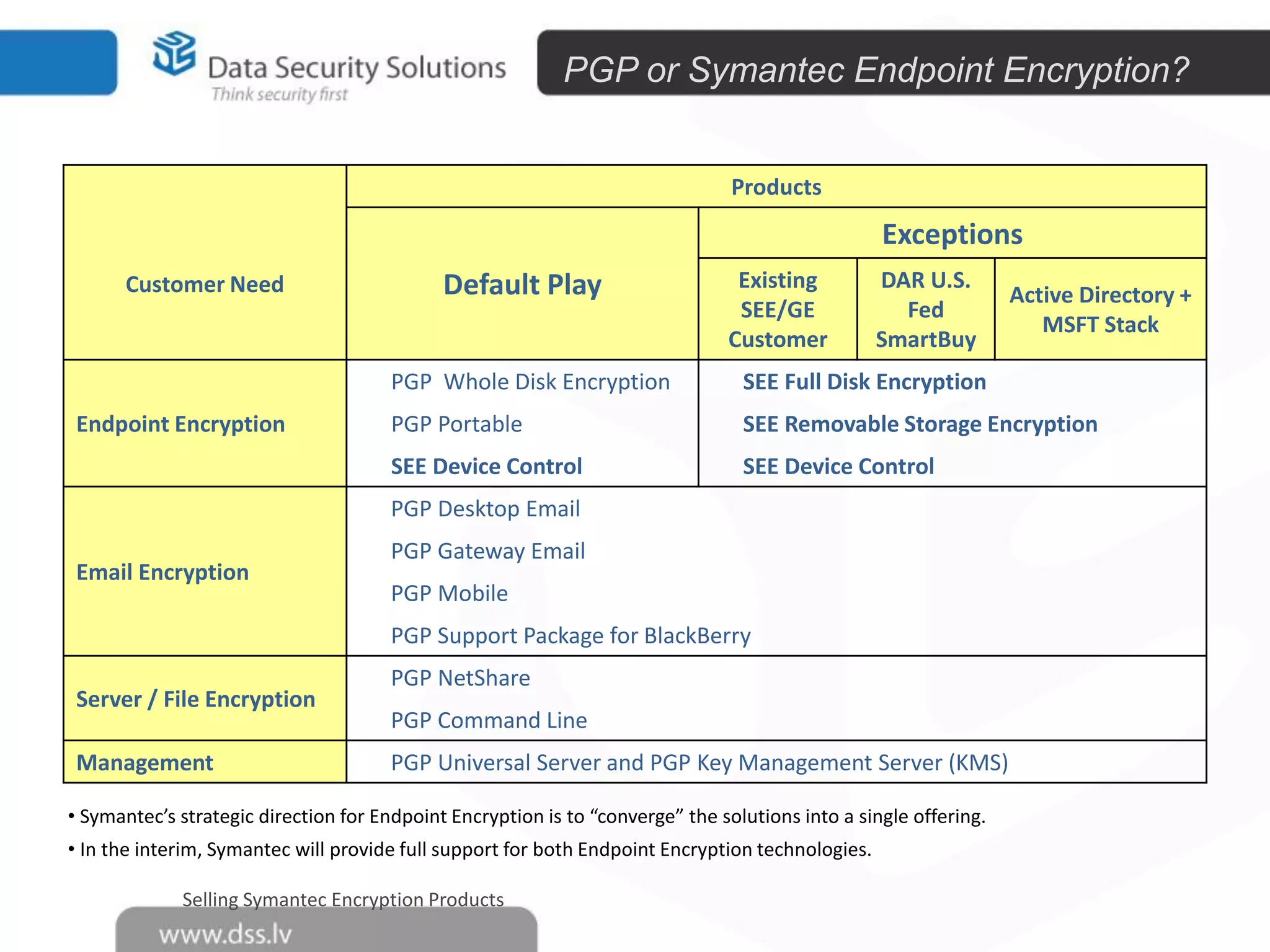
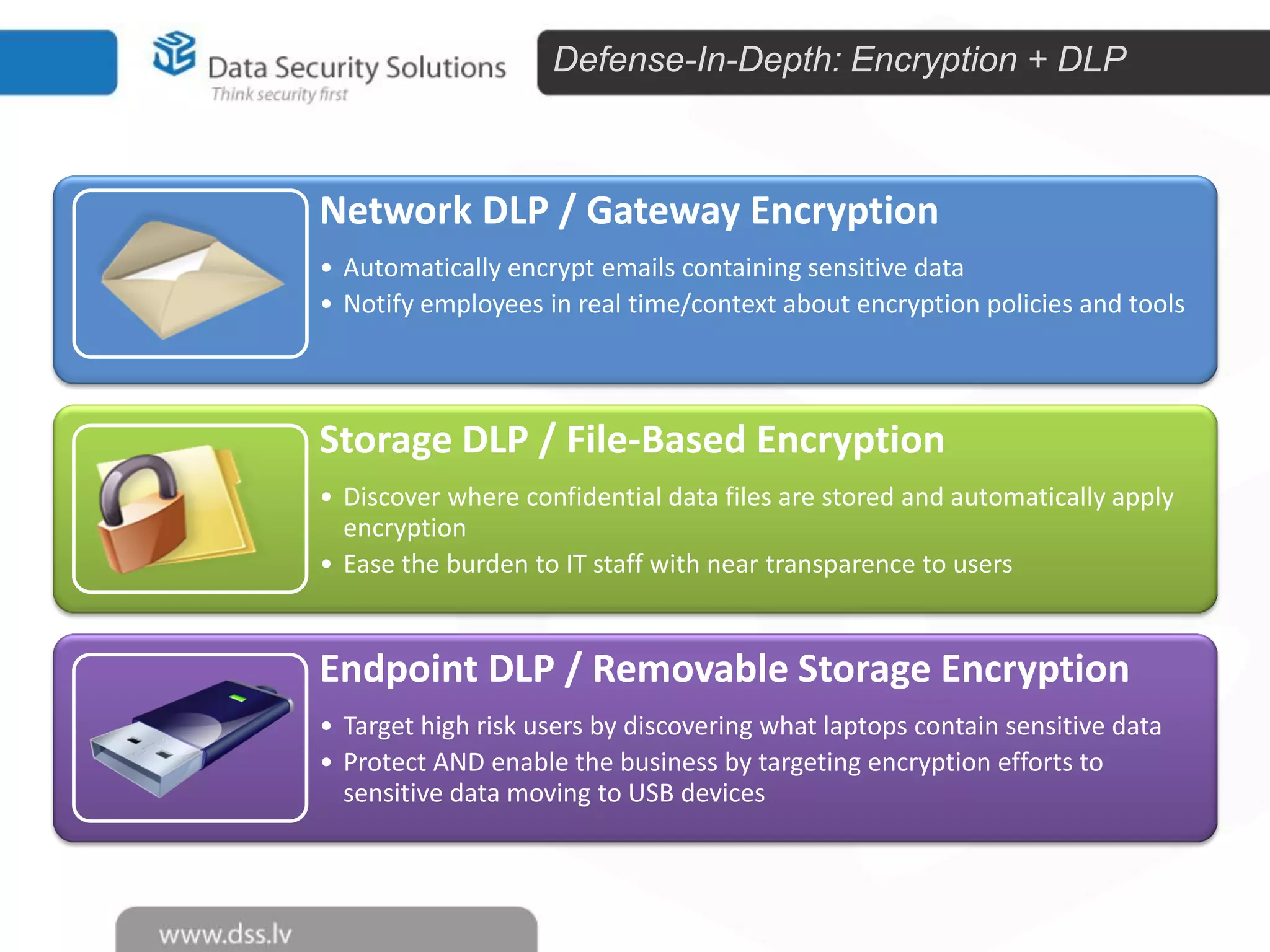
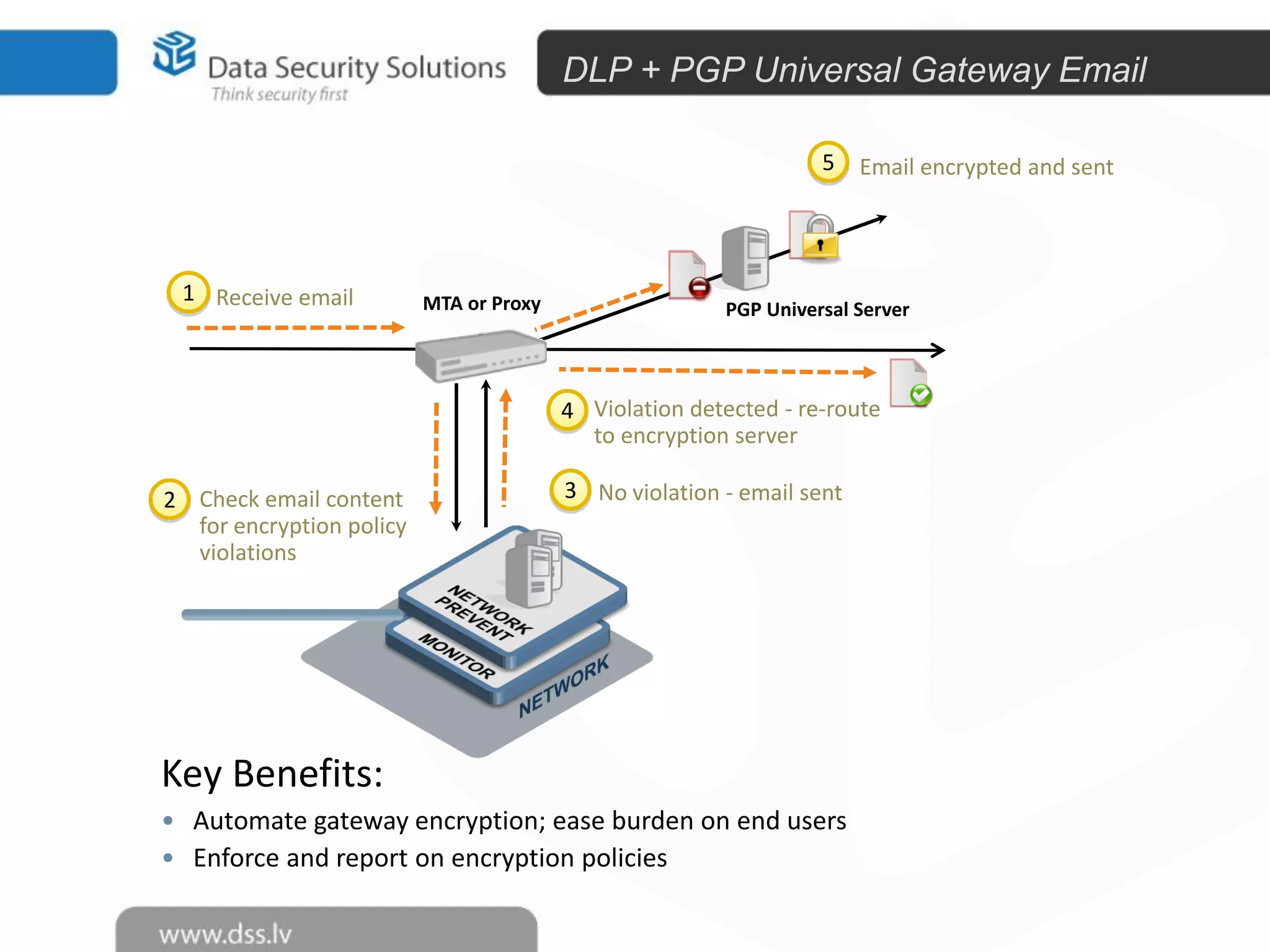
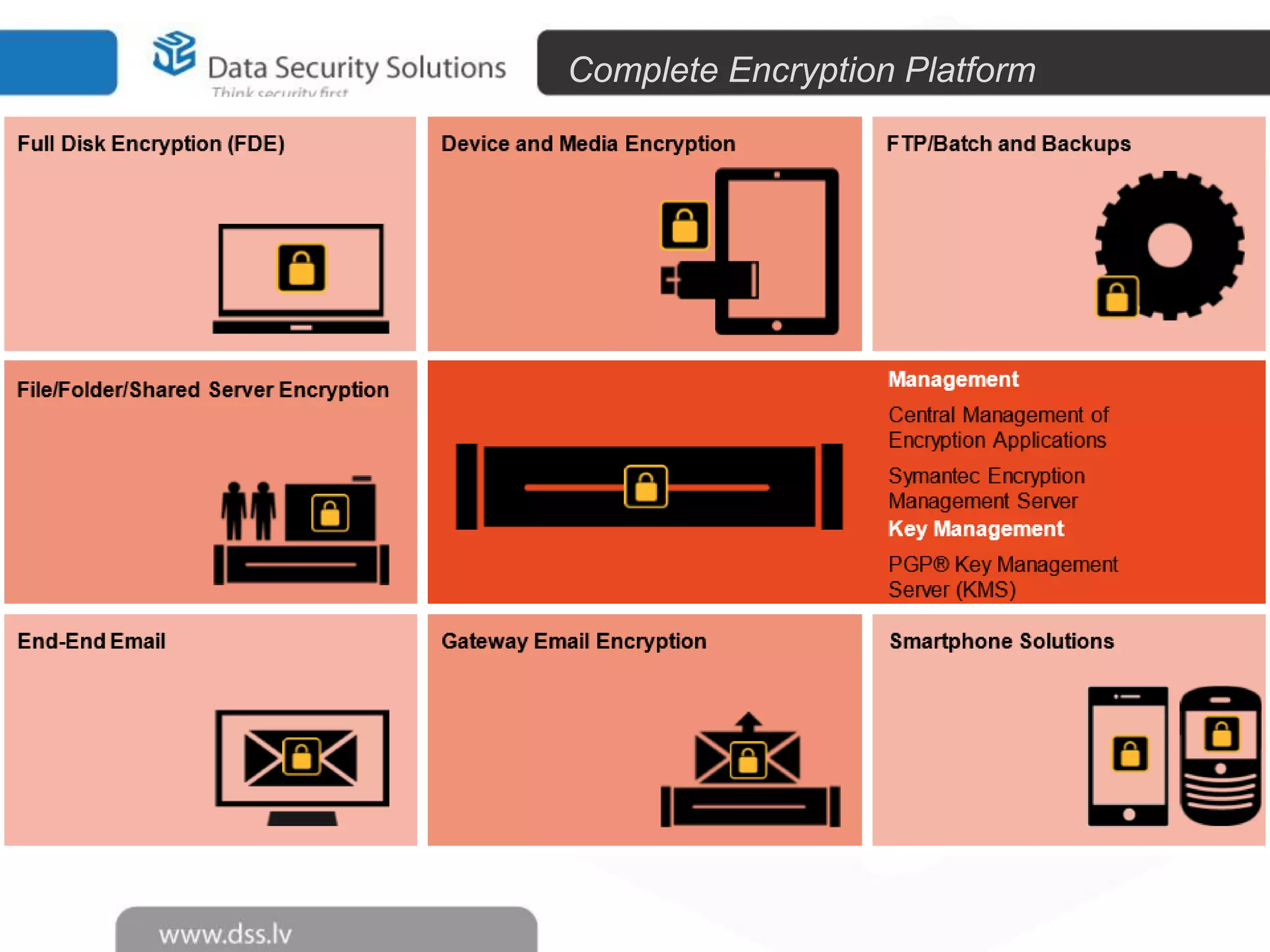
The document outlines the importance of encryption in cyber security, highlighting its role in protecting data and meeting compliance objectives. It discusses the evolution of technology from desktop to mobile and emphasizes the need for robust data security solutions as mobility increases the risk of data loss. Additionally, it presents Symantec's encryption offerings as essential tools for businesses to build a digital fortress against cyber threats.