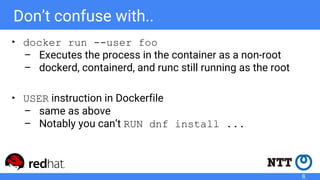
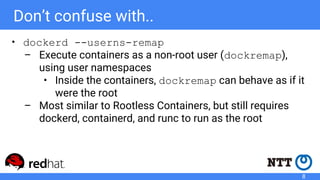
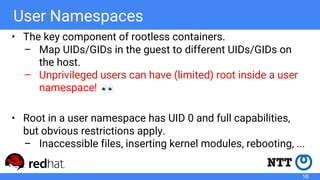
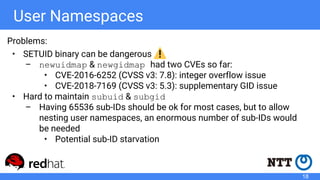
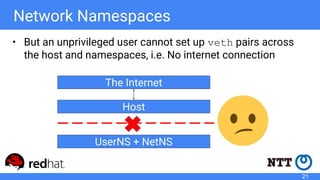
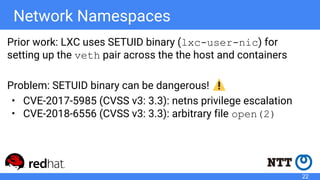
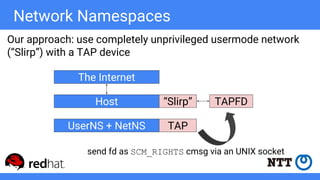
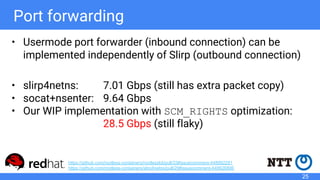
The document discusses rootless containers, which allow unprivileged users to create and manage containers without requiring root access, primarily for security and user isolation purposes. It highlights the importance of user namespaces, the vulnerabilities of traditional container runtimes, and the implementation details of various container technologies like Podman, Buildah, and Kubernetes in relation to rootless functionality. Additionally, it addresses the current status and challenges of adopting rootless containers and the integration of related tools in different environments.






![User Namespaces
• To allow multi-user mappings, shadow-utils provides newuidmap and
newgidmap (packaged by most distributions).
– SETUID binaries writing mappings configured in /etc/sub[ug]id
/etc/subuid:
1000:420000:65536
/proc/42/uid_map:
0 1000 1
1 420000 65536
Provided by the admin (real root)
User can configure map UIDs after
unsharing a user namespace
17](https://image.slidesharecdn.com/devconfcz2019rootlesscontainers-190125124744/85/Rootless-Containers-17-320.jpg)








![runc
• Supports rootless mode since 1.0.0-rc4 (merged March
2017).
• Since 1.0.0-rc5 (Feb 2018):
– /sys/fs/cgroup can be used if they are set up to be
writable.
– Multi-user mappings are supported if they are set up
with /etc/sub[ug]id.
33](https://image.slidesharecdn.com/devconfcz2019rootlesscontainers-190125124744/85/Rootless-Containers-33-320.jpg)