The document presents 'DriverGuard', an insertable hypervisor designed to enhance the security of device drivers by utilizing VM introspection and stealth breakpoints. It addresses vulnerabilities in device drivers that can be exploited through various attack vectors without disrupting system operations, aimed particularly at critical infrastructure systems. The implementation and performance evaluation indicate that DriverGuard effectively protects sensitive regions and maintains acceptable overhead for sensitive data accesses.

![National Institute of Advanced Industrial Science and Technology
Motivation 2/2Motivation 2/2
• Are De ice Dri ers safe?• Are Device Drivers safe?
– Device Drivers were thought to be safe since they run in
privilege mode However device drivers become a target ofprivilege mode. However, device drivers become a target of
attacks as the importance is increased, and vulnerabilities are
revealed.
– Stuxnet[5] and Duqu[3] are famous attacks for device drivers.
• They are targeted attacks on nuclear reactor, chemical plant, etc.y g p
– If target device driver works on a critical infrastructure, the
availability is important. The countermeasures must be taken
without stopping the operating system.](https://image.slidesharecdn.com/iwsec14-suzaki-140827192940-phpapp02/75/Kernel-Memory-Protection-by-an-Insertable-Hypervisor-which-has-VM-Introspection-and-Stealth-Breakpoints-IWSEC2014-4-2048.jpg)


![National Institute of Advanced Industrial Science and Technology
Insertable HypervisorInsertable Hypervisor
• Thin type-I (bare-metal) hypervisor
P th h hit t (BitVi [VEE’09])– Para-passthrough architecture (BitVisor[VEE’09])
• No Device Model. Guest OS can access devices directly.
Small Trusted Computing Base (TCB)– Small Trusted Computing Base (TCB)
• No HostOS make small TCB.
• DriverGuard uses Chainload function of GRUB boot loader• DriverGuard uses Chainload function of GRUB boot-loader.
BIOSExisting System
GRUB D i G d
Go back to GRUBApplications
(User Space)
GRUB DriverGuard
(resides in memory)
chain loader
Preinstalled OS
DriverGuard
(hypervisor) Insert at boot time
NTLDR Windows
(Windows Bootloader)
(hypervisor)
Hardware](https://image.slidesharecdn.com/iwsec14-suzaki-140827192940-phpapp02/75/Kernel-Memory-Protection-by-an-Insertable-Hypervisor-which-has-VM-Introspection-and-Stealth-Breakpoints-IWSEC2014-8-2048.jpg)
![National Institute of Advanced Industrial Science and Technology
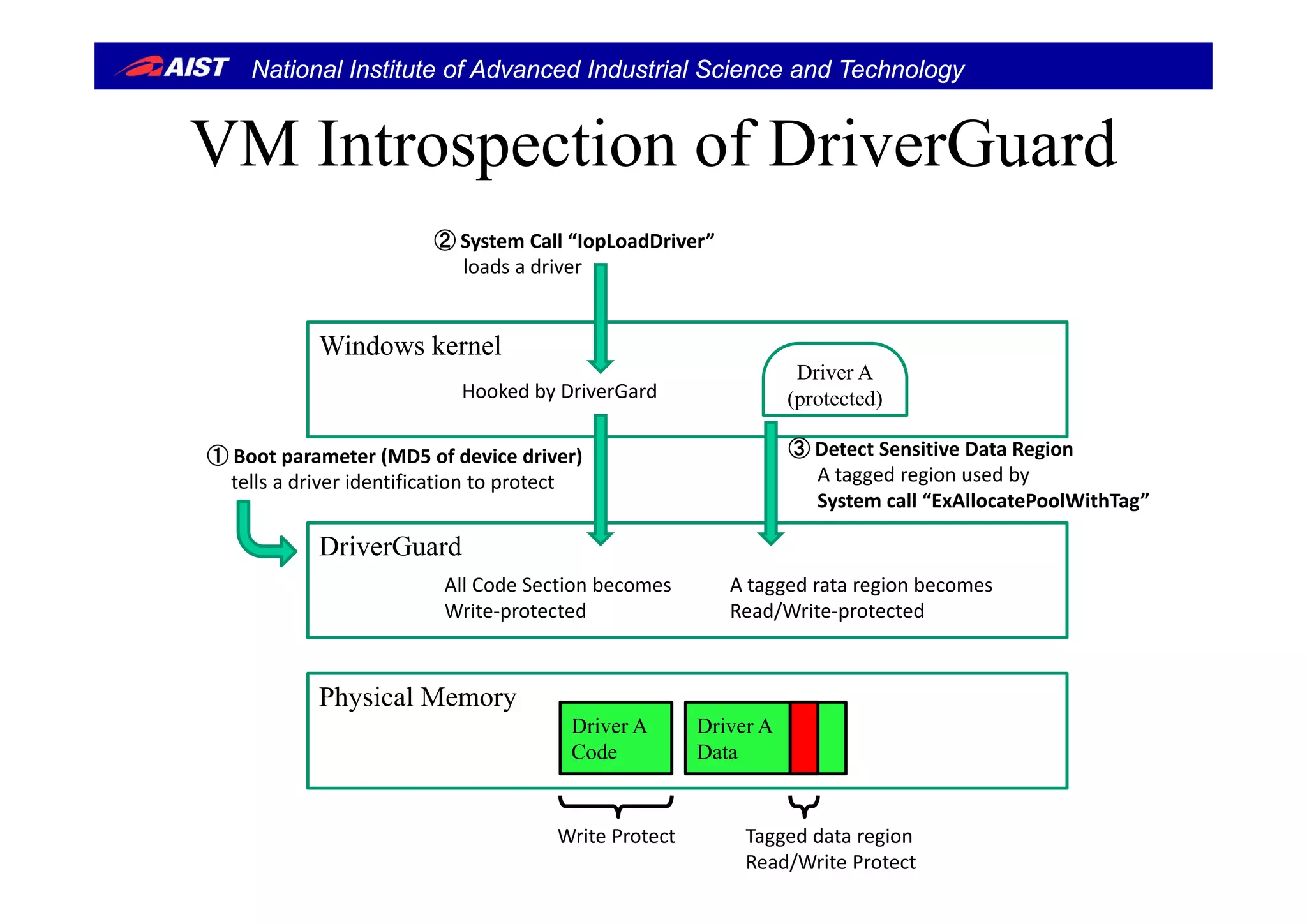
VM IntrospectionVM Introspection
• DriverGuard must recognize the memory map and
behavior of the guest OS since it needs to know memory
regions for code and sensitive data. The function is called
“VM introspection”.
– Ether[CCS’08] on Xen, LibVM on KVM, Xen, and QEMU.
– Unfortunately, they requires Host OS and Device Model.
• DriverGuard uses GreenKiller [BlackHat’08]
– GreenKiller has VM Introspection which is built on BitVisor– GreenKiller has VM Introspection which is built on BitVisor.
Unfortunately, GreenKiller is designed for Windows XP which
has no ASLR (Address Space Layout Randomization).( p y )](https://image.slidesharecdn.com/iwsec14-suzaki-140827192940-phpapp02/75/Kernel-Memory-Protection-by-an-Insertable-Hypervisor-which-has-VM-Introspection-and-Stealth-Breakpoints-IWSEC2014-9-2048.jpg)
![National Institute of Advanced Industrial Science and Technology
VM Introspection for ASLRVM Introspection for ASLR
• ASLR (Address Space Layout Randomization).( p y )
– It allocates the starting address of code and data at random
and prevents attacks which assume fixed address (e.g., buffer
overflow attack).
– Some implementations of ASLR have little entropy and are
vulnerable for Brute Force Attack [CCS’04].
• DriverGuard uses the technique of brute force attack
– The search space is not wide. DriverGuard checks the header
(44 bytes) of each page of kernel space.](https://image.slidesharecdn.com/iwsec14-suzaki-140827192940-phpapp02/75/Kernel-Memory-Protection-by-an-Insertable-Hypervisor-which-has-VM-Introspection-and-Stealth-Breakpoints-IWSEC2014-10-2048.jpg)

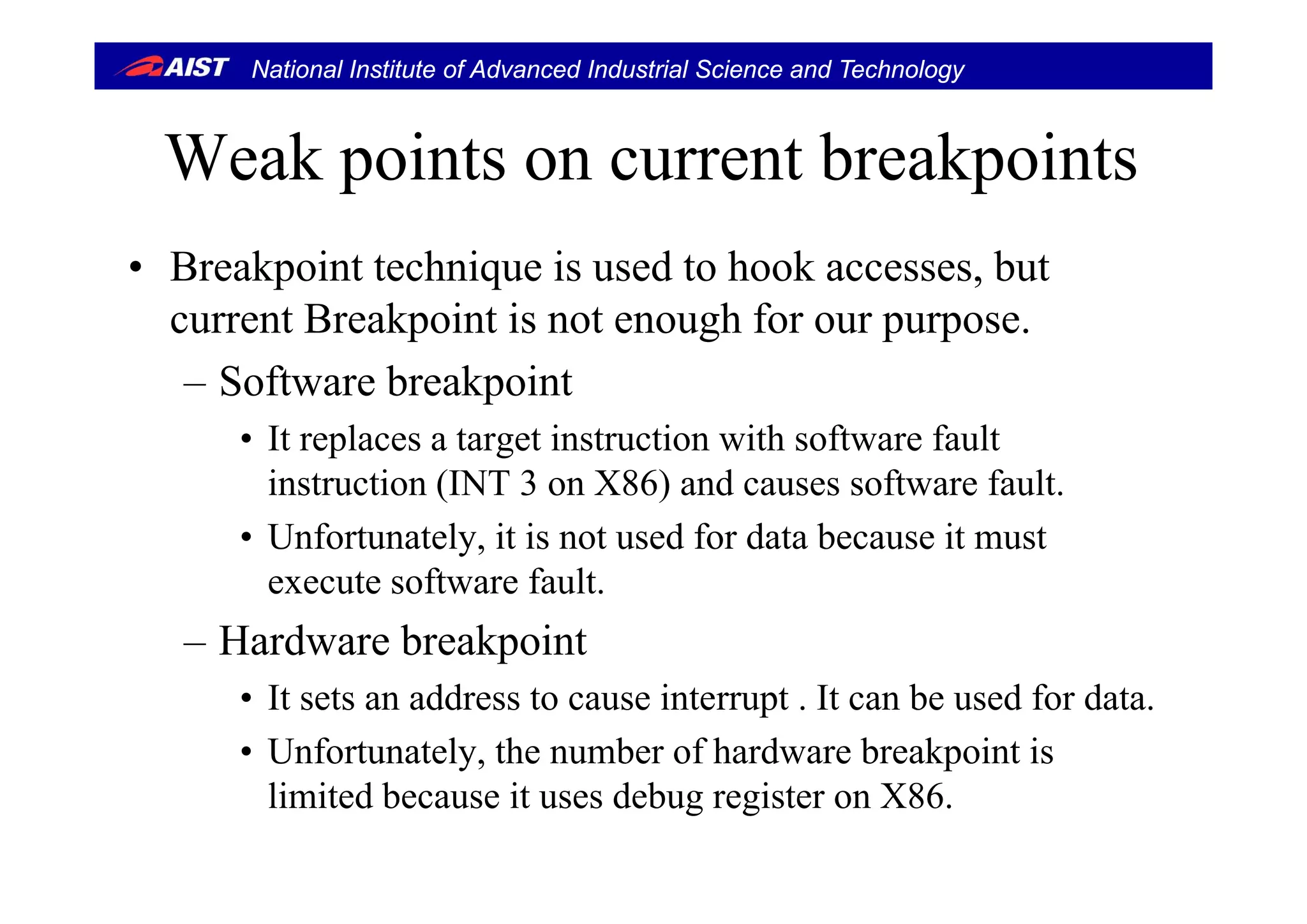
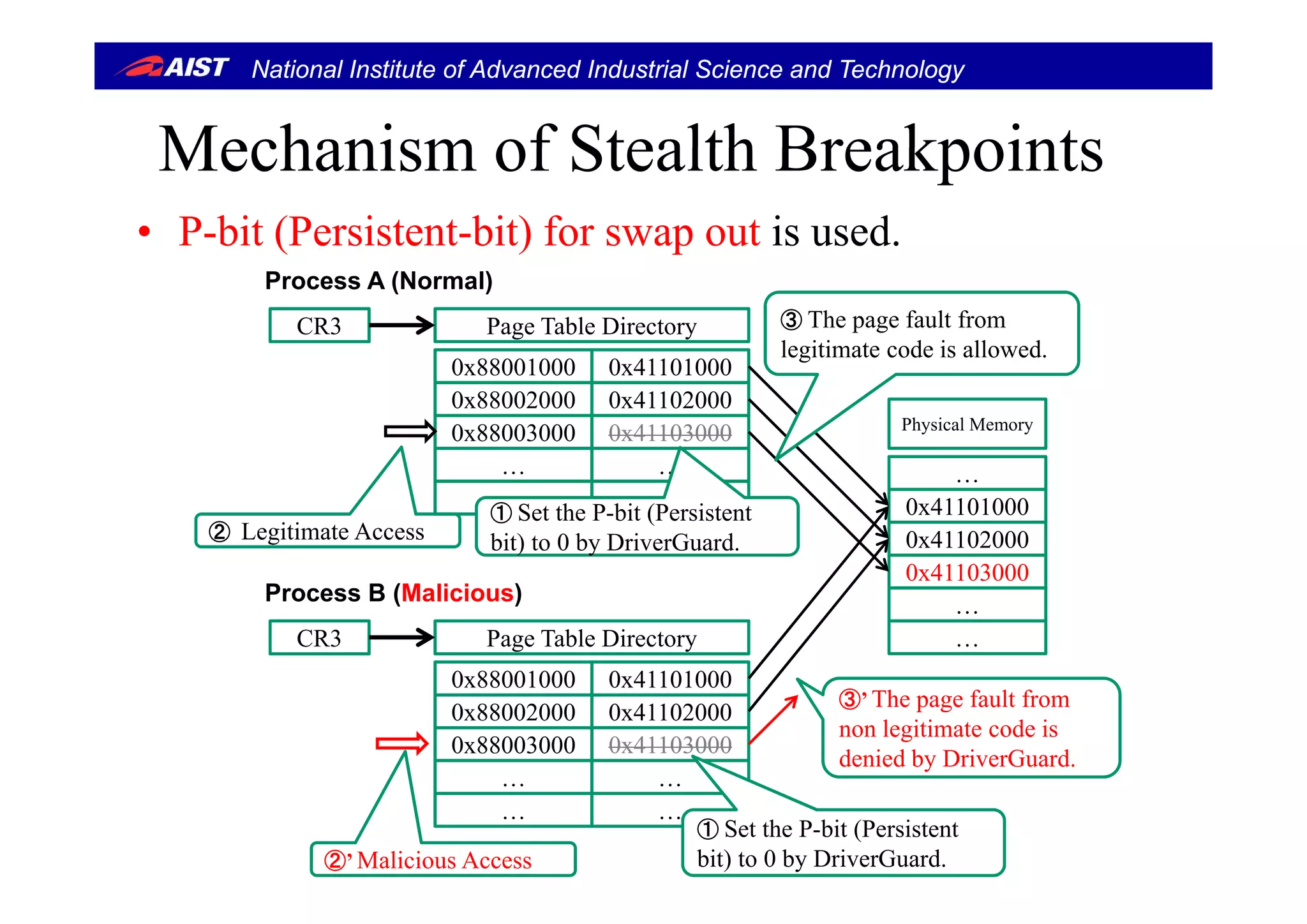
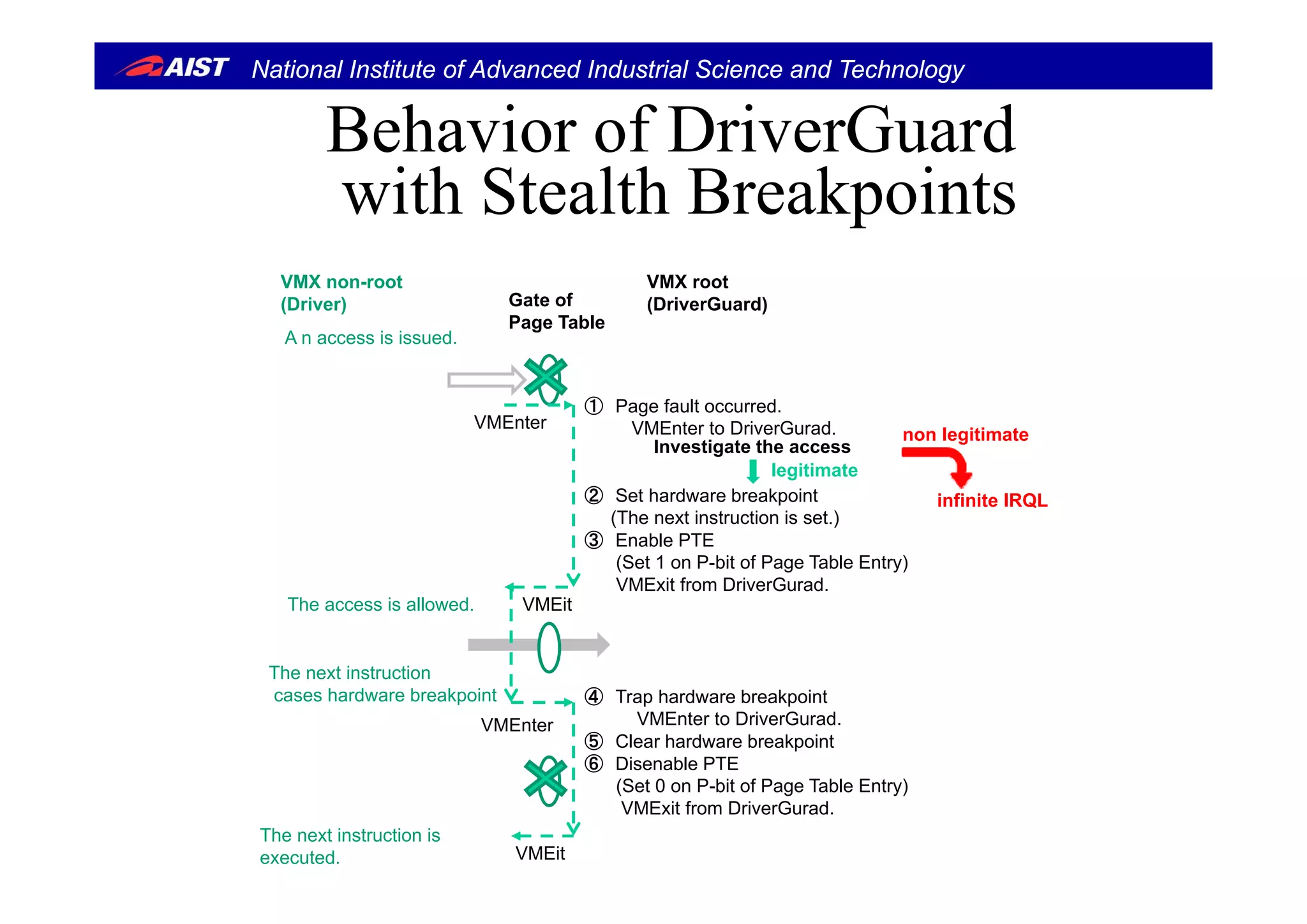
![National Institute of Advanced Industrial Science and Technology
Stealth breakpointsStealth breakpoints [ACSAC’05]
• Stealth Breakpoints is developed to analyze malware• Stealth Breakpoints is developed to analyze malware.
– Because malware detects current breakpoints and changes its
behaviorbehavior.
• Stealth Breakpoints manipulates page table entry (PTE)
and causes page fault when an access come to the breakand causes page fault, when an access come to the break
point.
Pros– Pros
• No limit of the number
• It can treat code and data regionsIt can treat code and data regions
– Cons
• The unit is page (4KB)p g ( )
• Slower than software fault](https://image.slidesharecdn.com/iwsec14-suzaki-140827192940-phpapp02/75/Kernel-Memory-Protection-by-an-Insertable-Hypervisor-which-has-VM-Introspection-and-Stealth-Breakpoints-IWSEC2014-14-2048.jpg)
![National Institute of Advanced Industrial Science and Technology
Implementation of DriverGuardImplementation of DriverGuard
• Dri erG ard is based on BitVisor [VEE’09]• DriverGuard is based on BitVisor [VEE’09]
• Target is Windows 7 (32 bit)
– Limitations
• Page size is 4KB. Windows cannot treat PSE: Page Size Extension.
Hib i i d• Hibernation is not treated.
• Device Driver is loaded with IopLoadDriver system call.
• Sensitive data is allocated by tagged memory (which causes SystemSensitive data is allocated by tagged memory (which causes System
call “ExAllocatePoolWithTag”)
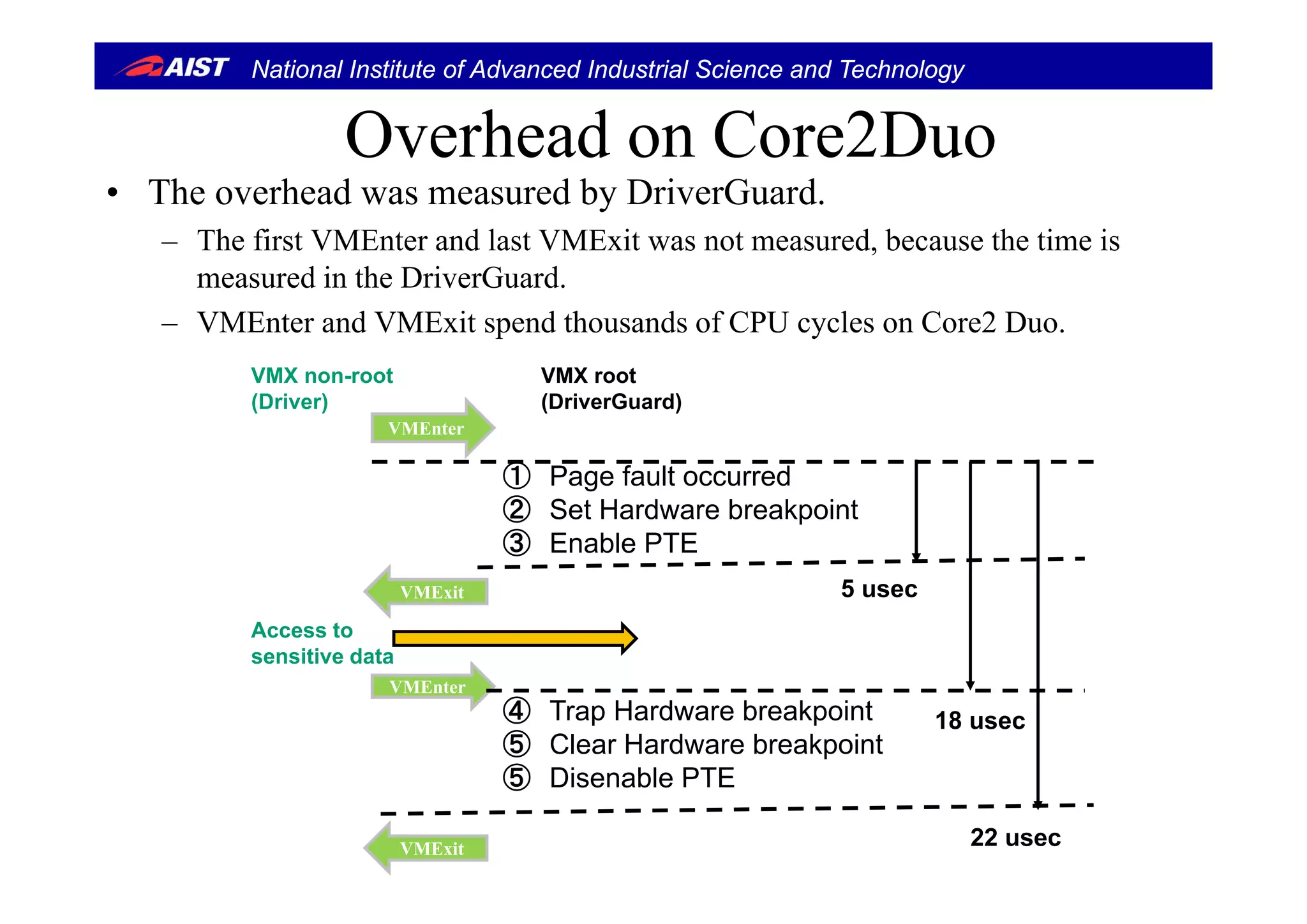
• Core2 Duo E6850 (3GHz)( )
– DriverGuard uses 170 MB memory.
• It means that the memory for Windows 7 is reduced.](https://image.slidesharecdn.com/iwsec14-suzaki-140827192940-phpapp02/75/Kernel-Memory-Protection-by-an-Insertable-Hypervisor-which-has-VM-Introspection-and-Stealth-Breakpoints-IWSEC2014-17-2048.jpg)
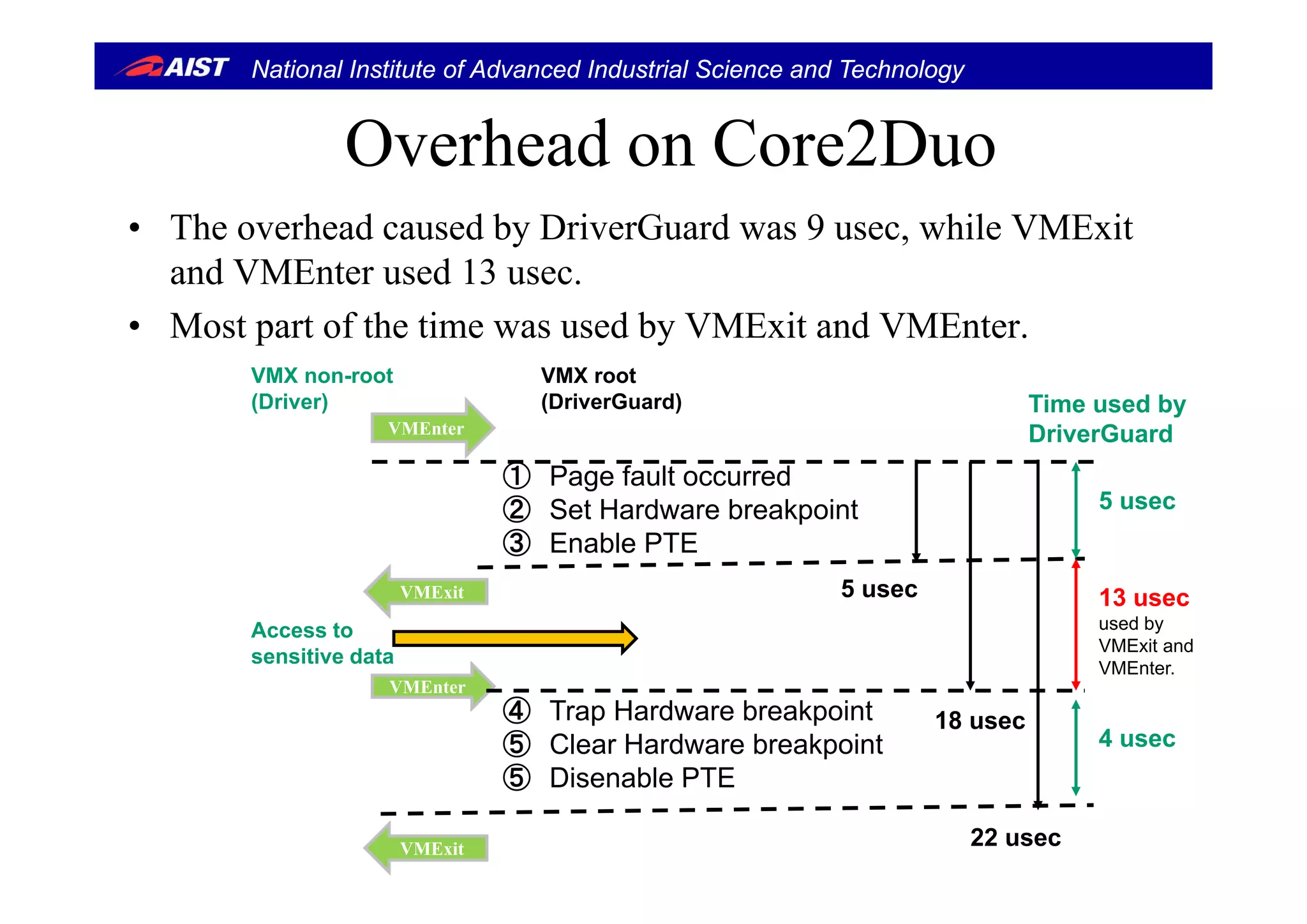
![National Institute of Advanced Industrial Science and Technology
Related WorksRelated Works
• Hypervisor which protect devices• Hypervisor which protect devices
– SecVisor[SOSP’10]
• It requires additional hyper-calls• It requires additional hyper-calls.
– HUKO[NDSS’11]
• It is designed to protect the kernel from untrusted device driver.It is designed to protect the kernel from untrusted device driver.
• Taint tracking technique is useful to prevent information
leakageleakage.
– Some hypervisors have taint tracking
• TTAnalyze [EICAR’06] TEMU[ICISS’08] V2E[VEE’12]TTAnalyze [EICAR 06], TEMU[ICISS 08], V2E[VEE 12]
– They take much time, because they must track a target data all
time.](https://image.slidesharecdn.com/iwsec14-suzaki-140827192940-phpapp02/75/Kernel-Memory-Protection-by-an-Insertable-Hypervisor-which-has-VM-Introspection-and-Stealth-Breakpoints-IWSEC2014-21-2048.jpg)
