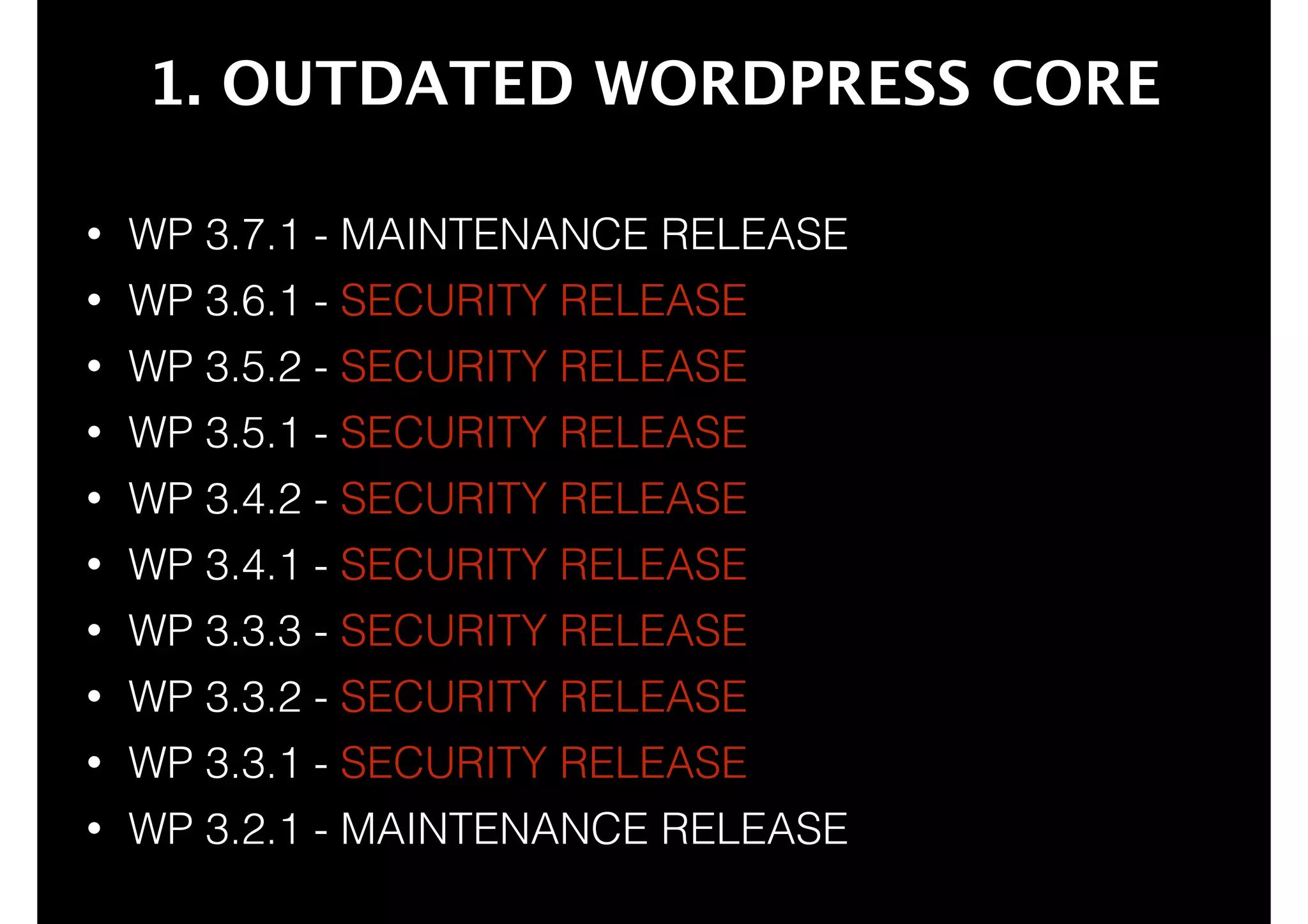
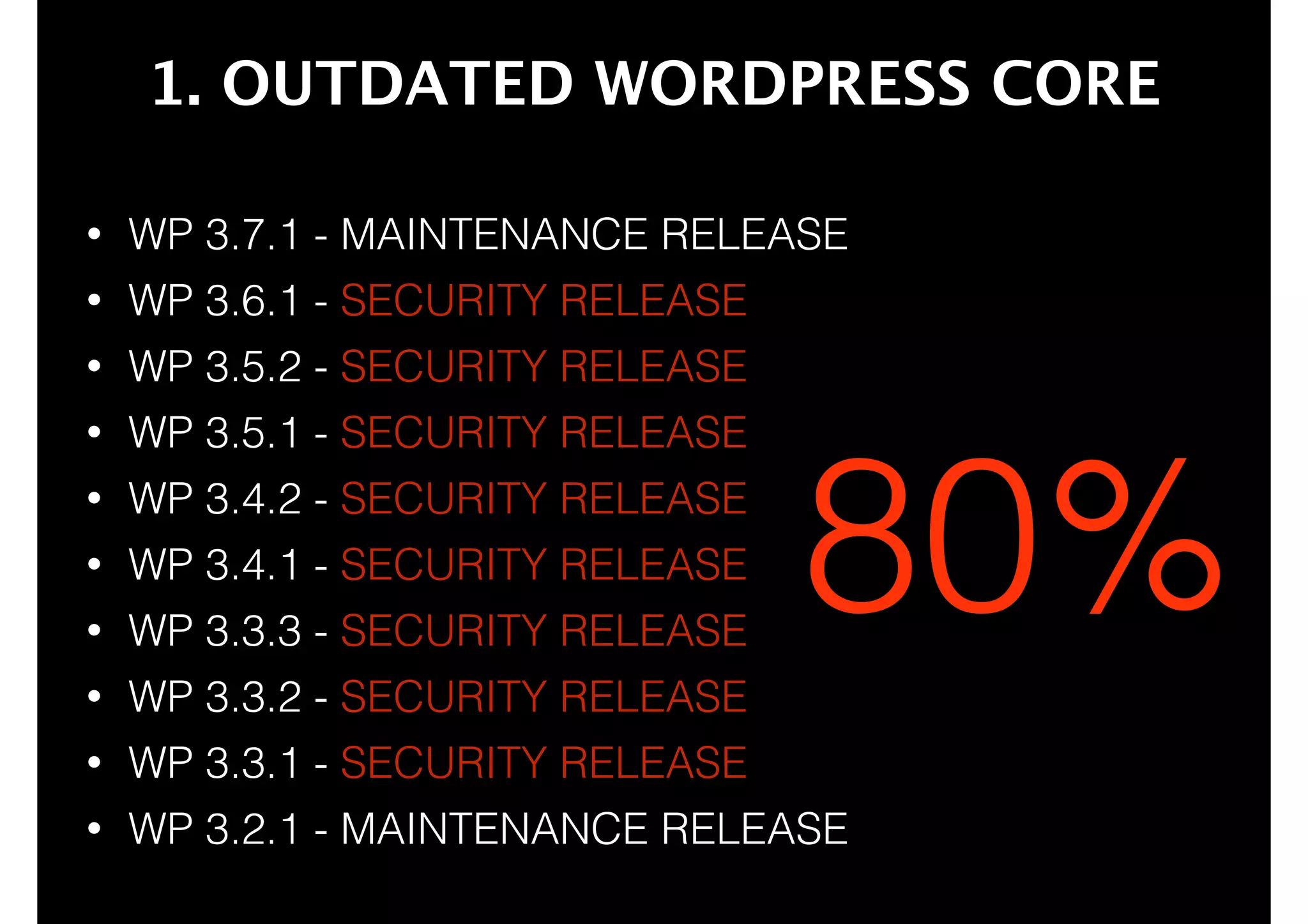
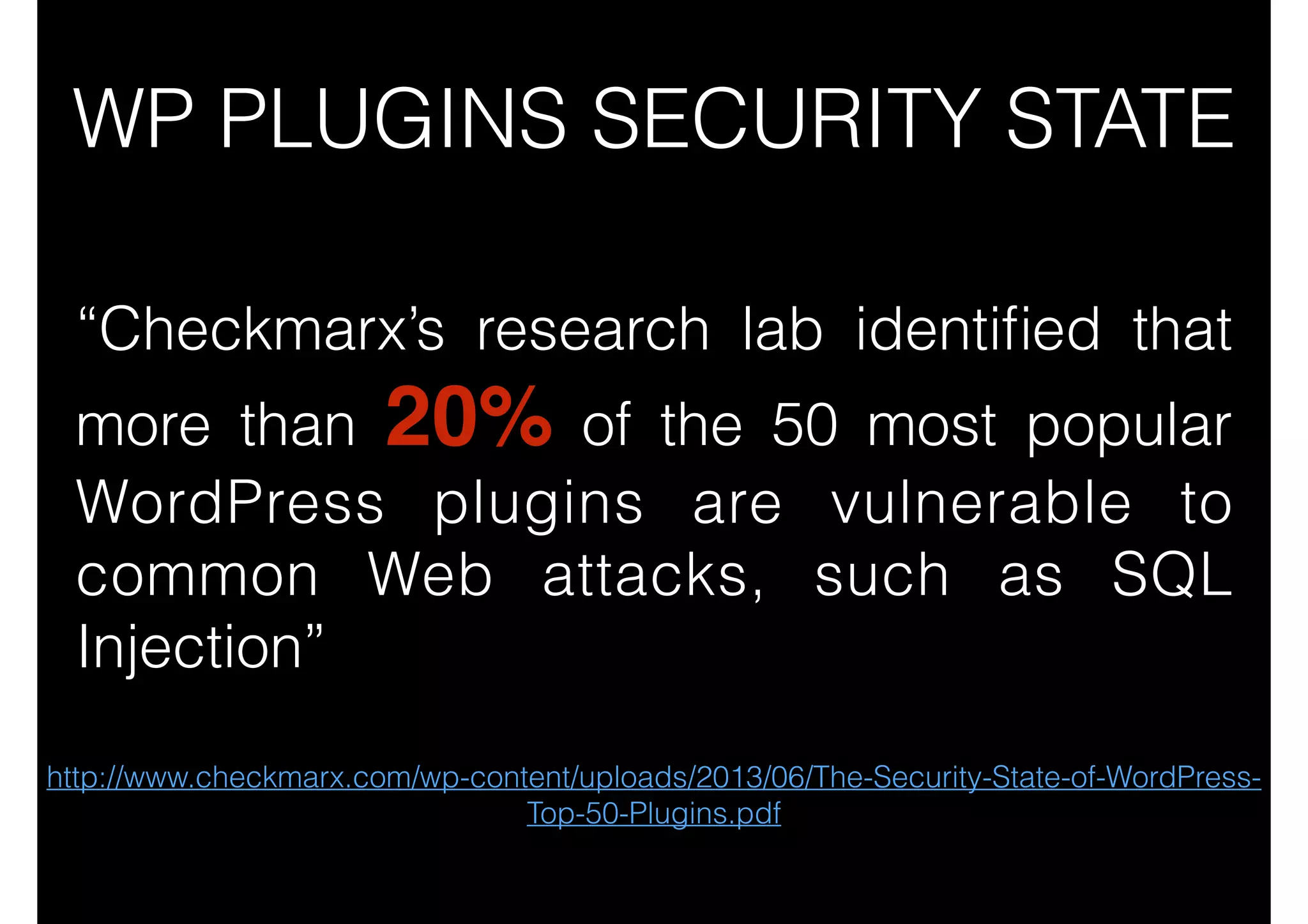
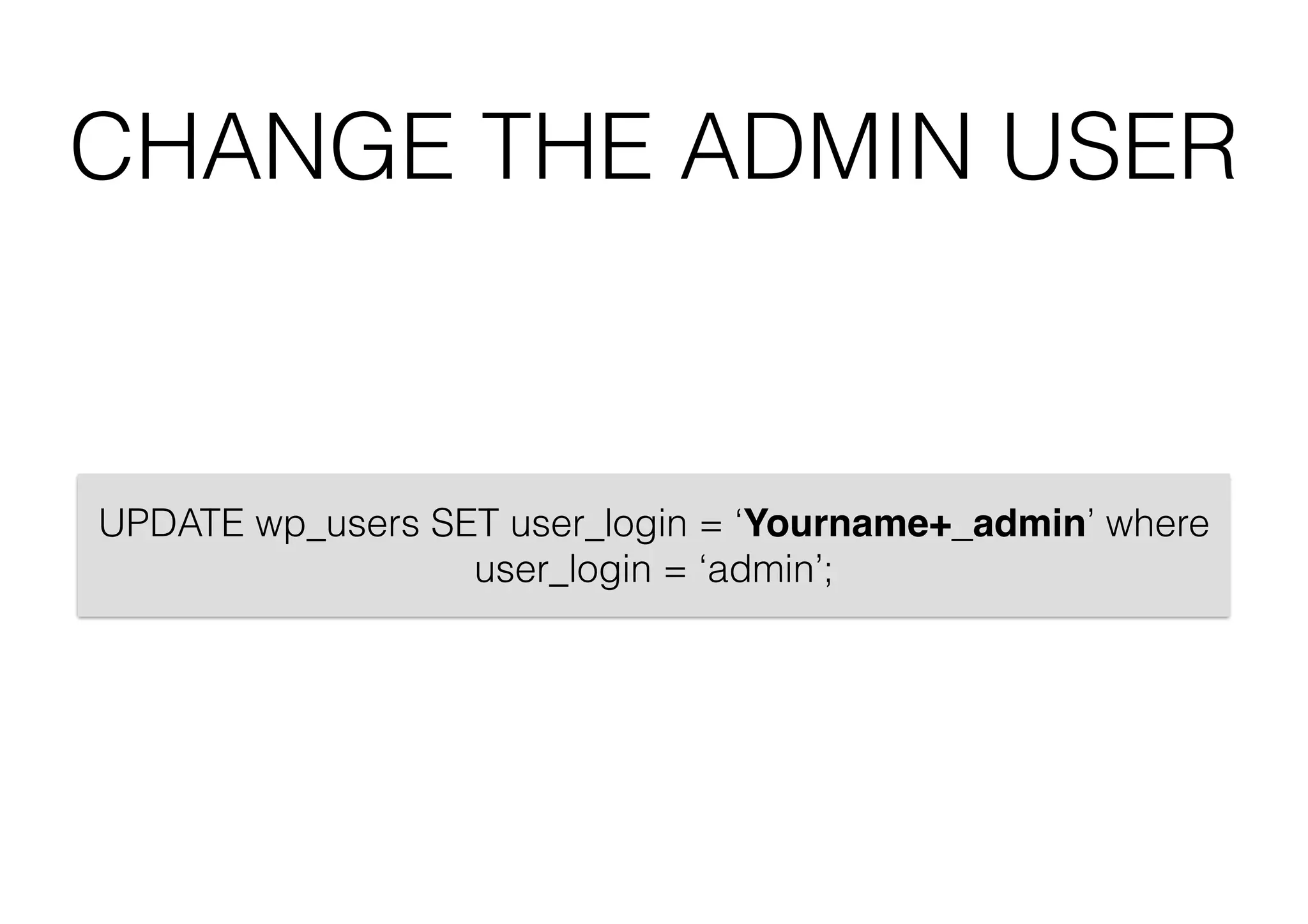
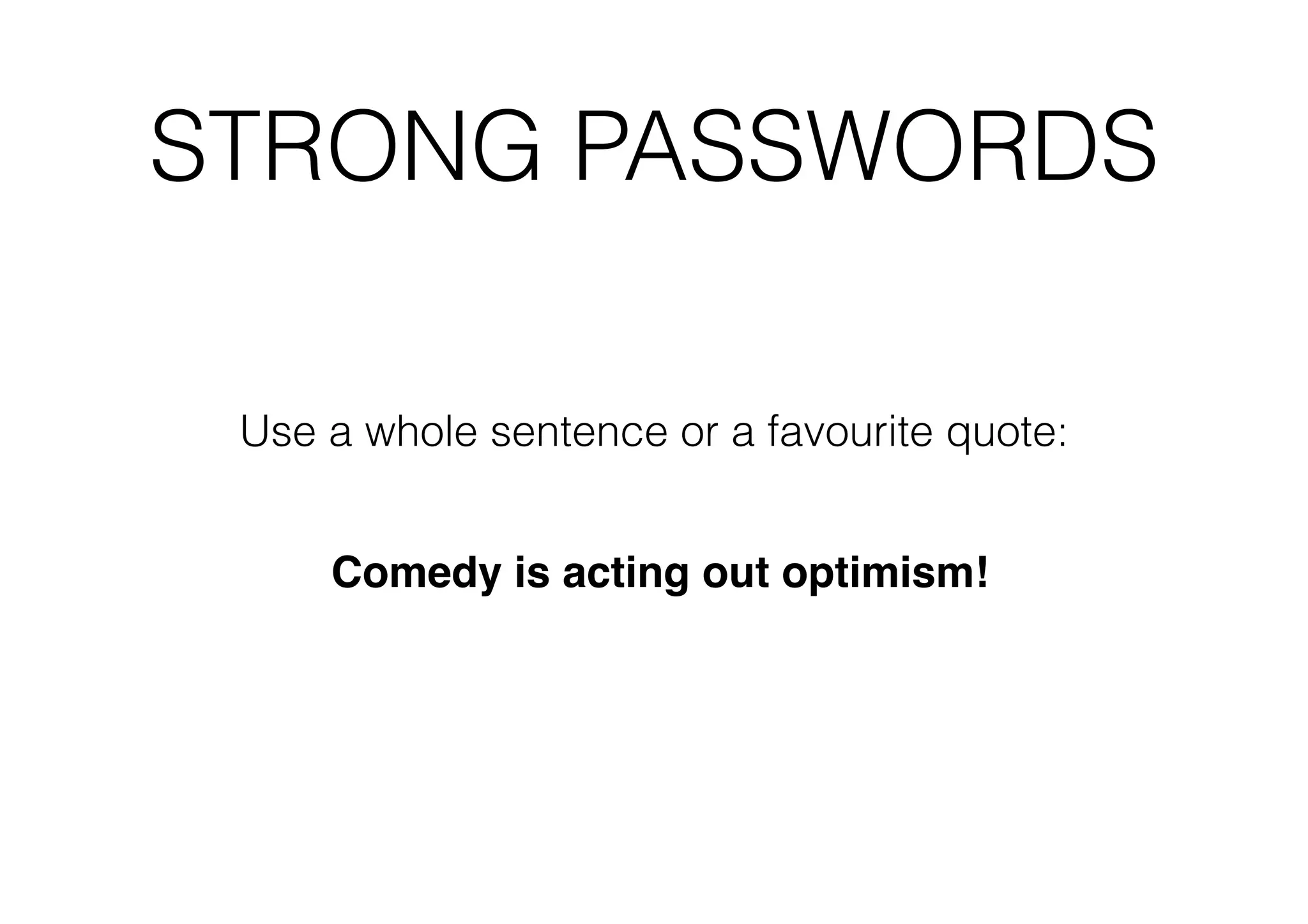
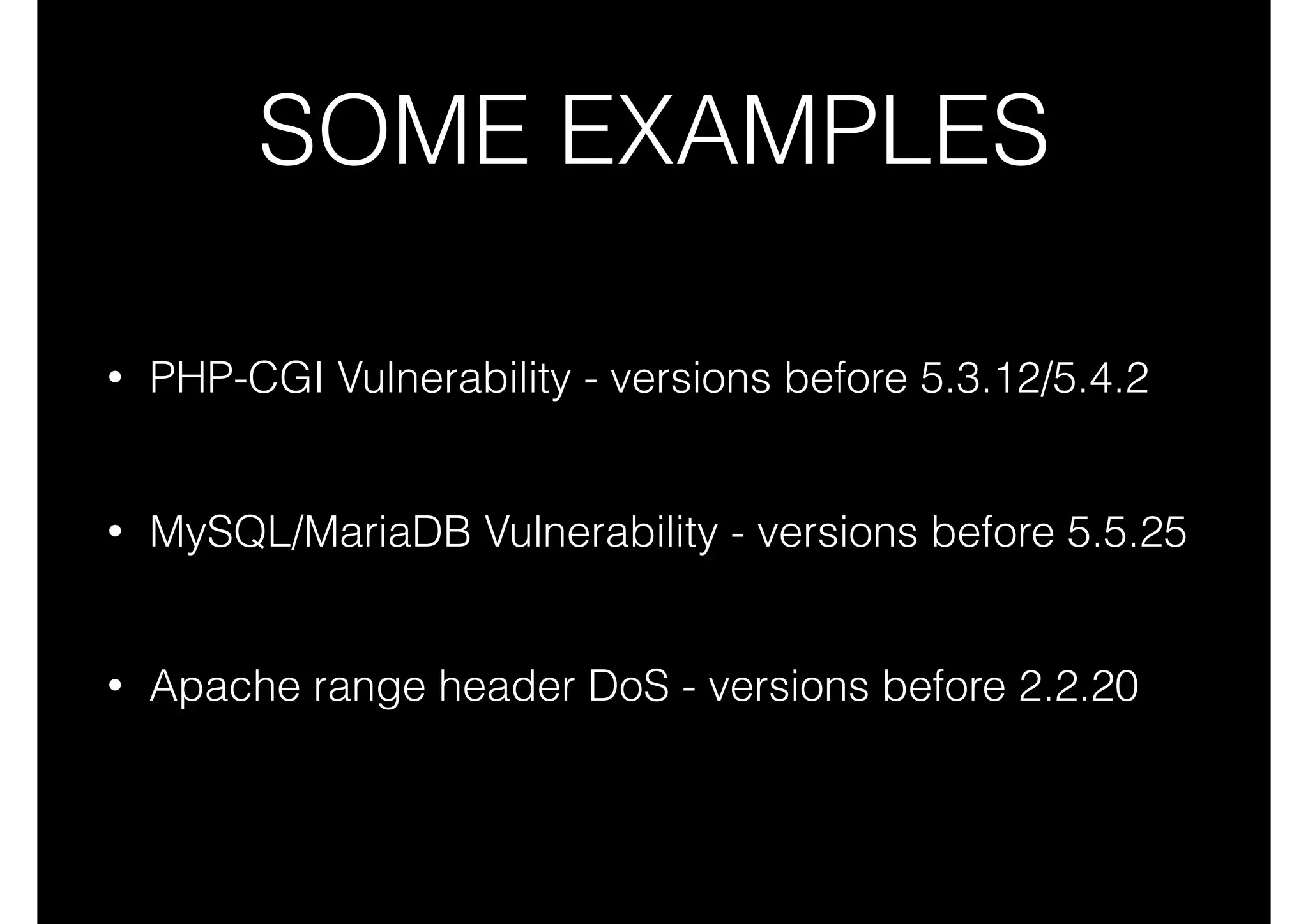
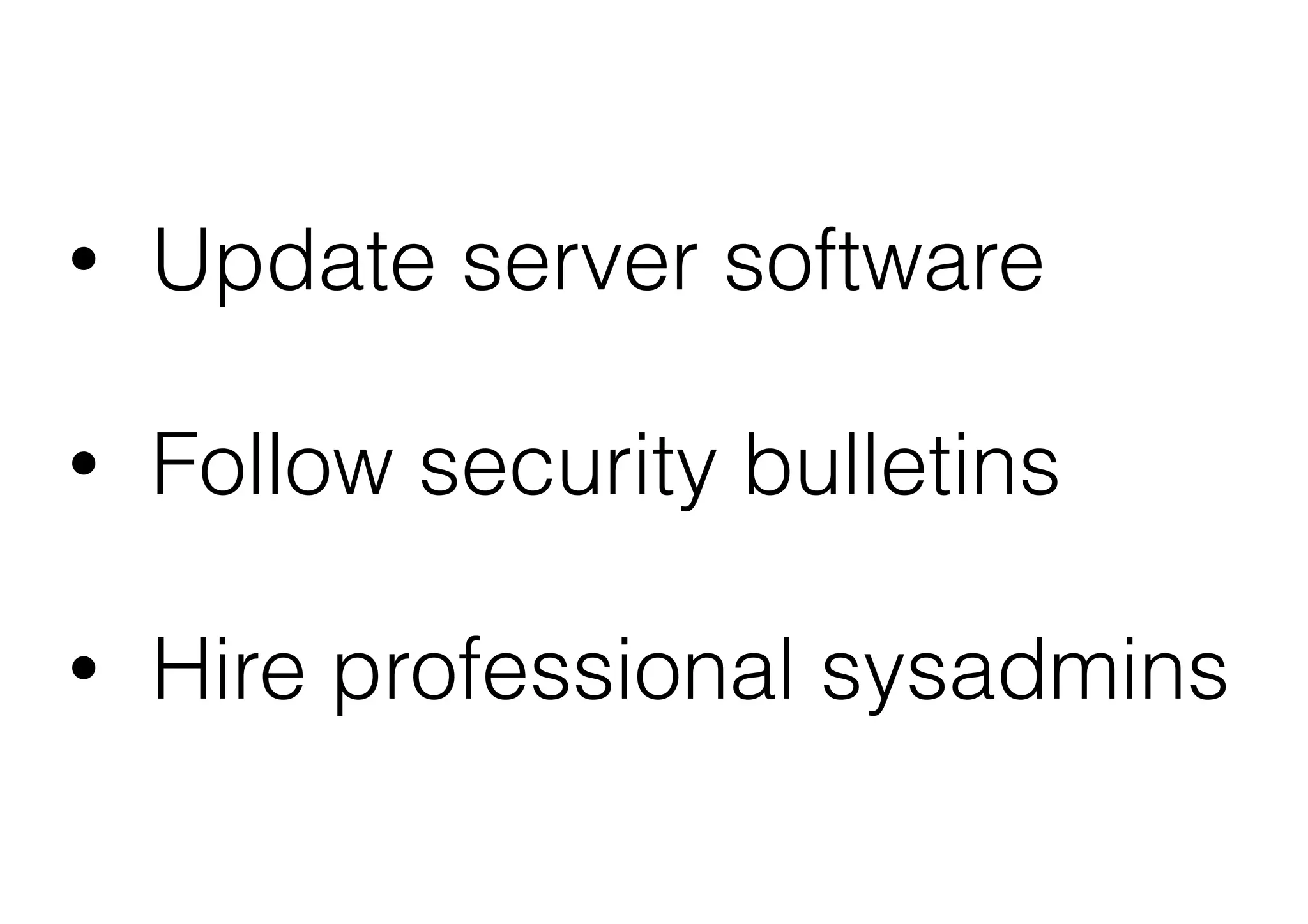
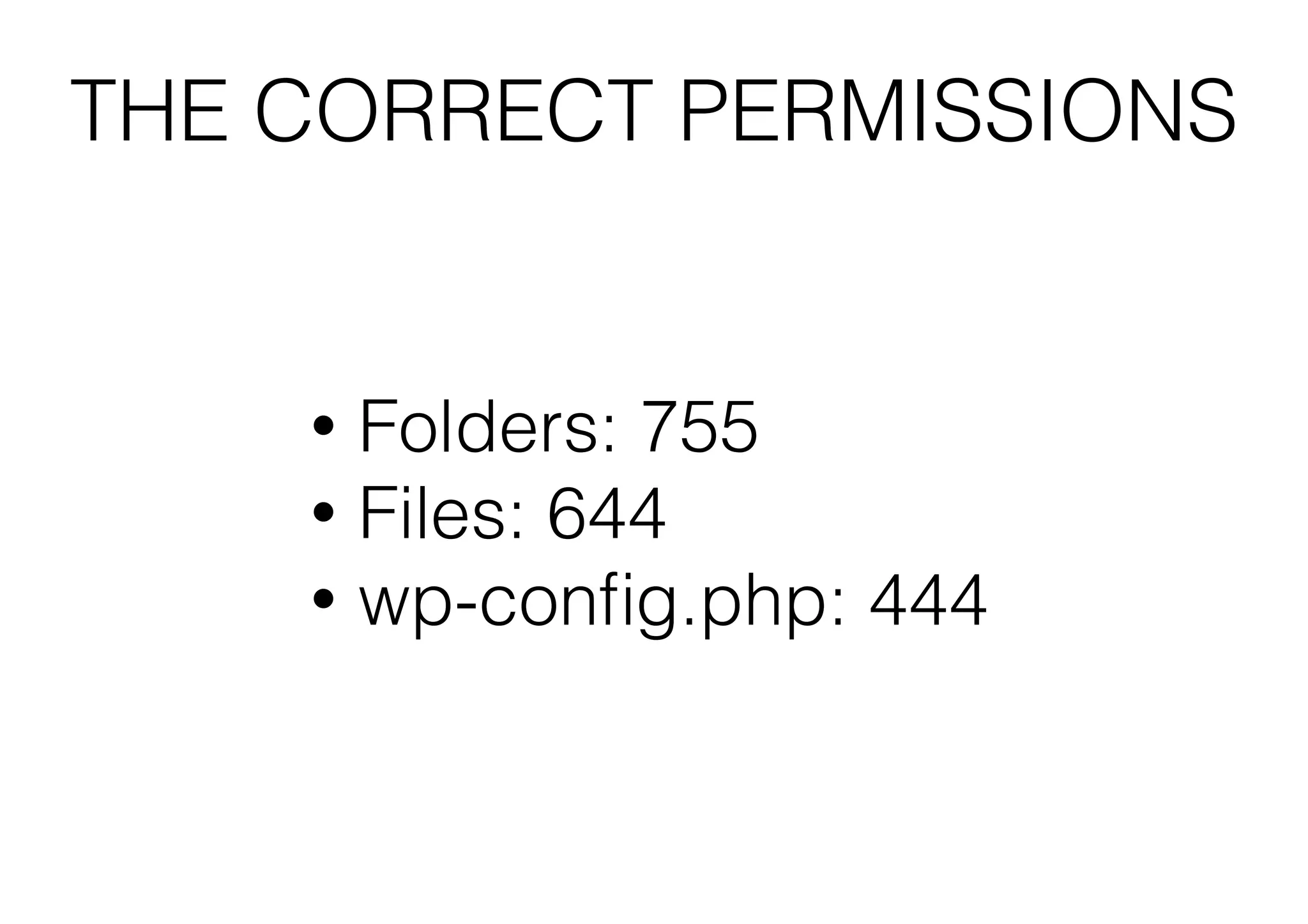
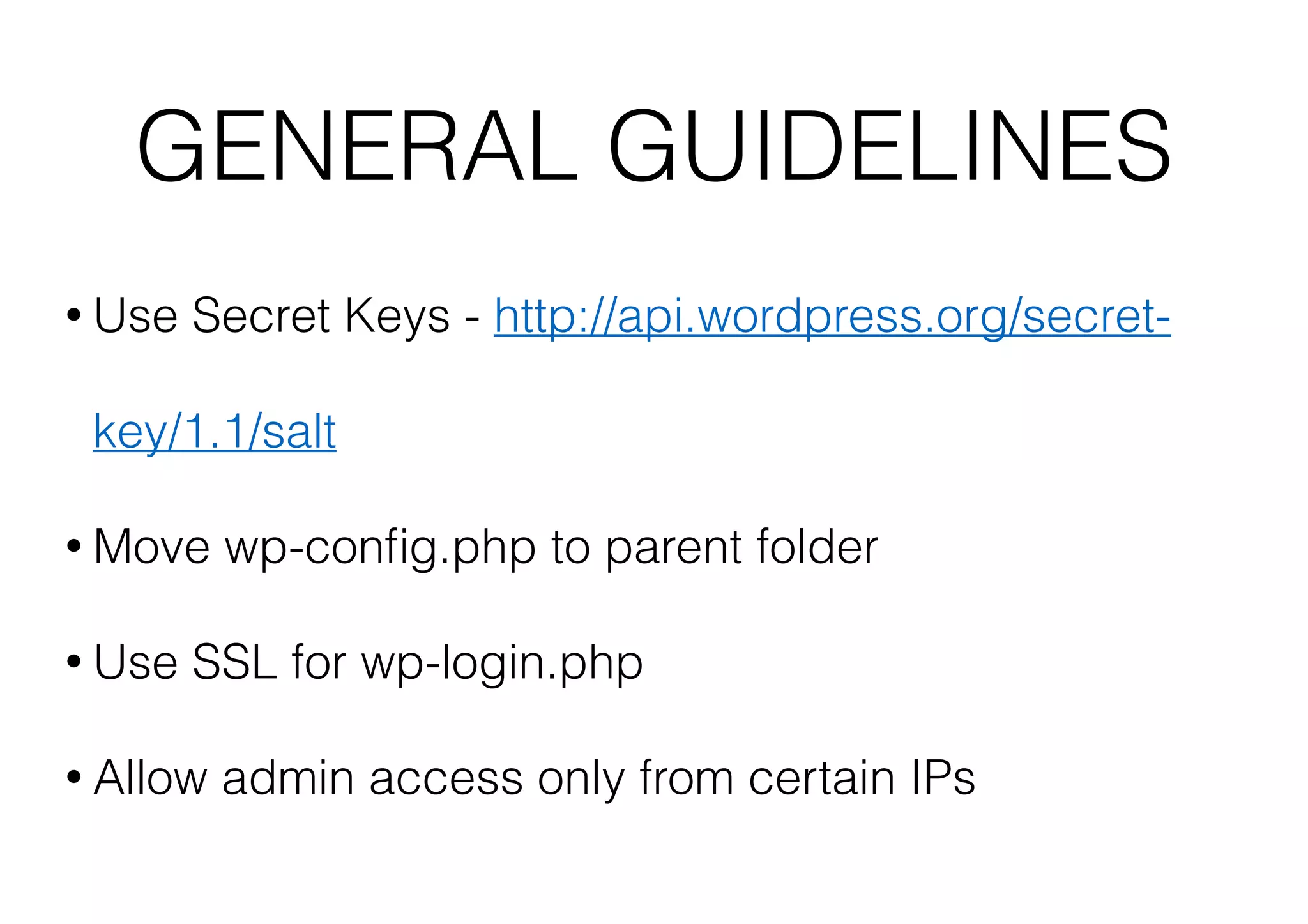
This document outlines 8 ways to hack a WordPress site, including having an outdated WordPress core or plugins/themes, weak login credentials, malware, vulnerable server software, incorrect server configurations, and wrong file permissions. It provides examples for each vulnerability and recommends keeping everything updated, using strong passwords, proper permissions, and working with experienced administrators to secure a site.