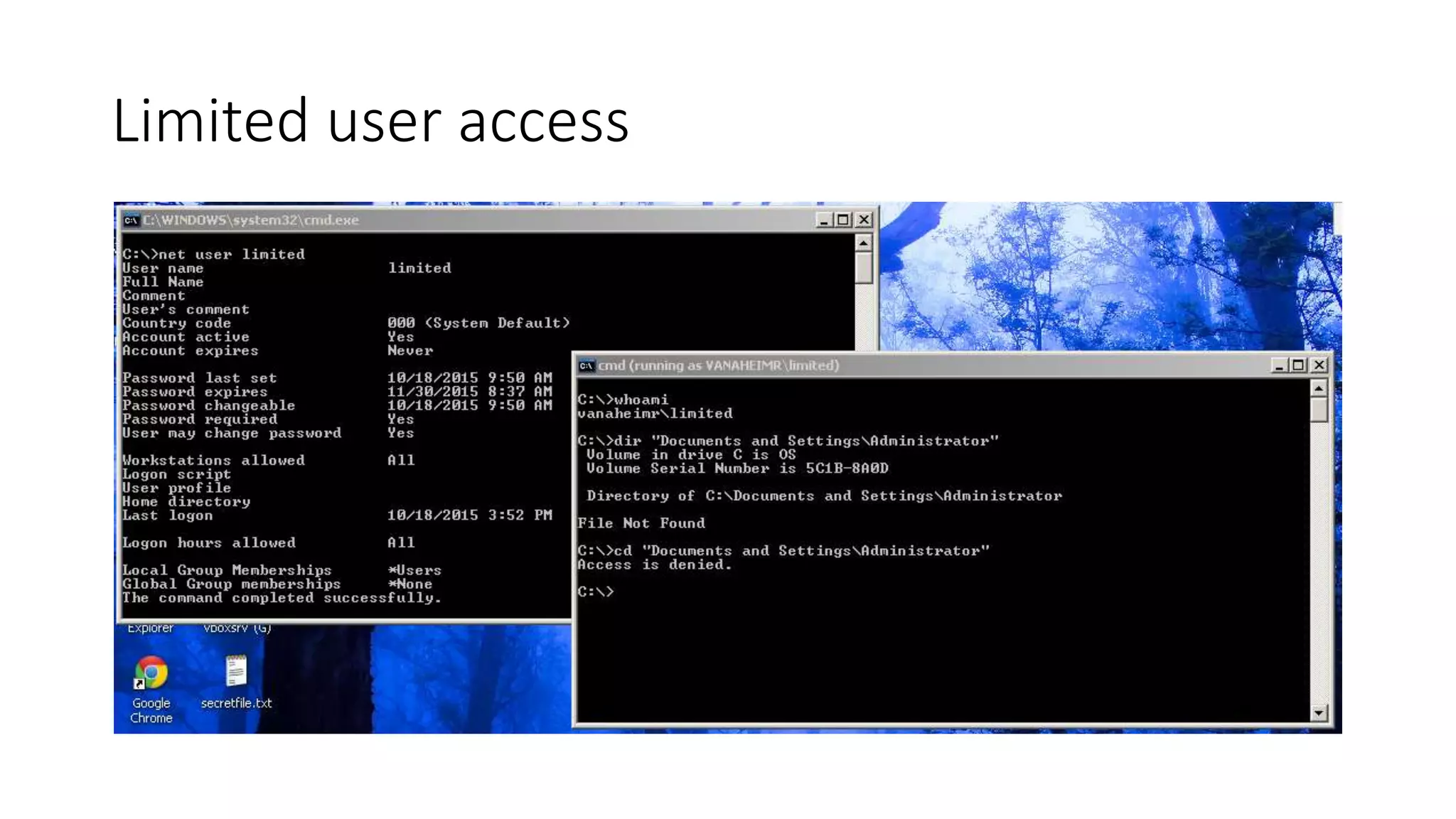
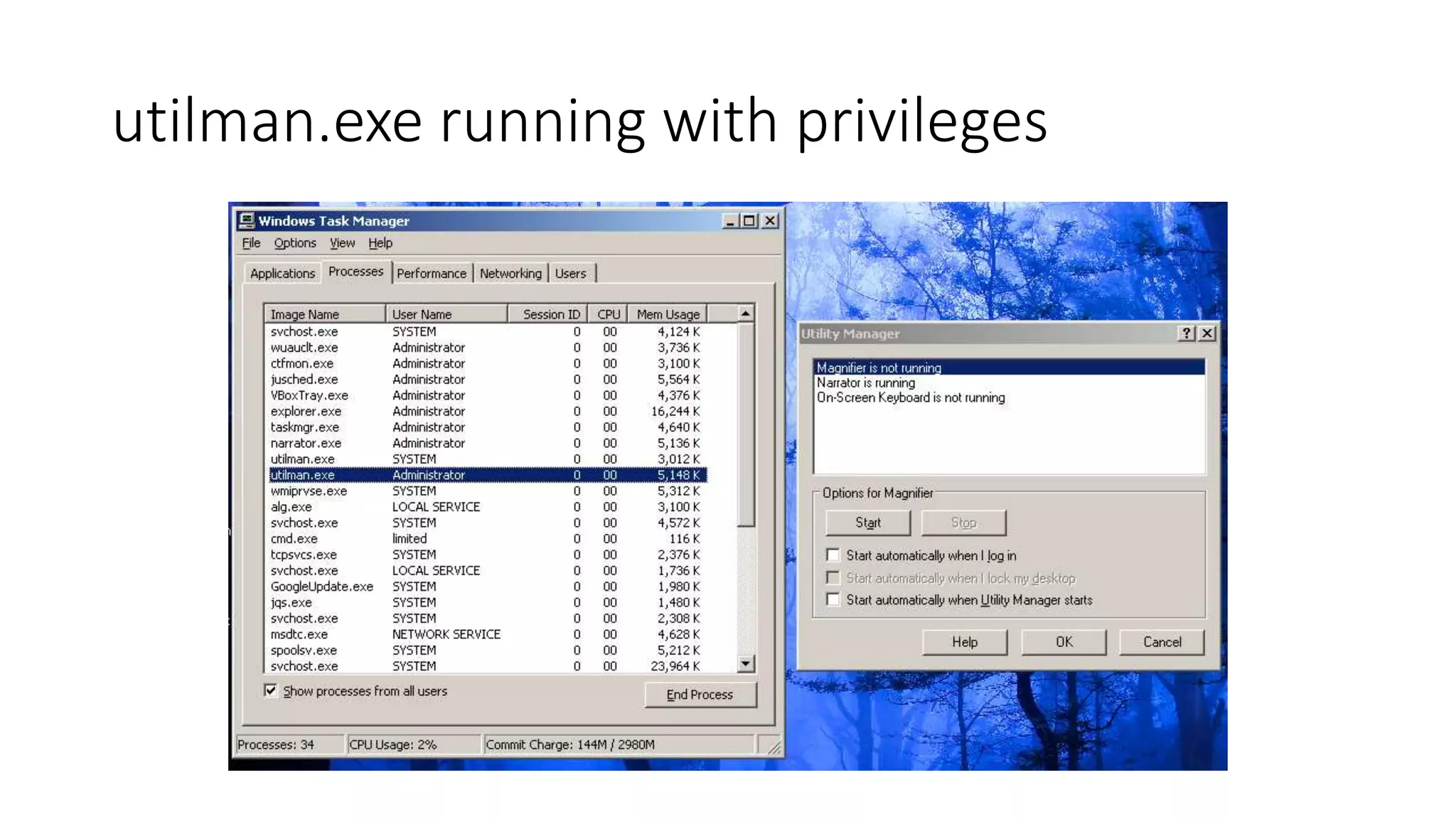
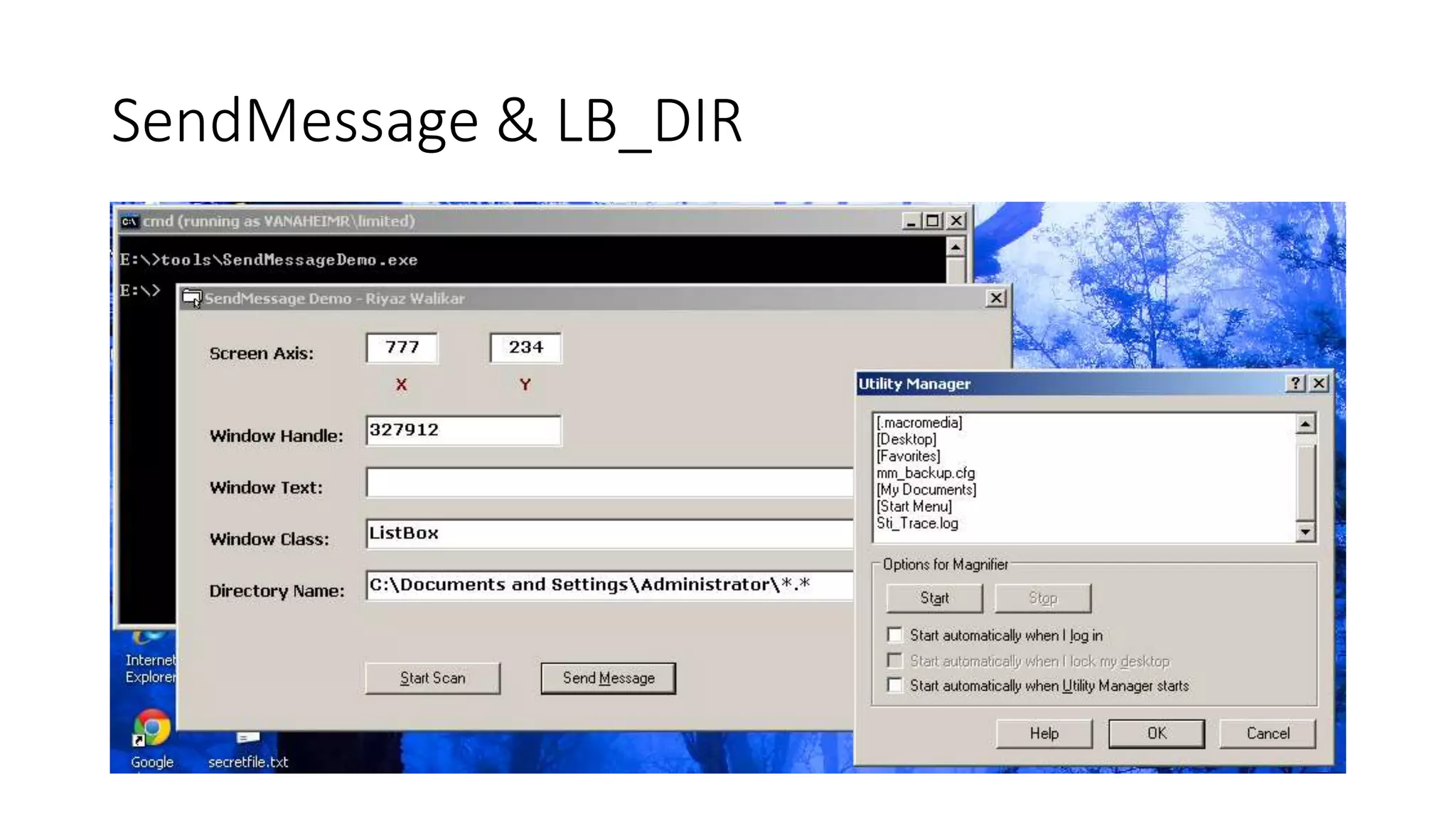
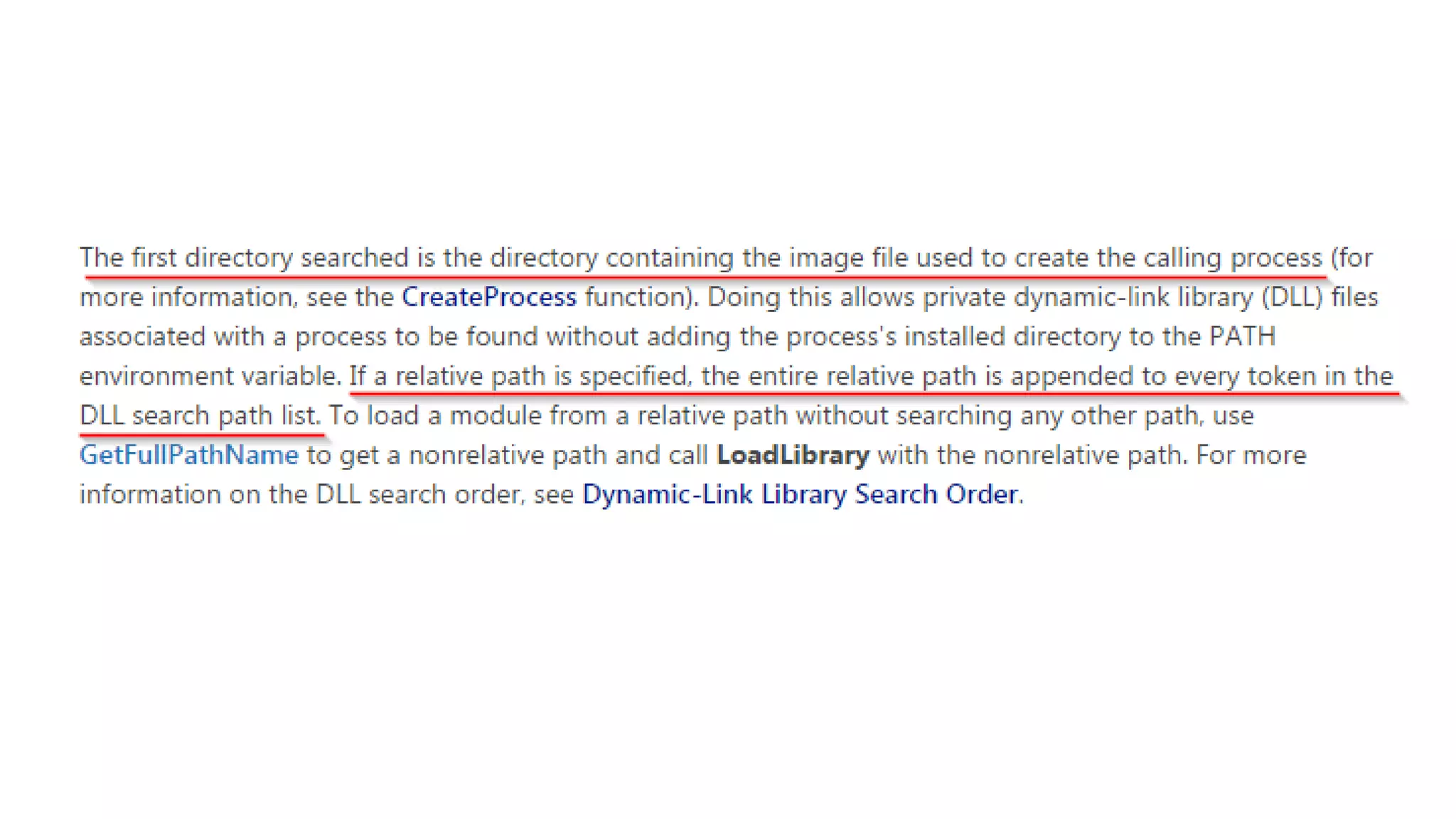
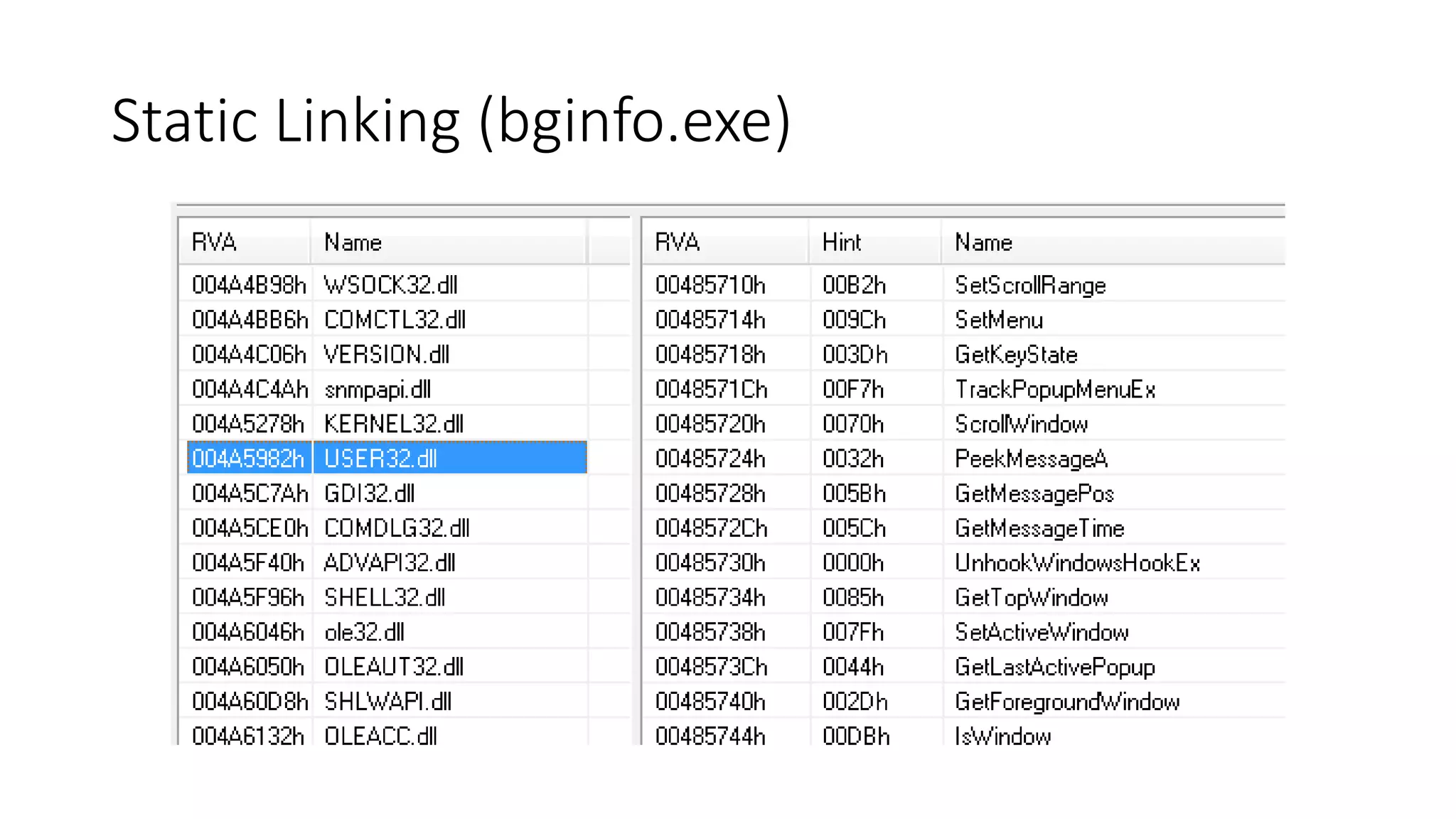
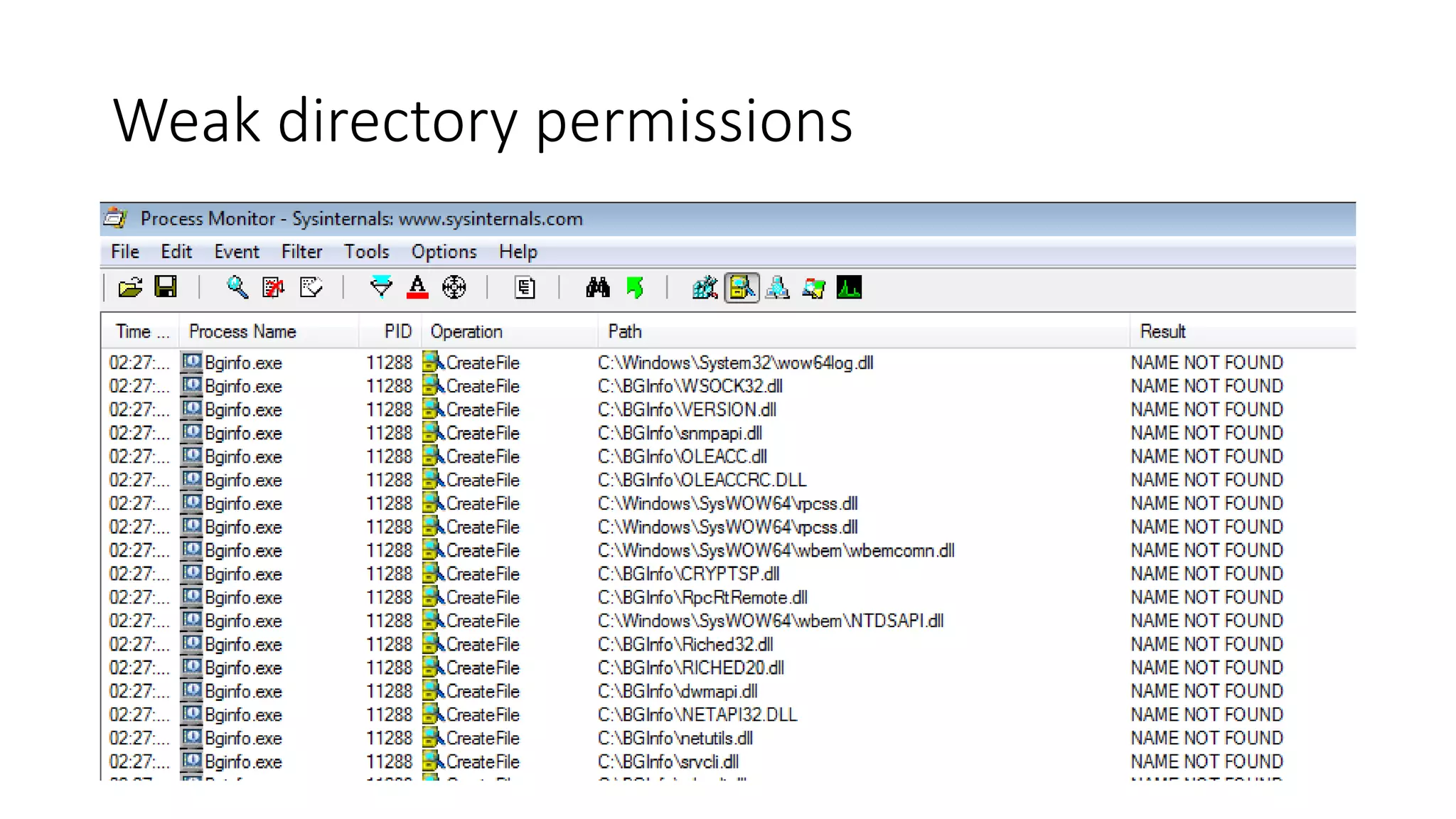
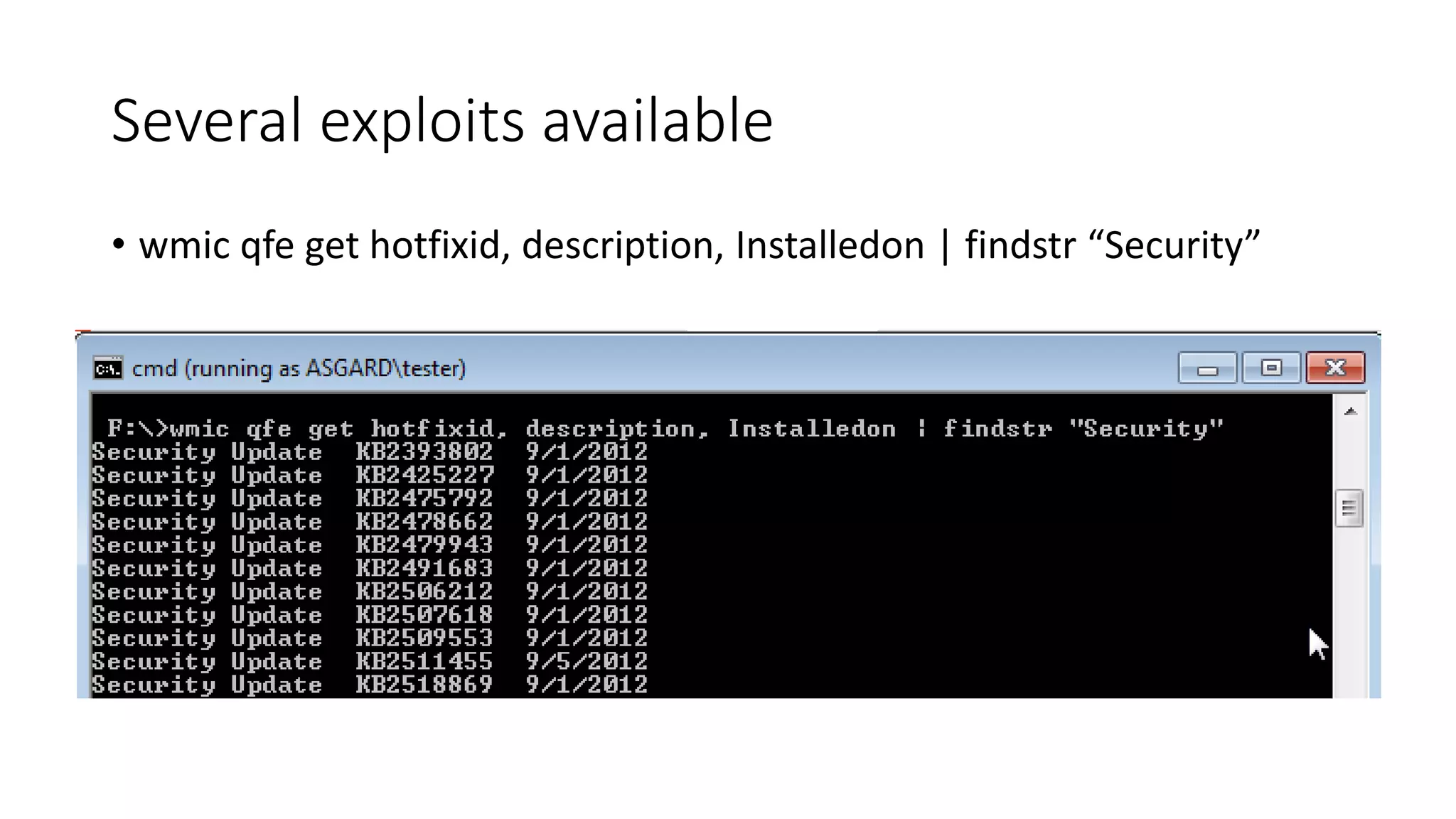
The document outlines a pentester's methodology for Windows privilege escalation, emphasizing techniques for exploiting network flaws and misconfigurations. It discusses various methods such as token impersonation, scheduled task abuse, and window messaging attacks, with real-world examples and demonstrations. Additionally, it provides resources and tools for further exploration of Windows security vulnerabilities.







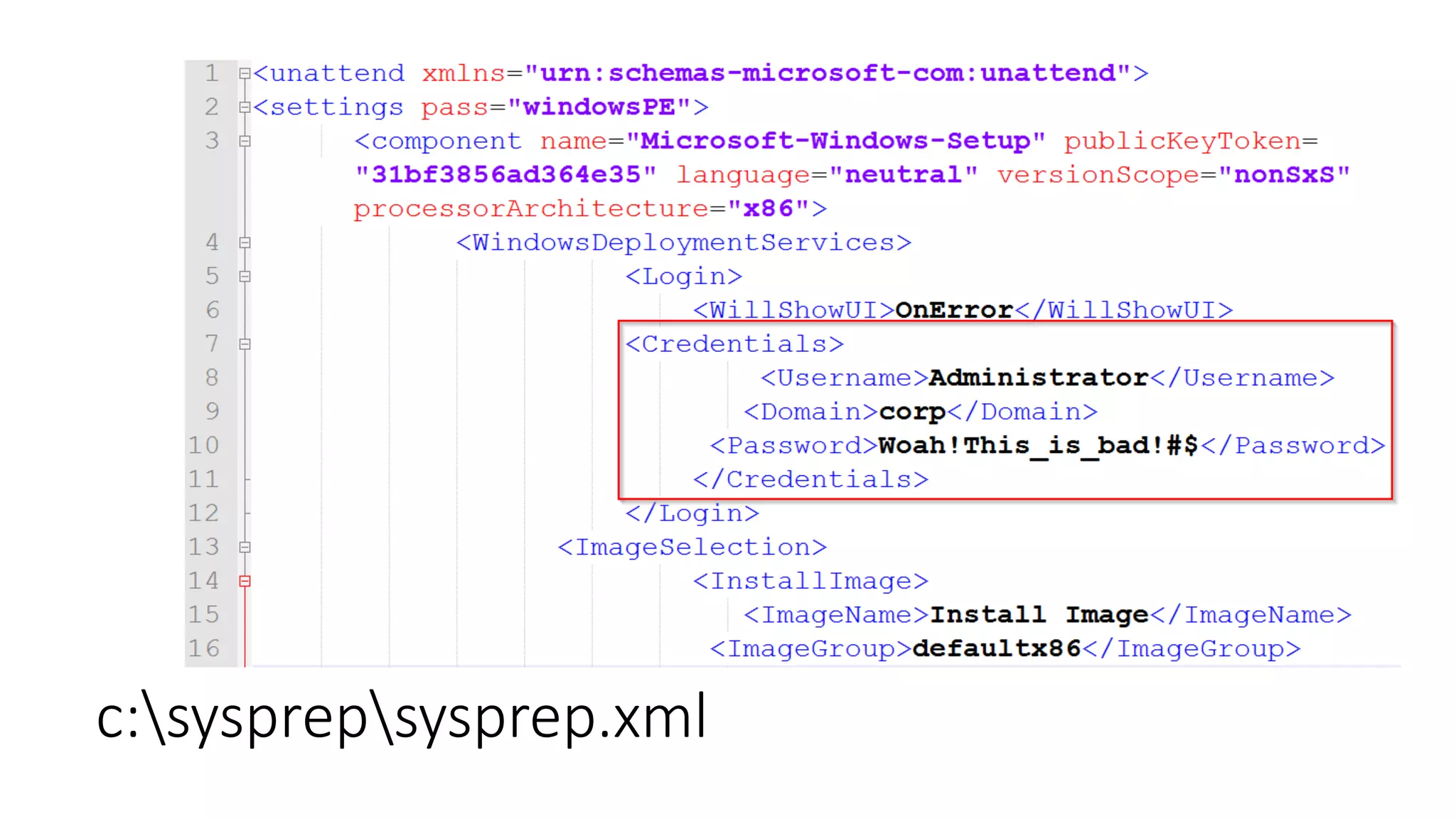
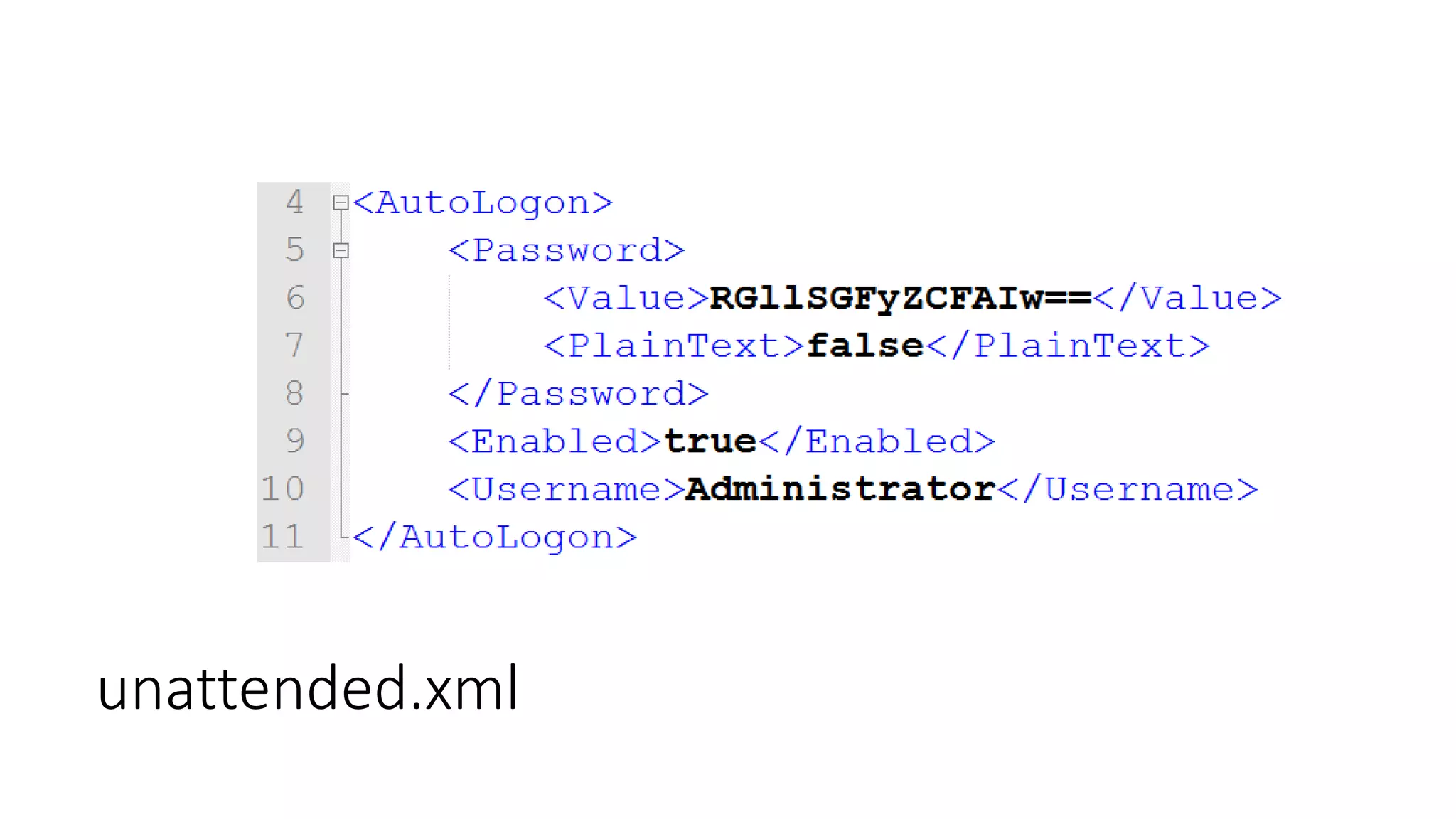
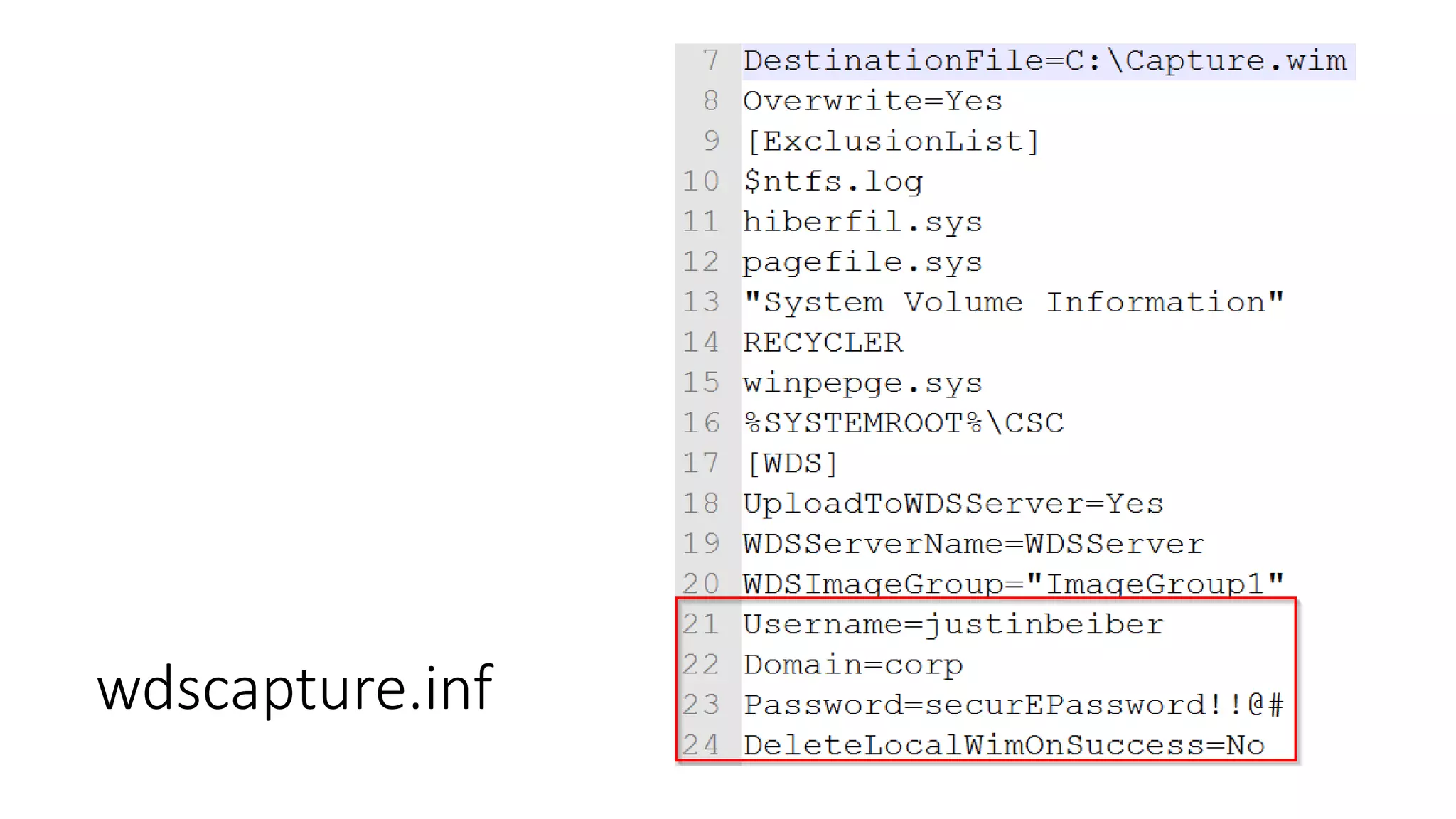
![Passwords in files/registry
[unencrypted (like for real!)]](https://image.slidesharecdn.com/windowsprivesctalk-151021184037-lva1-app6892/75/Windows-Privilege-Escalation-12-2048.jpg)



![*vnc
• RealVNC [HKEY_LOCAL_MACHINESOFTWARERealVNCvncserver]
• TightVNC [HKEY_CURRENT_USERSoftwareTightVNCServer]
• TigerVNC [HKEY_LOCAL_USERSoftwareTigerVNCWinVNC4]
• UltraVNC [C:Program FilesUltraVNCultravnc.ini]](https://image.slidesharecdn.com/windowsprivesctalk-151021184037-lva1-app6892/75/Windows-Privilege-Escalation-19-2048.jpg)
![Other places / software
• Autologon [HKLMSoftwareMicrosoftWindows
NTCurrentVersionWinlogon]
• HKEY_CURRENT_USERSoftwareSimonTathamPuTTYSessions
• Search the OS using dir /s and findstr /S /I (.xlsx, .docx, .pdf etc.)
• Search the Windows registry using reg query](https://image.slidesharecdn.com/windowsprivesctalk-151021184037-lva1-app6892/75/Windows-Privilege-Escalation-20-2048.jpg)