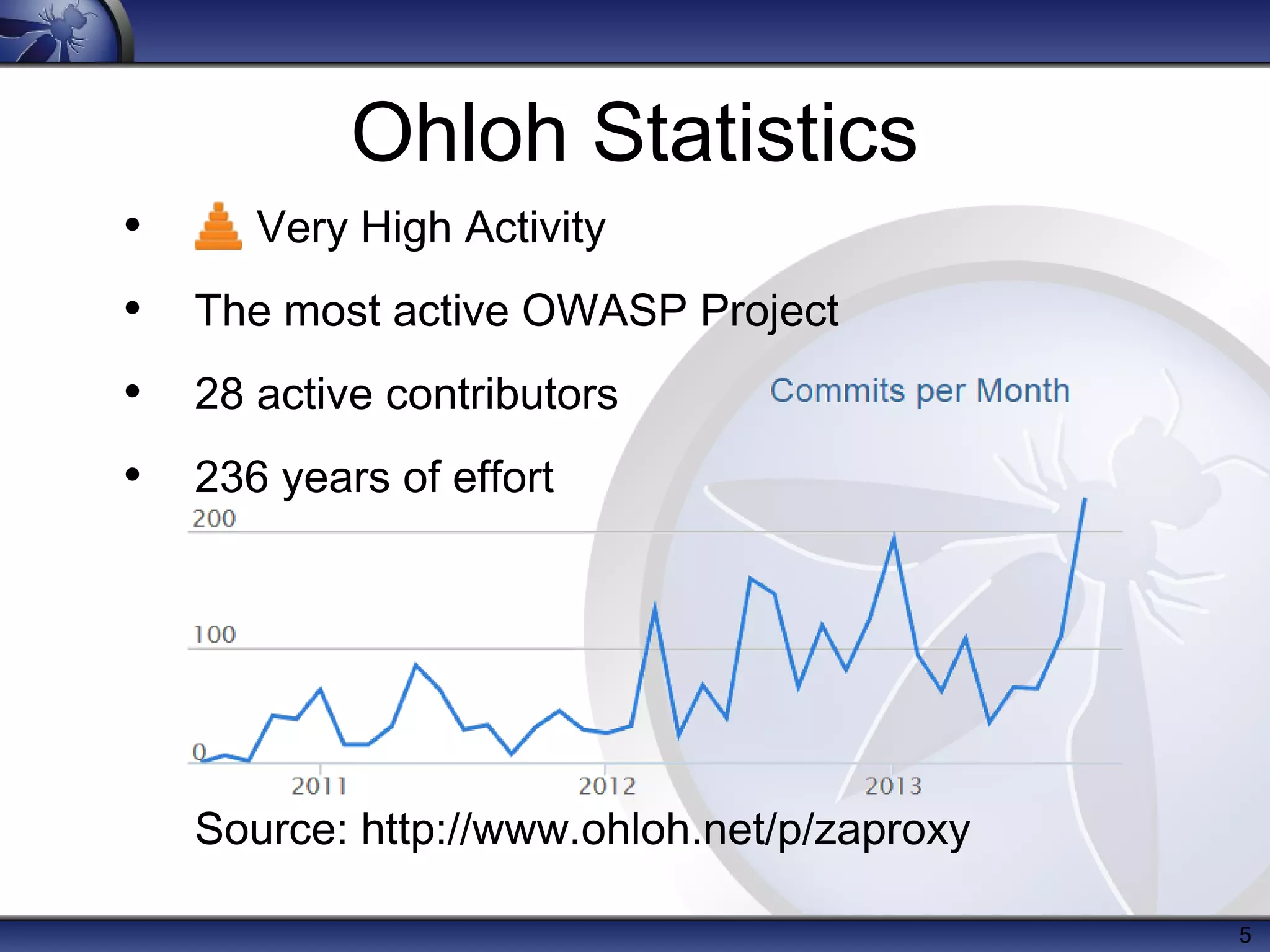
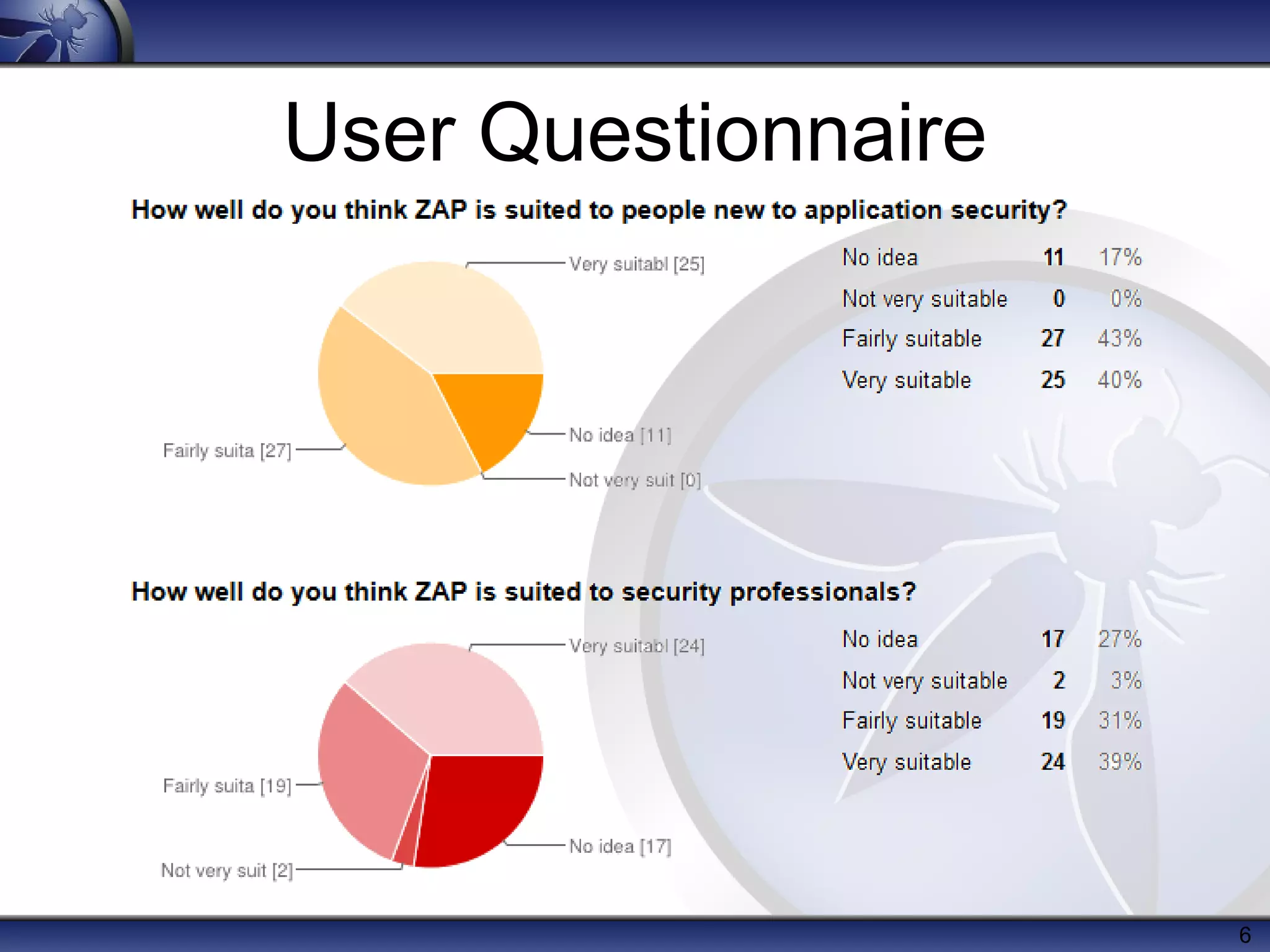
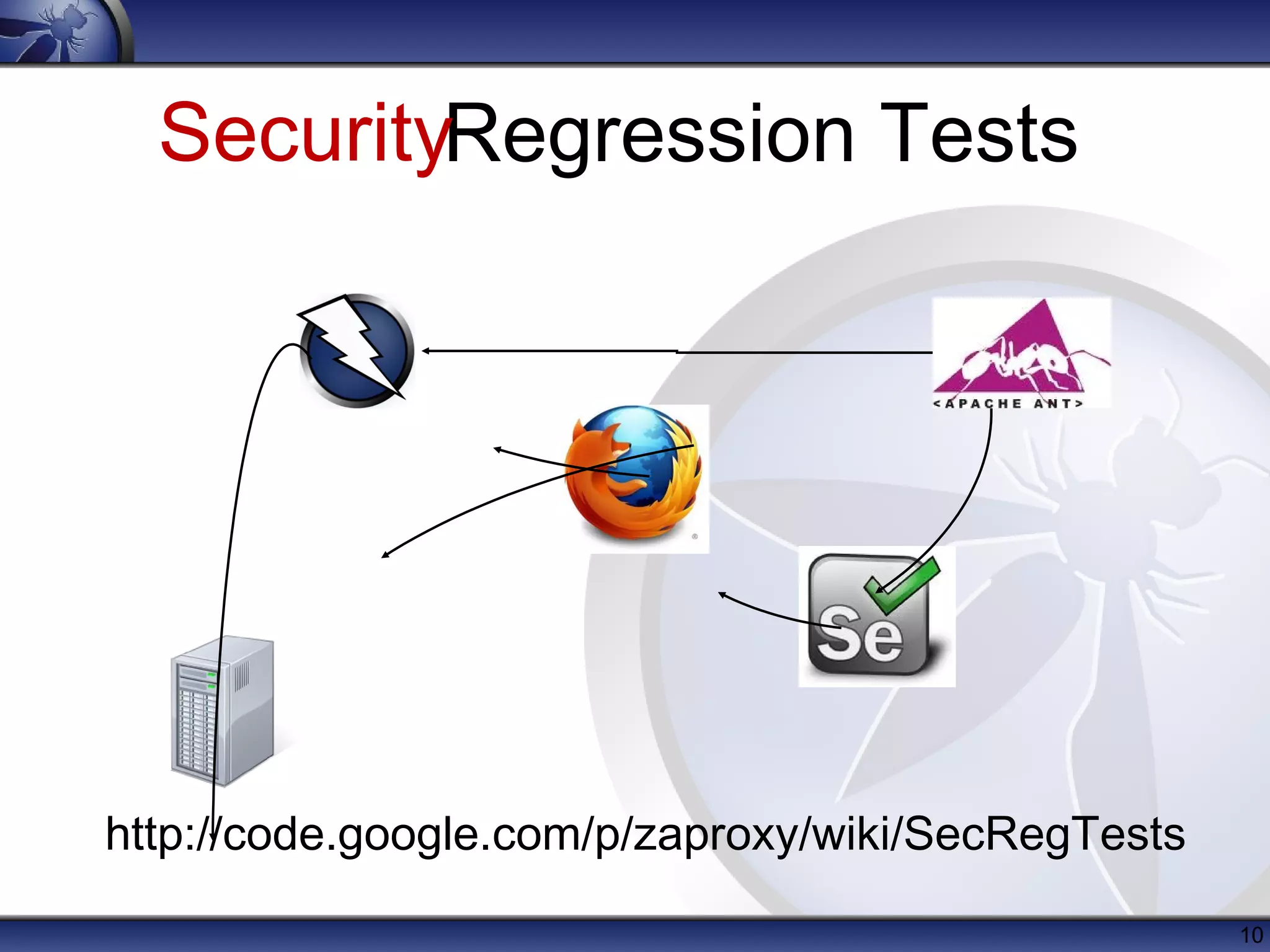
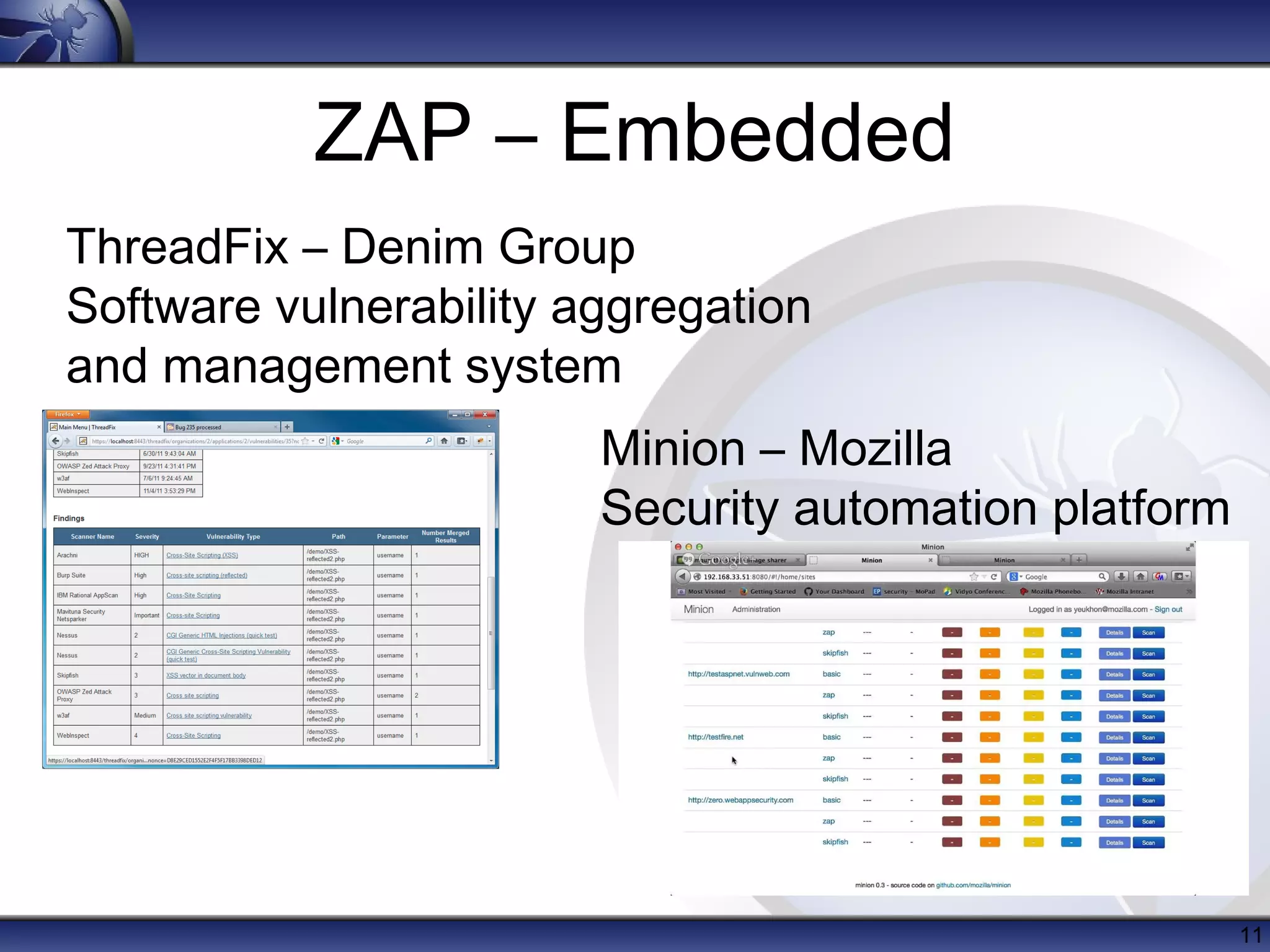
The OWASP Zed Attack Proxy (ZAP) is a free, open-source web application penetration testing tool suitable for both beginners and professionals, offering features like an intercepting proxy, various scanning capabilities, and add-ons. Since its release in 2010, ZAP has become a prominent project within OWASP with significant community involvement and extensive documentation. Recent enhancements include session awareness, advanced reporting, and integration with tools like ThreadFix and the Mozilla security automation platform.