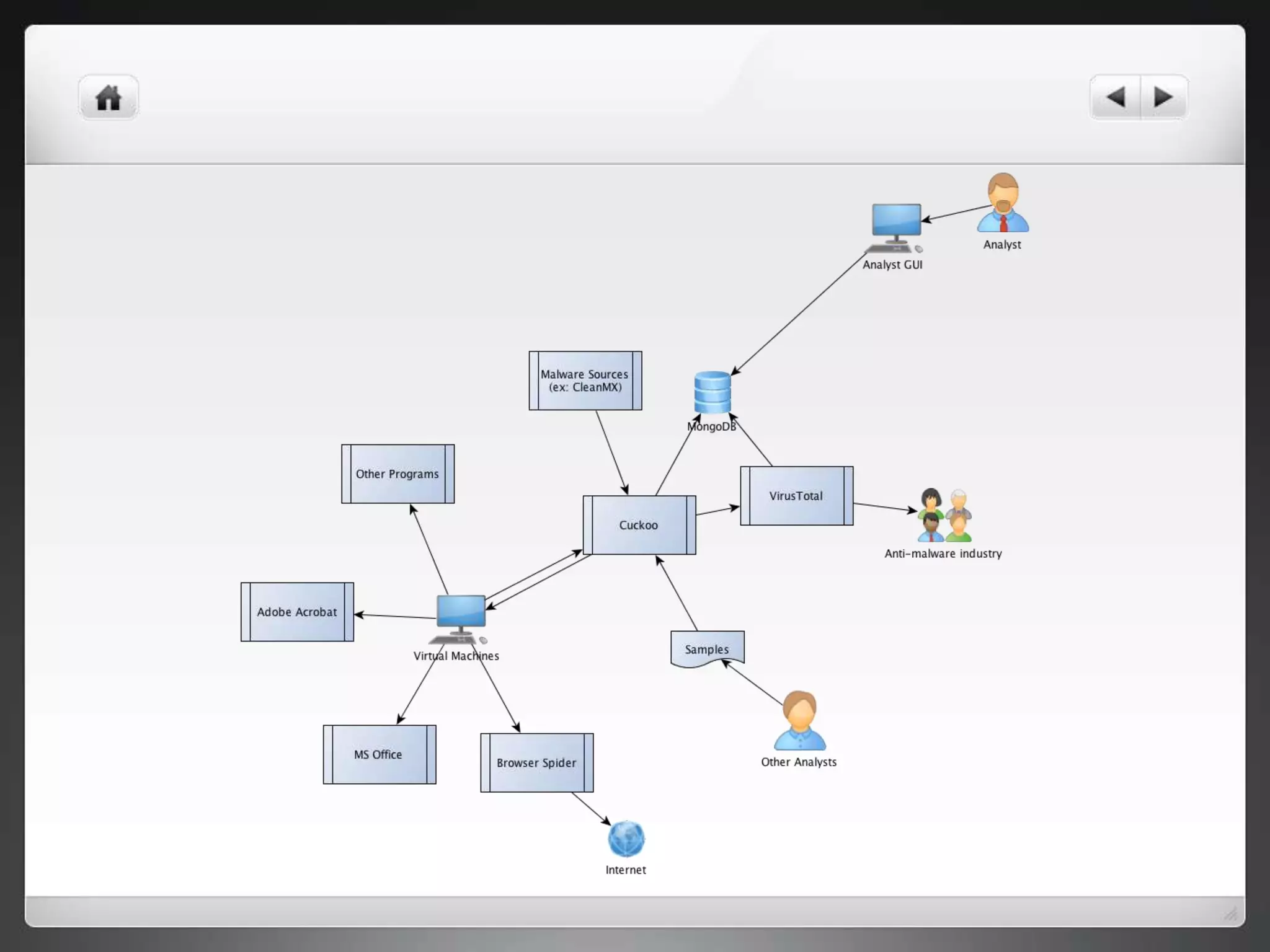
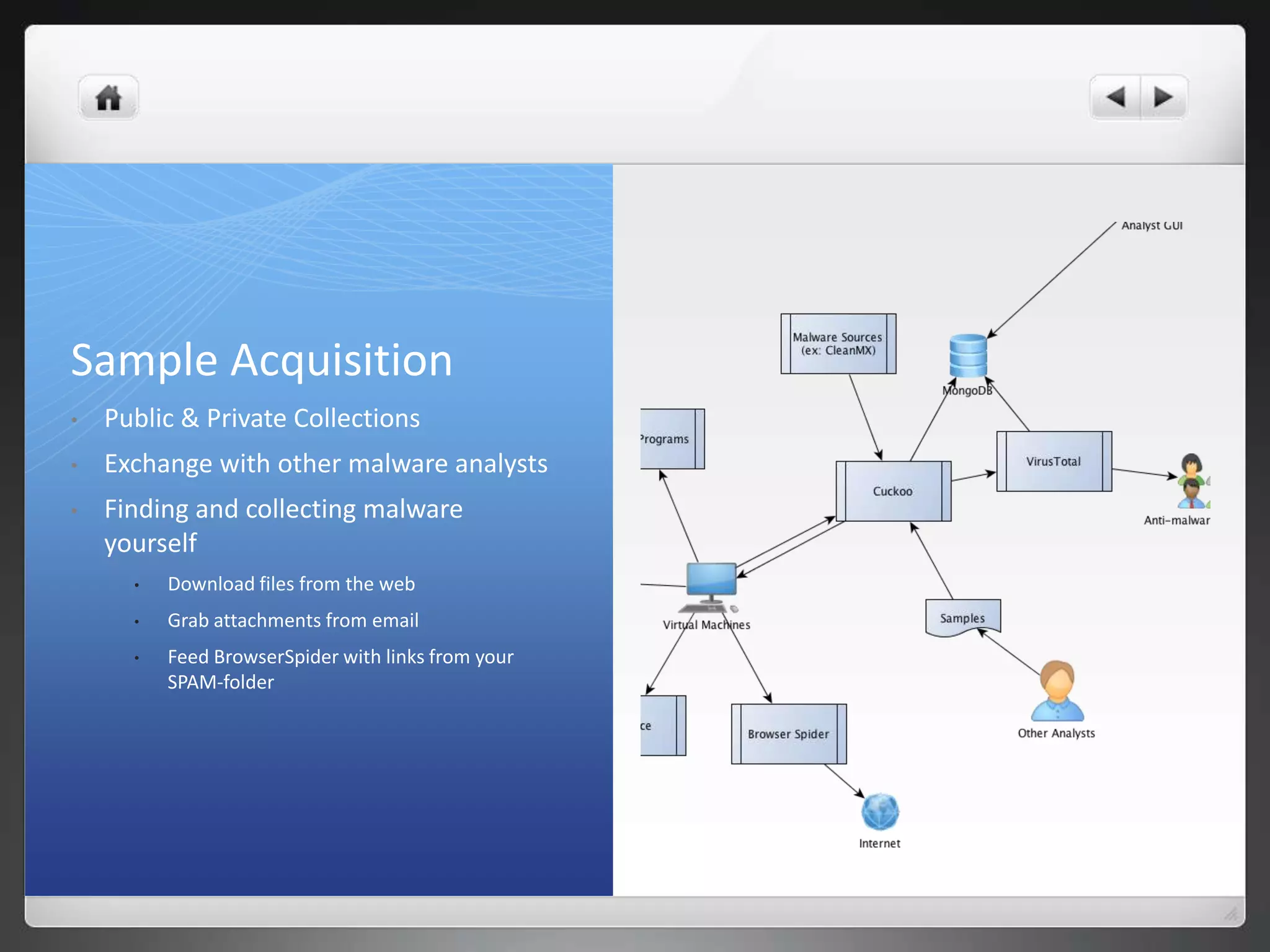
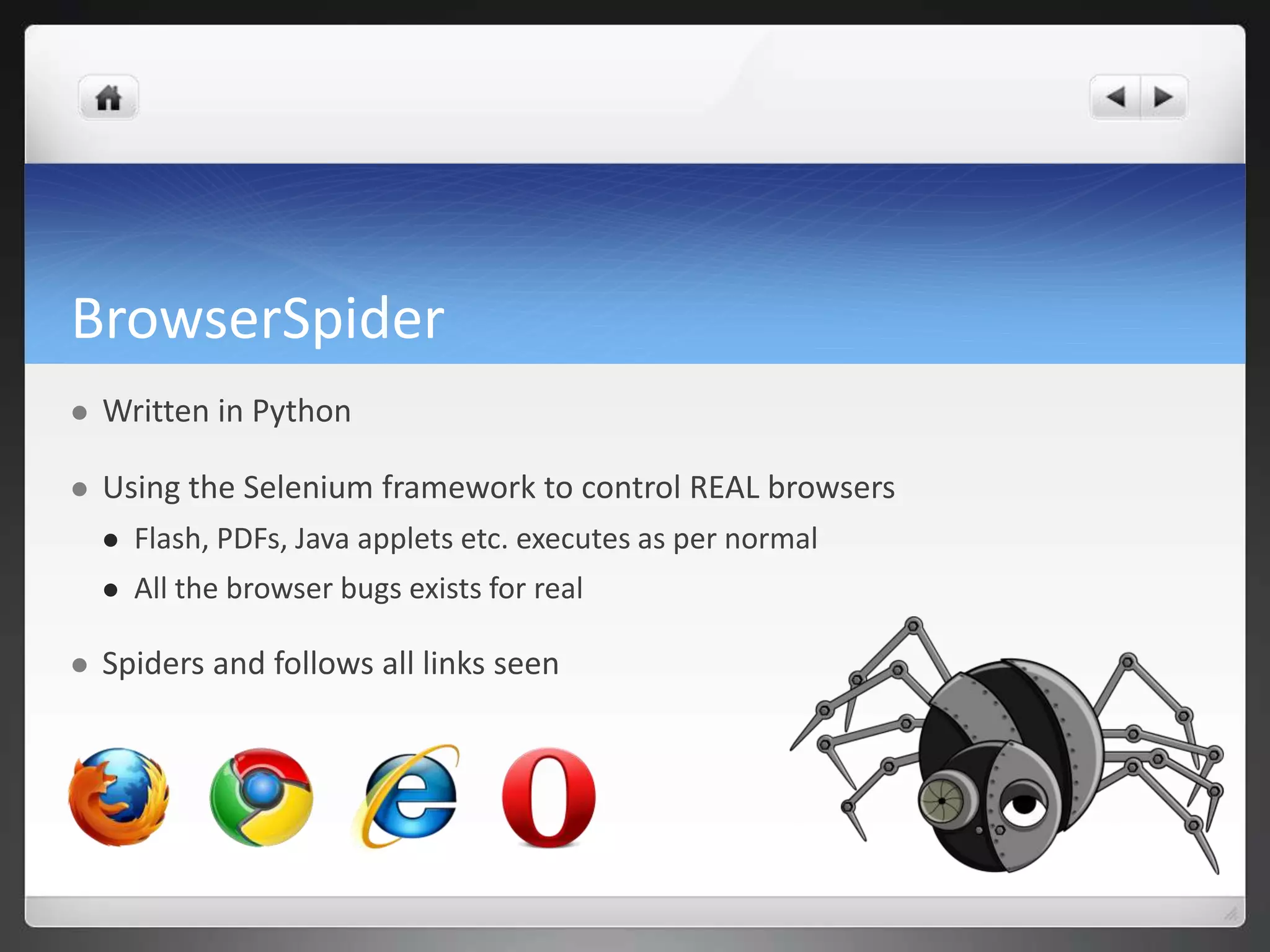
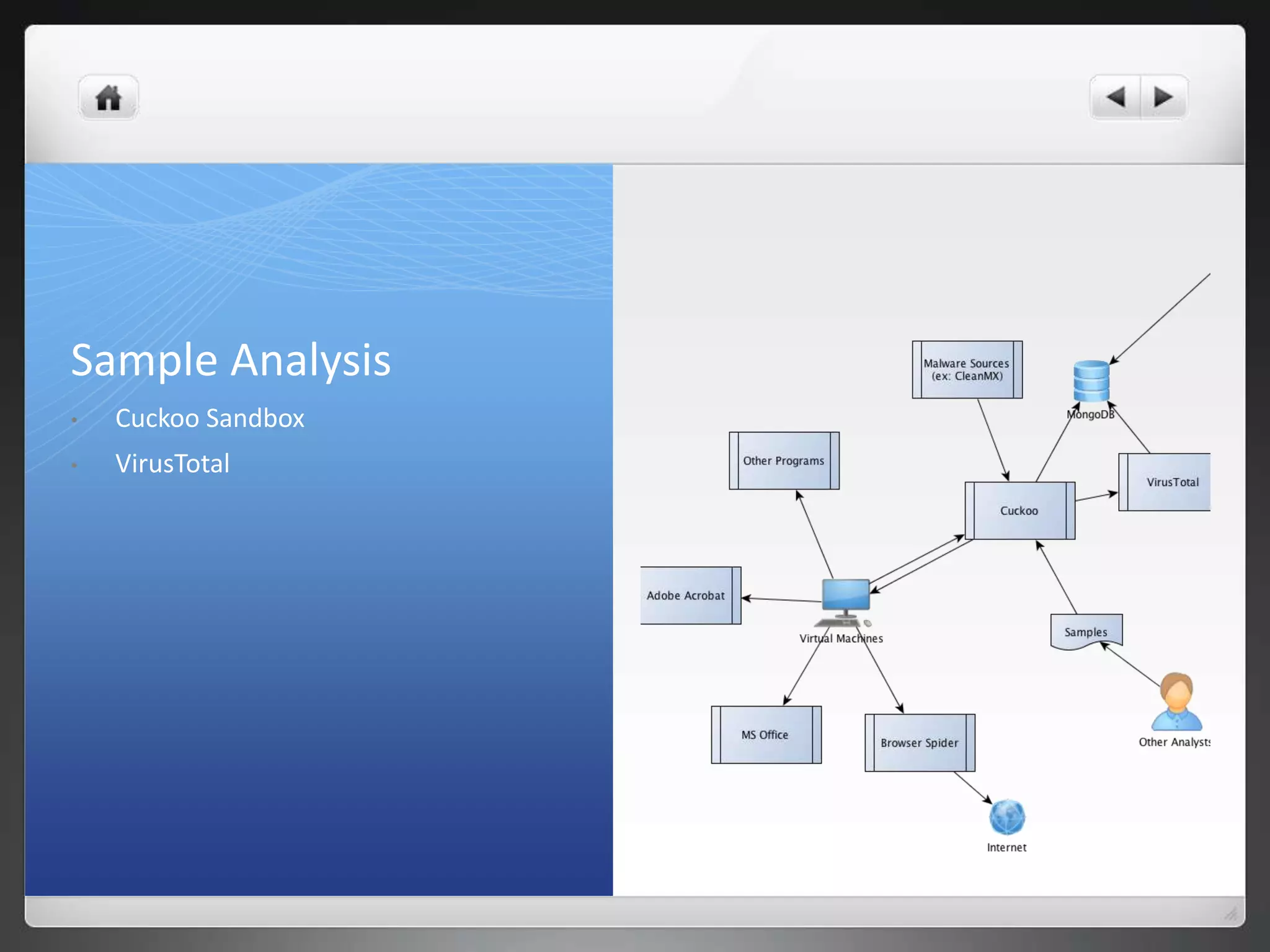
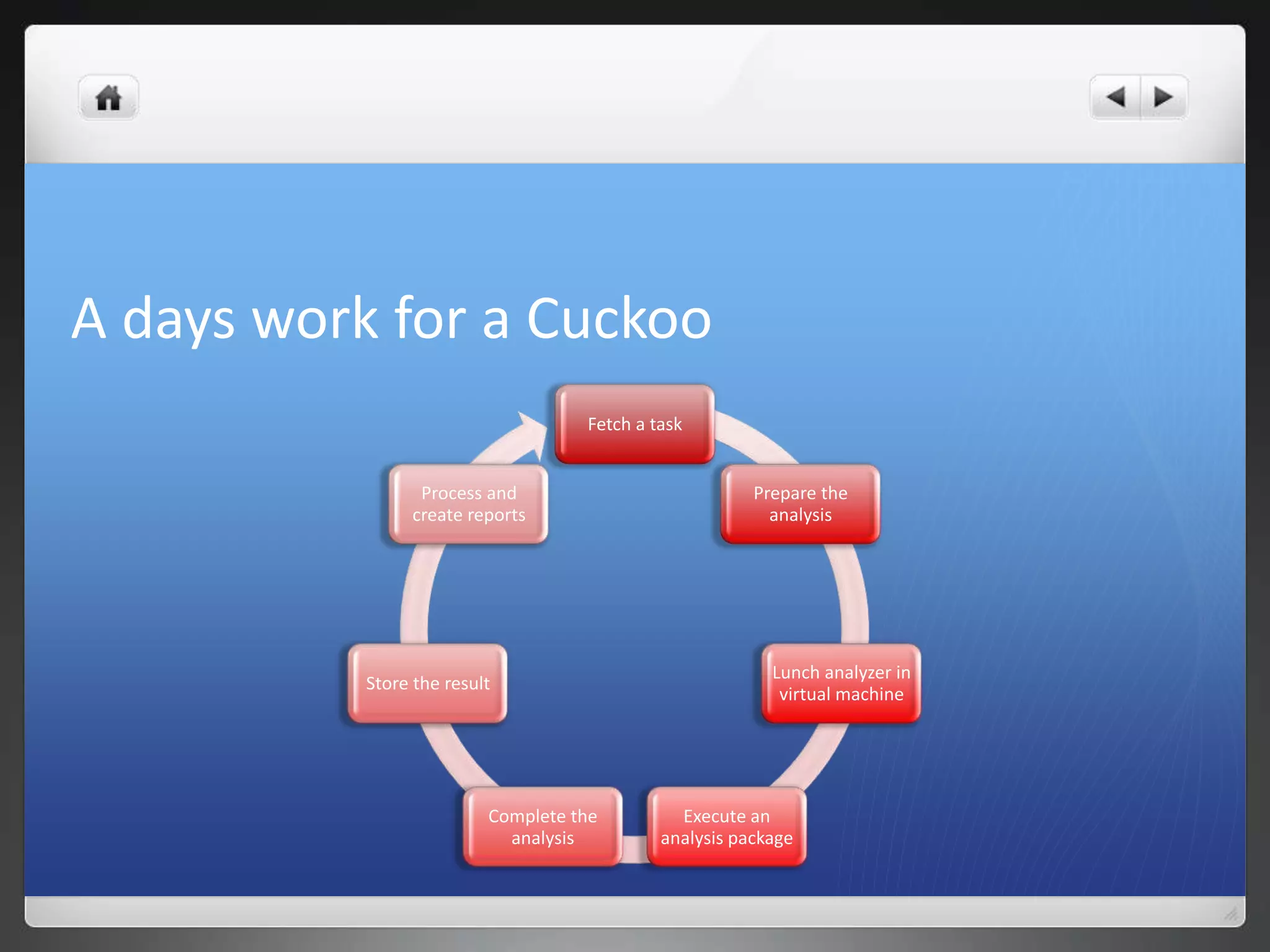
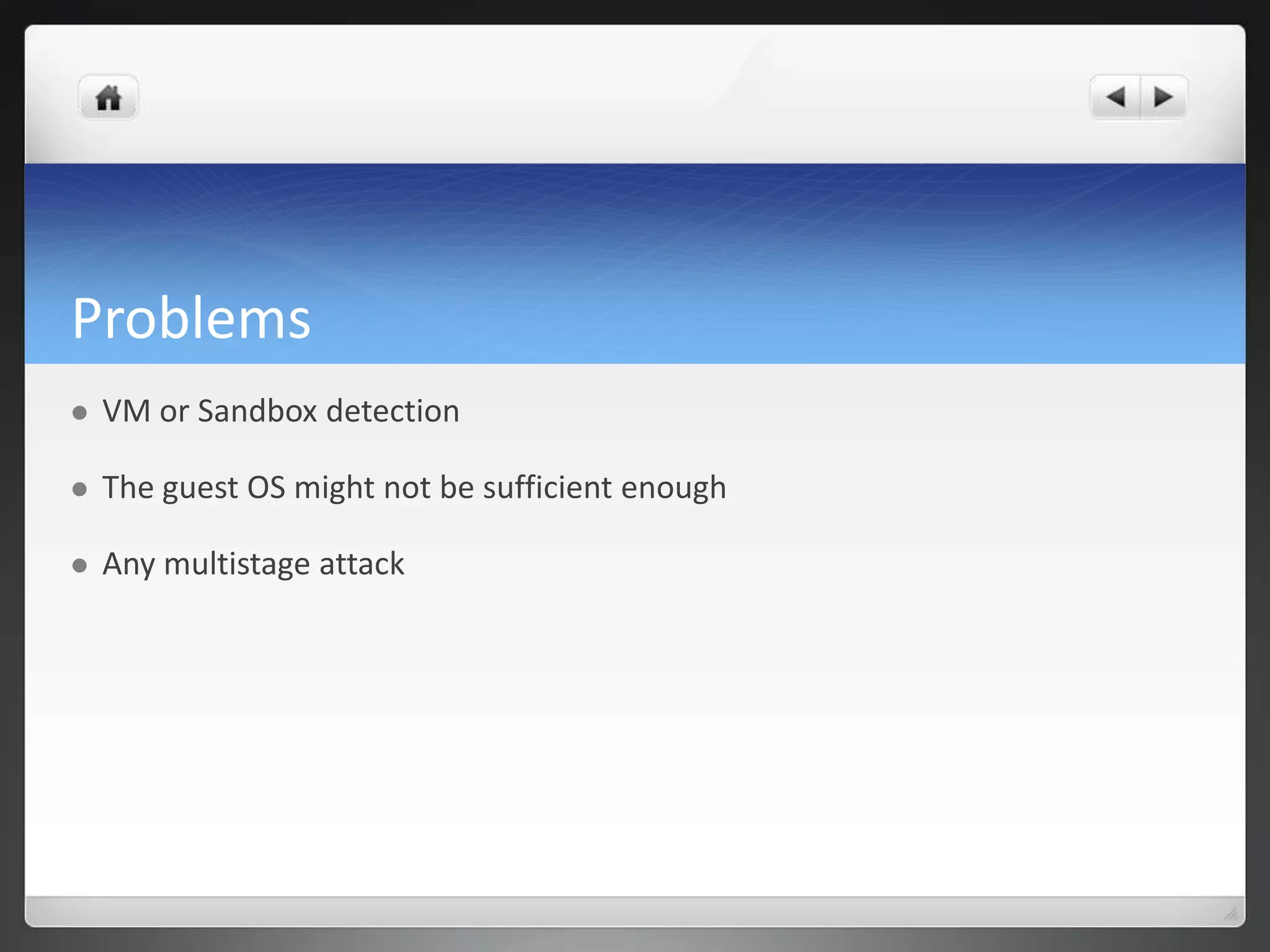
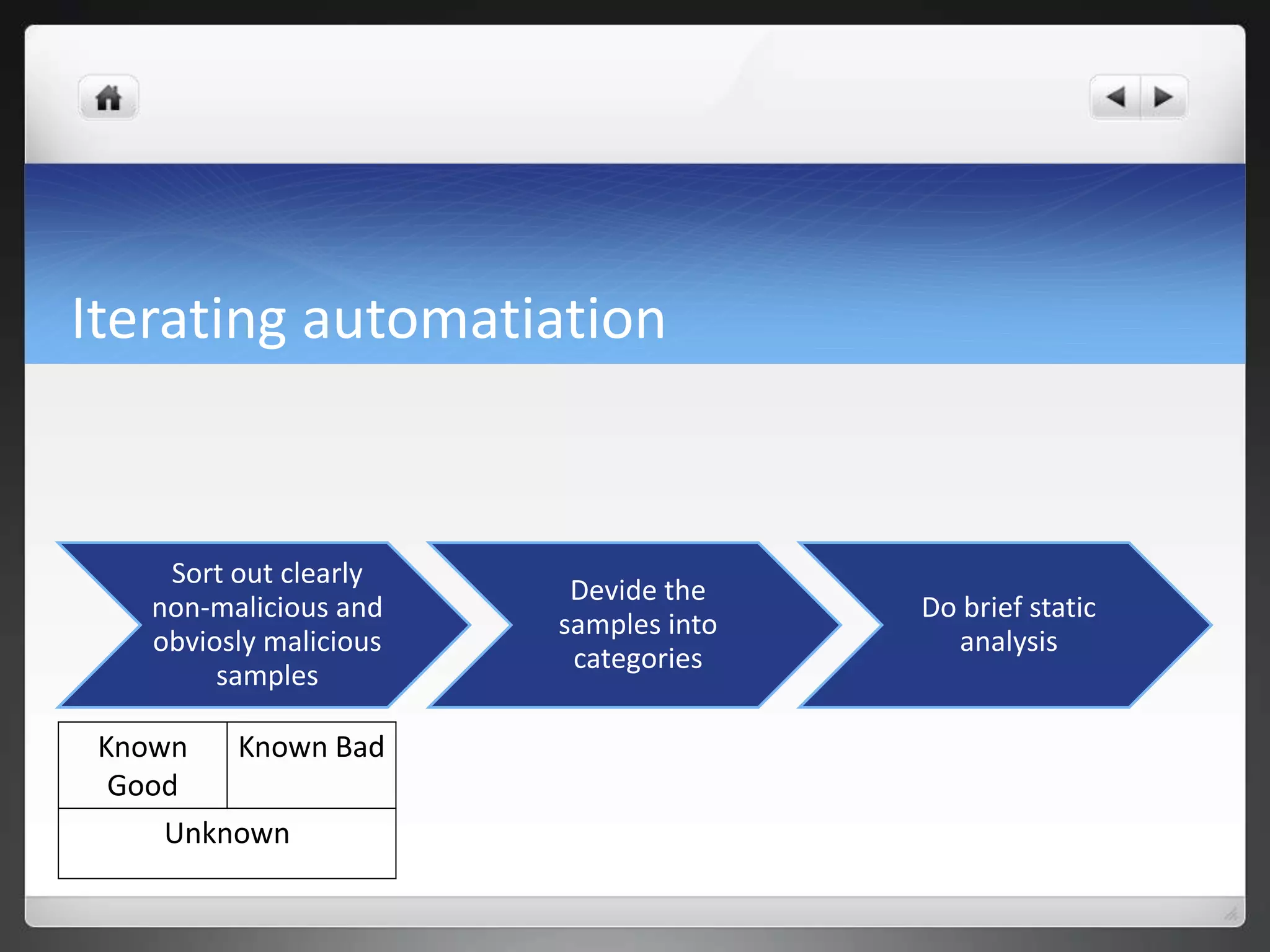
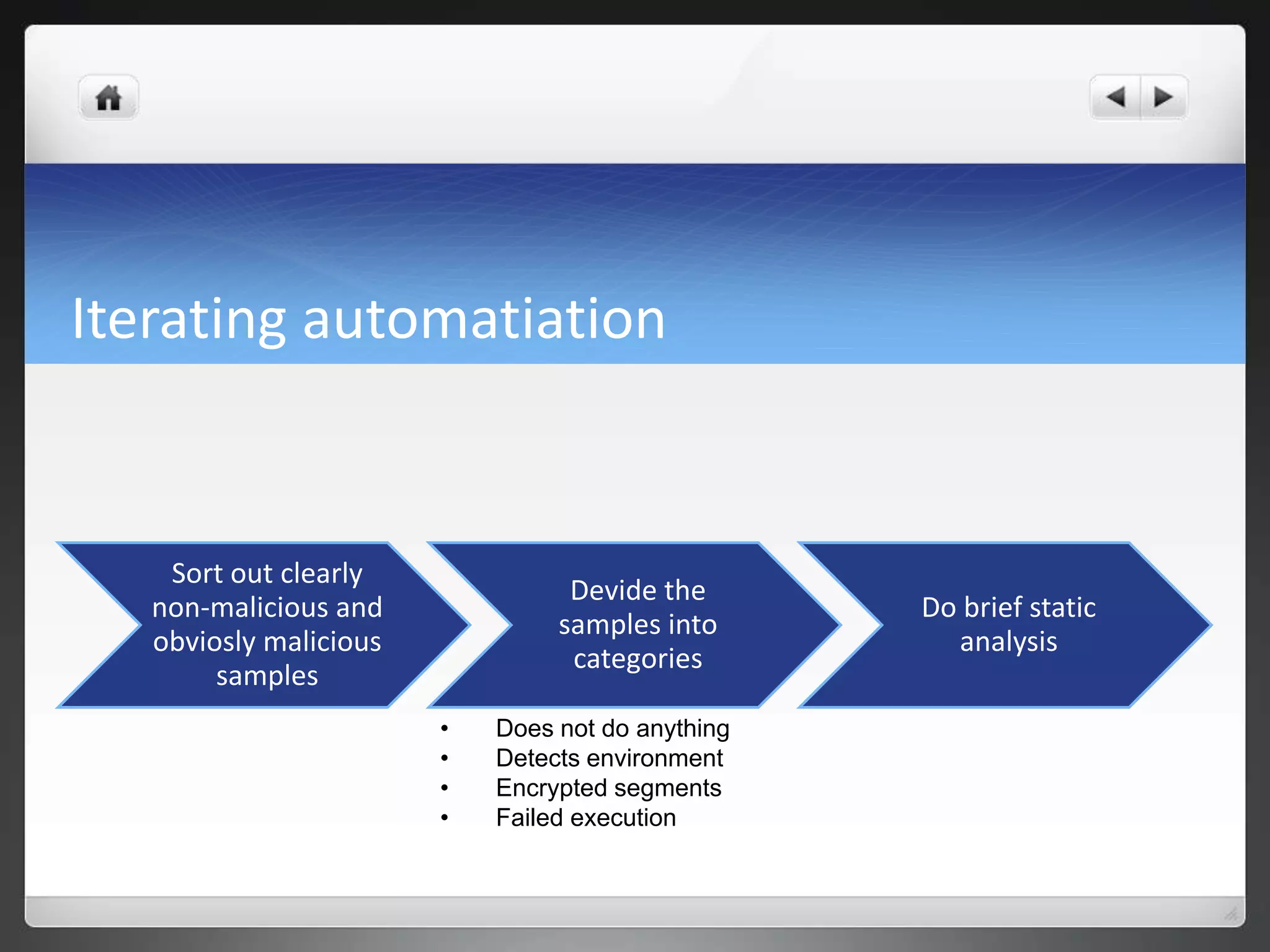
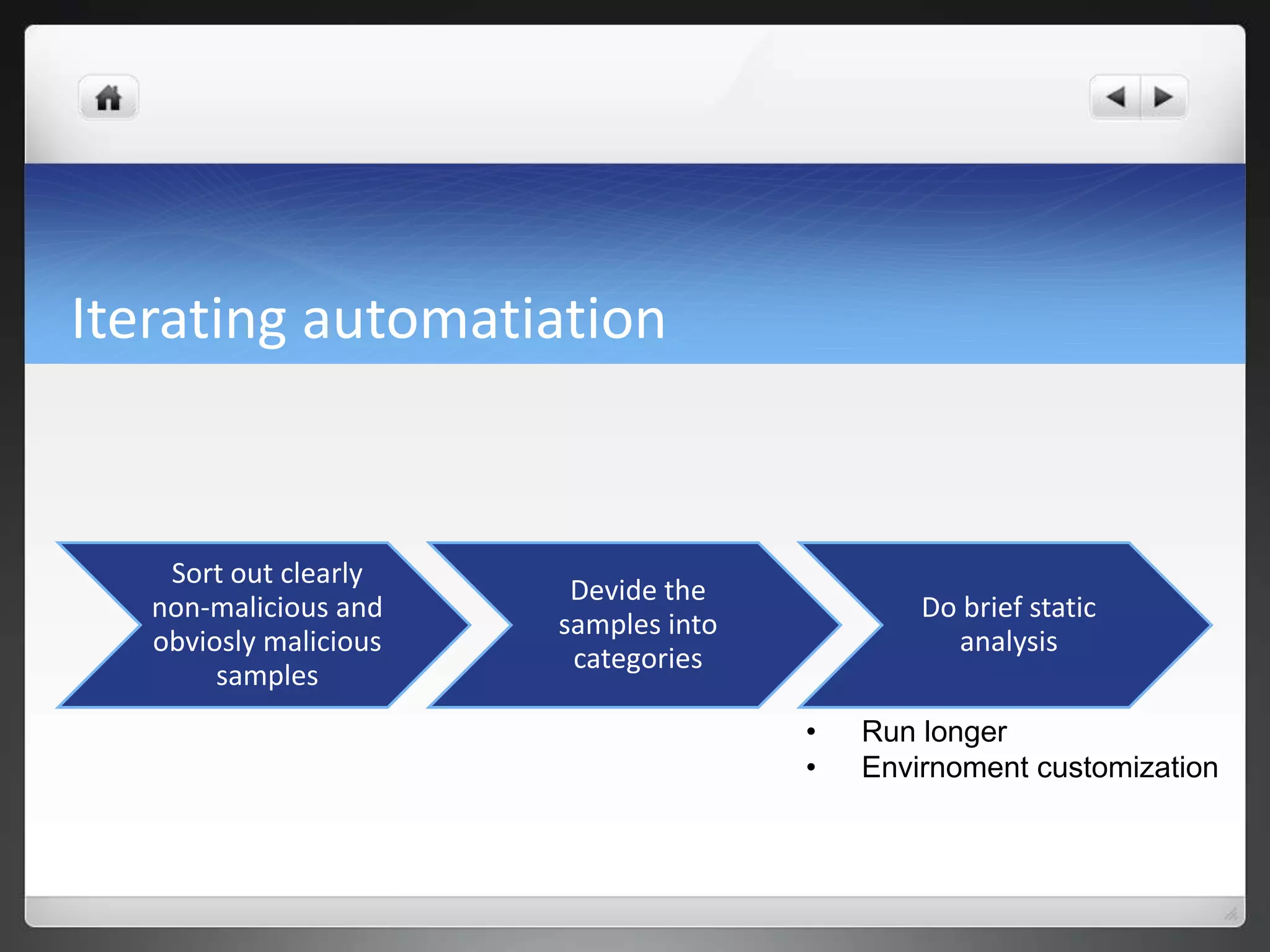
The document notes that manually analyzing malware can be time consuming and boring. MART was created to automate parts of the process such as sample acquisition, analysis using tools like Cuckoo Sandbox, and reporting. This reduces the time spent by malware analysts and allows them to focus on more complex samples. The system also aims to address limitations of virtual machine-based analysis by integrating additional techniques. Overall, MART streamlines malware analysis as a hobby while cutting costs compared to paying for commercial solutions.