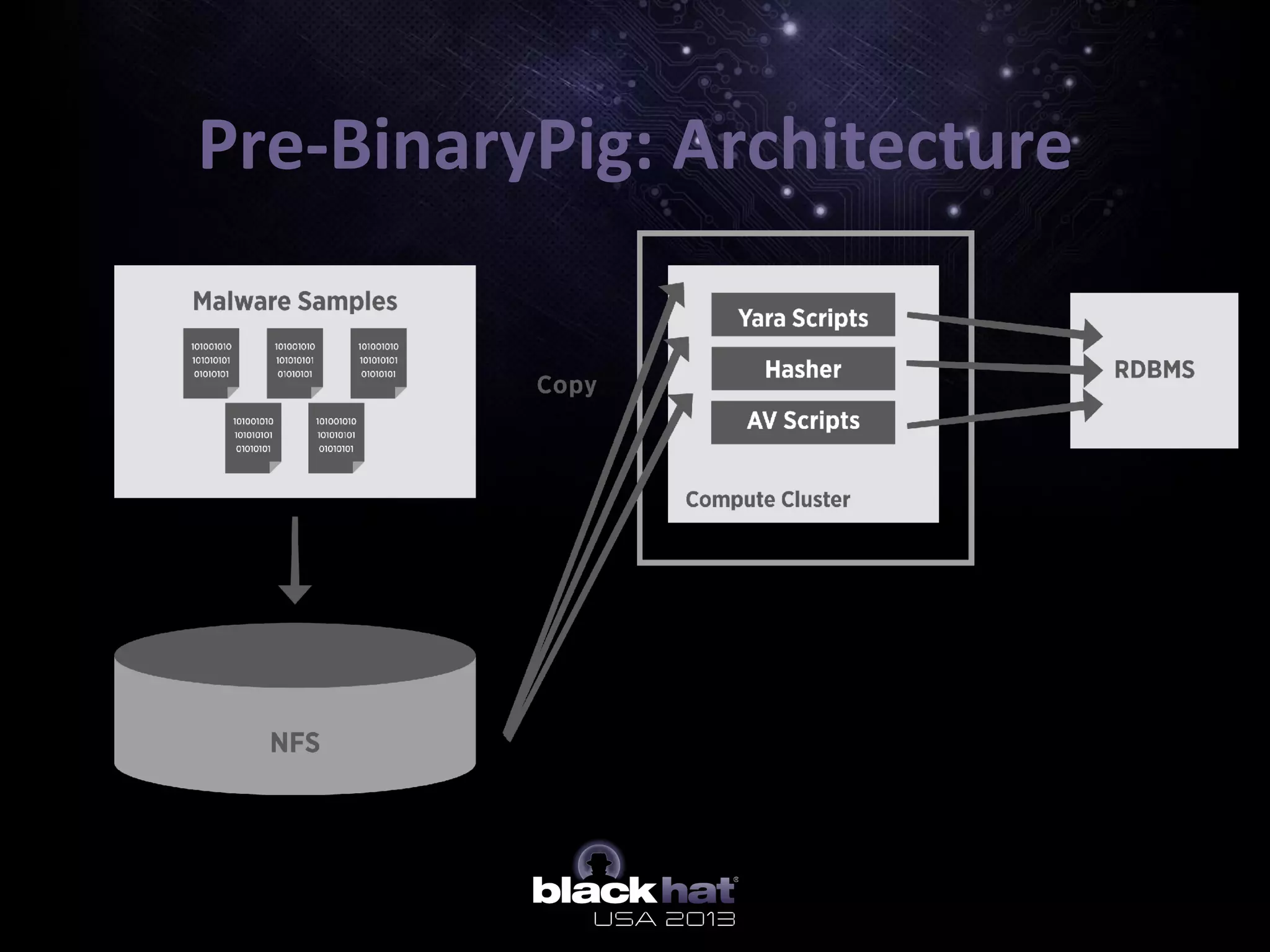
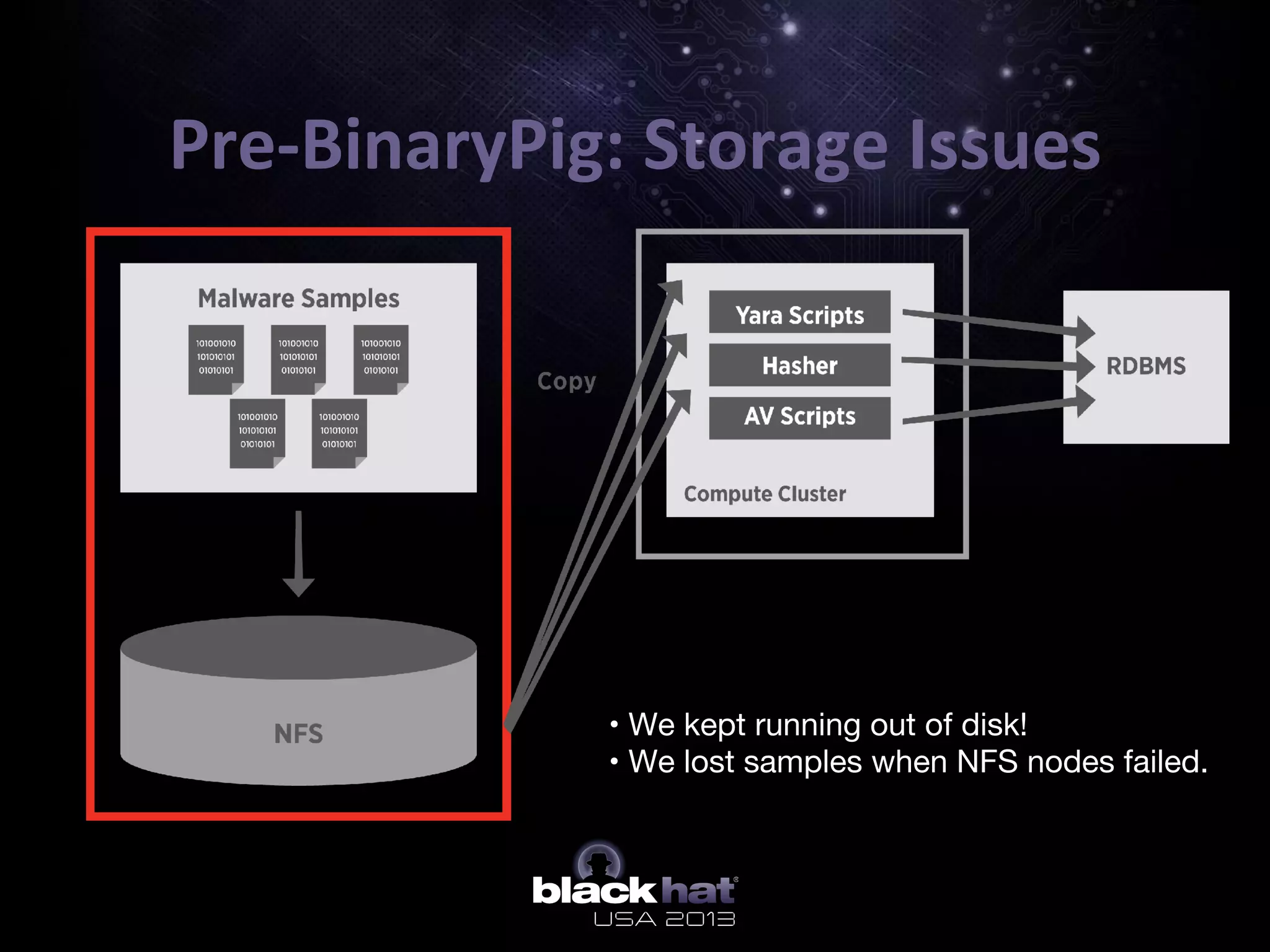
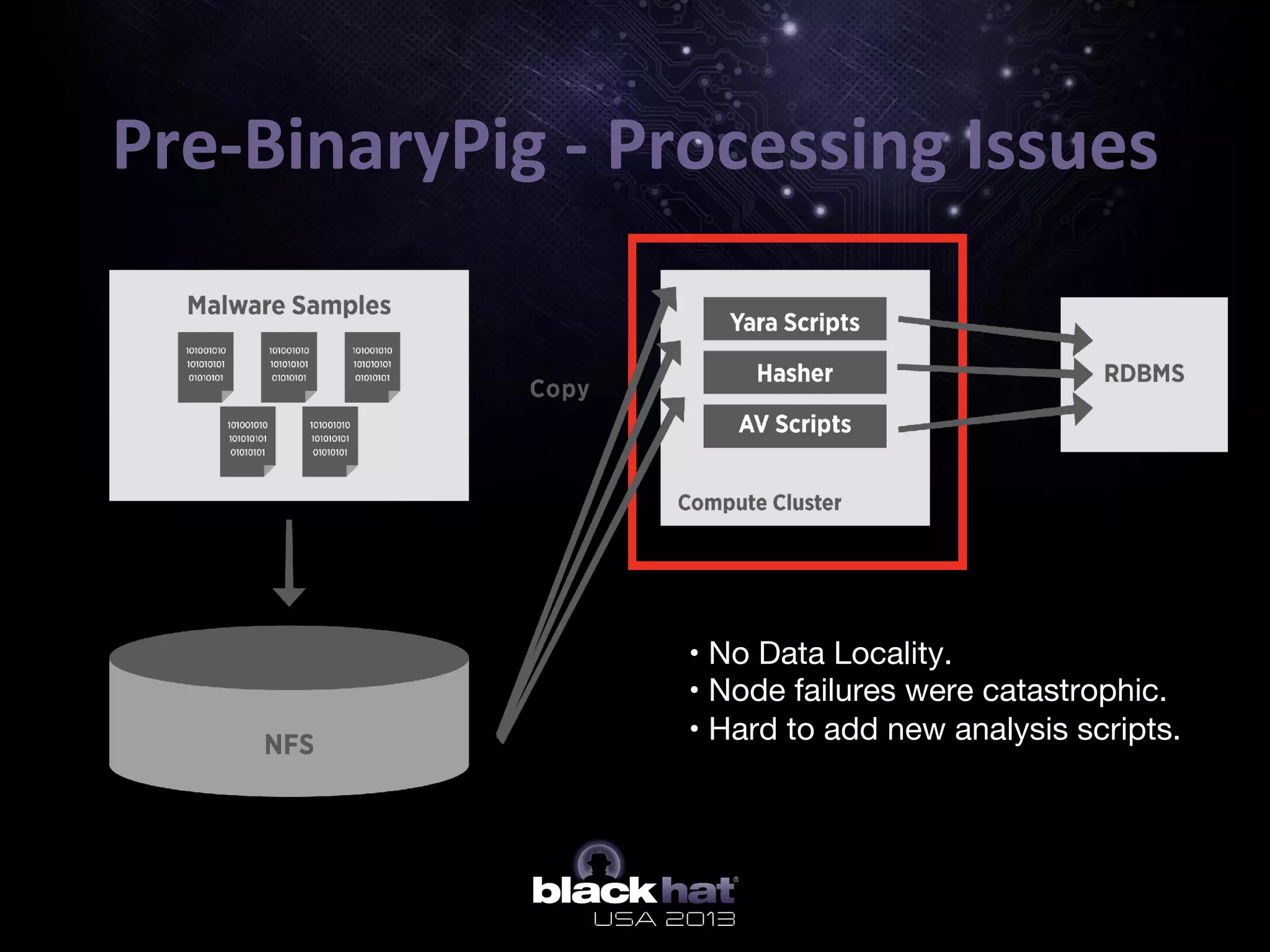
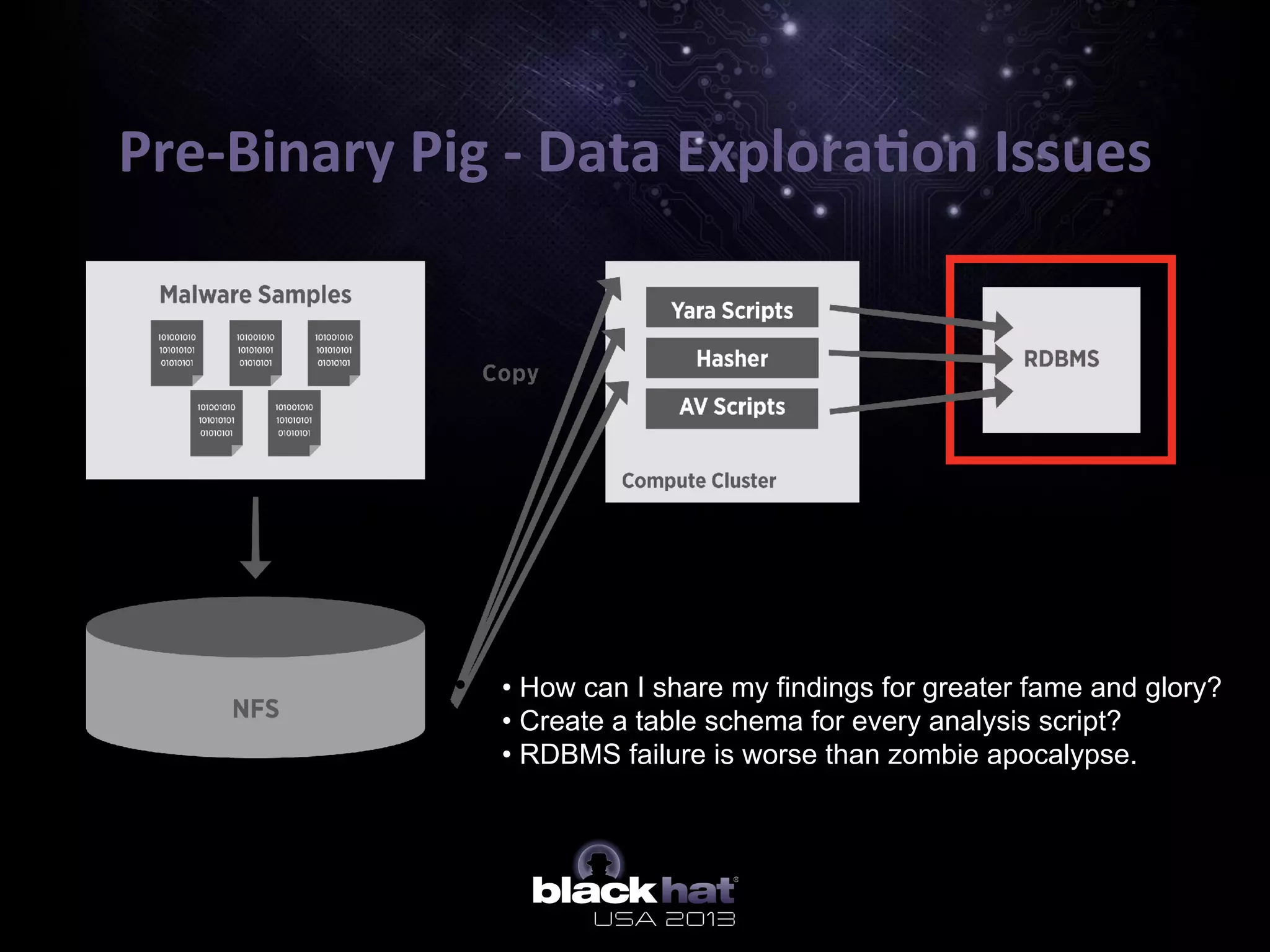
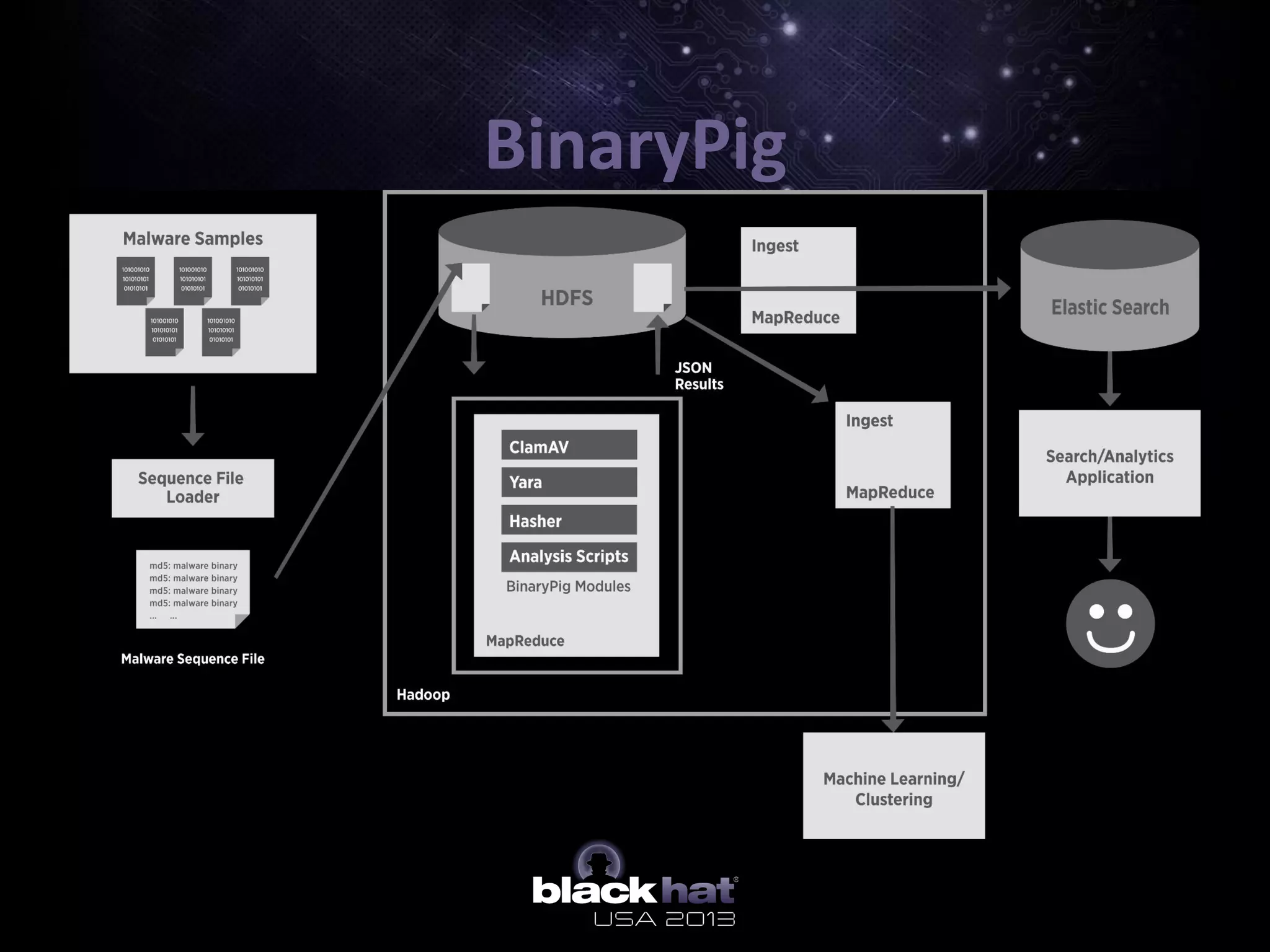
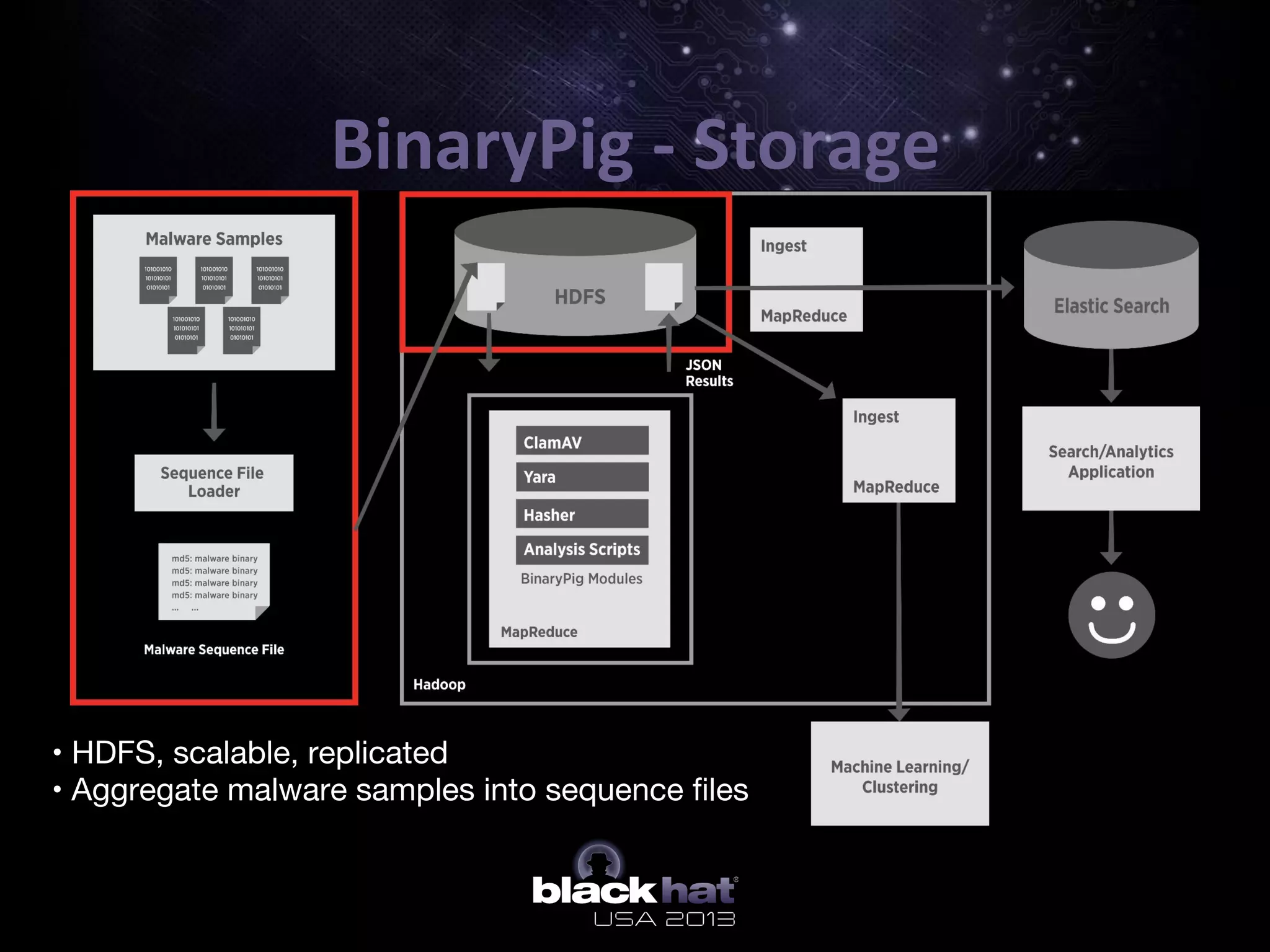
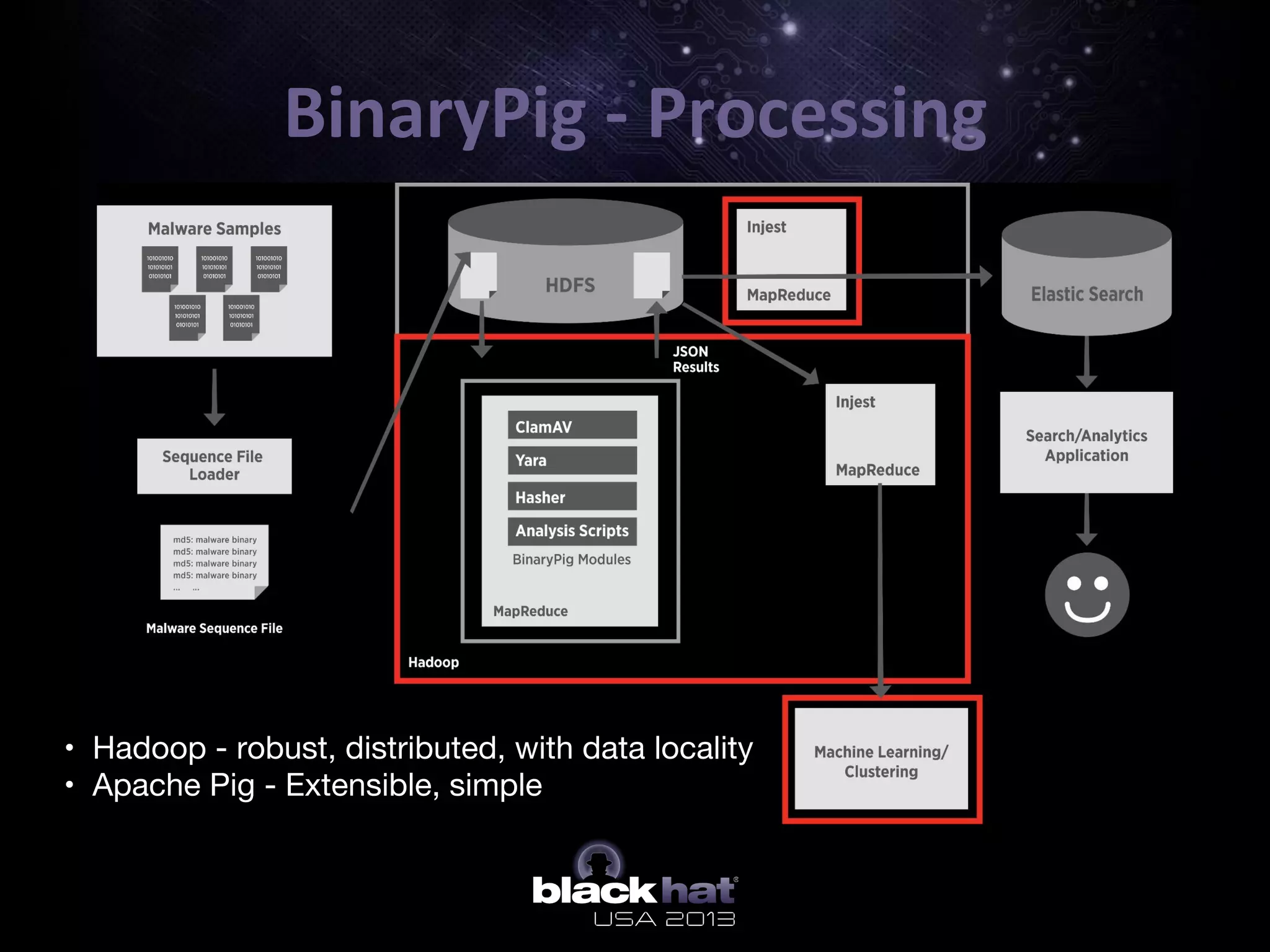
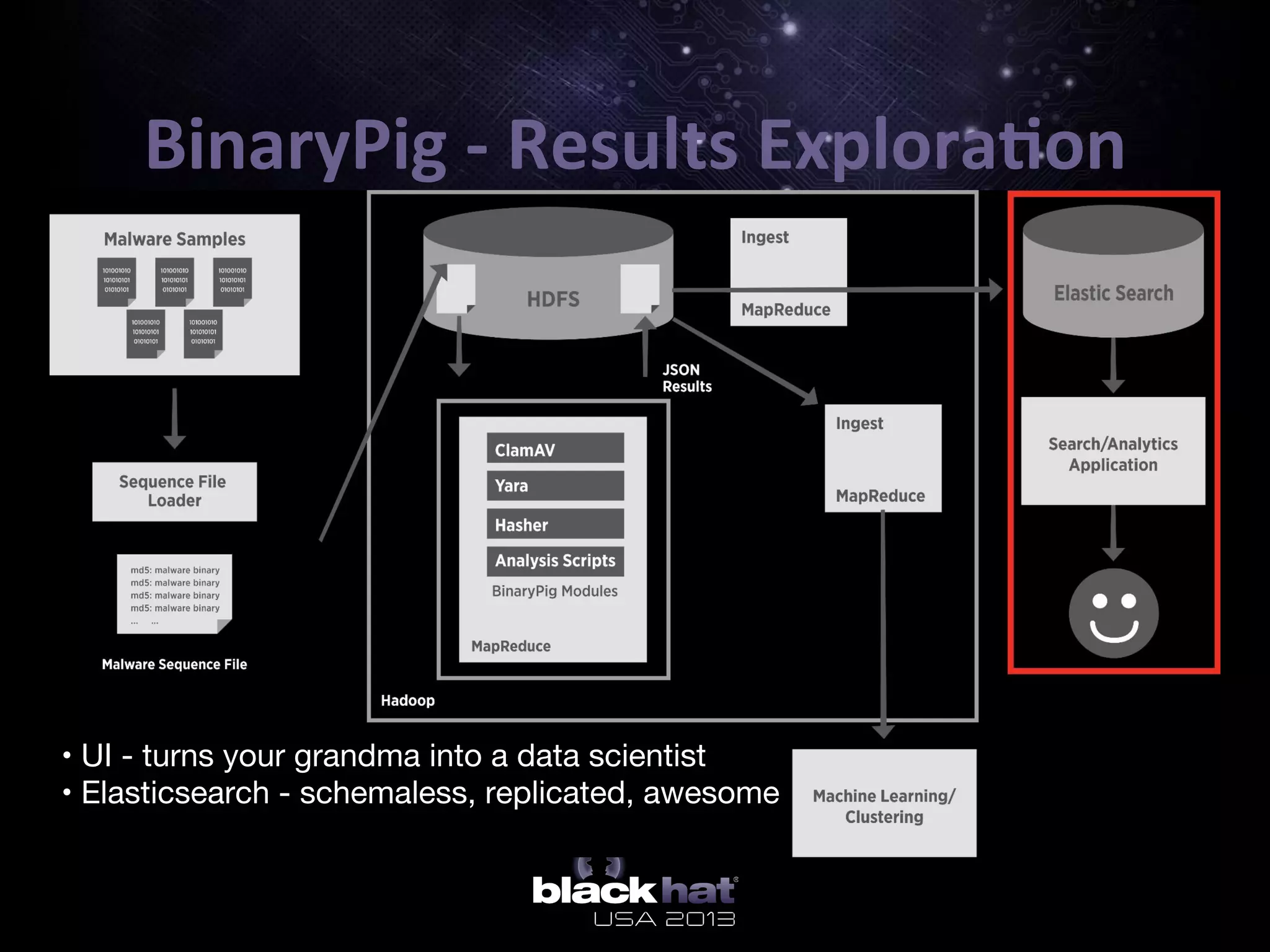
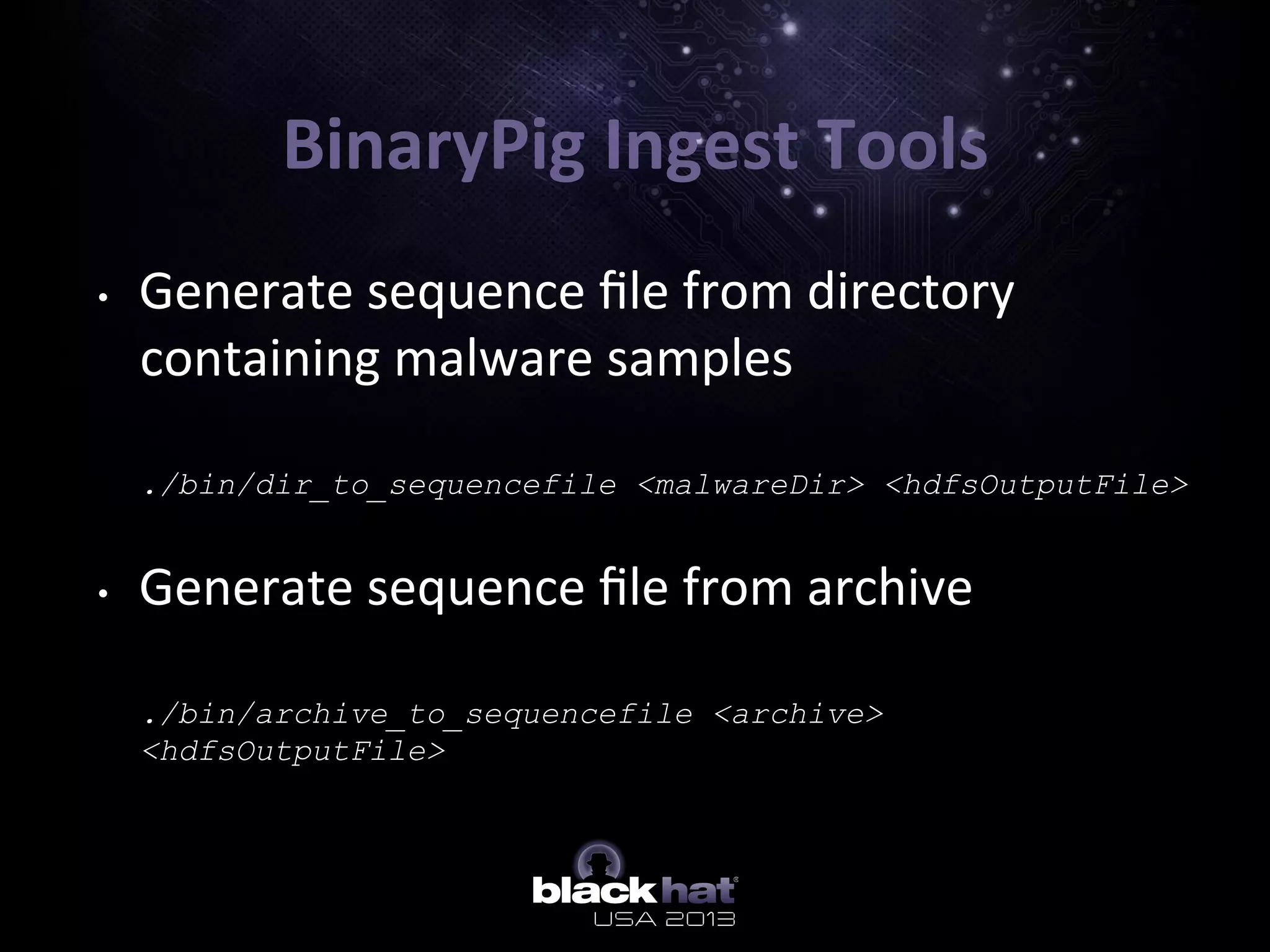
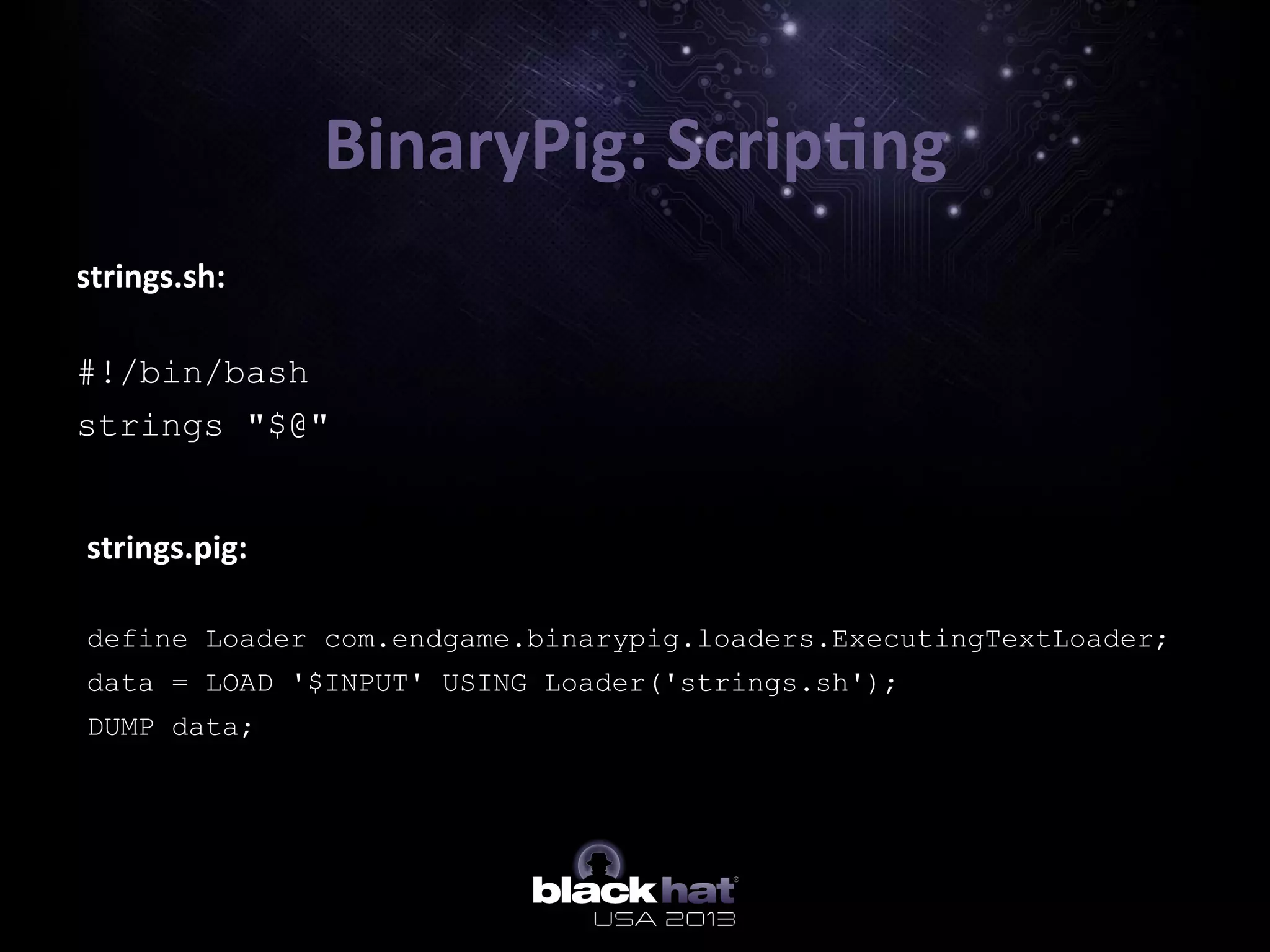
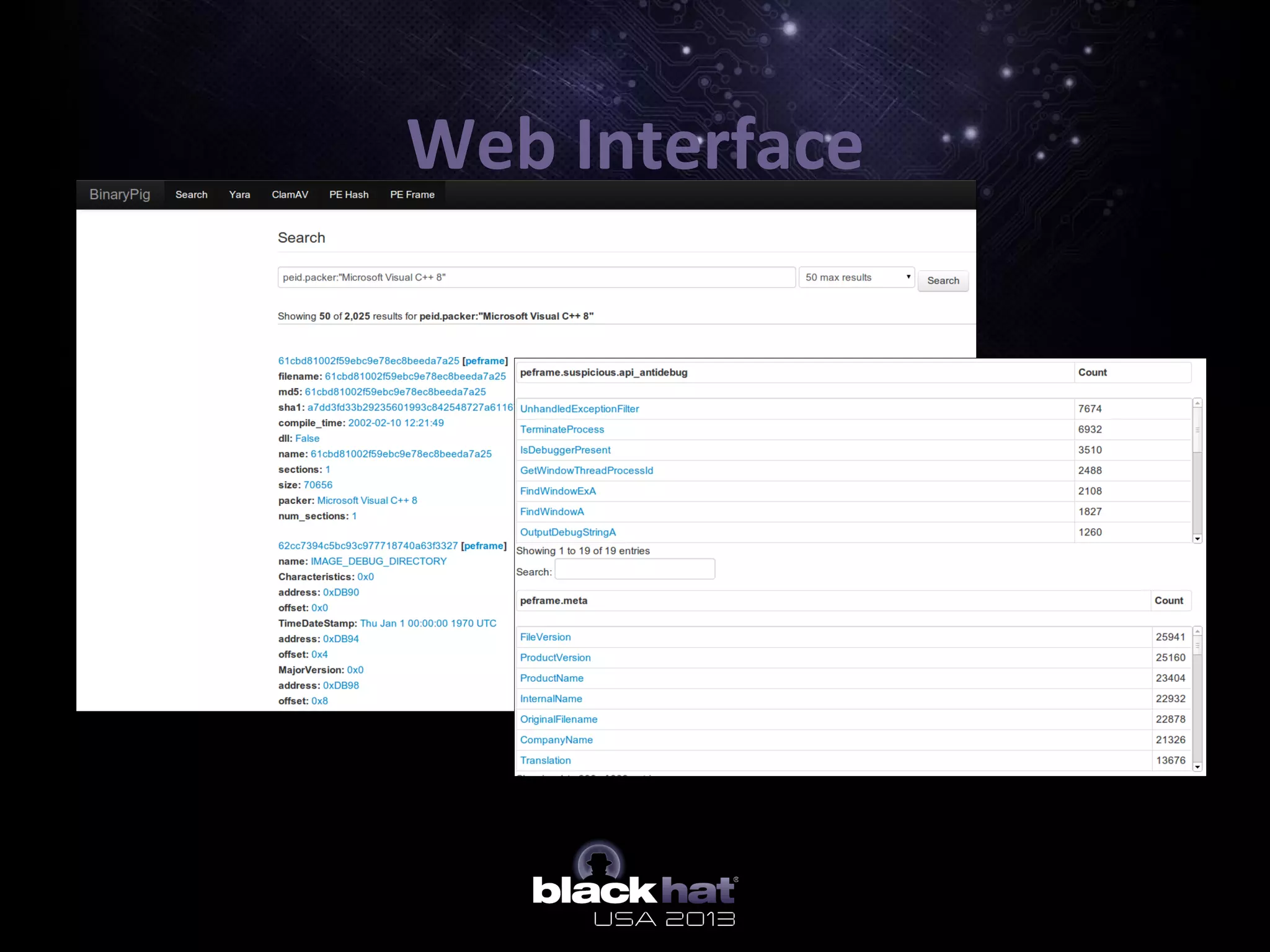
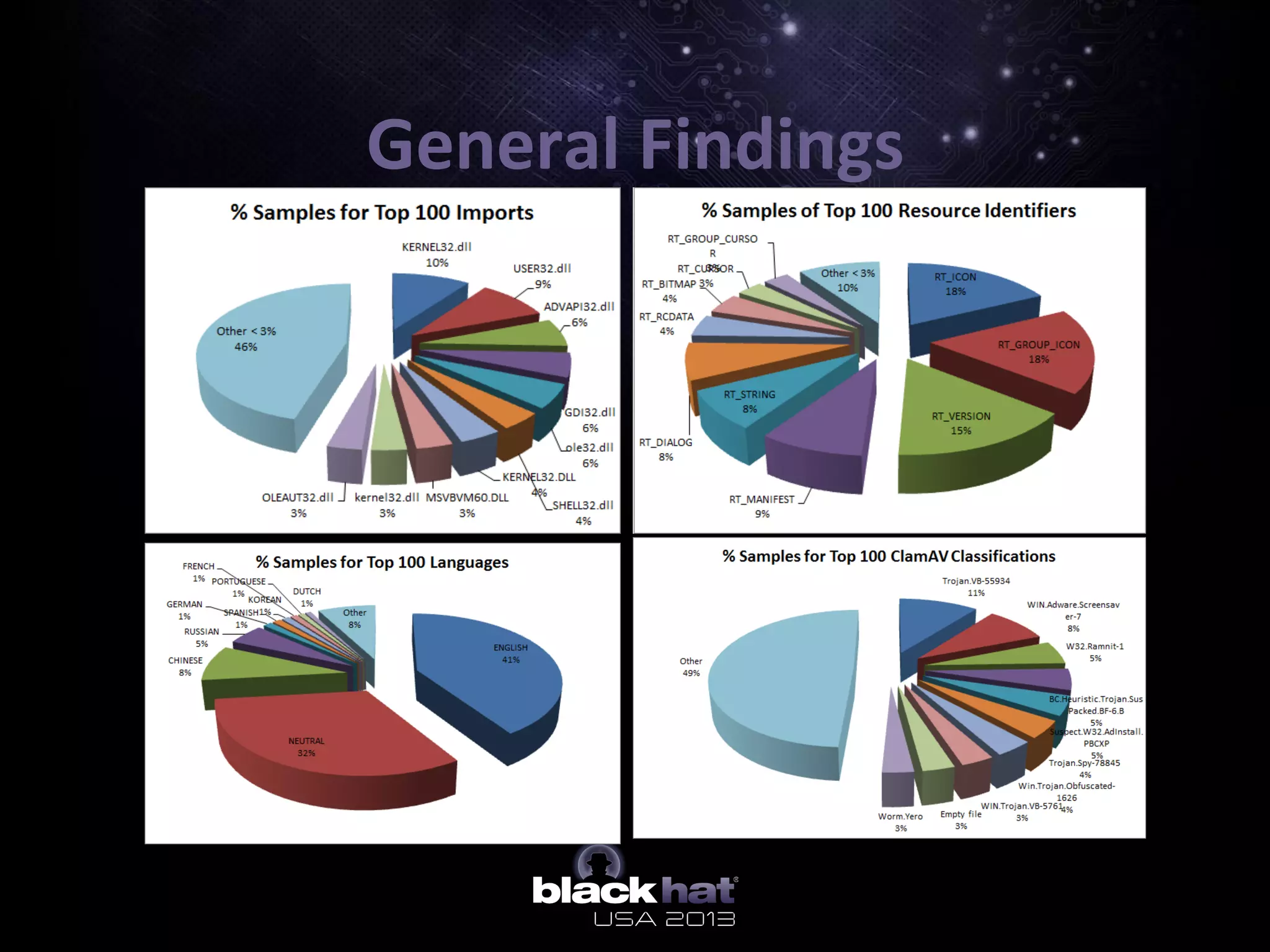
The document describes BinaryPig, a framework for processing small binary files like malware samples using Apache Hadoop and Apache Pig. It allows for scalable storage and analysis of large datasets. BinaryPig addresses issues with previous approaches like lack of data locality, failure resilience, and dynamic schema support. It introduces loaders for running analysis scripts and daemons on binary data to extract features. Clustering results on a dataset of 20 million malware samples are also presented to demonstrate BinaryPig's capabilities for malware triage and research.