Embed presentation
Download as PDF, PPTX

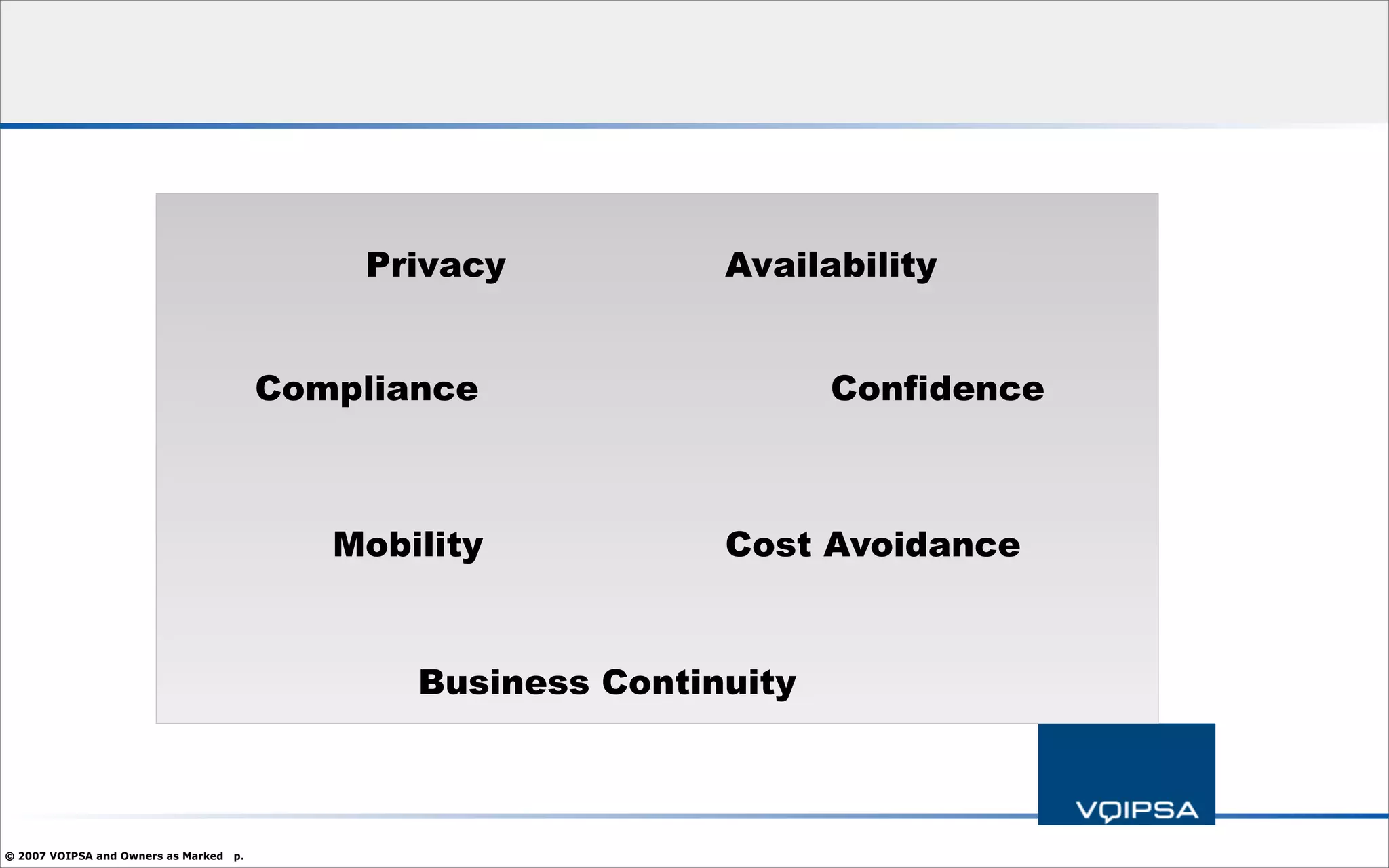

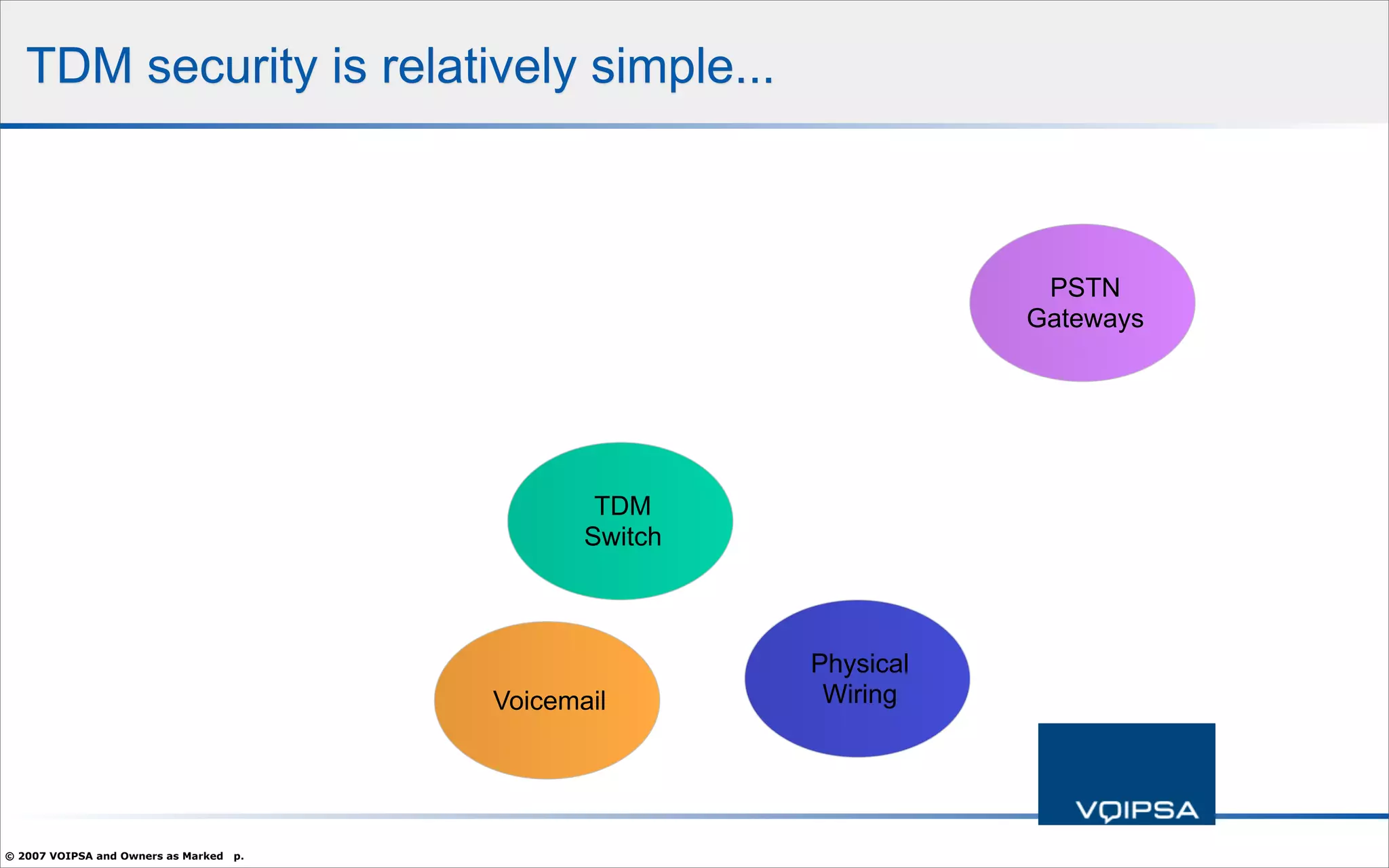
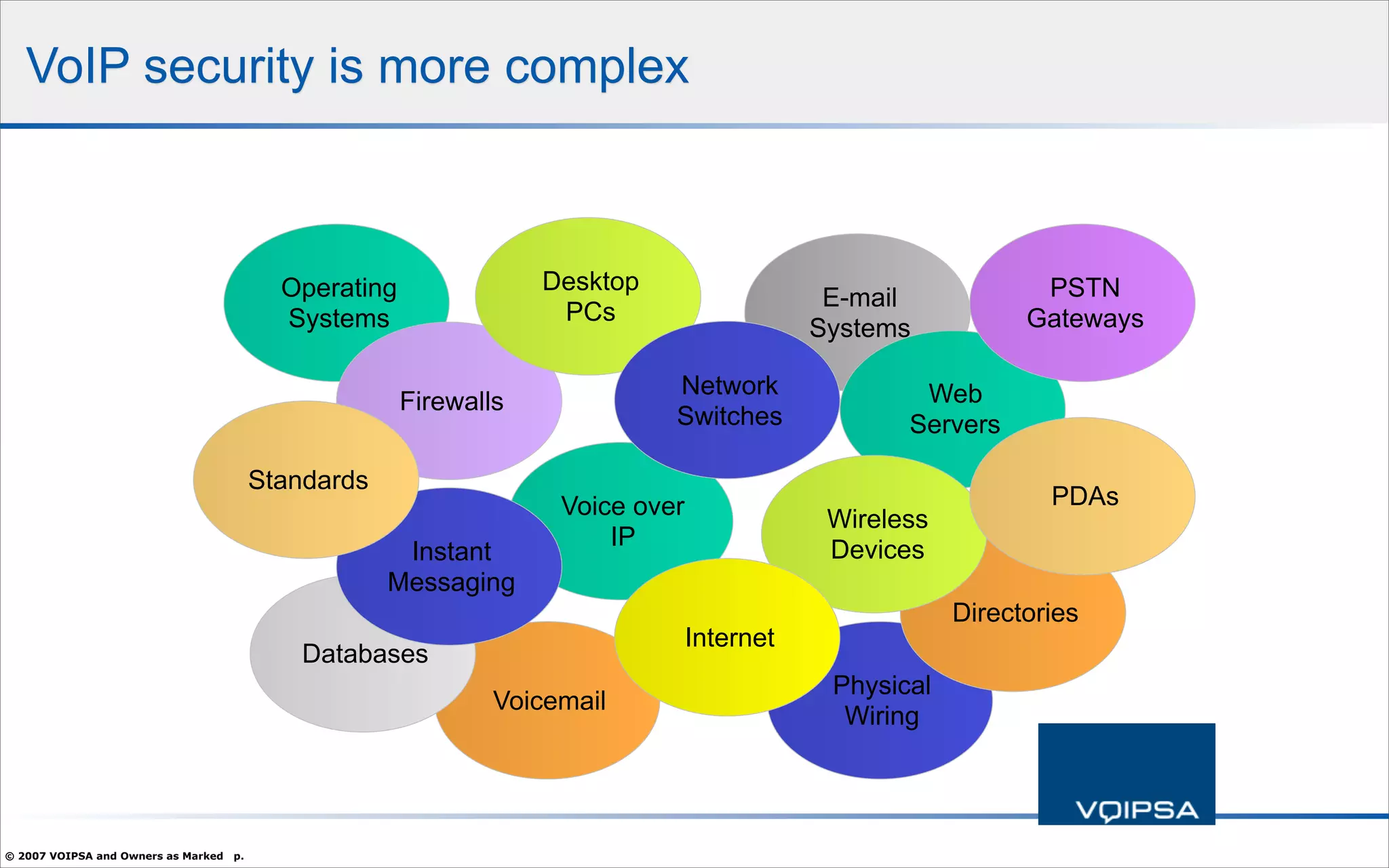
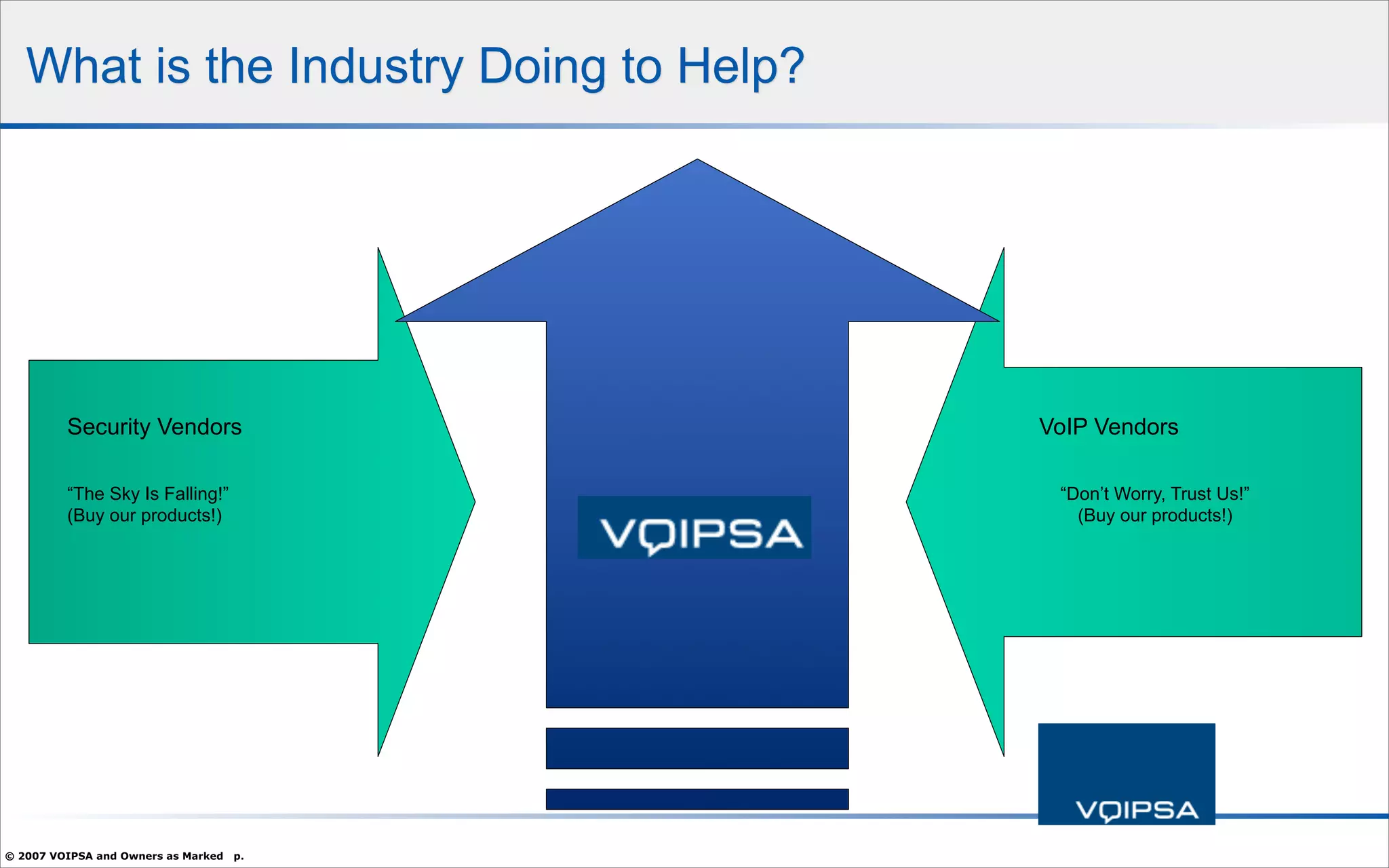
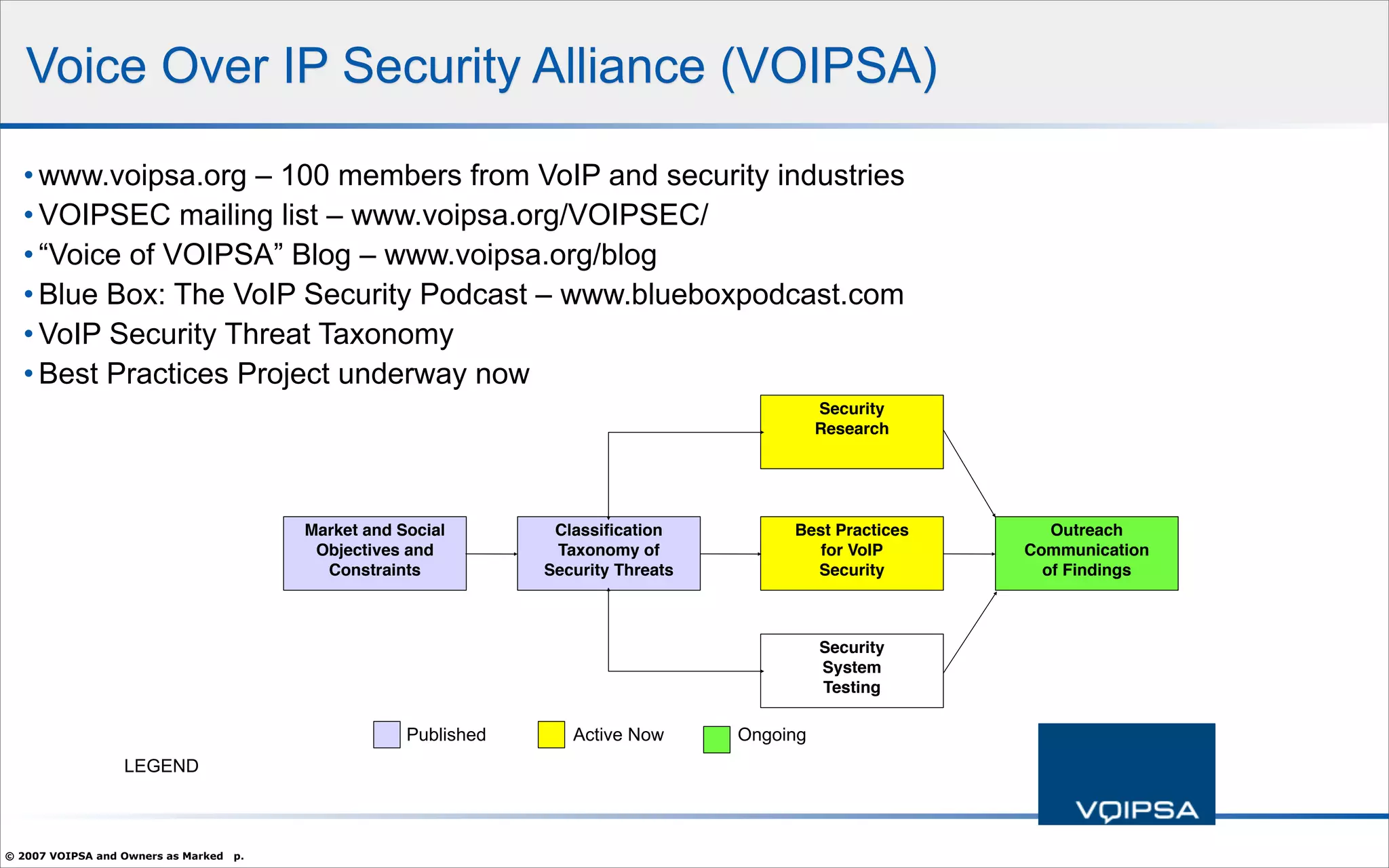



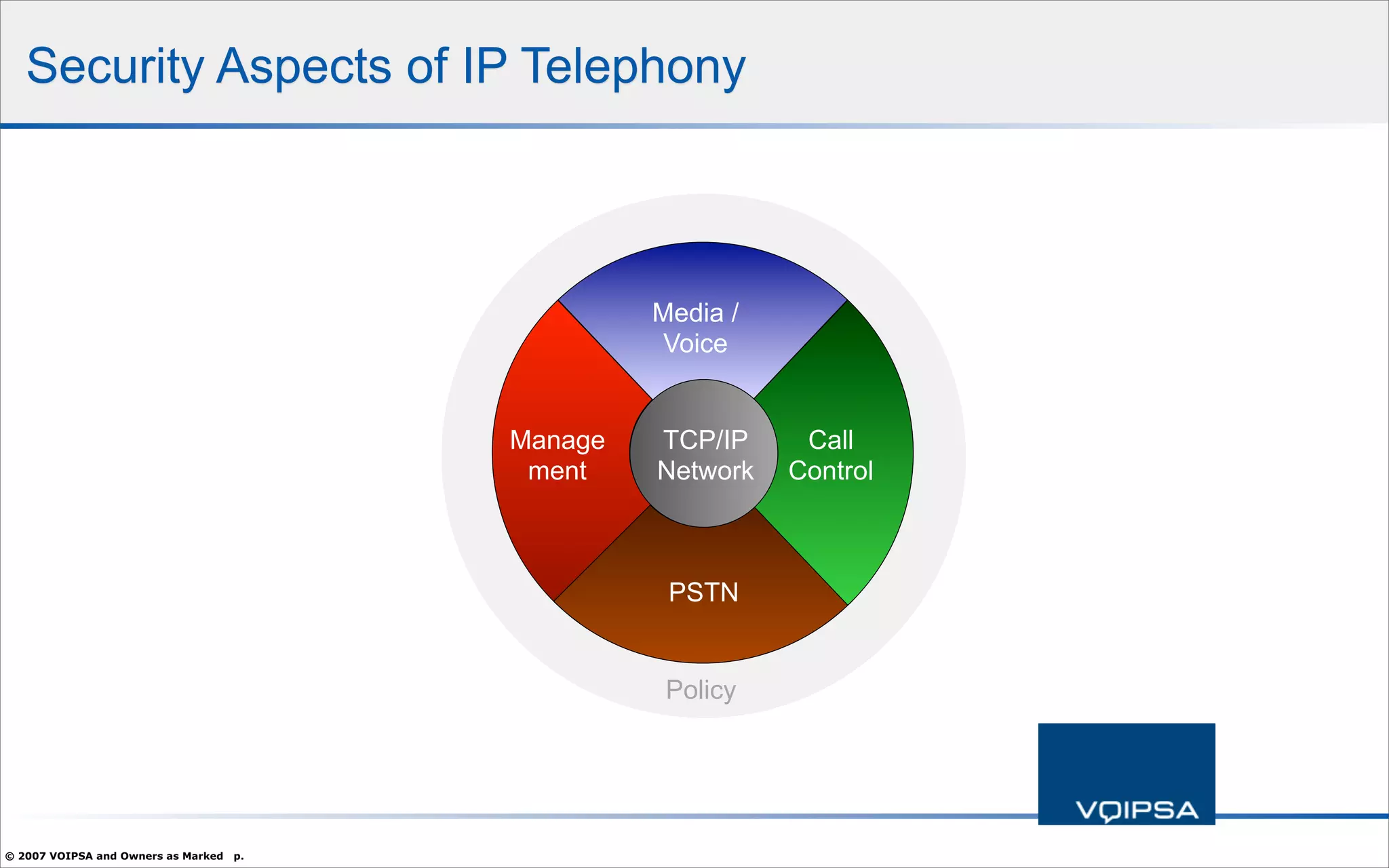
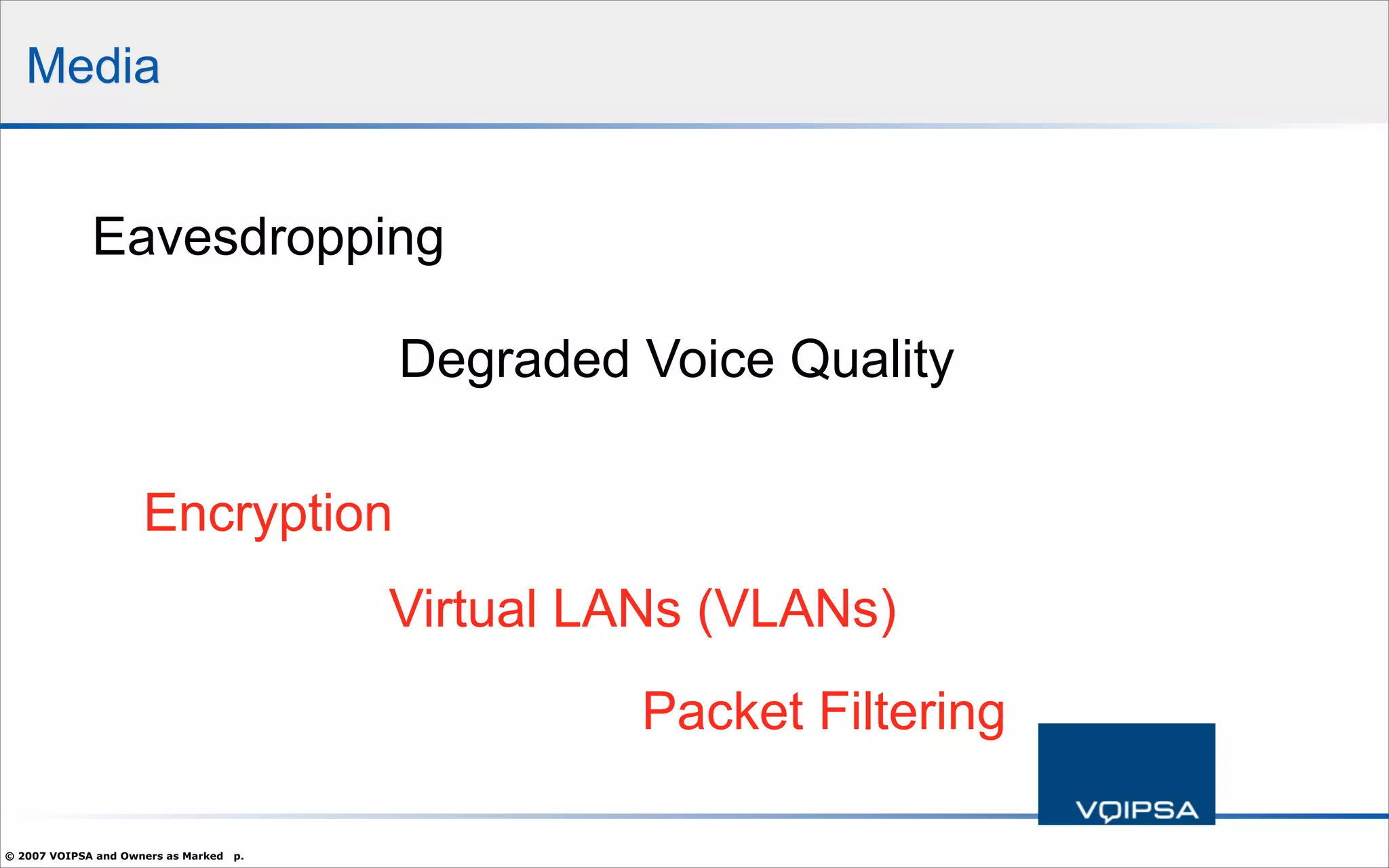
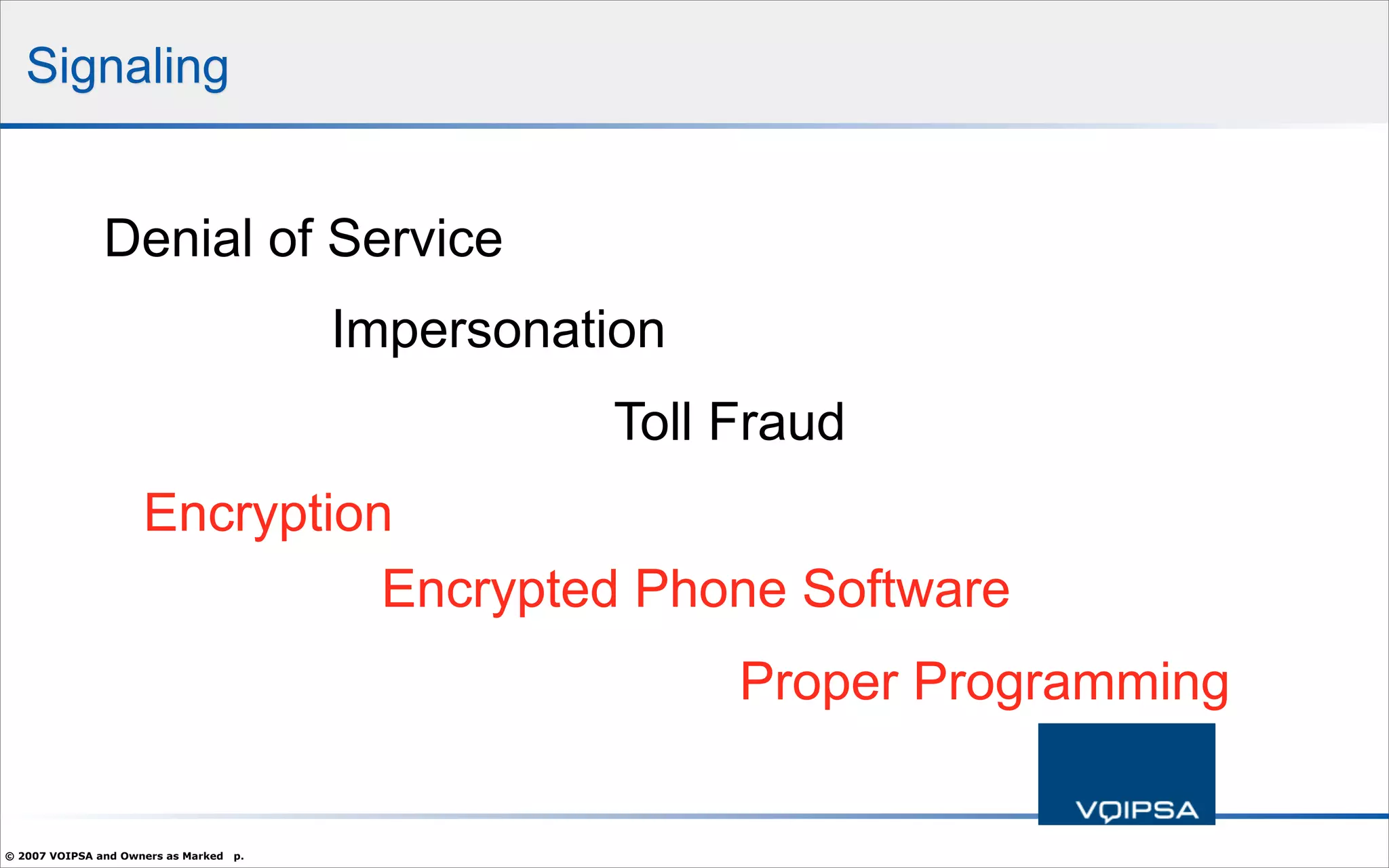
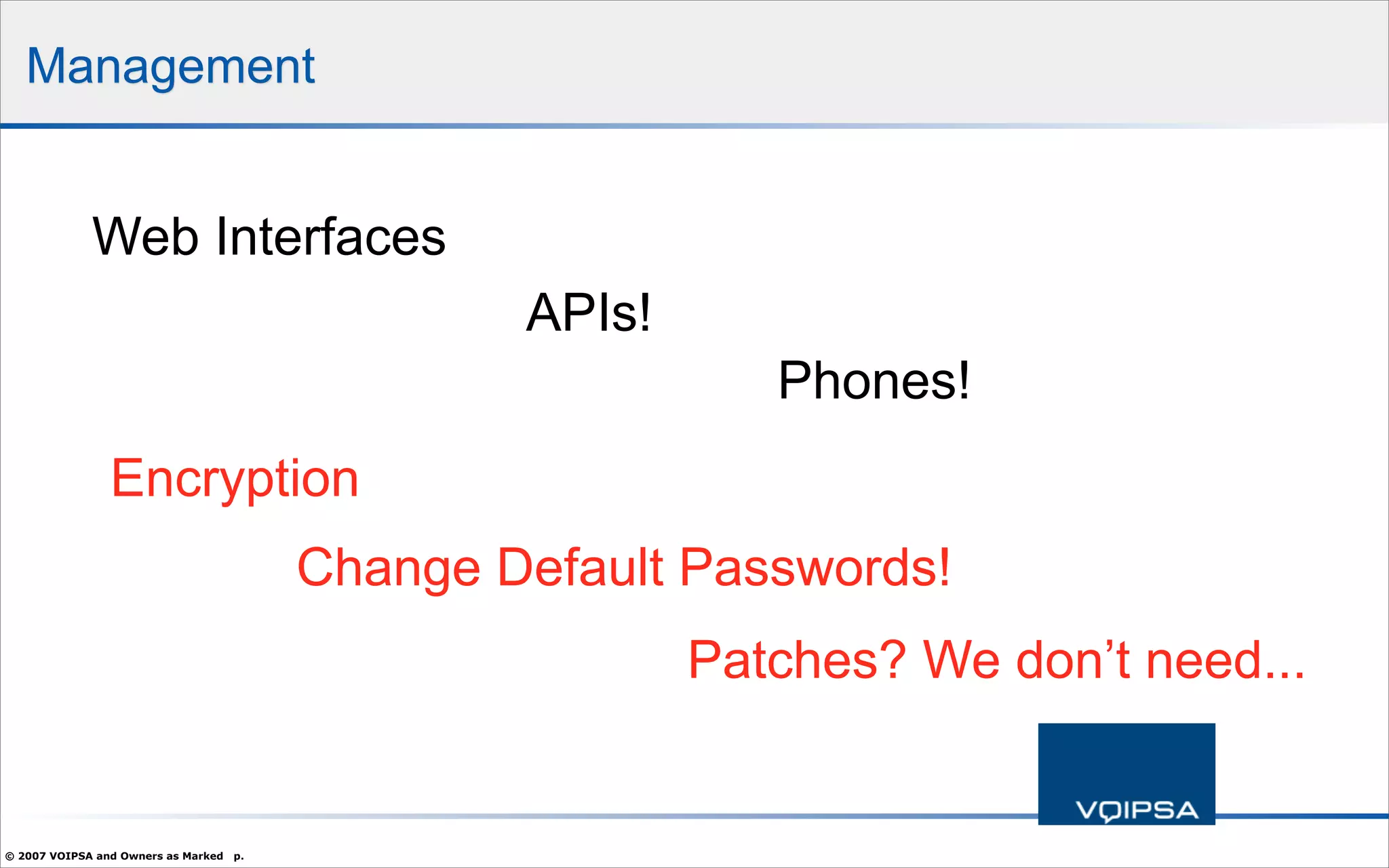
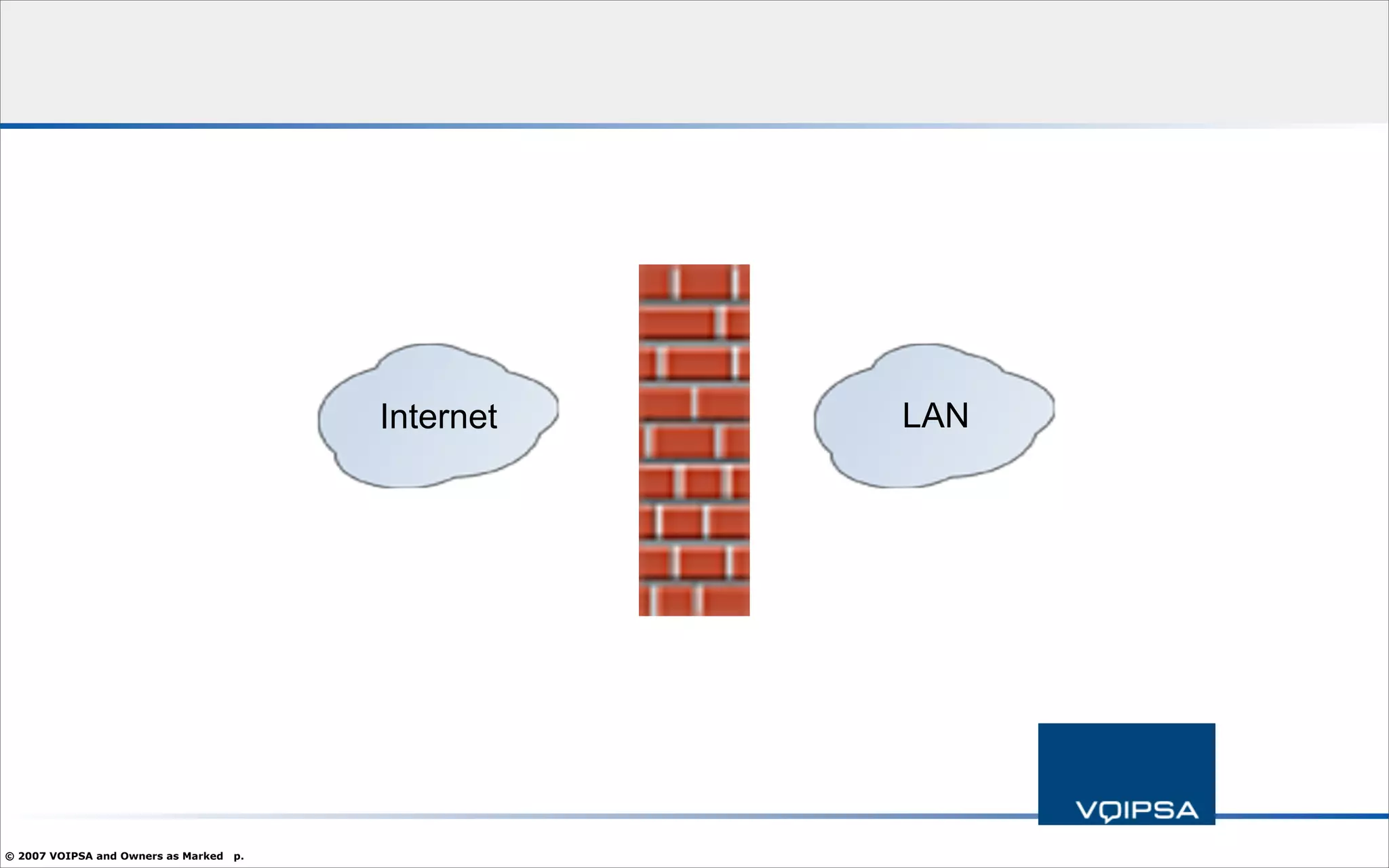

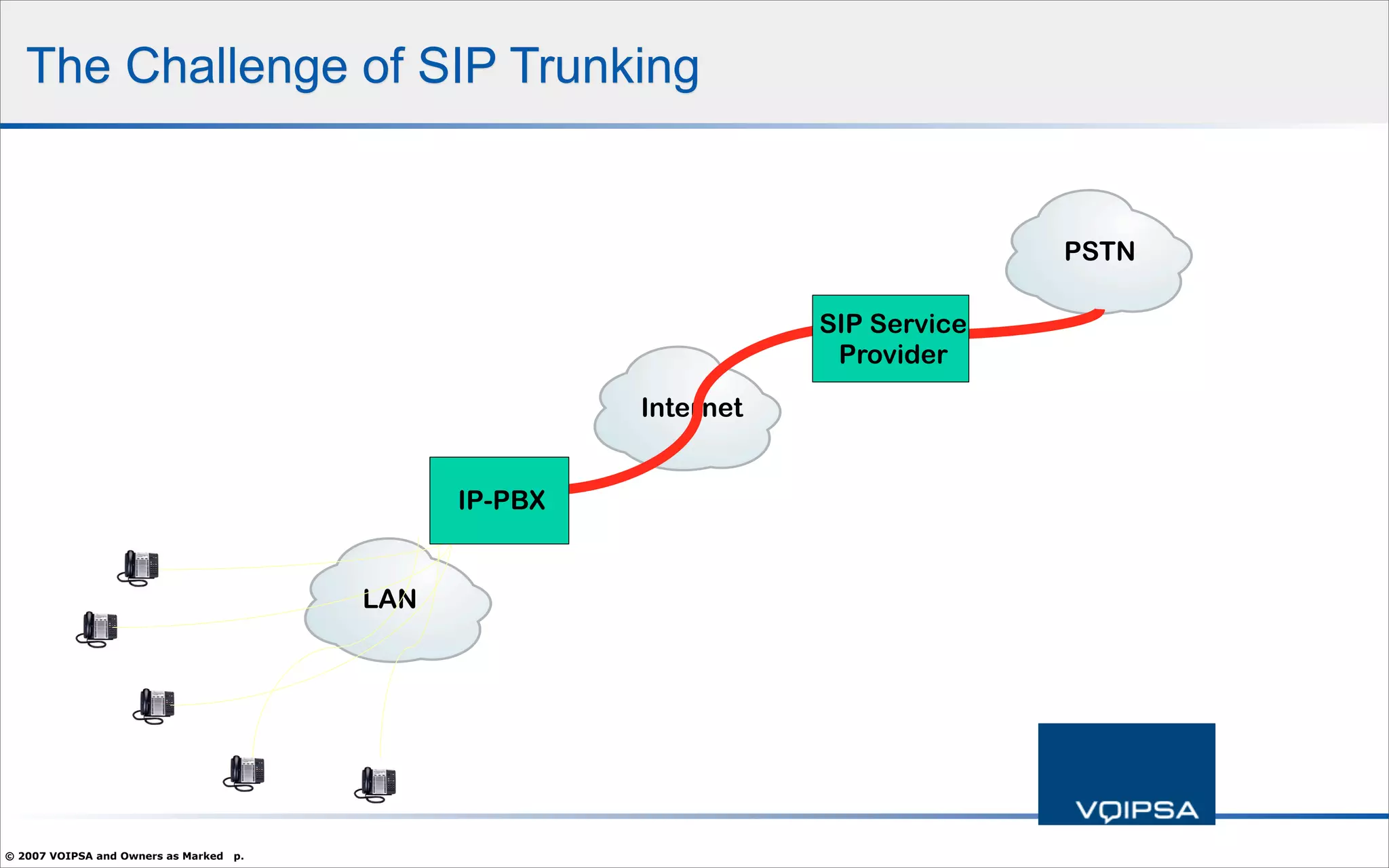


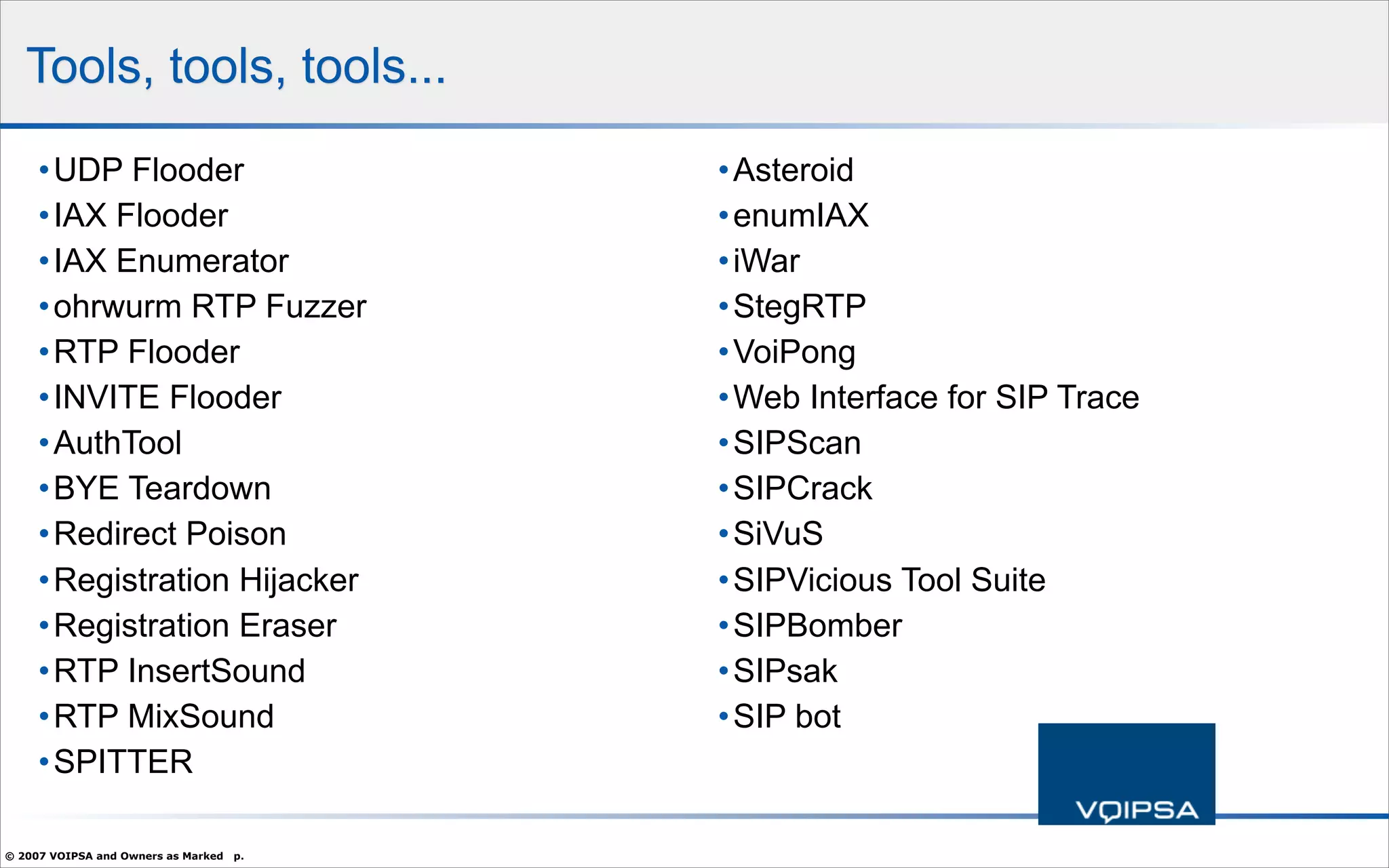







The document discusses the security concerns and complexities involved in Voice over IP (VoIP) systems, highlighting the differences between traditional telephony security and VoIP security requirements. It includes information on potential threats, industry best practices for mitigating risks, and resources available for VoIP security tools and research. Additionally, the author, Dan York, emphasizes the importance of ongoing collaboration among VoIP and security vendors to improve overall system integrity.































