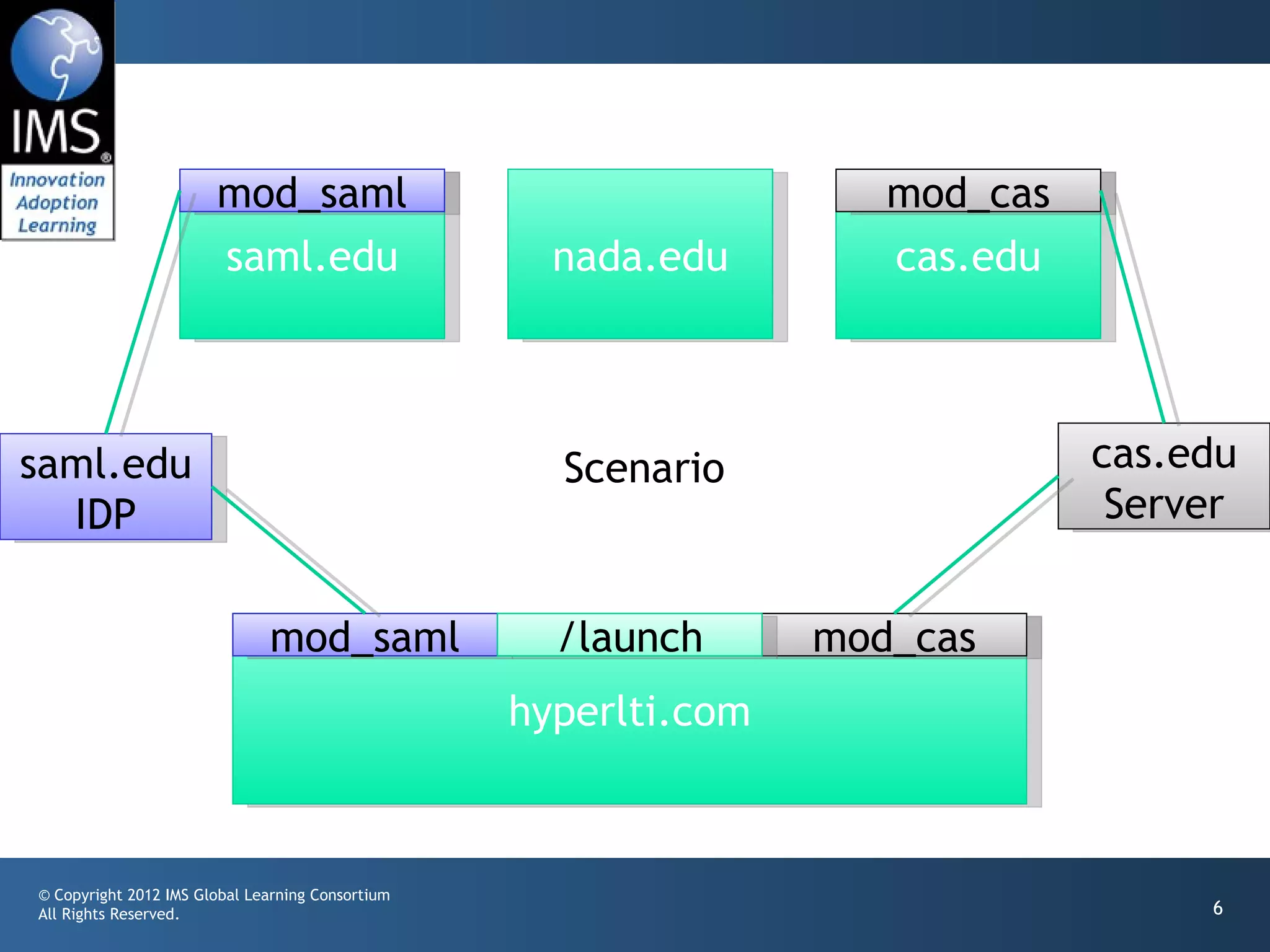
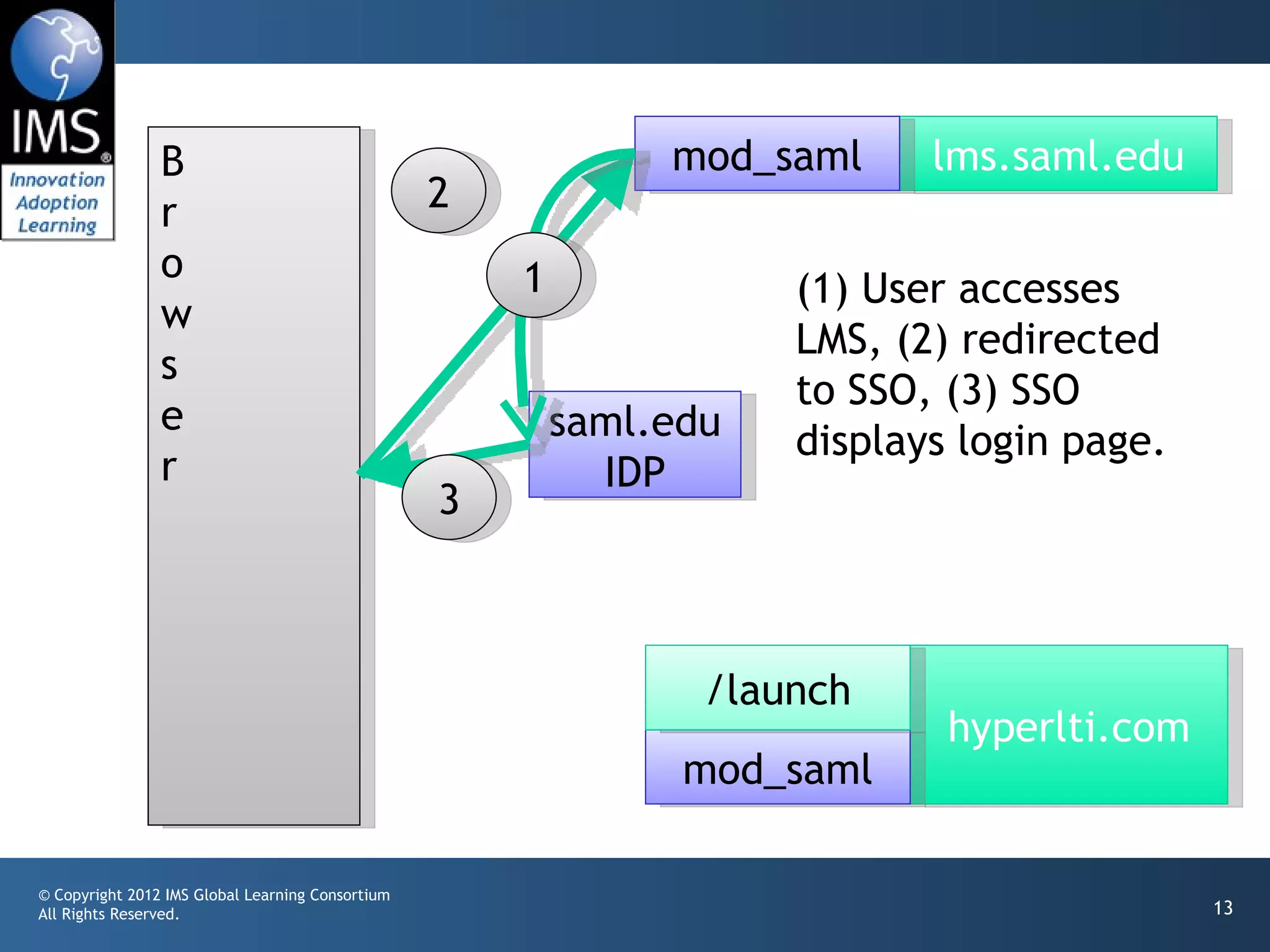
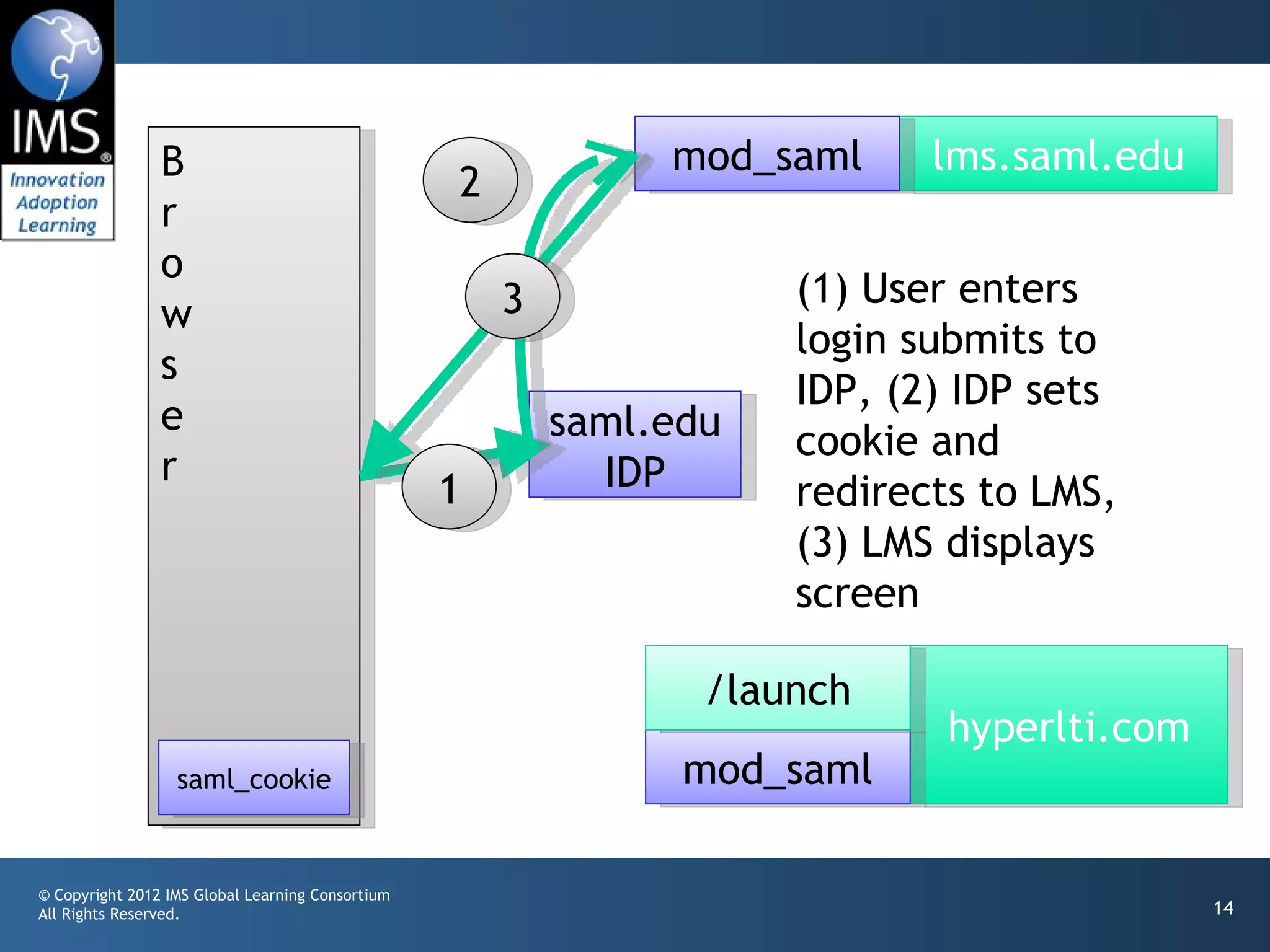
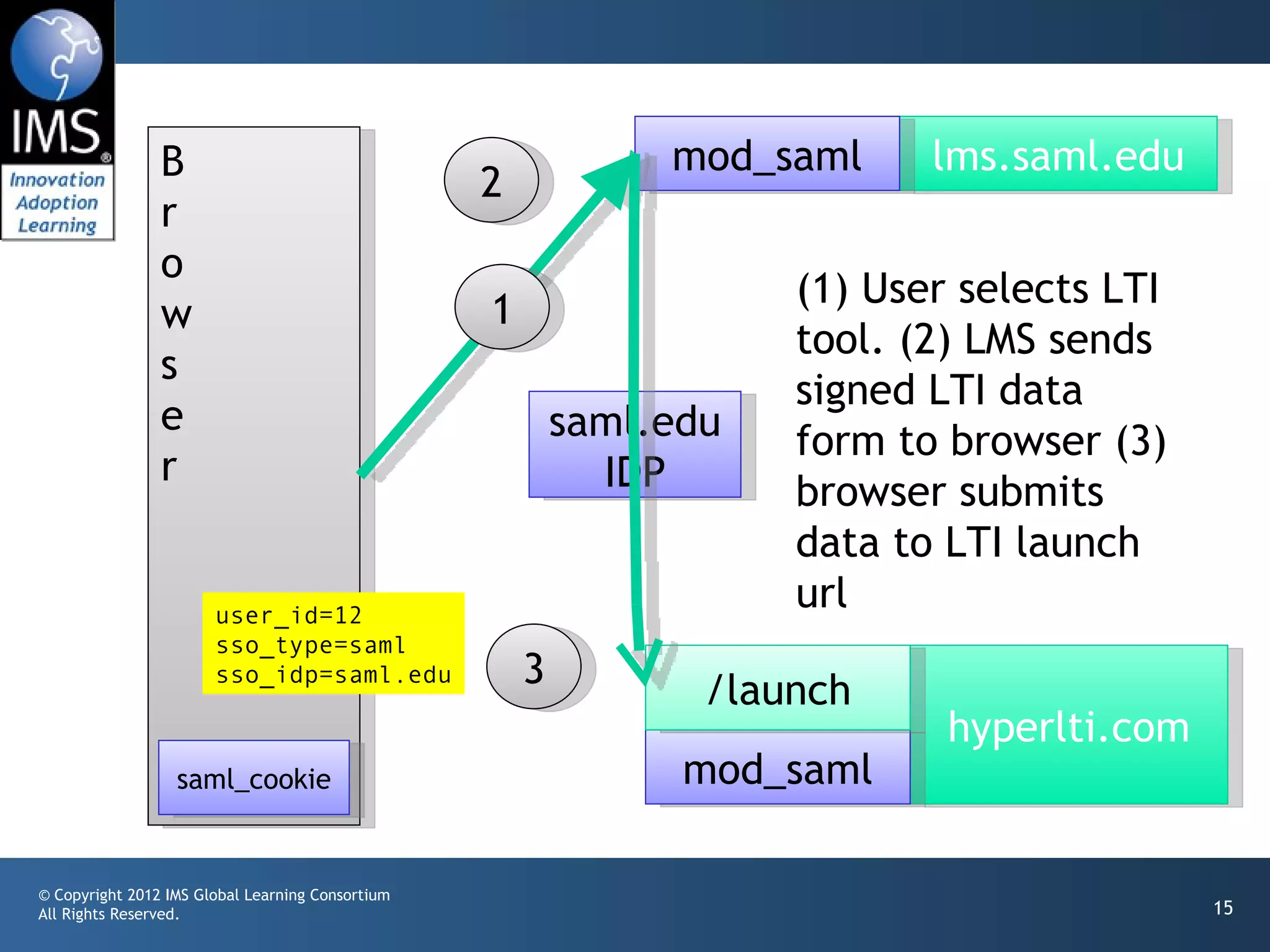
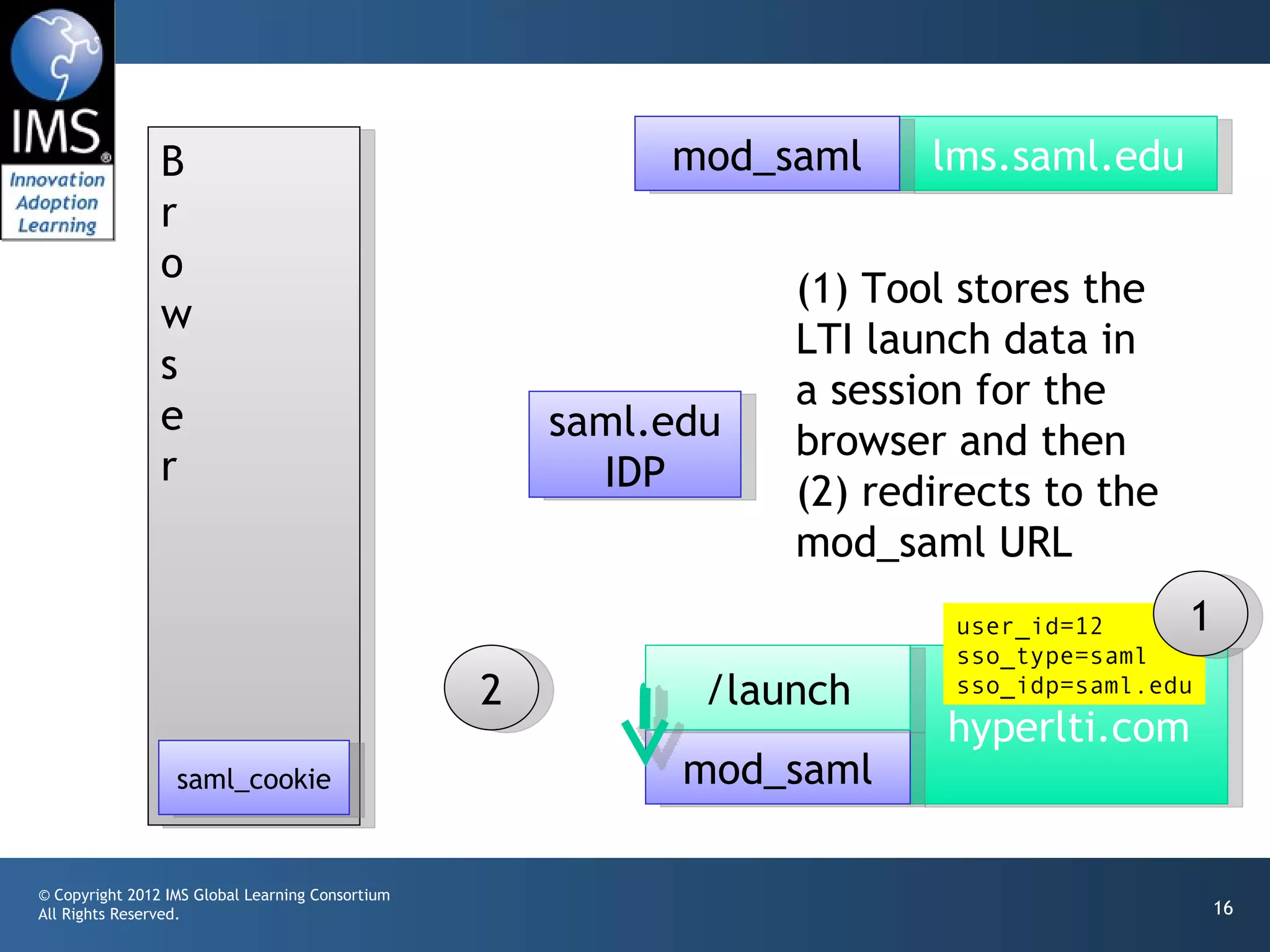
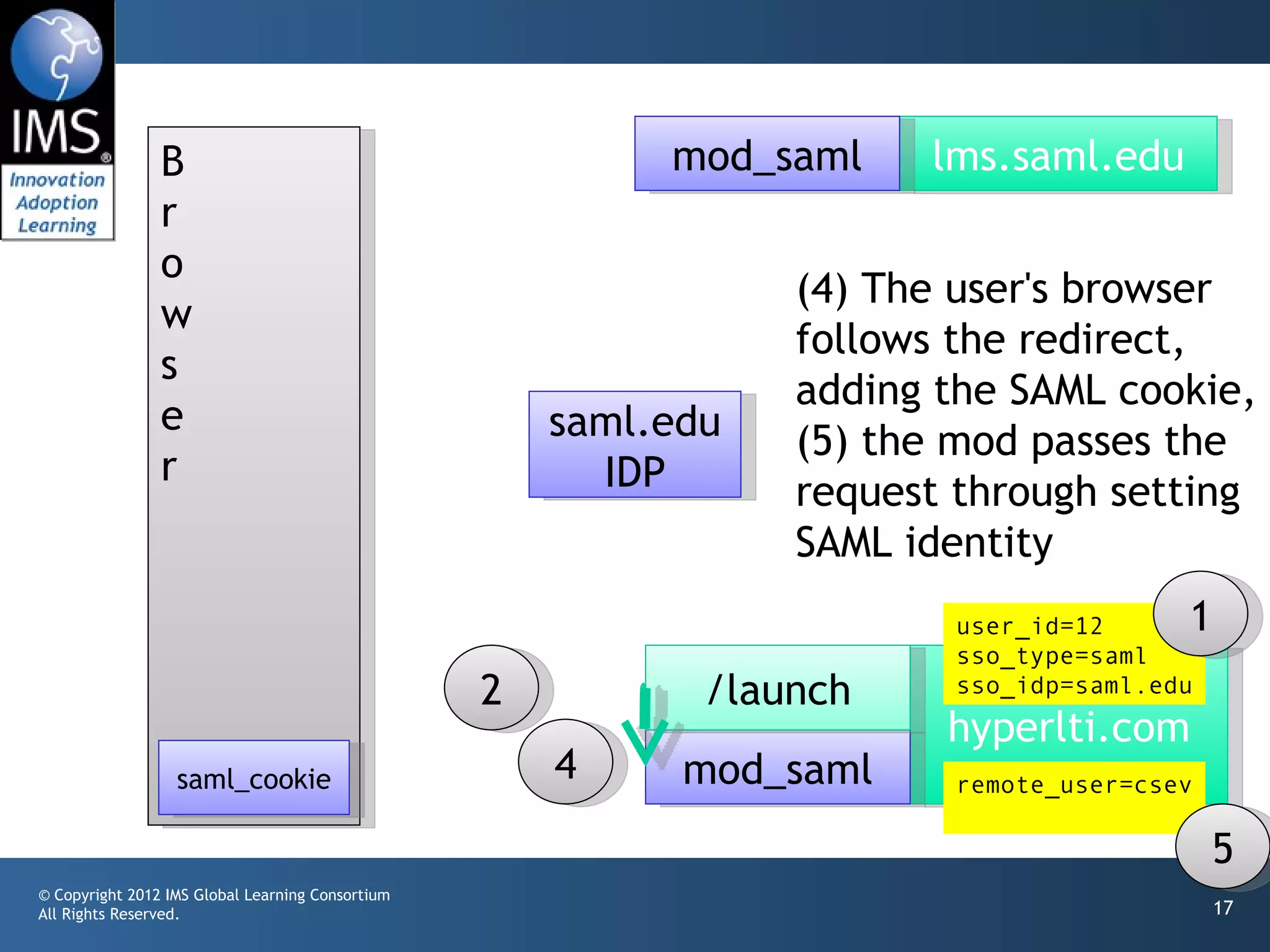
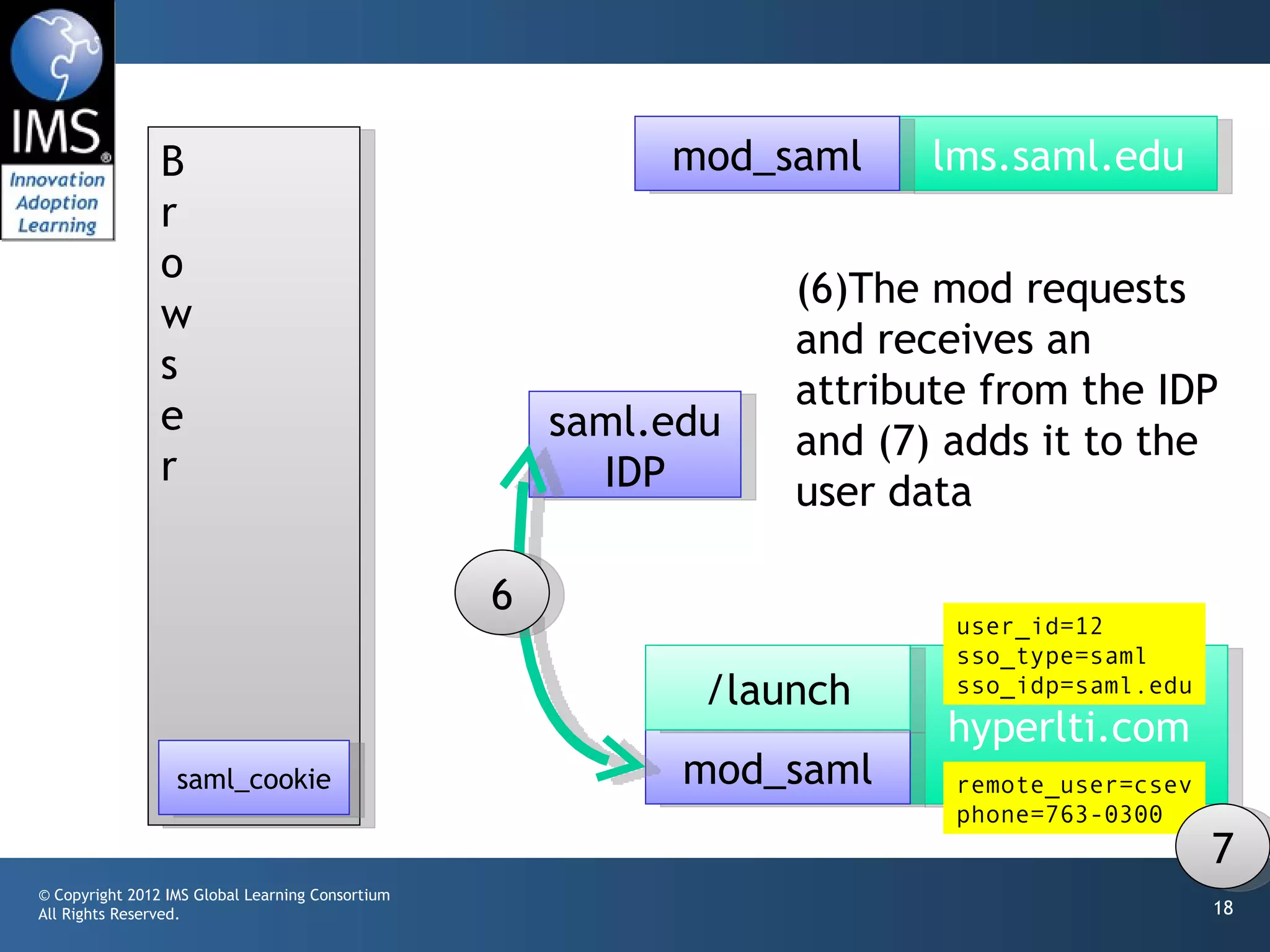
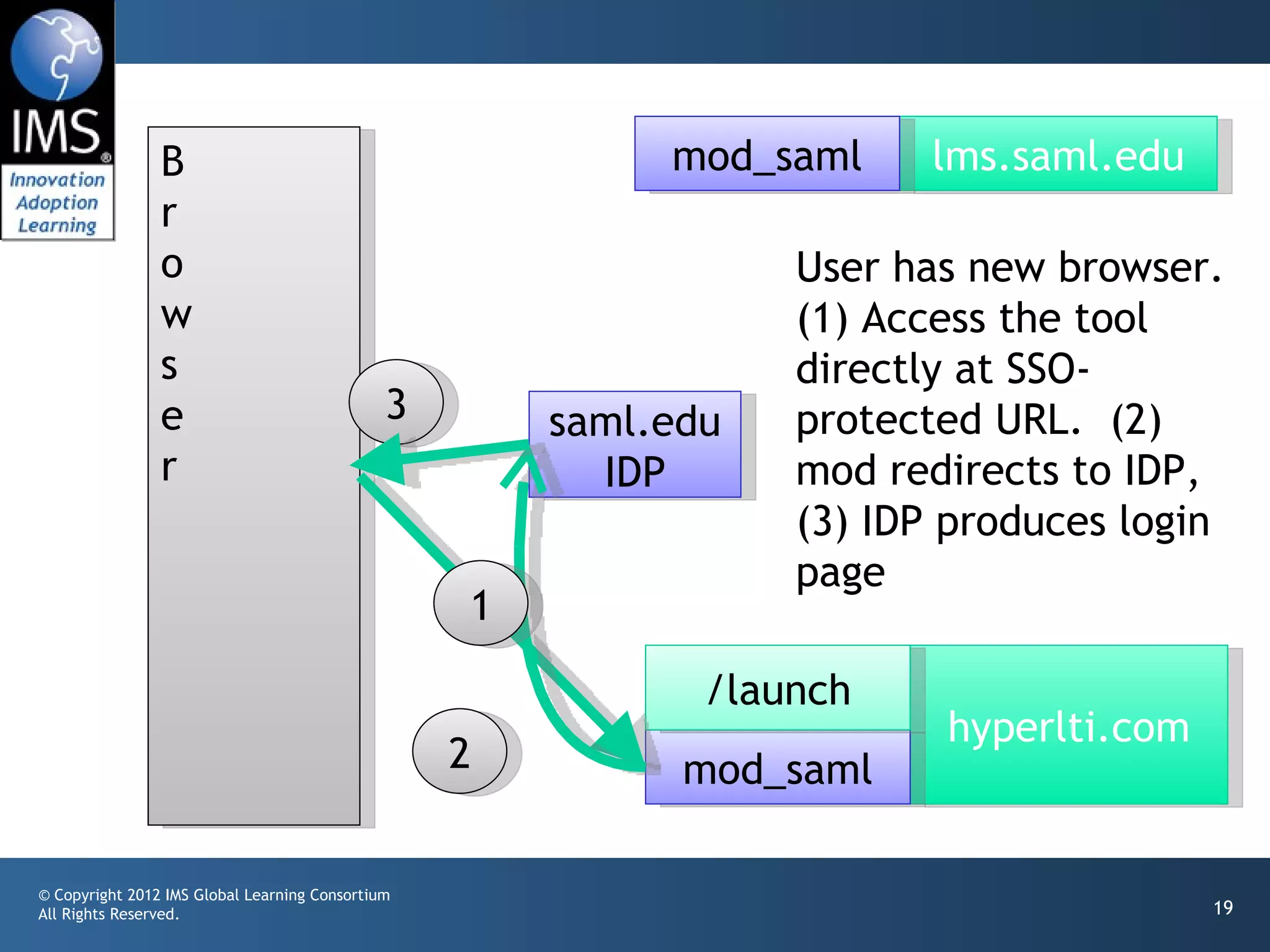
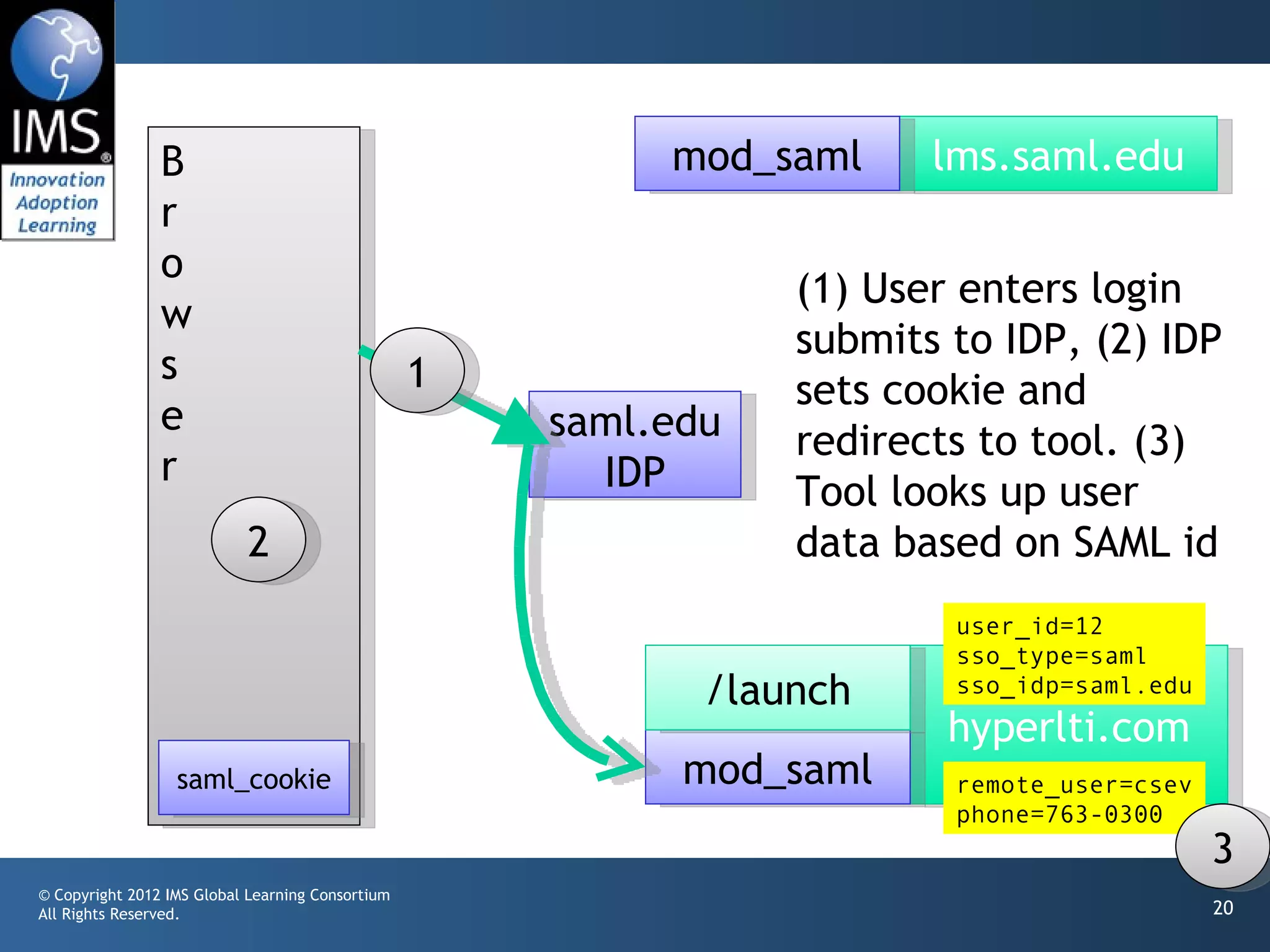
The document outlines a draft proposal for integrating IMS Learning Tools Interoperability (LTI) with Single Sign-On (SSO) using SAML, emphasizing the need to communicate user identities between Learning Management Systems (LMS) and external tools. It discusses the design concepts for LTI launch processes, ensuring that user identities are linked without directly forwarding SSO identities. The proposal aims to facilitate smoother user experiences across different SSO types and identity providers.