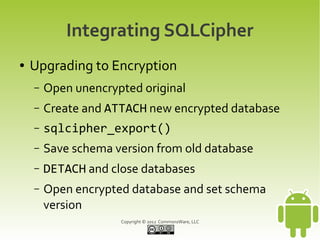
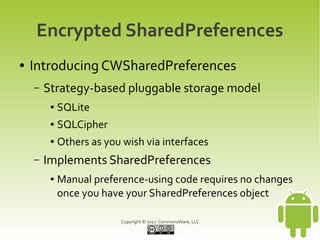
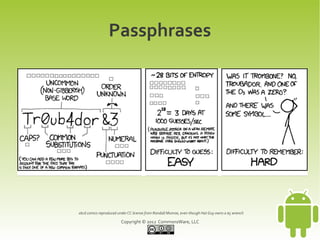
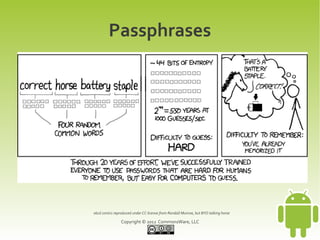
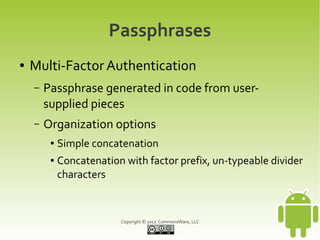
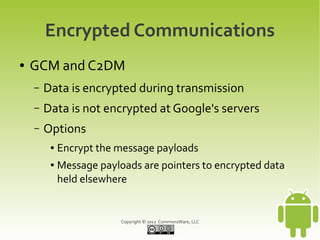
This document provides an overview and summary of a workshop on securing user data with SQLCipher. The workshop covers who is at risk of having their device data compromised, techniques for offense and defense including full-disk encryption and SQLCipher, hands-on exercises for integrating SQLCipher, and encrypting shared preferences, files, and communications. It also discusses strategies for passphrase entry and multi-factor authentication to improve security.