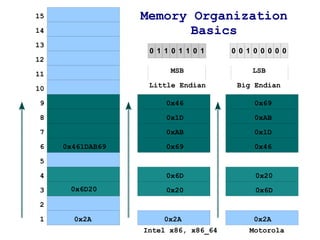
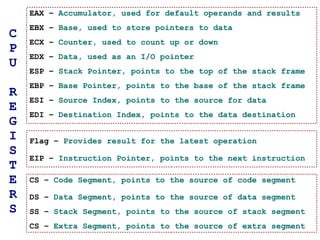
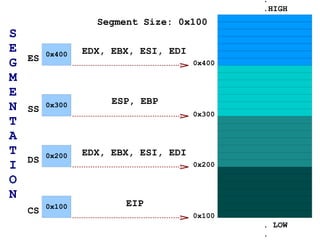
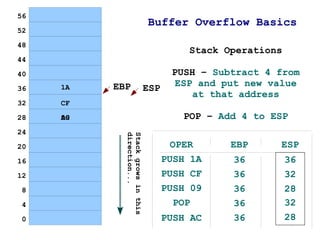
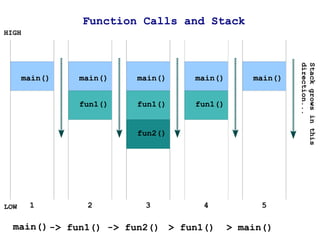
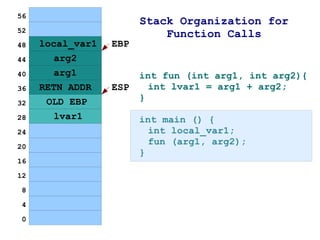
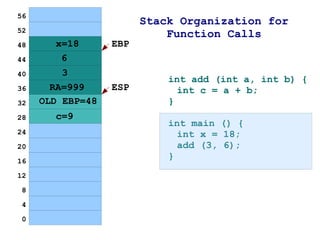
The document discusses memory organization and buffer overflow exploits. It explains how the CPU and memory are organized, and how data is represented in binary, octal, decimal, and hexadecimal numbering systems. It then covers buffer overflow basics like stack operations, function calls and stack organization, and provides an example of a buffer overflow exploit that overwrites the EIP register to change the program flow.


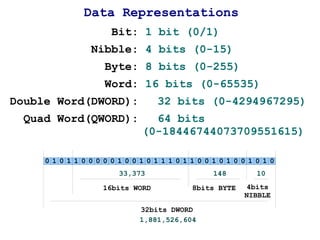
![220 Buffer Overflow Example
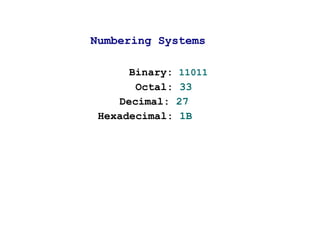
216
x=6
212
&argv[1]
208 int vuln (char *argv) {
RA=999 char buf[80];
204
OLD EBP=212 EBP int a = 9;
200
strcpy (buf, argv);
}
int main (int argc,
char **argv) {
int x = 6;
buf[80] vuln (argv[1]);
120
a=9 ESP }
116
112
108
104](https://image.slidesharecdn.com/emo-120410061935-phpapp01/85/Emo-Exploitation-13-320.jpg)
![220 Buffer Overflow Example
216
x=6 int vuln (char *argv) {
212
&argv[1] char buf[80];
208 int a = 9;
RA=999 strcpy (buf, argv);
204
OLD EBP=212 EBP }
200
AAAA
int main (int argc,
char **argv) {
... int x = 6;
vuln (argv[1]);
}
AAAA
120
a=9 ESP
116
112
python -c 'print “A”*80'
108
104](https://image.slidesharecdn.com/emo-120410061935-phpapp01/85/Emo-Exploitation-14-320.jpg)
![220 Buffer Overflow Example
216
x=6 int vuln (char *argv) {
212
&argv[1] char buf[80];
208 int a = 9;
RA=999 strcpy (buf, argv);
204
AAAA EBP }
200
AAAA
int main (int argc,
char **argv) {
... int x = 6;
vuln (argv[1]);
}
AAAA
120
a=9 ESP
116
112
python -c 'print “A”*84'
108
104](https://image.slidesharecdn.com/emo-120410061935-phpapp01/85/Emo-Exploitation-15-320.jpg)
![220 Buffer Overflow Example
216
x=6 int vuln (char *argv) {
212
&argv[1] char buf[80];
208 int a = 9;
AAAA strcpy (buf, argv);
204
AAAA EBP }
200
AAAA
int main (int argc,
char **argv) {
... int x = 6;
vuln (argv[1]);
}
AAAA
120
a=9 ESP
116
112
python -c 'print “A”*88'
108
104](https://image.slidesharecdn.com/emo-120410061935-phpapp01/85/Emo-Exploitation-16-320.jpg)

![220 EIP 220
216 41414141 216
x=6 SIGSEGV x=6
212 212
&argv[1] &argv[1]
208 208
41414141 RTN ADDR 00000120
204 204
41414141 90909090
200 EBP 200
41414141 6851C931
D0FF77C2
... 93C7B854
90909090
41414141 90909090
120 ESP 120
a=9 a=9
116 116
112 EIP 112
108 00000120 108
104
GAME OVER! 104](https://image.slidesharecdn.com/emo-120410061935-phpapp01/85/Emo-Exploitation-18-320.jpg)