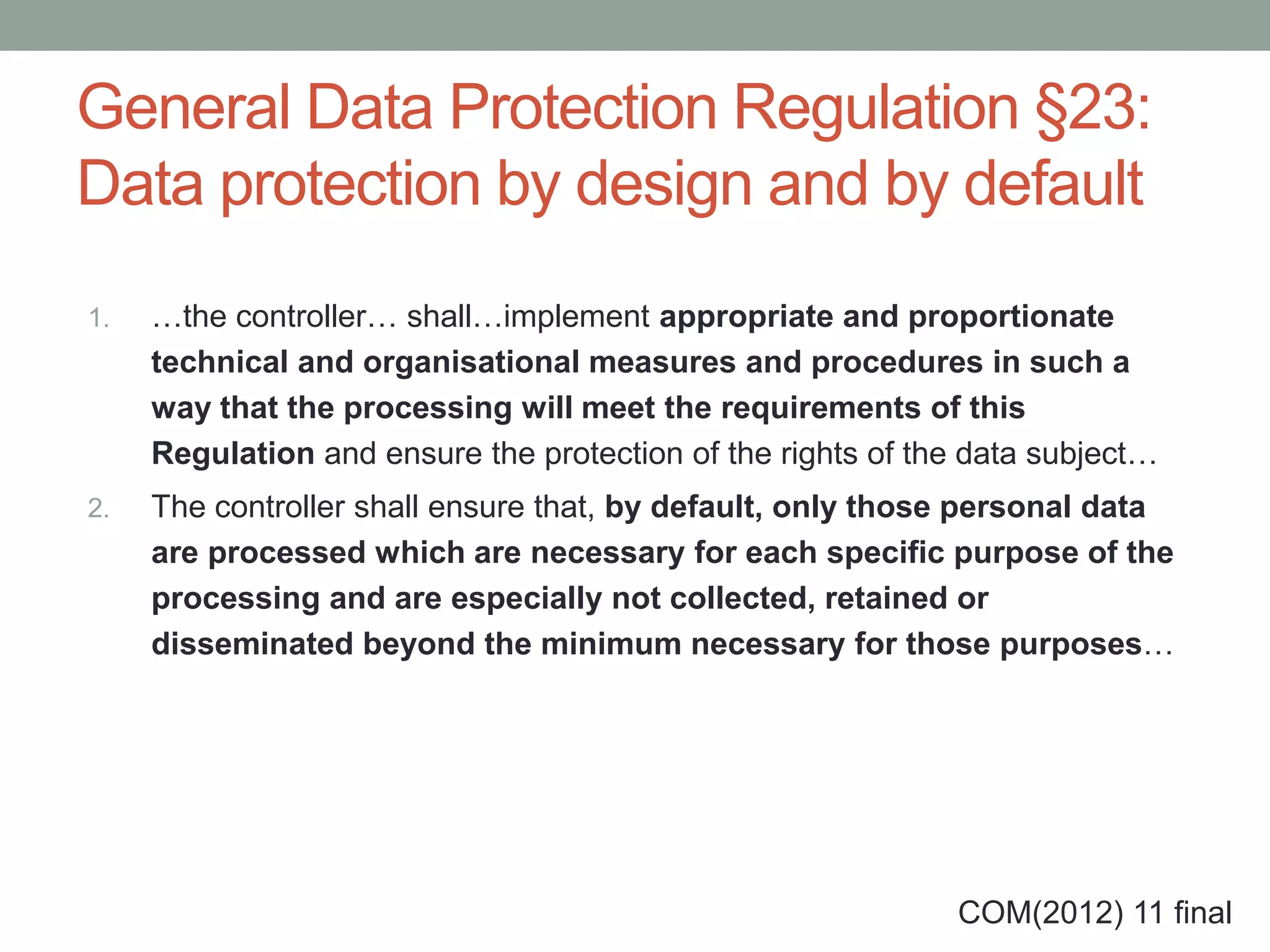
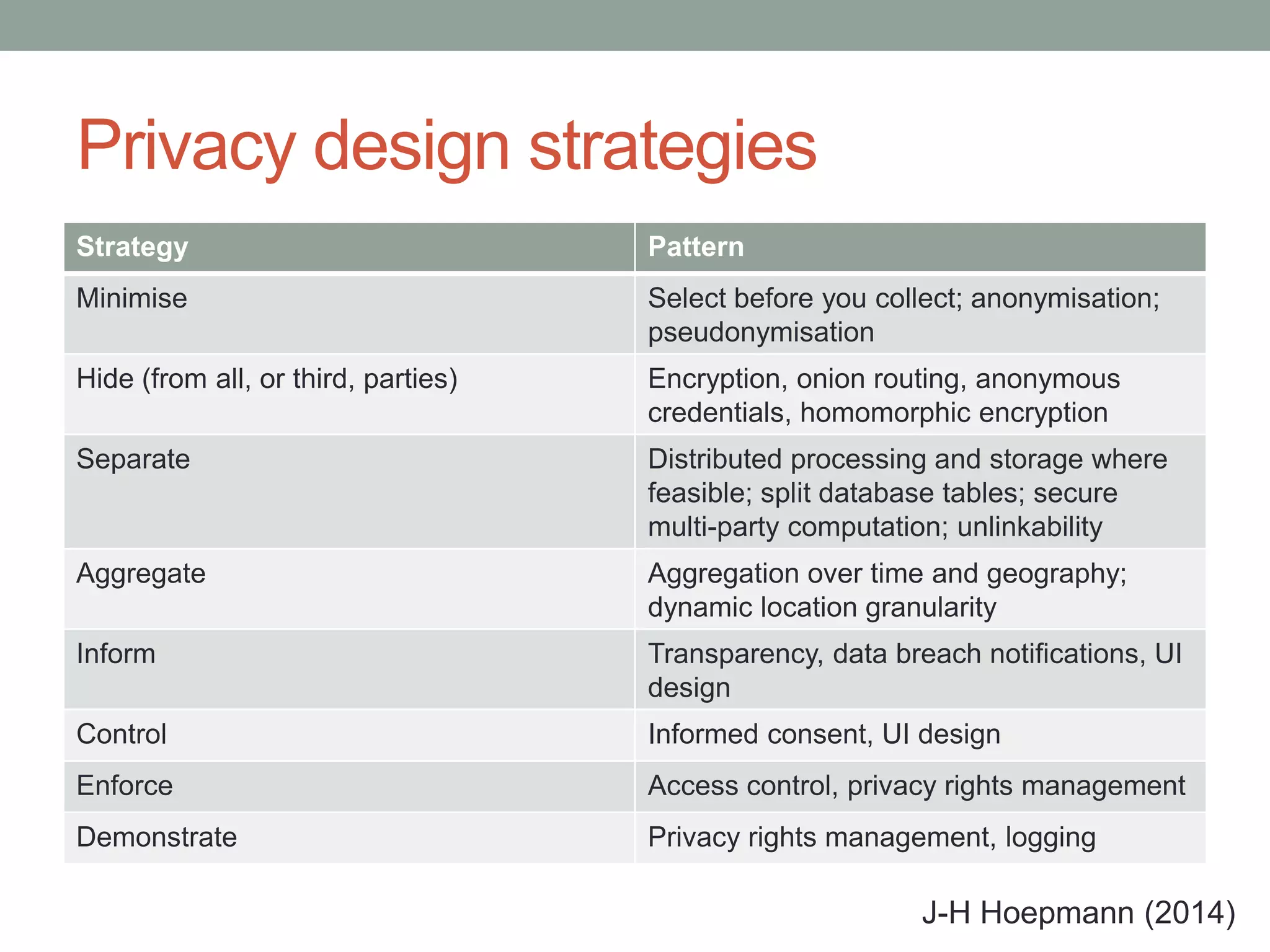
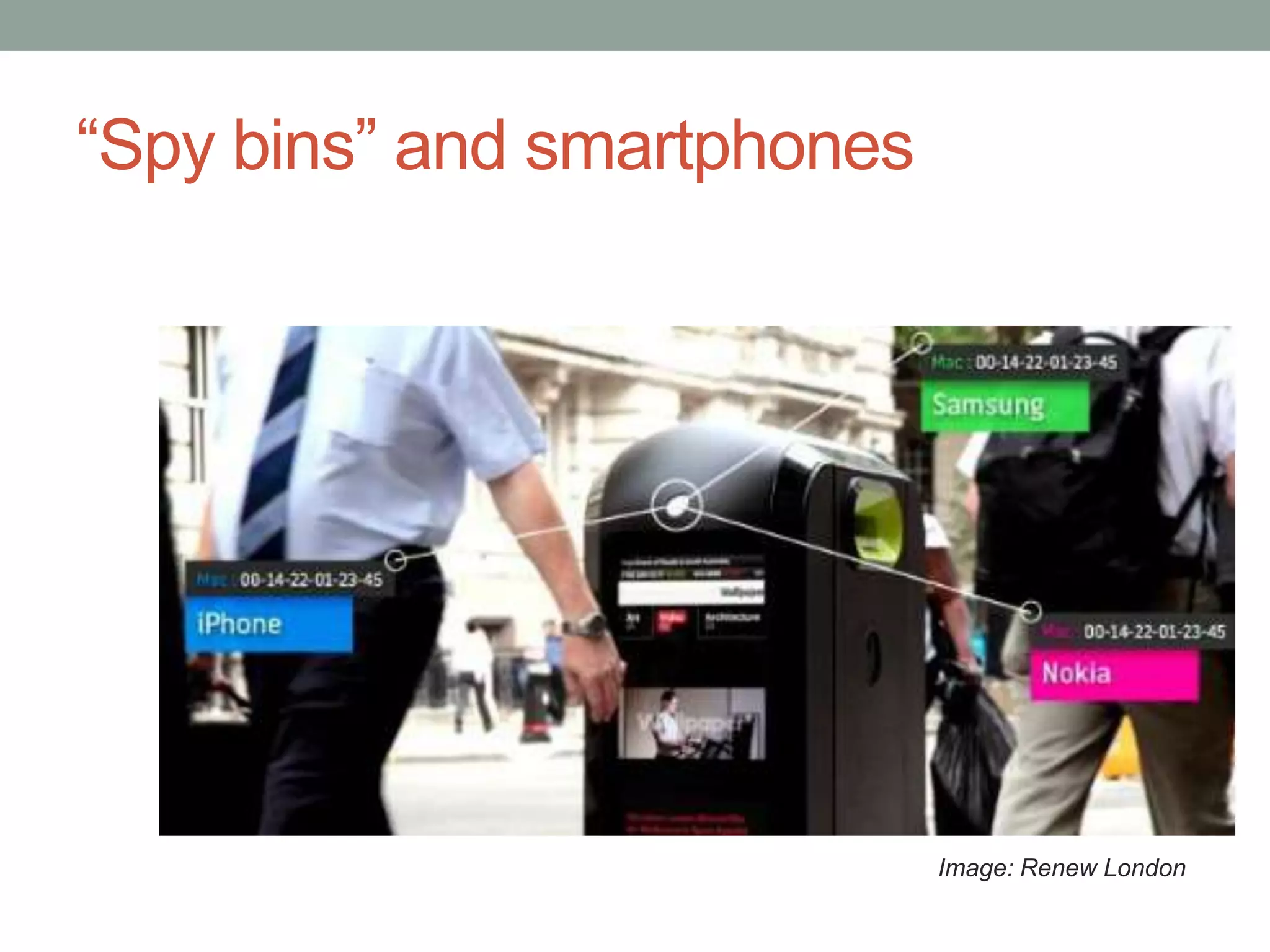
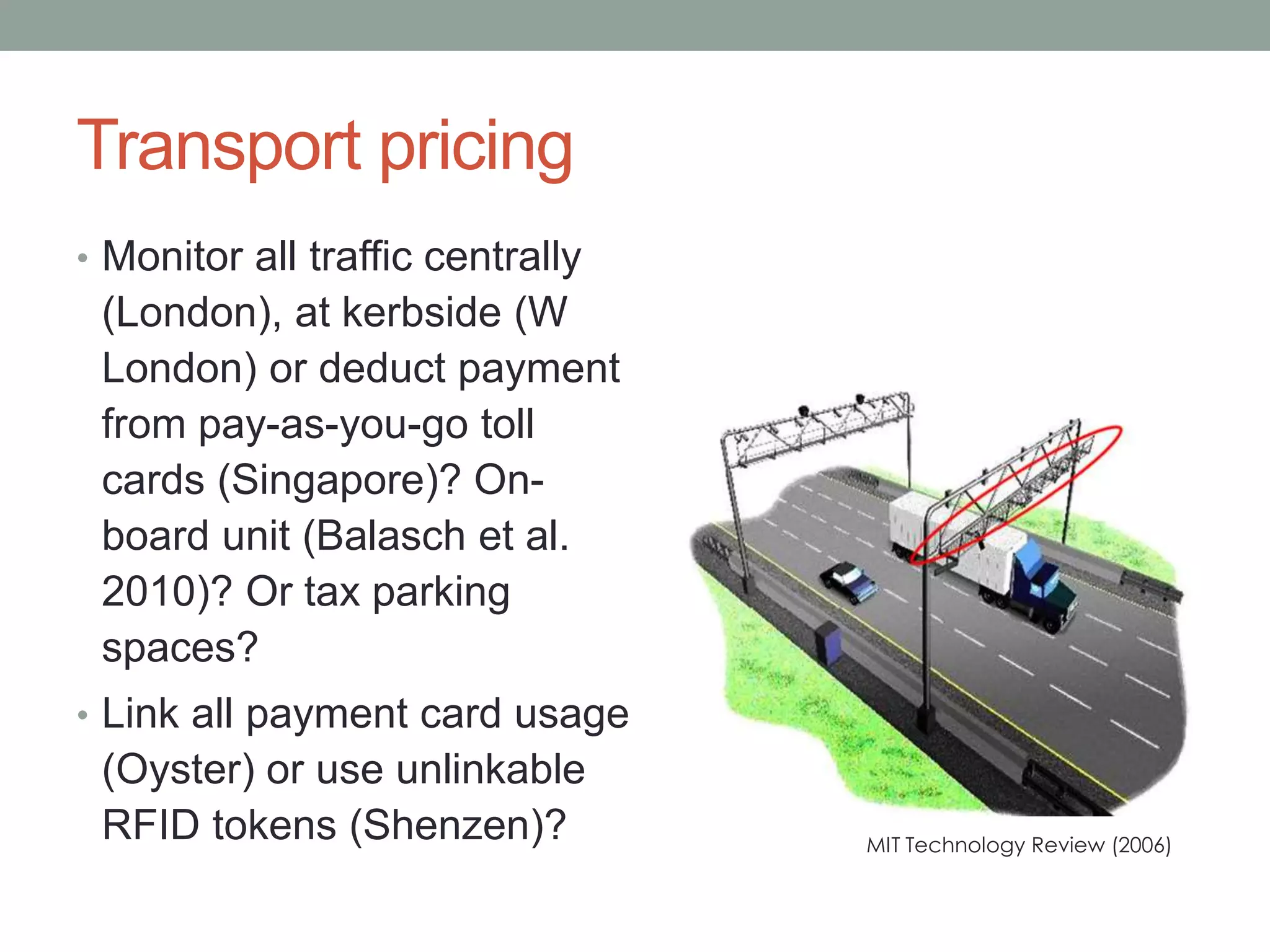
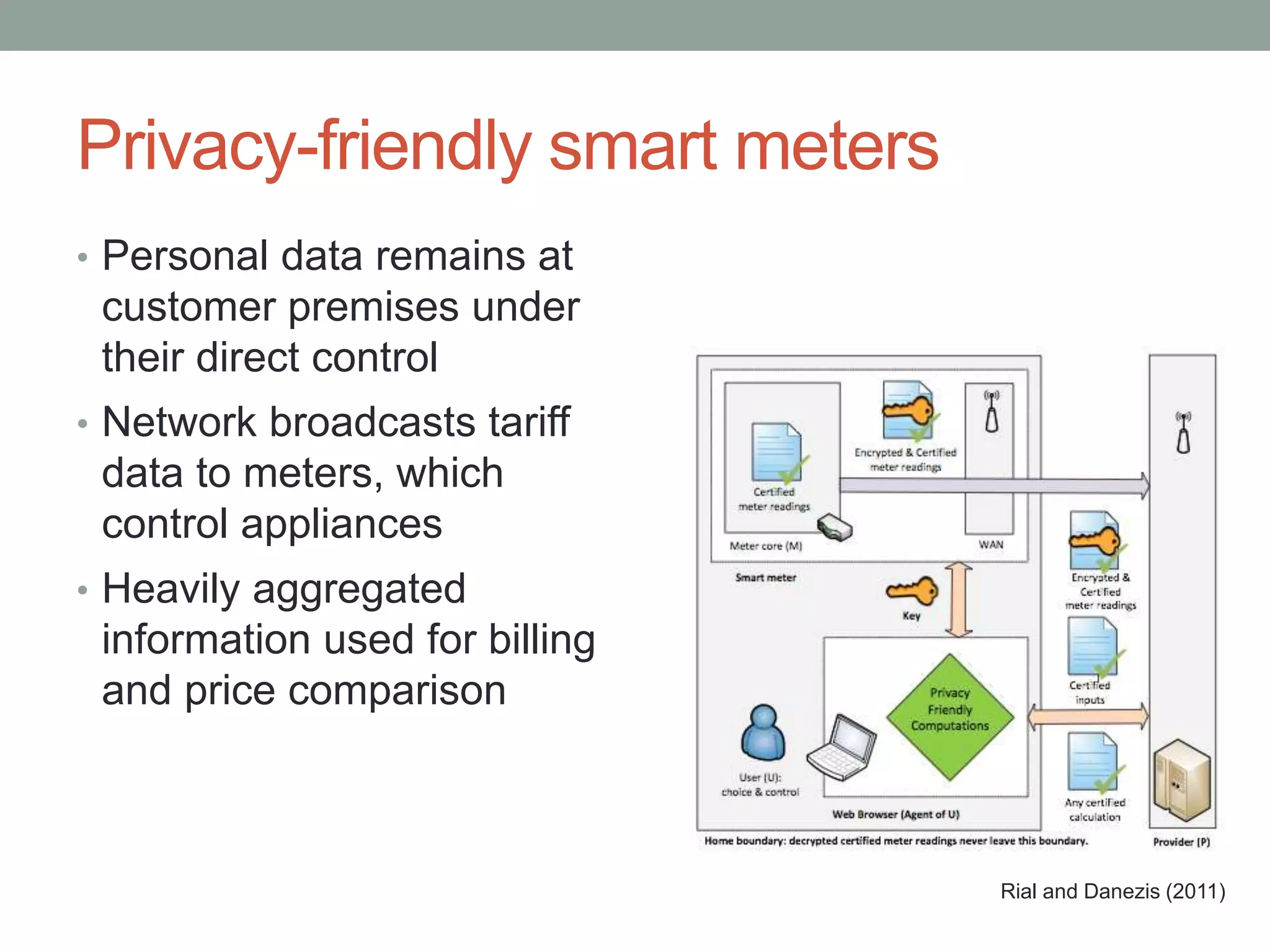
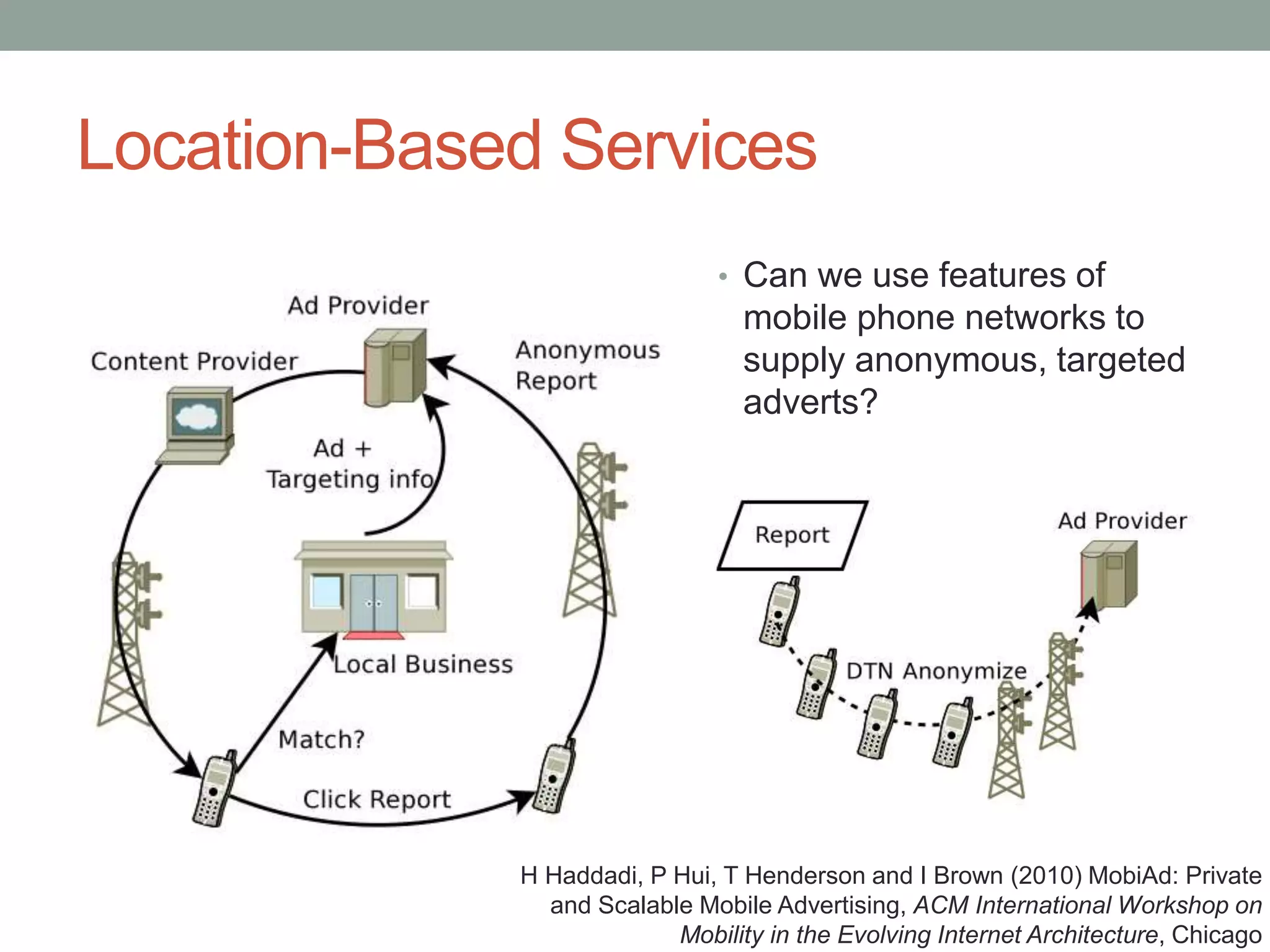
The document outlines the principles of 'Privacy by Design,' emphasizing proactive measures and user-centric approaches in data protection. It discusses foundational guidelines for implementing privacy in organizational practices, as well as the role of data protection regulations and privacy rights. Additionally, it addresses strategies for ensuring privacy in various technologies and highlights challenges and limitations in achieving effective privacy protections.