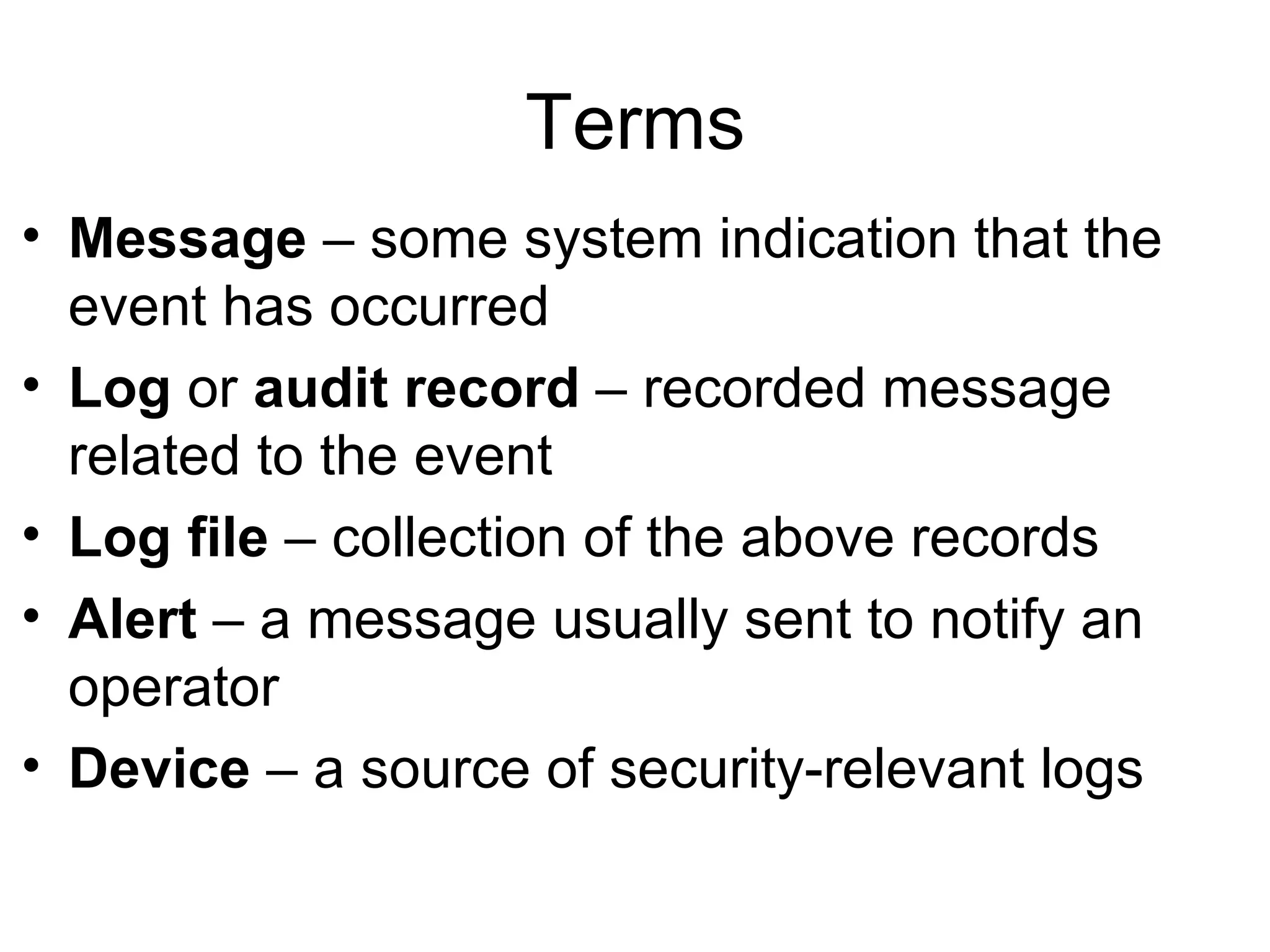
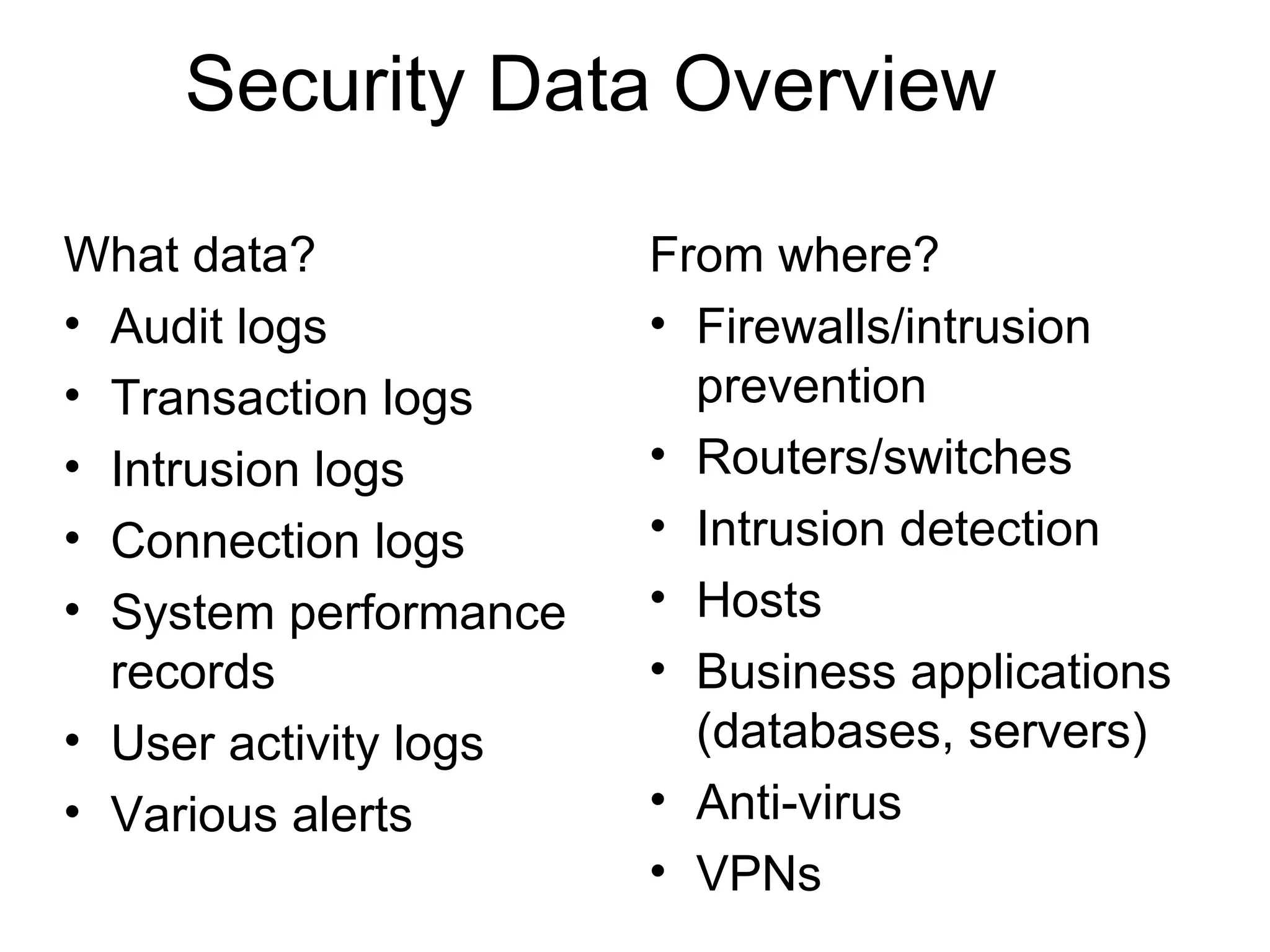
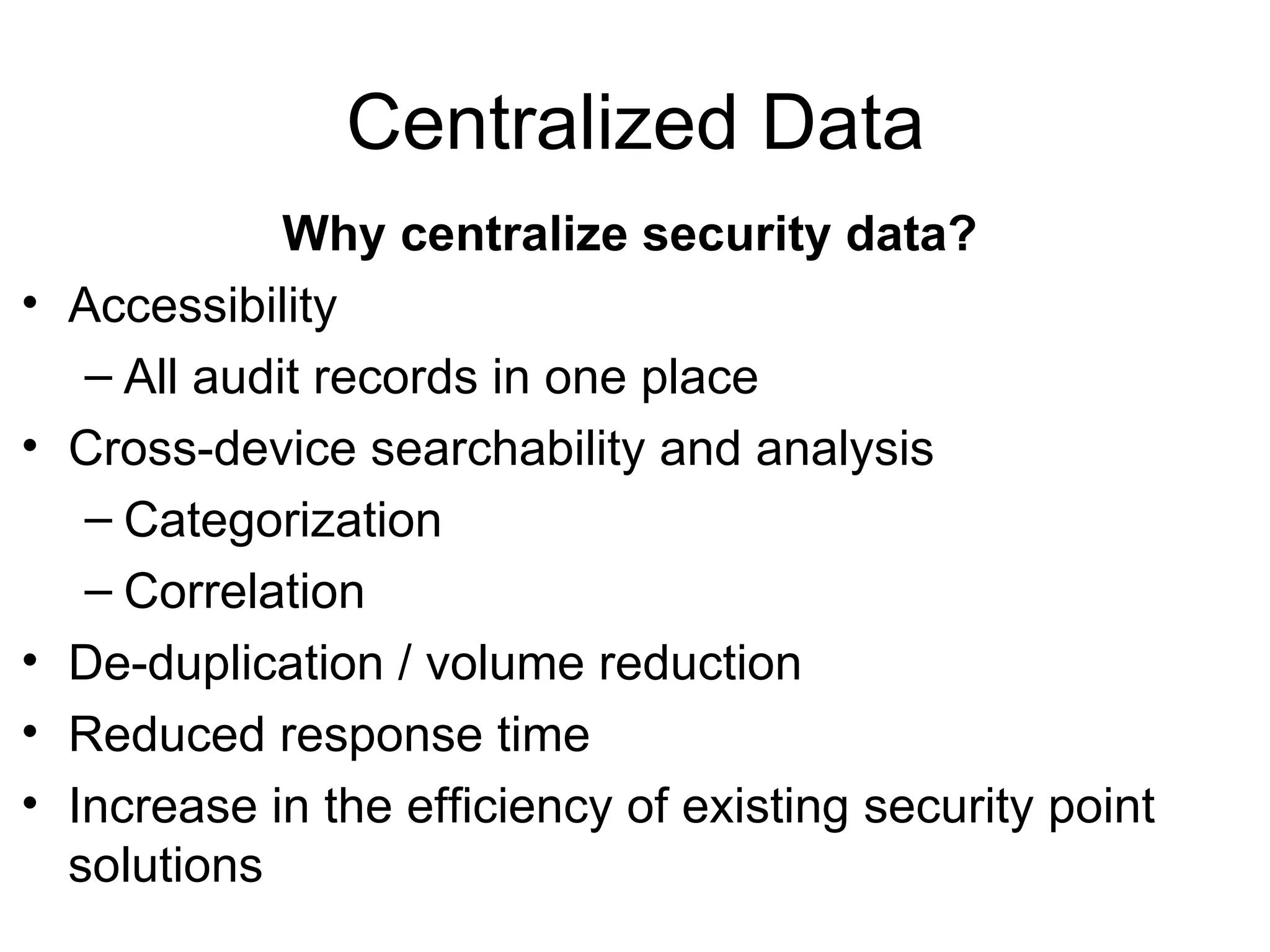
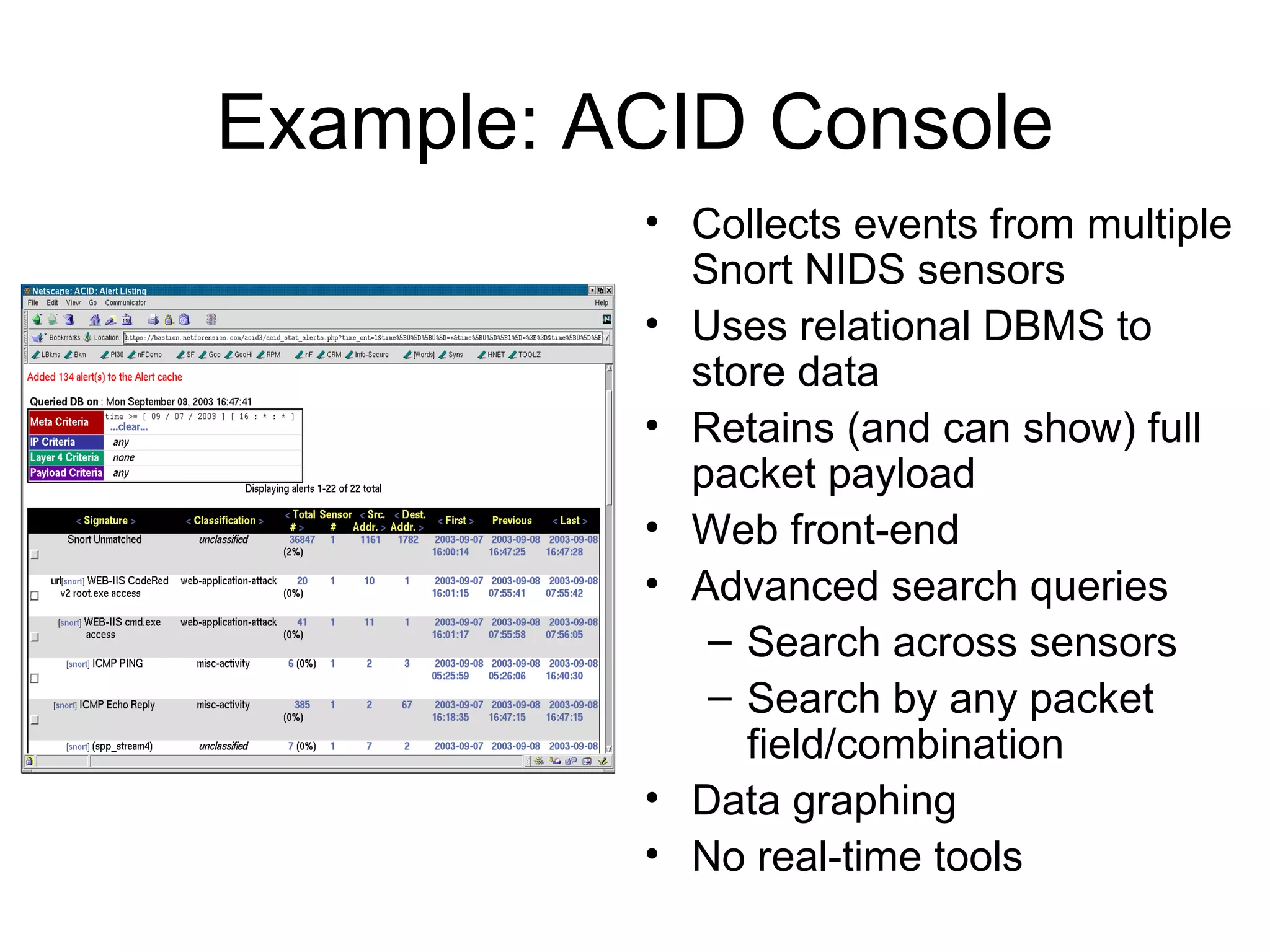
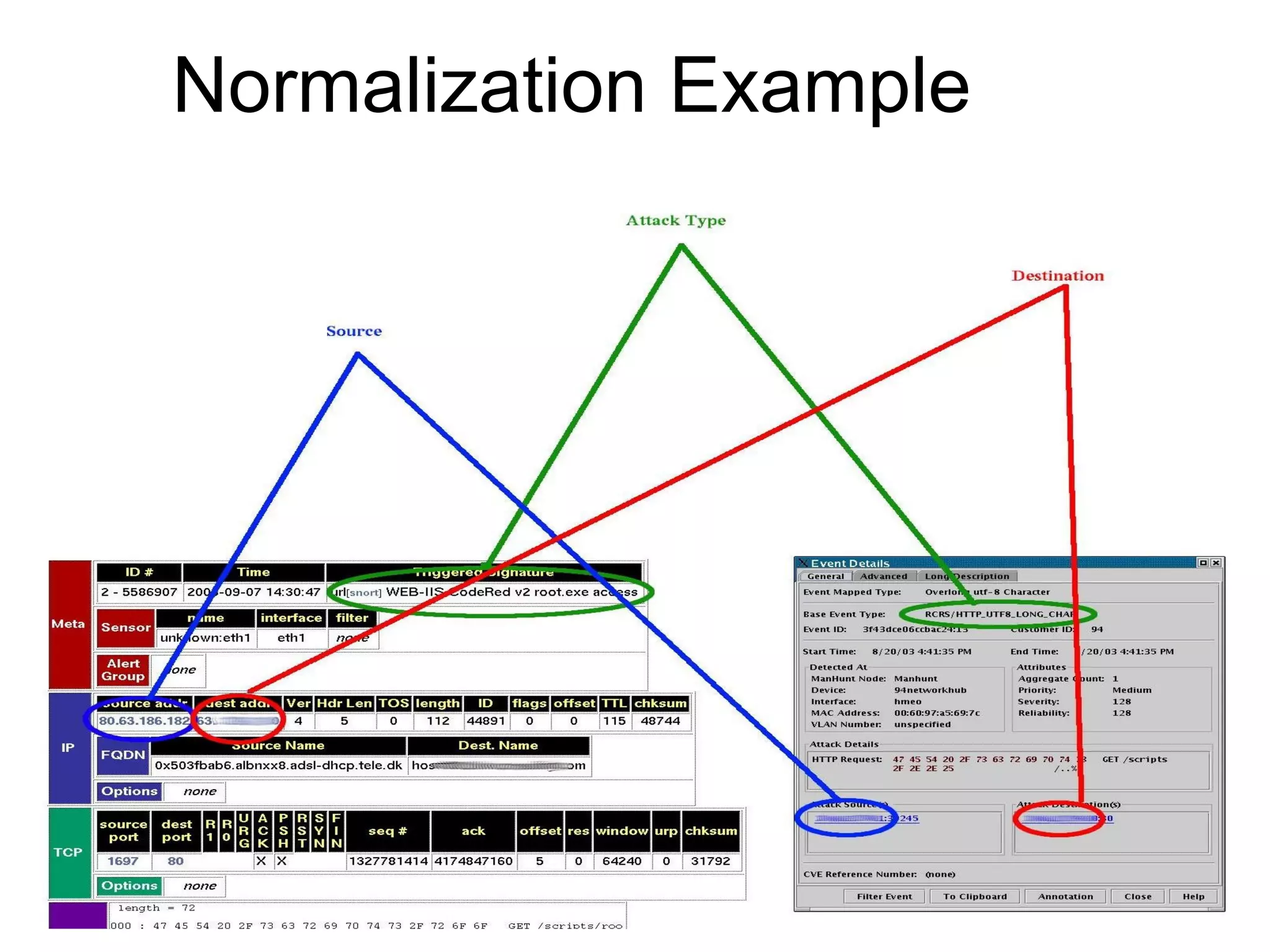
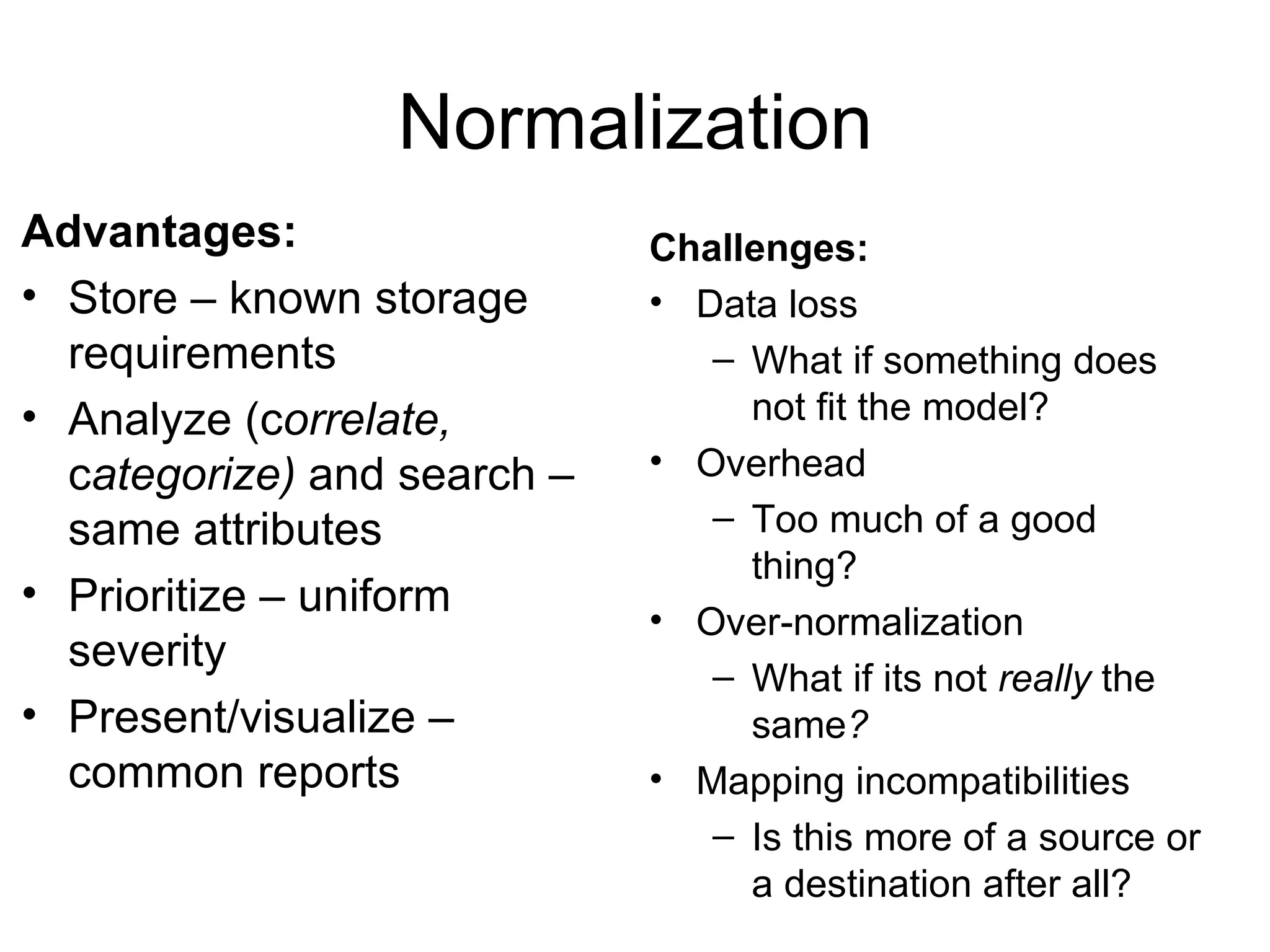
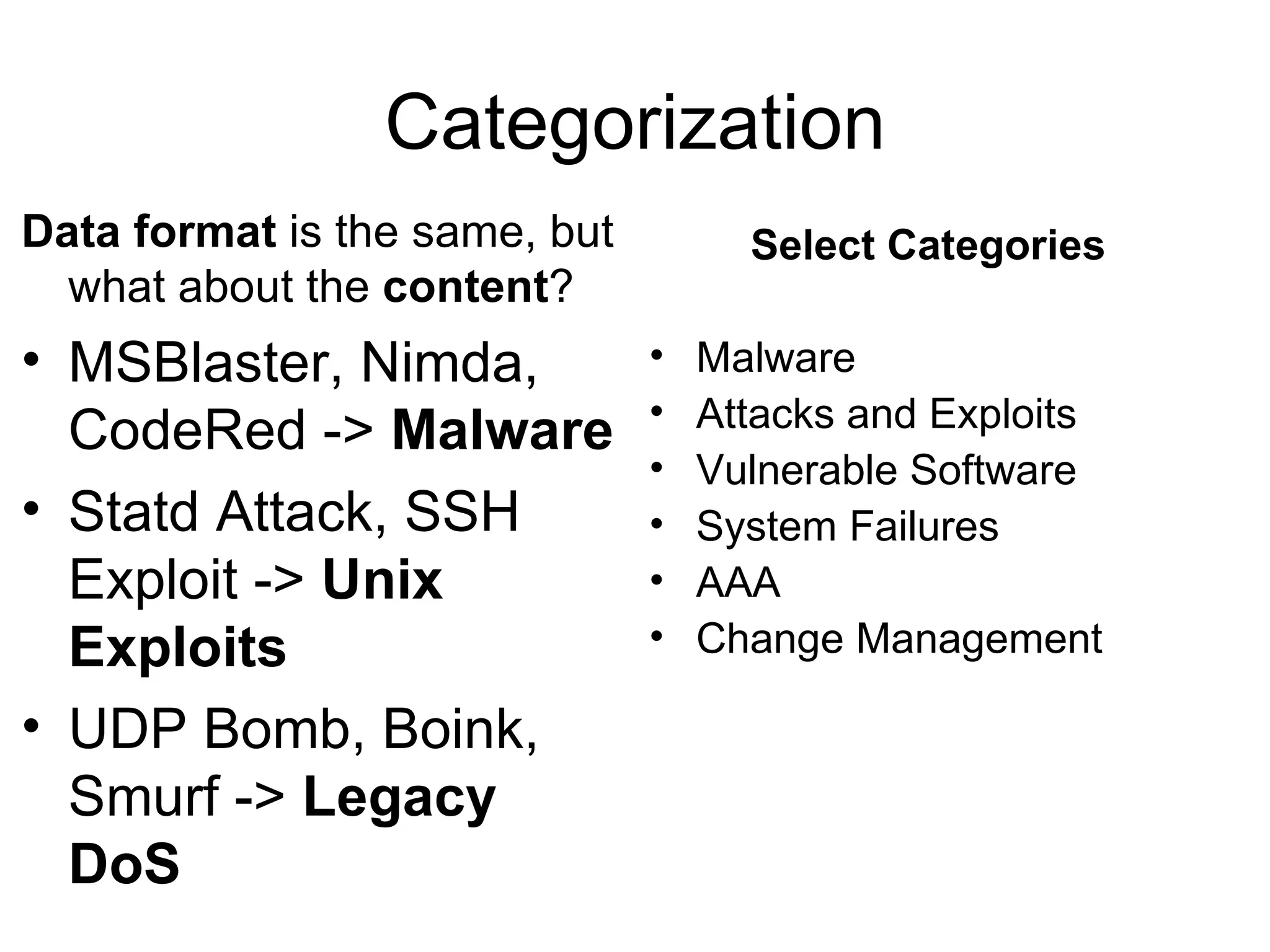
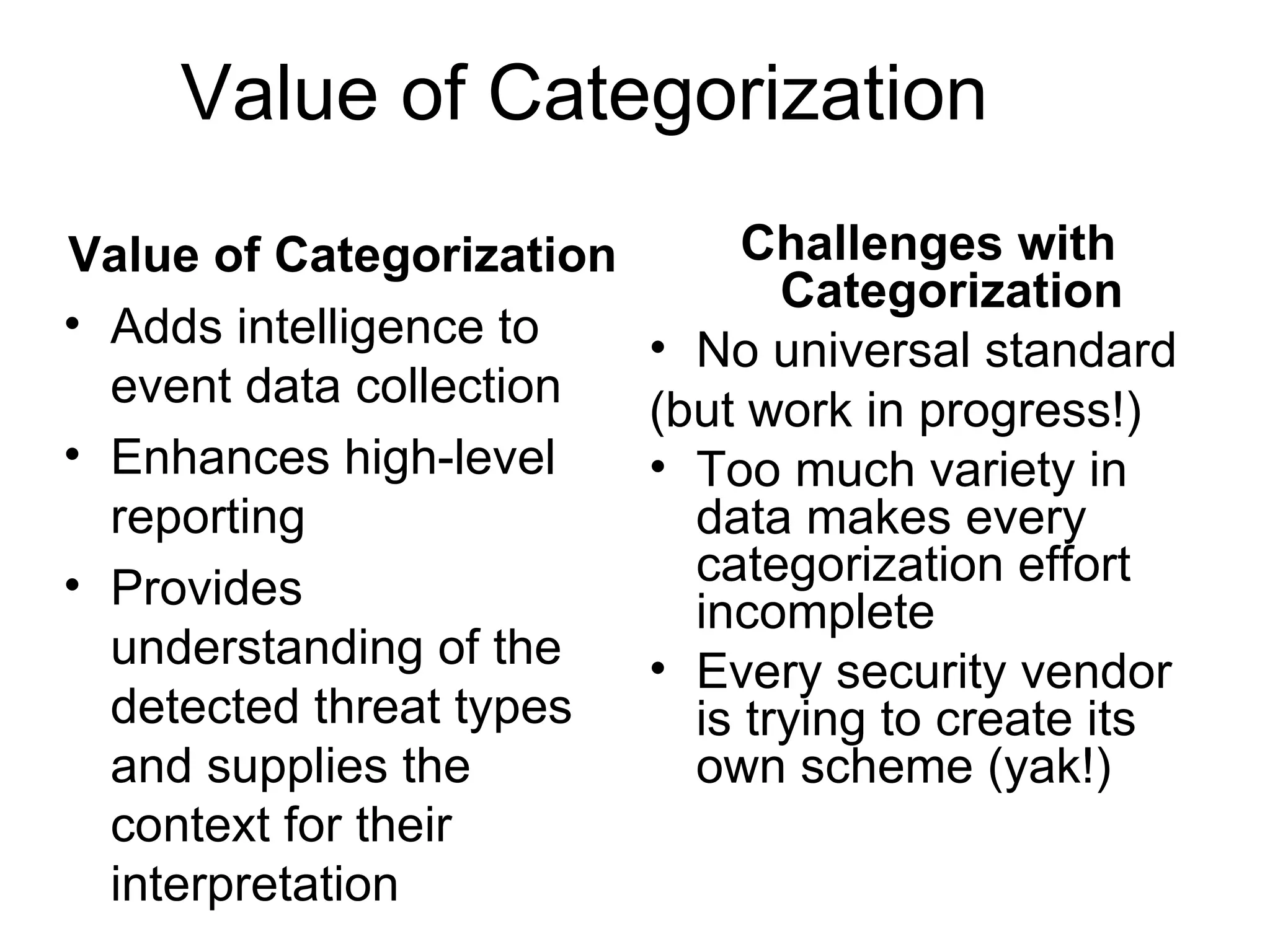
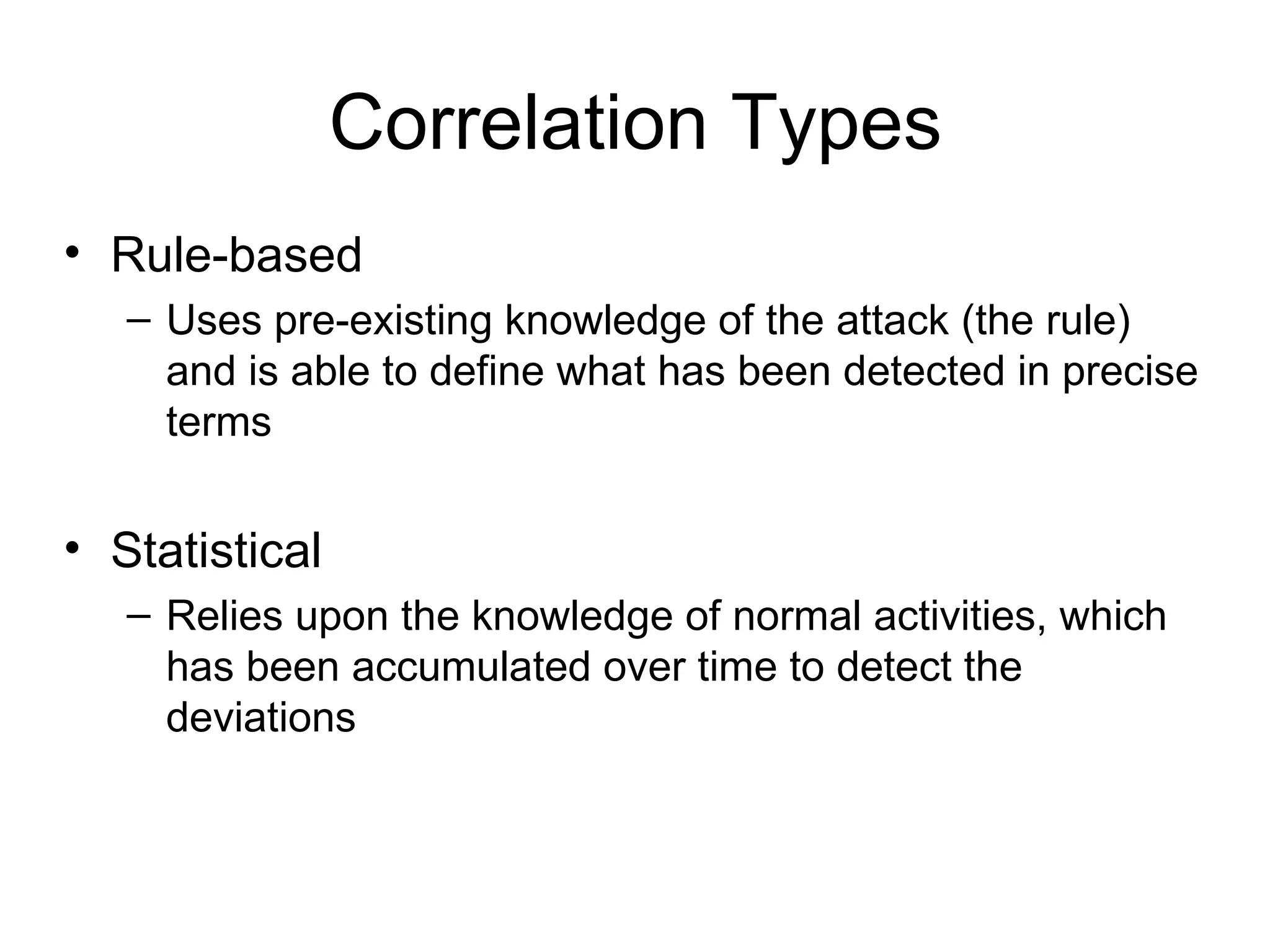
Centralizing security data provides several benefits such as easier management, auditing, and analysis across devices. It allows access to all audit records in one place, cross-device search and correlation, categorization of event types, and reduced response time. To centralize data, organizations need to collect, normalize, transport securely, process, store, and report on data from various sources like firewalls, intrusion detection systems, and applications. Challenges include dealing with large volumes of diverse data formats and ensuring chain of custody of the data. Normalization converts data to a common format to facilitate storage, analysis, search, and reporting. Correlation establishes relationships between events to improve threat identification by looking at sets of related events.