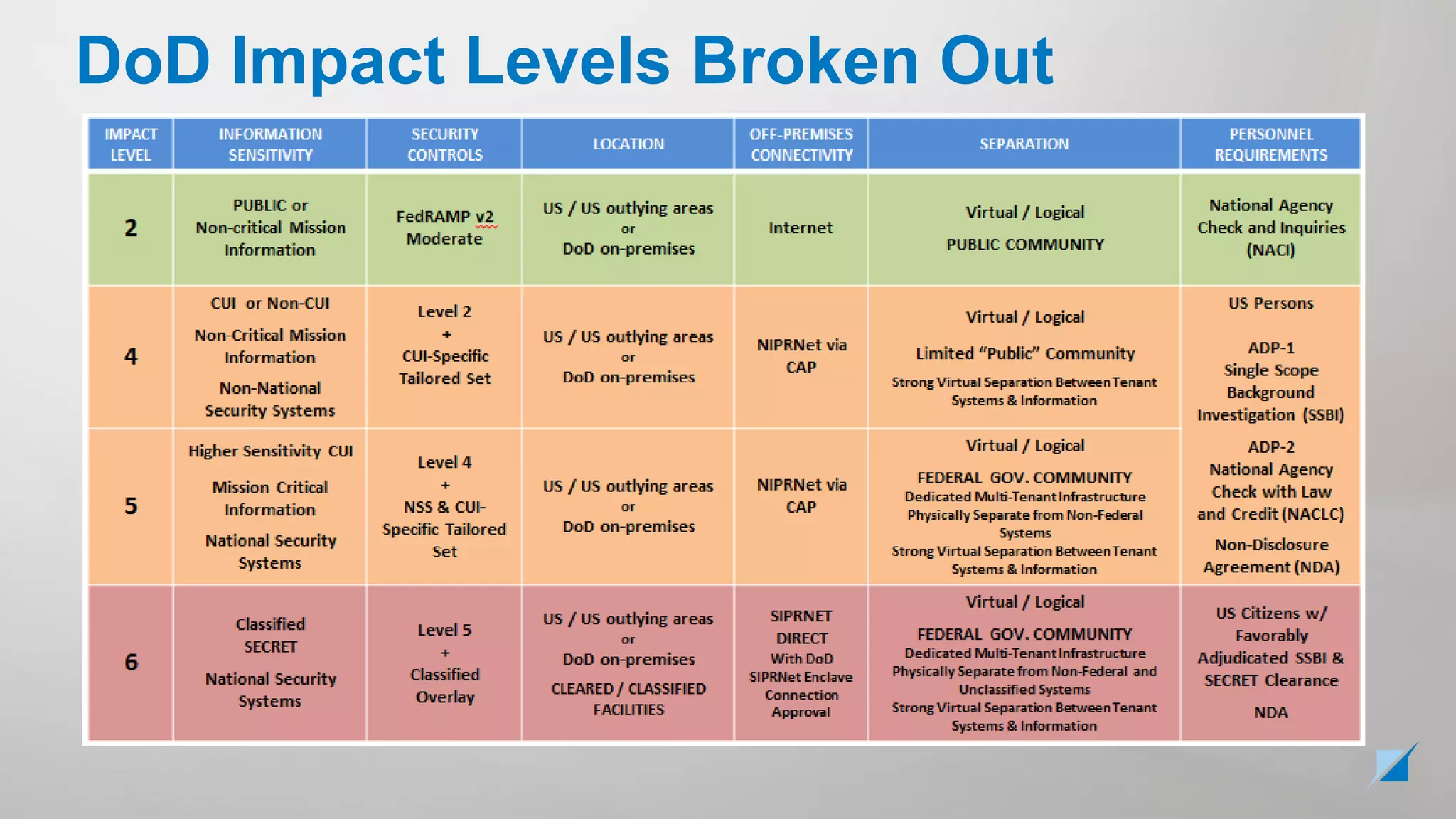
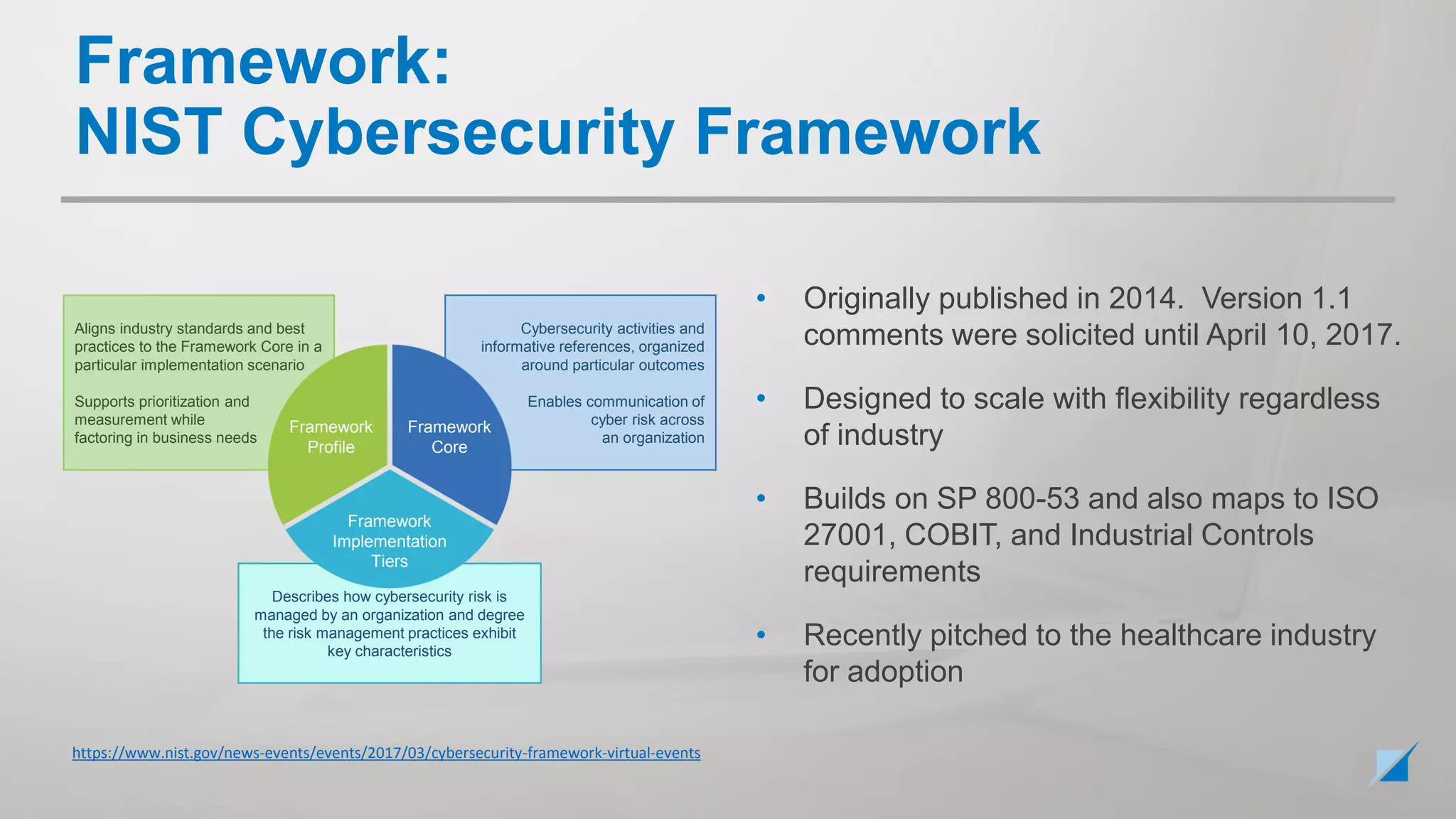
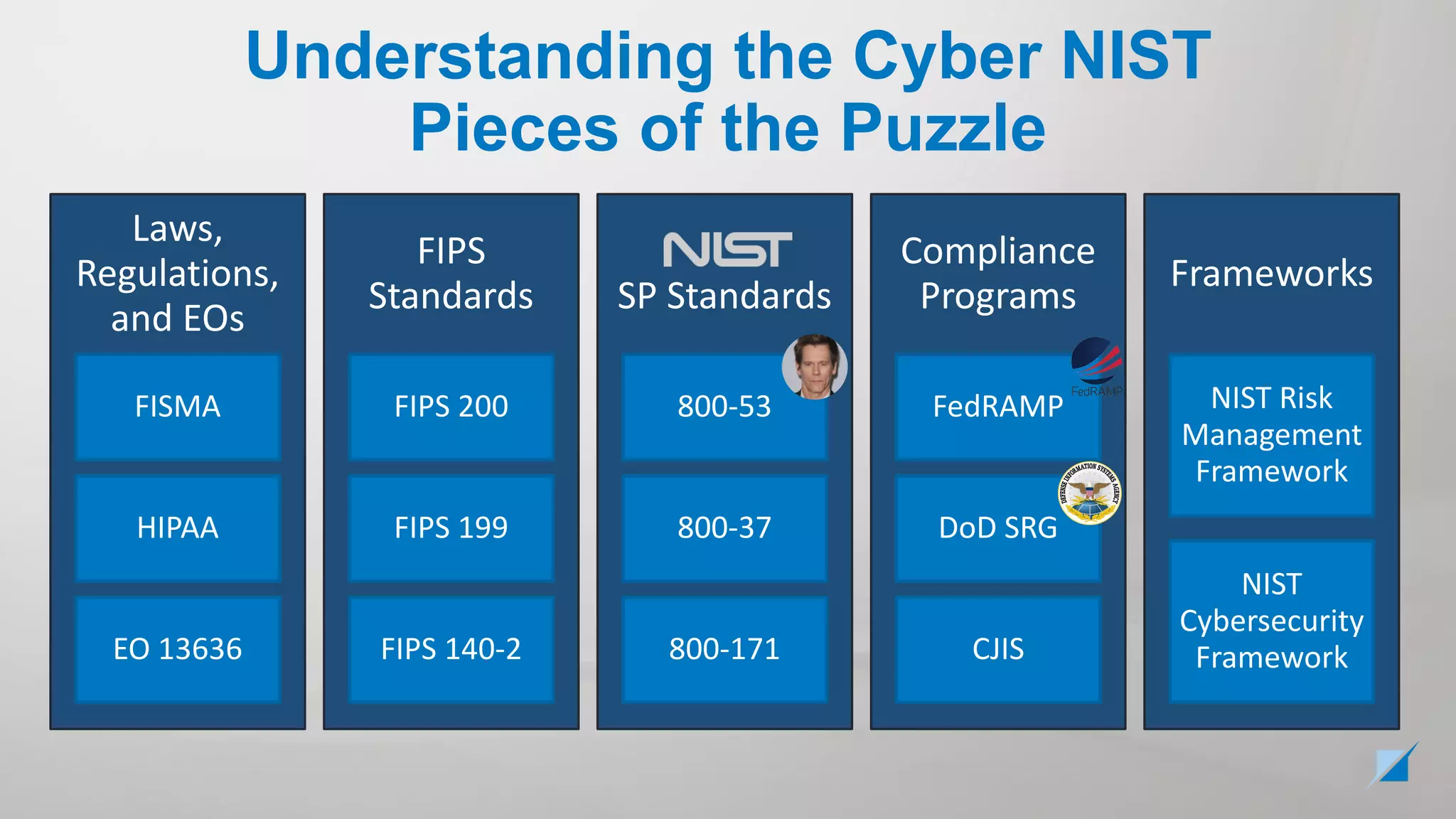
The document provides an overview of the various cybersecurity laws, regulations, frameworks, and standards relevant to federal compliance, particularly those governed by NIST. It discusses key elements such as FISMA, the NIST Special Publications like SP 800-53 and SP 800-171, and the Federal Risk and Authorization Management Program (FedRAMP). The goal is to clarify the relationships among these components and dispel misconceptions while providing guidance for organizations dealing with federal cybersecurity requirements.