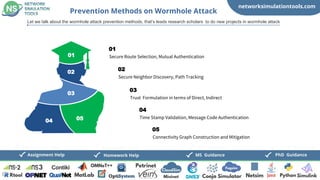
The document discusses various techniques for detecting and preventing wormhole attacks in network simulations, including location validation, authentication, and trust formulation. It outlines imminent project topics for research scholars, such as lightweight cryptosystems and software-defined routing. Additionally, it offers guidance and assistance for PhD and MS students focusing on these topics.